Tcp protocols
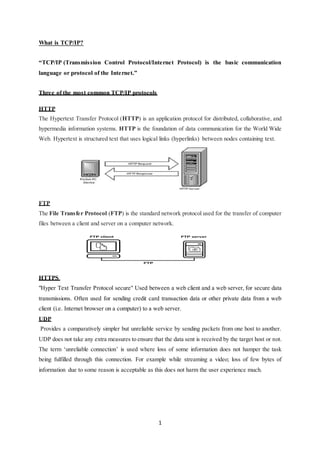
- 1. 1 What is TCP/IP? “TCP/IP (Transmission Control Protocol/Internet Protocol) is the basic communication language or protocol of the Internet.” Three of the most common TCP/IP protocols HTTP The Hypertext Transfer Protocol (HTTP) is an application protocol for distributed, collaborative, and hypermedia information systems. HTTP is the foundation of data communication for the World Wide Web. Hypertext is structured text that uses logical links (hyperlinks) between nodes containing text. FTP The File Transfer Protocol (FTP) is the standard network protocol used for the transfer of computer files between a client and server on a computer network. HTTPS "Hyper Text Transfer Protocol secure" Used between a web client and a web server, for secure data transmissions. Often used for sending credit card transaction data or other private data from a web client (i.e. Internet browser on a computer) to a web server. UDP Provides a comparatively simpler but unreliable service by sending packets from one host to another. UDP does not take any extra measures to ensure that the data sent is received by the target host or not. The term ‘unreliable connection’ is used where loss of some information does not hamper the task being fulfilled through this connection. For example while streaming a video; loss of few bytes of information due to some reason is acceptable as this does not harm the user experience much.
- 2. 2 SMTP SMTP stands for Simple Mail Transfer Protocol. SMTP is used when email is delivered from an email client, such as Outlook Express, to an email server or when email is delivered from one email server to another. Domain names and TCP/IP addresses The TCP/IP address for a website or web server is typically not easy to remember. To remedy this issue, a domain name is used instead. For example, 216.58.216.164 is one of the IP address for Google and google.com is the domain name. Using this method, instead of a set of numbers, makes it much easier for users to remember Computer Hope's web address. Difference between TCP and UDP. TCP Transfer control protocol. UDP User diagram protocol. 1) Connection oriented. Connectionless. 2) Slower transmission of data. Faster transmission of data. 3) Resend of lost data. Do not resend of lost data. 4) Error checking. Errors not checked. 5)TCP does not control the Flow of data. UDP control the flow of data. 6) TCP header size is 20 bytes. UDP header size is 8 bytes. 7) Required more computer resources. Required less computer resources.