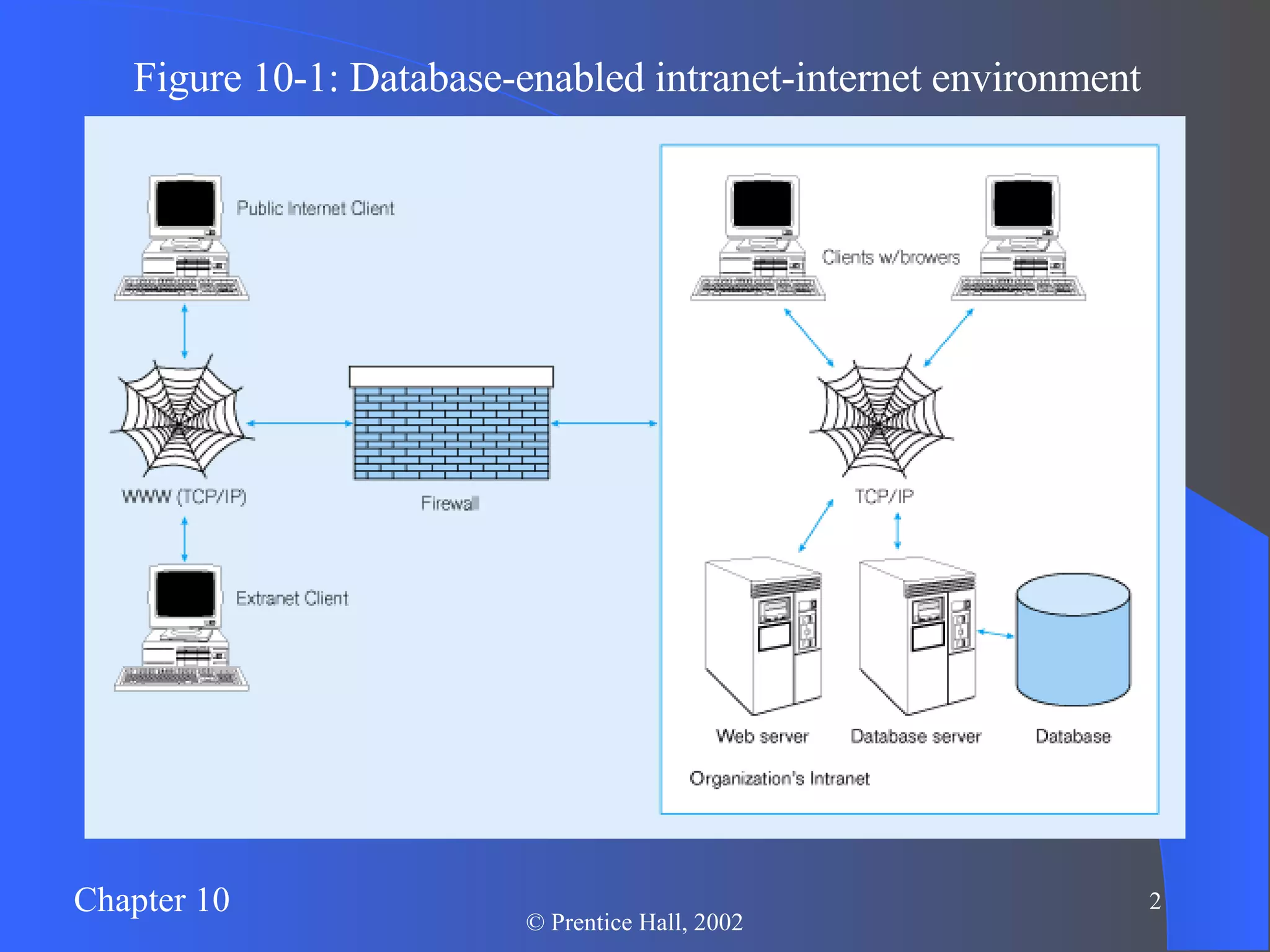
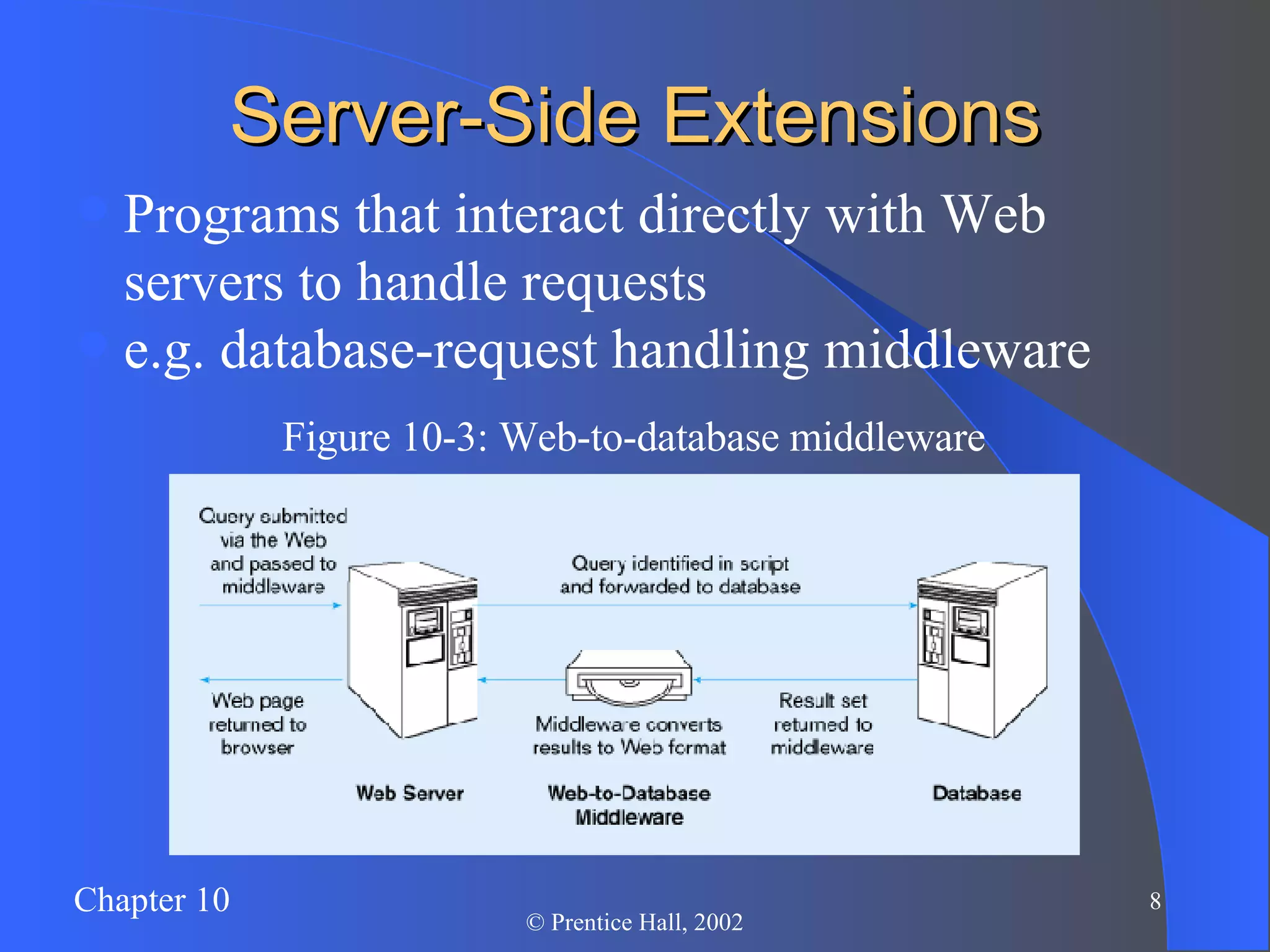
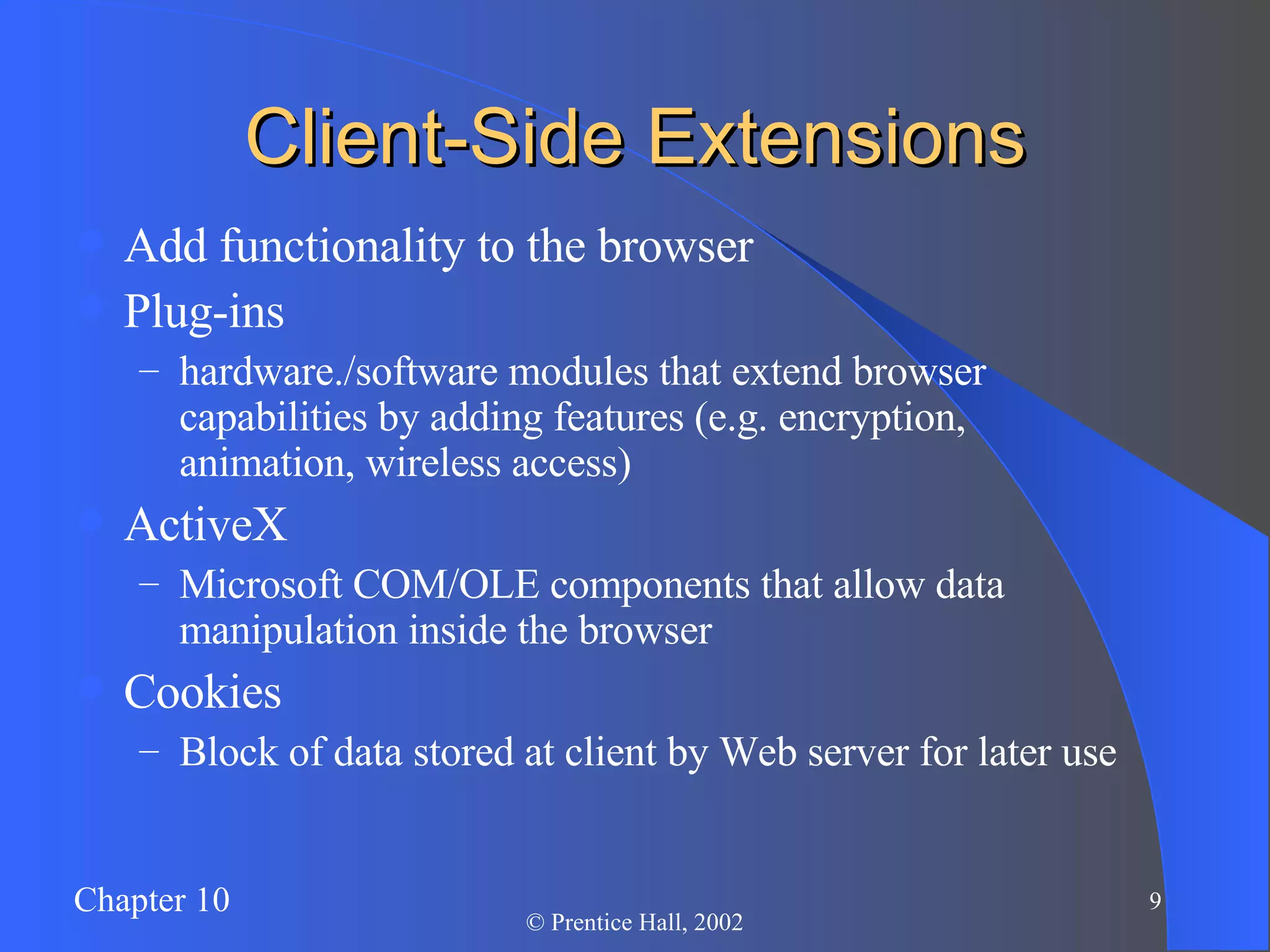
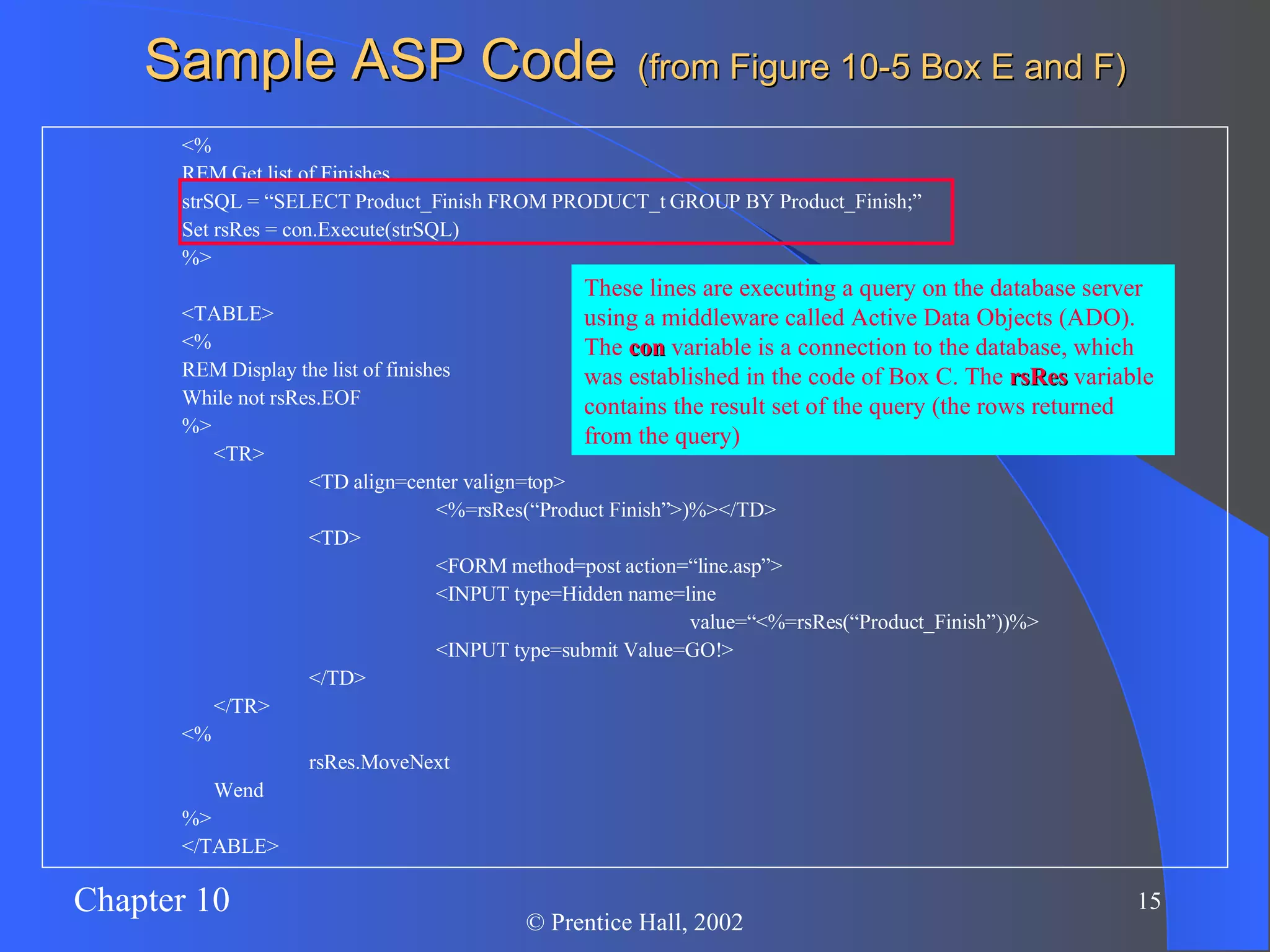
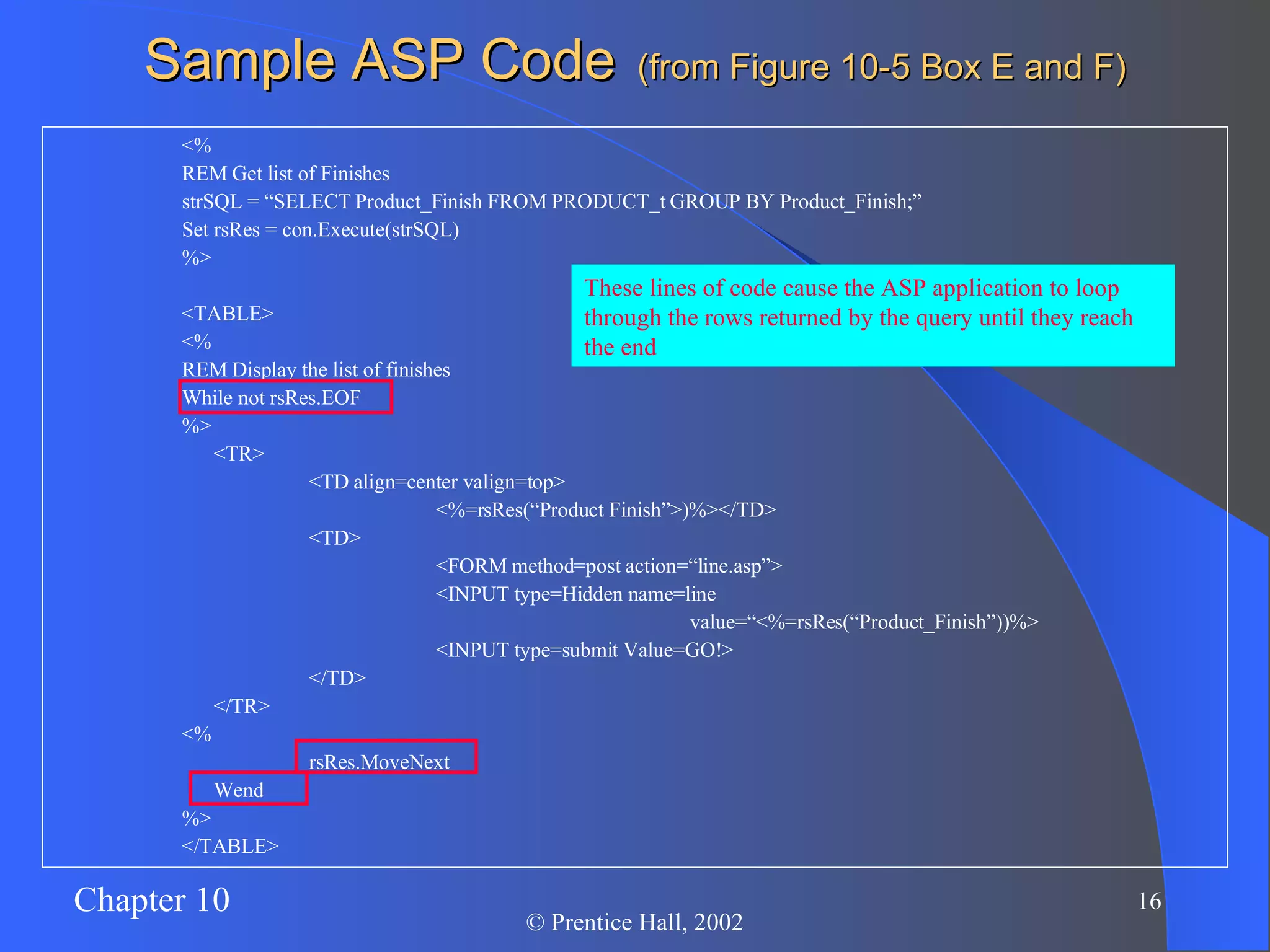
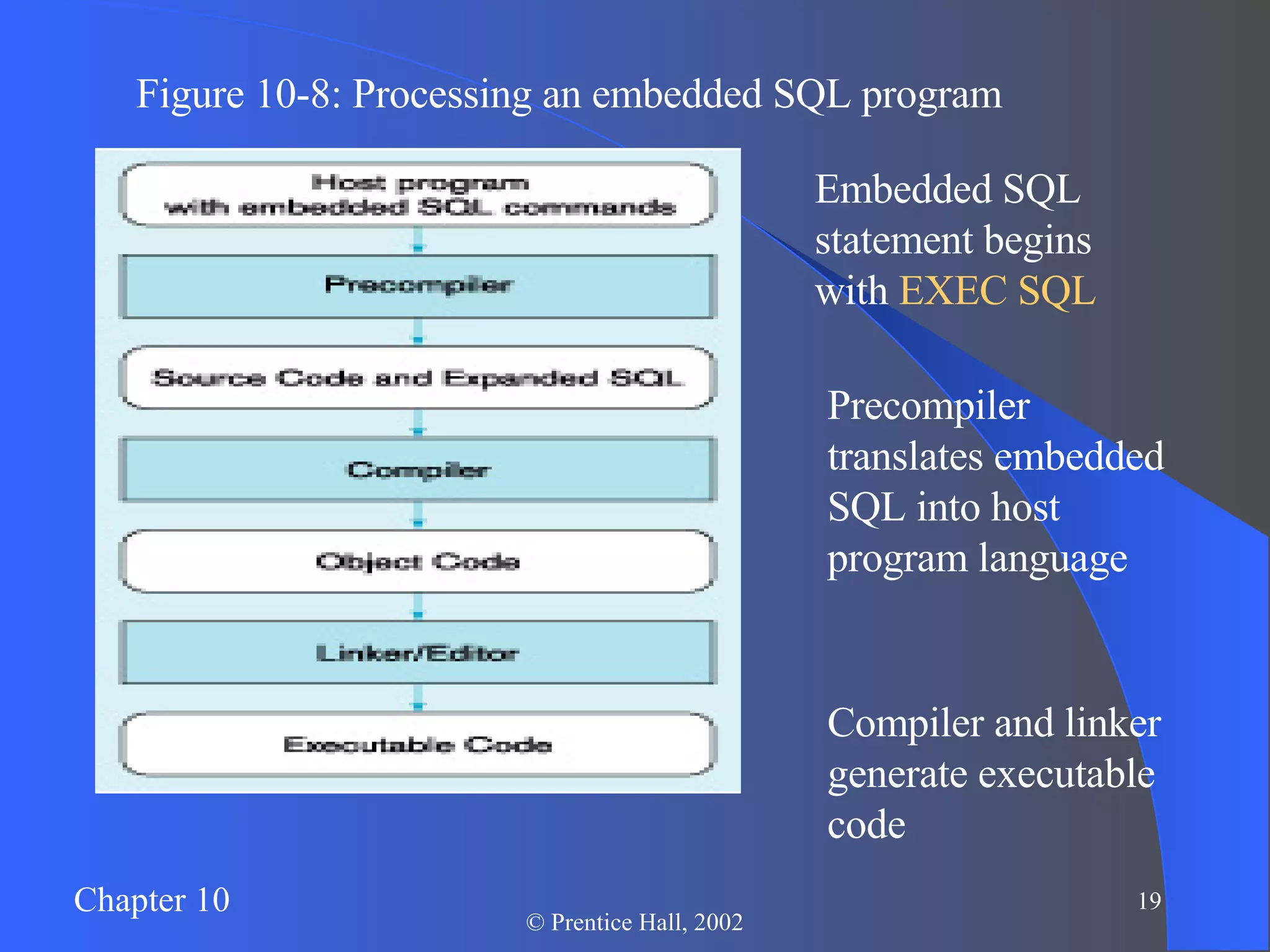
The document discusses database management in an internet environment. It describes how businesses use the internet for e-commerce and interactions with customers and suppliers. It also defines common web technologies like HTML, URLs, browsers, web servers and how they enable dynamic web pages and interactions with databases through scripts, APIs and middleware. Specific examples are provided of Active Server Pages code that queries a database and dynamically generates web page content. The document concludes with a discussion of managing website data and security considerations to prevent unauthorized access.