The document provides a comprehensive overview of Linux server administration, detailing tasks such as system monitoring, user and group management, filesystem management, software installation, and networking. Key components discussed include booting processes, runlevels, scheduling with cron, as well as configuring and managing various server services like Samba for file sharing, FTP for file transfer, and Apache for web serving. Additionally, it covers user security, privileges, and the organization of configuration files critical for system administration.














![Shutting Down the System
O Syntax:
shutdown [options] time [message]
O Time: XX:XX or +X or NOW
O -k: don’t really shutdown, just send message
O -r: reboot
O -h: halt
O -c: cancel a shutdown
O halt: calls shutdown –h
O reboot: calls shutdown -r](https://image.slidesharecdn.com/introtolinuxsystemsadministration-171120132400/85/Intro-to-linux-systems-administration-15-320.jpg)


















![Adding Users, cont
O Syntax:
useradd [options] [-g group] [-
d home]
[-s shell] username
O -g to define user’s initial group
O -d to define user’s home directory
O -s to define user’s default shell
O Other options for expiration, using defaults,
etc](https://image.slidesharecdn.com/introtolinuxsystemsadministration-171120132400/85/Intro-to-linux-systems-administration-34-320.jpg)
![Deleting Users
O Again, could just hack /etc/passwd
O More elegant:
O Syntax: userdel [-r] username
O -r to delete home directory and it’s contents](https://image.slidesharecdn.com/introtolinuxsystemsadministration-171120132400/85/Intro-to-linux-systems-administration-35-320.jpg)
![Modifying Users
O Syntax: usermod [options]
username
O Options are pretty much identical to those of
useradd
O Also, -l to change the user’s login name
O And –G to list additional groups to add user
to](https://image.slidesharecdn.com/introtolinuxsystemsadministration-171120132400/85/Intro-to-linux-systems-administration-36-320.jpg)



![ifconfig
O Displays or alters network device configs
O Syntax:
ifconfig interface
[options]
O With no options, shows interface’s config
O If interface omitted as well, show all configs
O Options include flags, IP address, subnet
mask, etc](https://image.slidesharecdn.com/introtolinuxsystemsadministration-171120132400/85/Intro-to-linux-systems-administration-41-320.jpg)



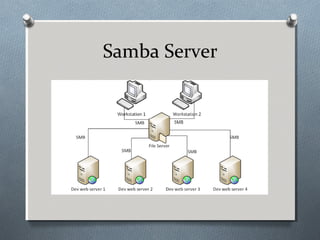
![Samba Server Installation
O Step 1: Install the vsftpd package:
O [root@localhost Desktop] # yum install
vsftpd
O Step 2: Configure the software:
O [root@localhost Desktop] # vim
/etc/vsftpd/vsftpd.conf
O Step 3: Starting the service:
O [root@localhost Desktop] # systemctl start
smb
O The service of Samba Web Server is started.](https://image.slidesharecdn.com/introtolinuxsystemsadministration-171120132400/85/Intro-to-linux-systems-administration-47-320.jpg)


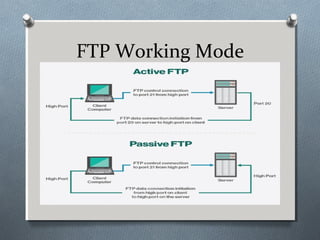
![FTP Installation
O Step 1: Install the vsftpd package:
O [root@localhost Desktop] # yum
install vsftpd
O Step 2: Configure the software:
O [root@localhost Desktop] # vim
/etc/vsftpd/vsftpd.conf
O Step 3: Starting the service:
O [root@localhost Desktop] #
systemctl start vsftpd](https://image.slidesharecdn.com/introtolinuxsystemsadministration-171120132400/85/Intro-to-linux-systems-administration-52-320.jpg)

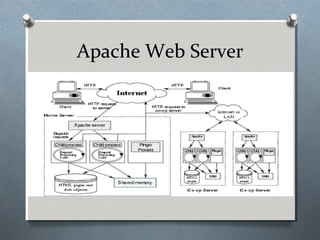

![Installation of HTPD
O Step 1: Install the httpd package:
O [root@localhost Desktop] # yum
install httpd
O Step 2: Configure the software:
O [root@localhost Desktop] # vim
/etc/httpd/conf/httpd.conf
O Step 3: Starting the service:
O [root@localhost Desktop] #
systemctl start httpd](https://image.slidesharecdn.com/introtolinuxsystemsadministration-171120132400/85/Intro-to-linux-systems-administration-56-320.jpg)
