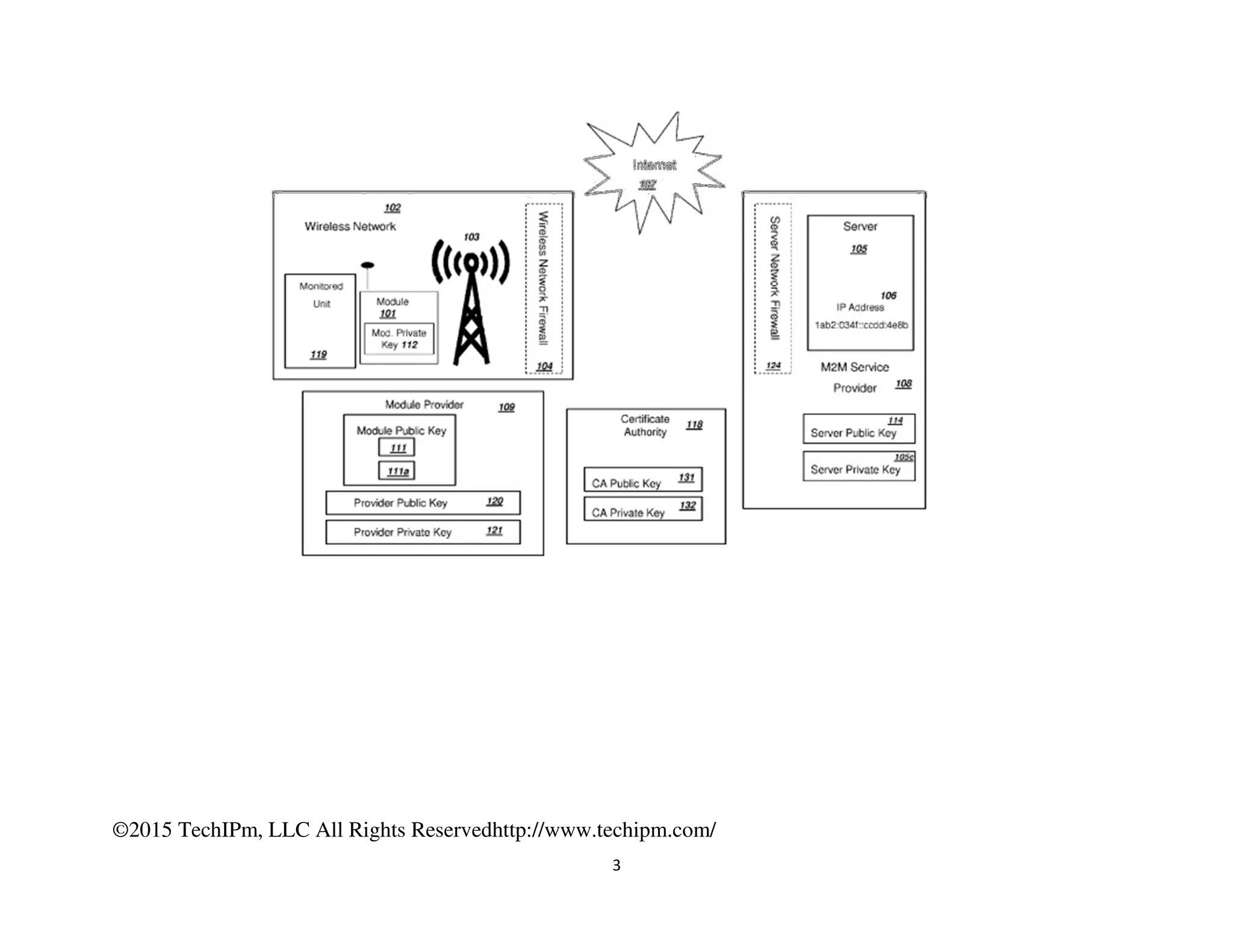
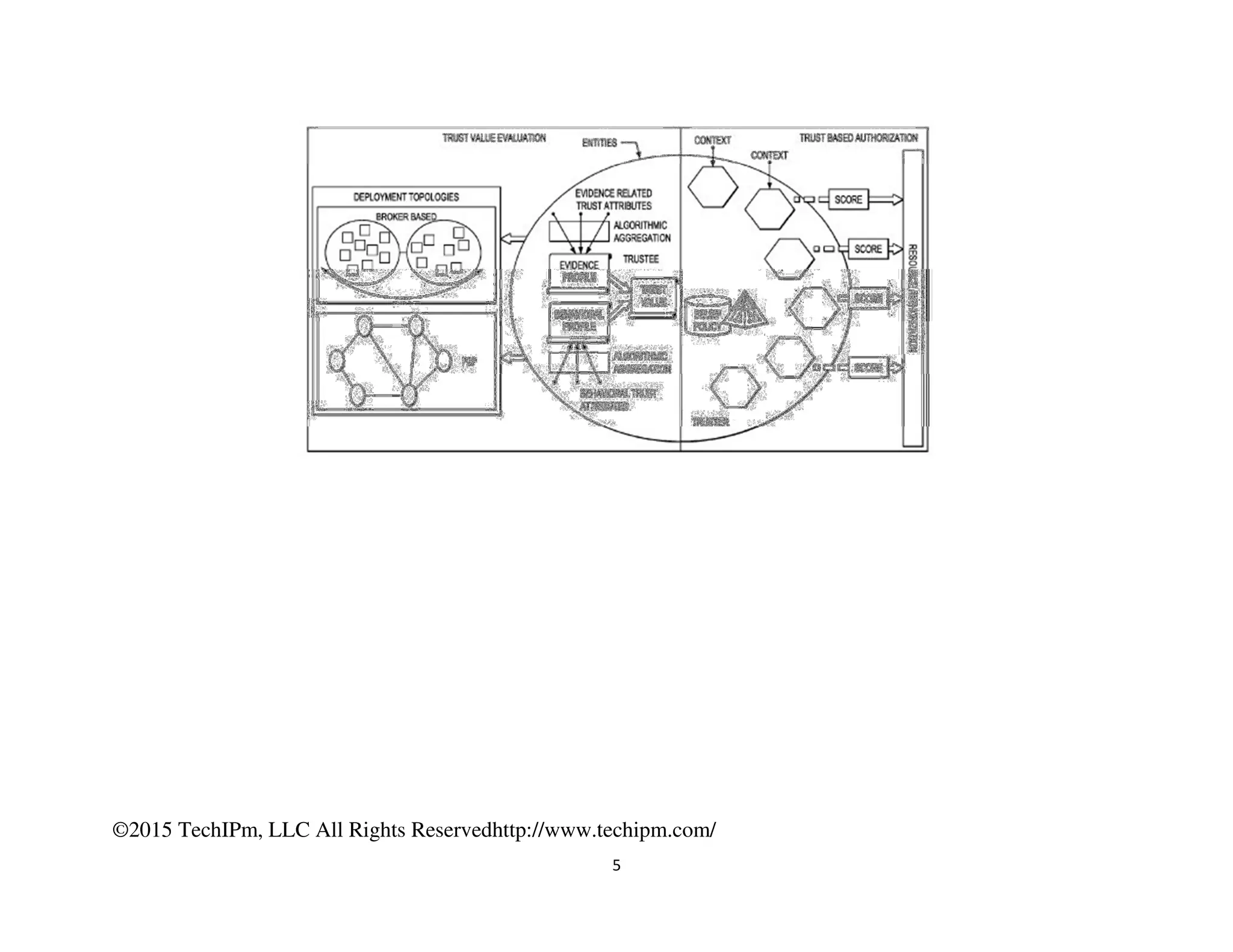
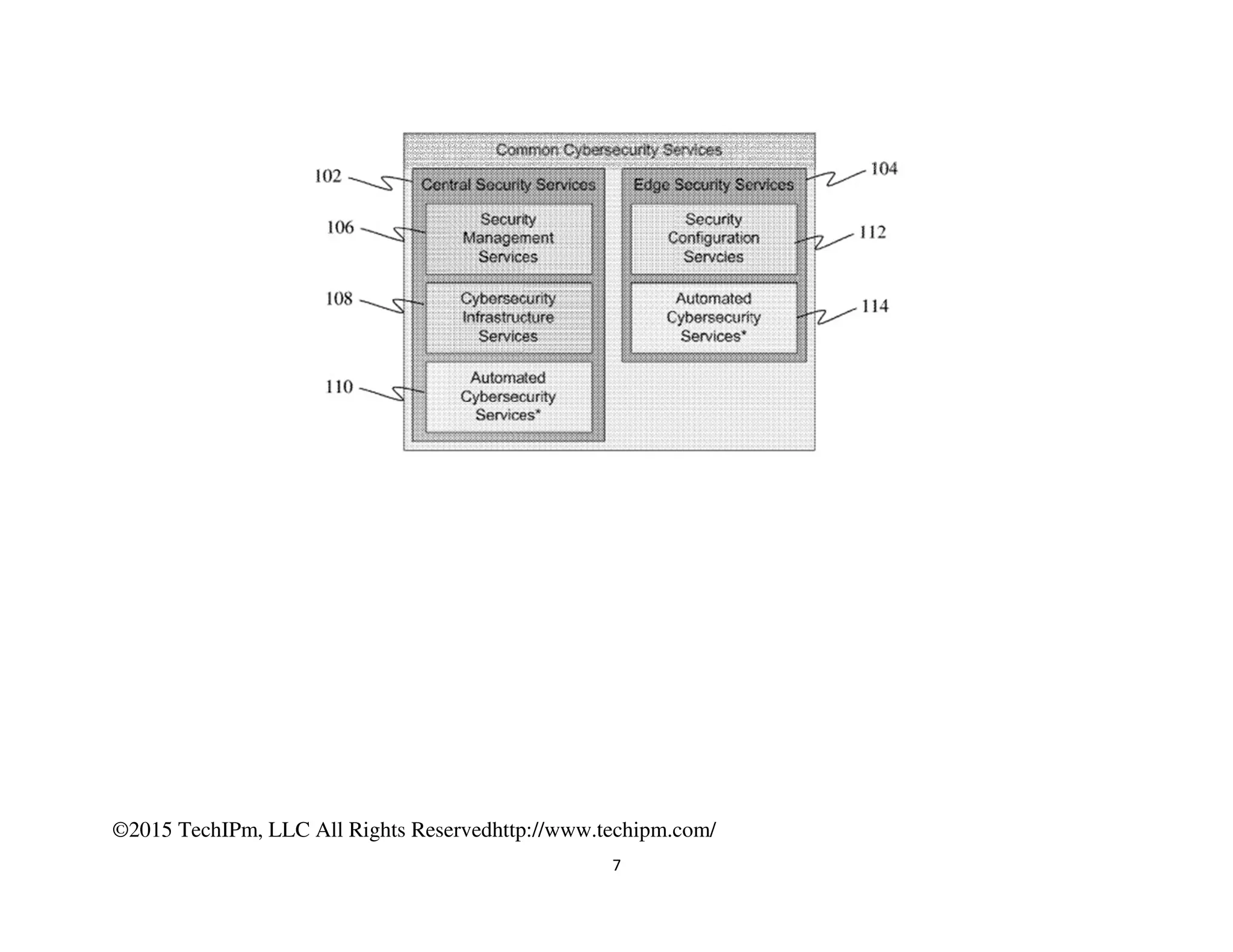
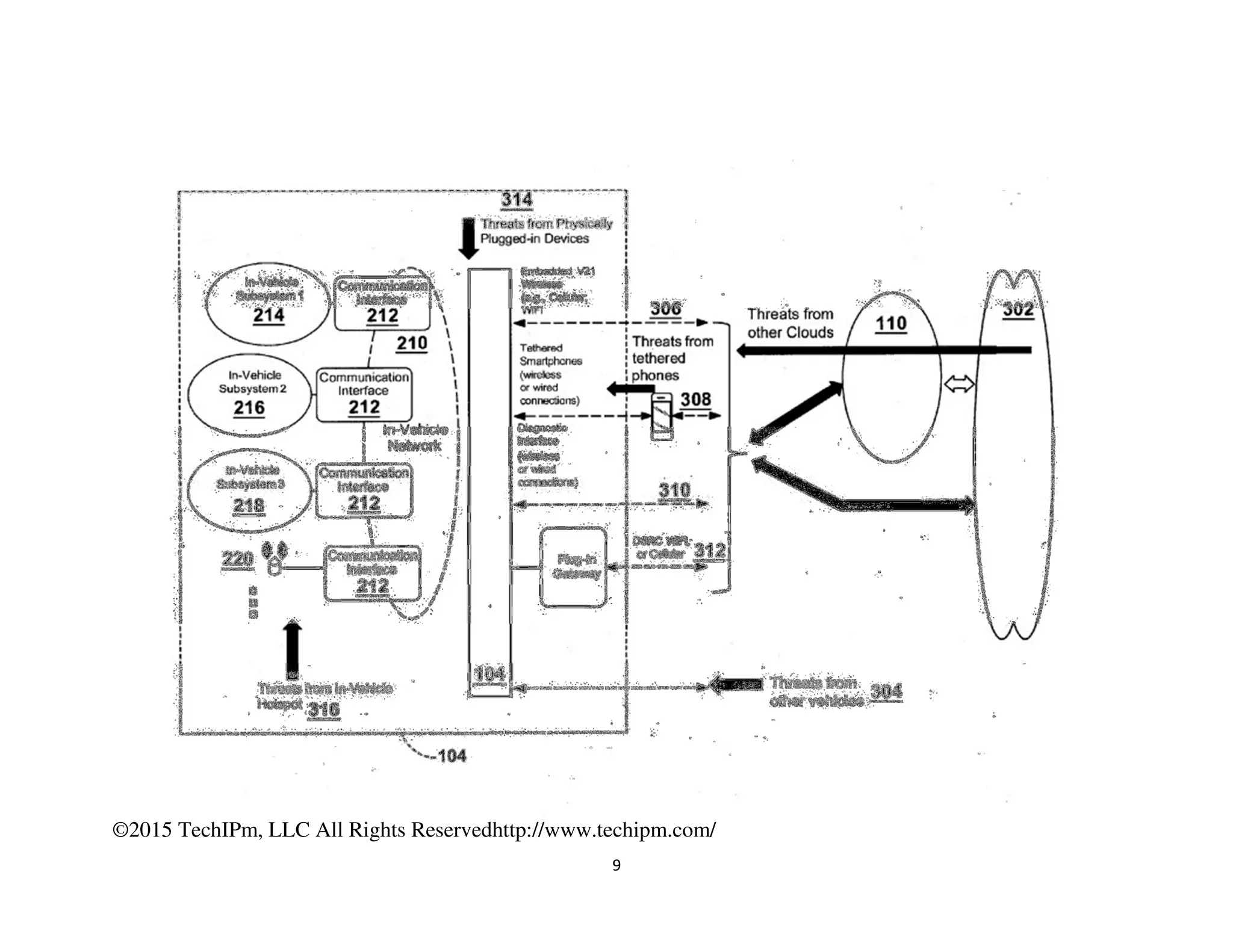
The document discusses various security measures for the Internet of Things (IoT), emphasizing the importance of centralized and distributed security architectures to manage access and trust in IoT networks. It highlights patent illustrations of systems that enable secure communications among IoT devices, smart grids, and connected cars, incorporating cryptographic techniques and trust management frameworks. Specific examples include systems for securing electric grids against cyber-attacks and protecting vehicle electronic systems from unauthorized communications.