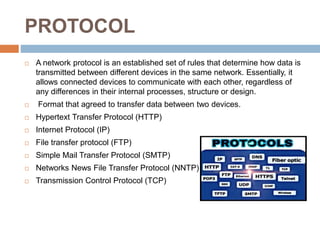
The document discusses the history, components, uses, and advantages/disadvantages of the Internet. It provides definitions of key terms like the World Wide Web, web browsers, search engines, and protocols. The Internet began in 1969 as a US government military network and became publicly available in the 1990s. It allows for communication, research, education, financial transactions, and more. However, it also enables the theft of personal information, spamming, malware infections, and social isolation in some cases. Nursing utilizes the Internet for communication, research, education, and accessing diagnostic and job information.