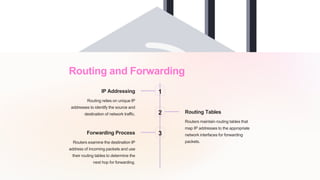
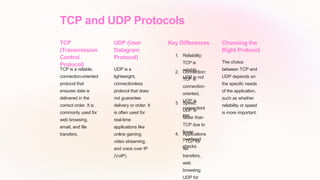
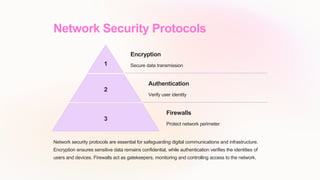
The document provides an introduction to foundational internet protocols. It discusses the TCP/IP model which consists of four layers and relies on standardized protocols like TCP, IP, HTTP, and SMTP. The modular design allows for flexibility and adaptation over time. It also covers IP addressing, routing, TCP and UDP protocols, HTTP and HTTPS, DNS, DHCP, and network security protocols.