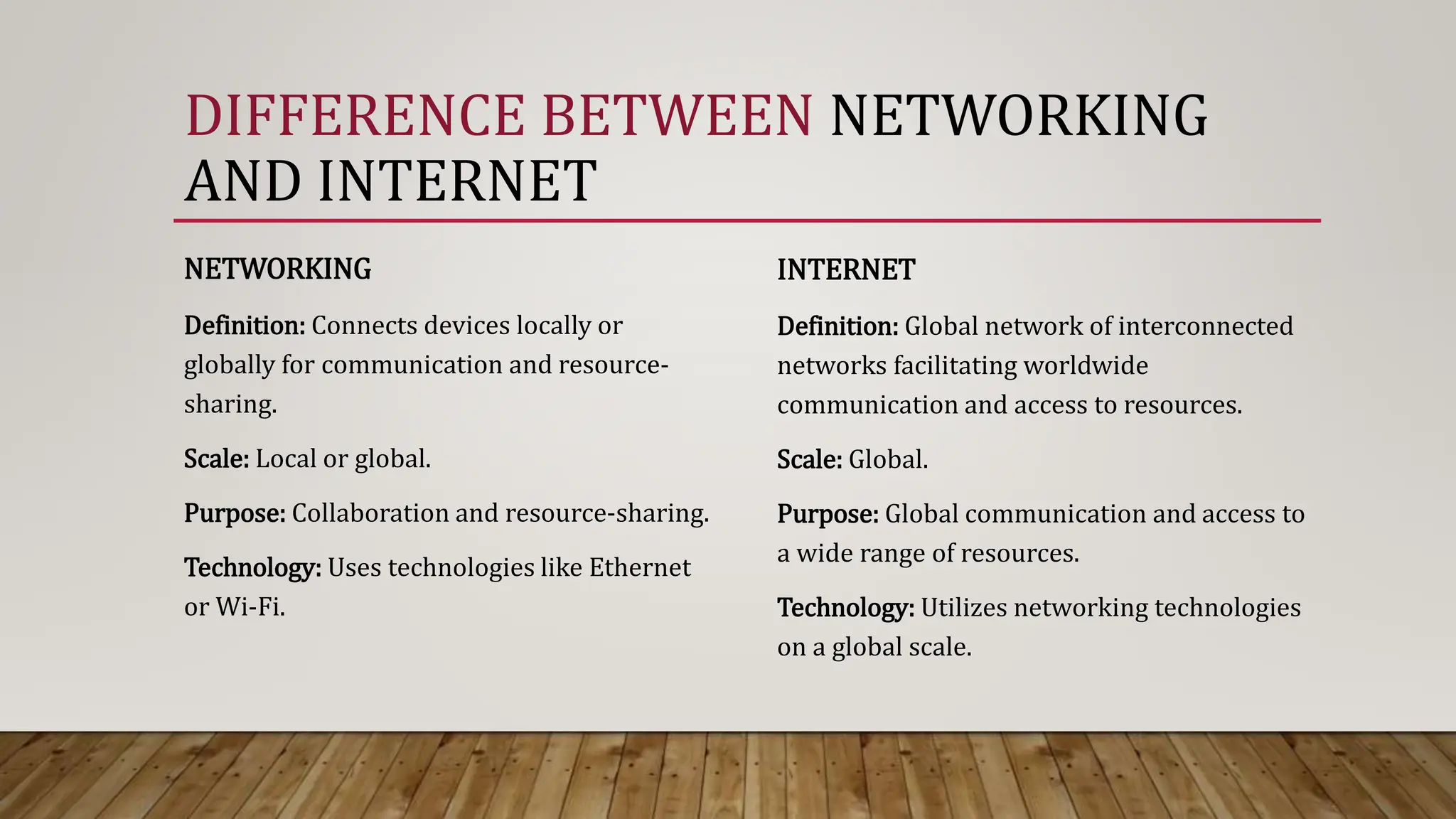
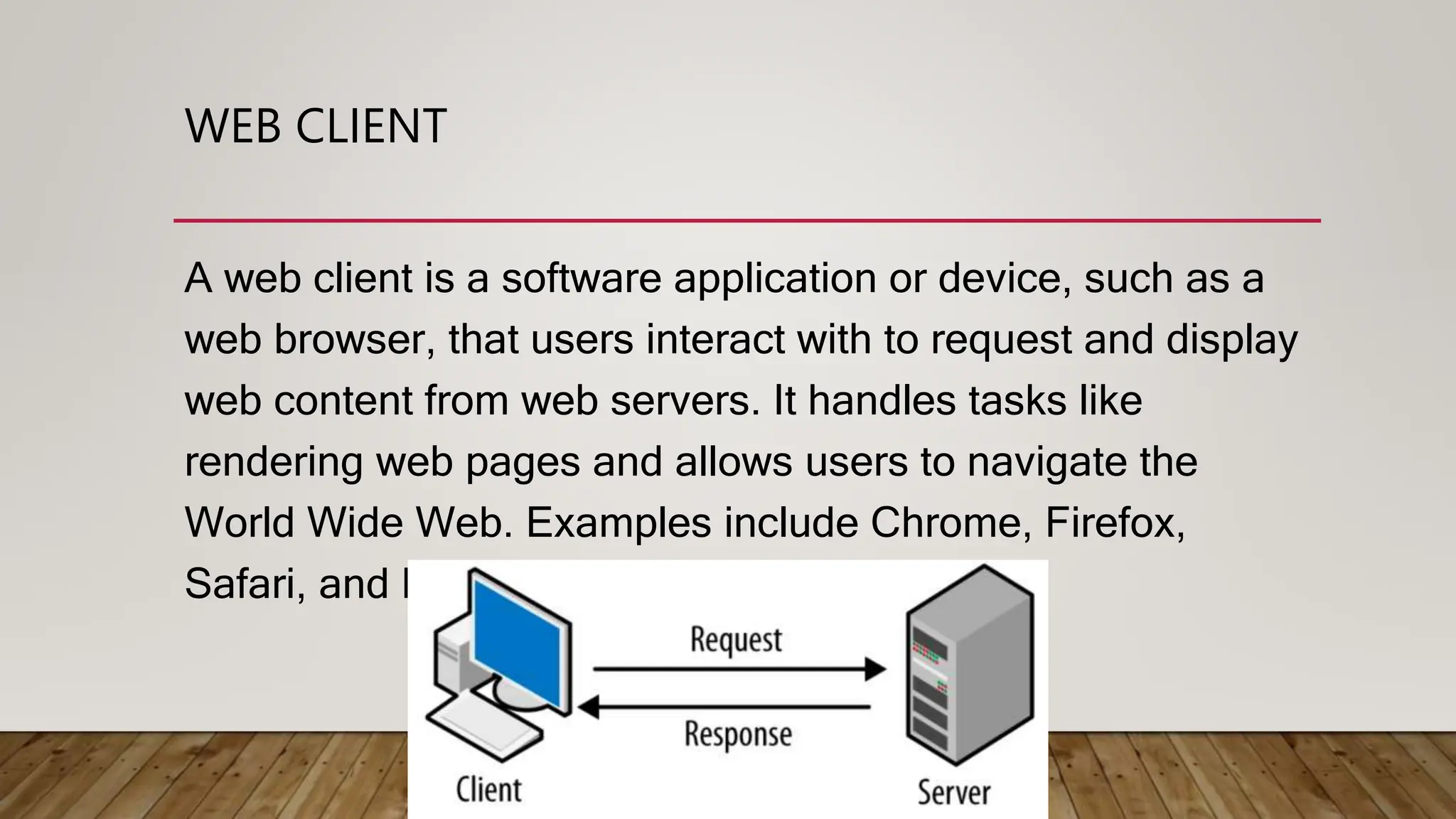
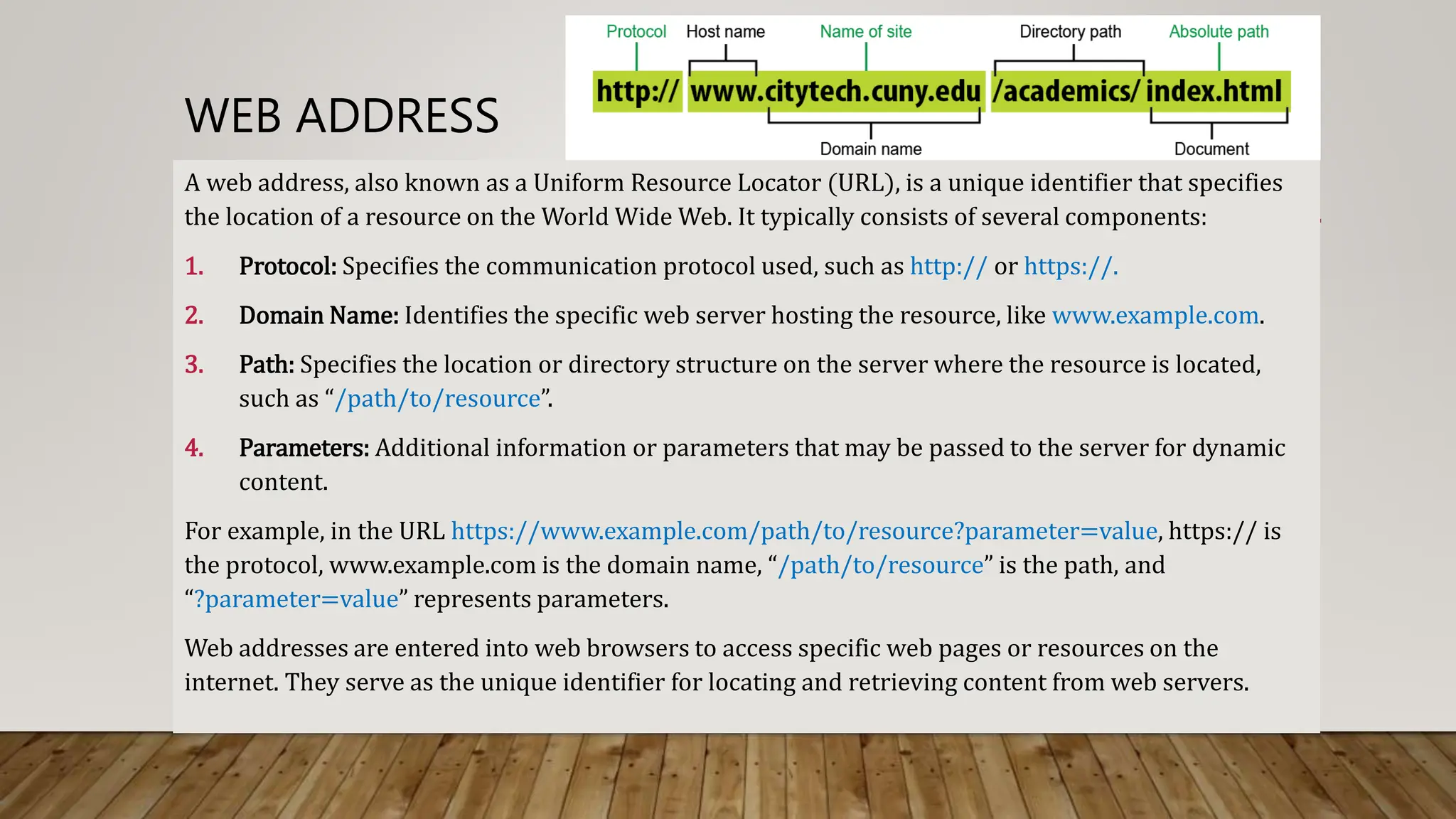
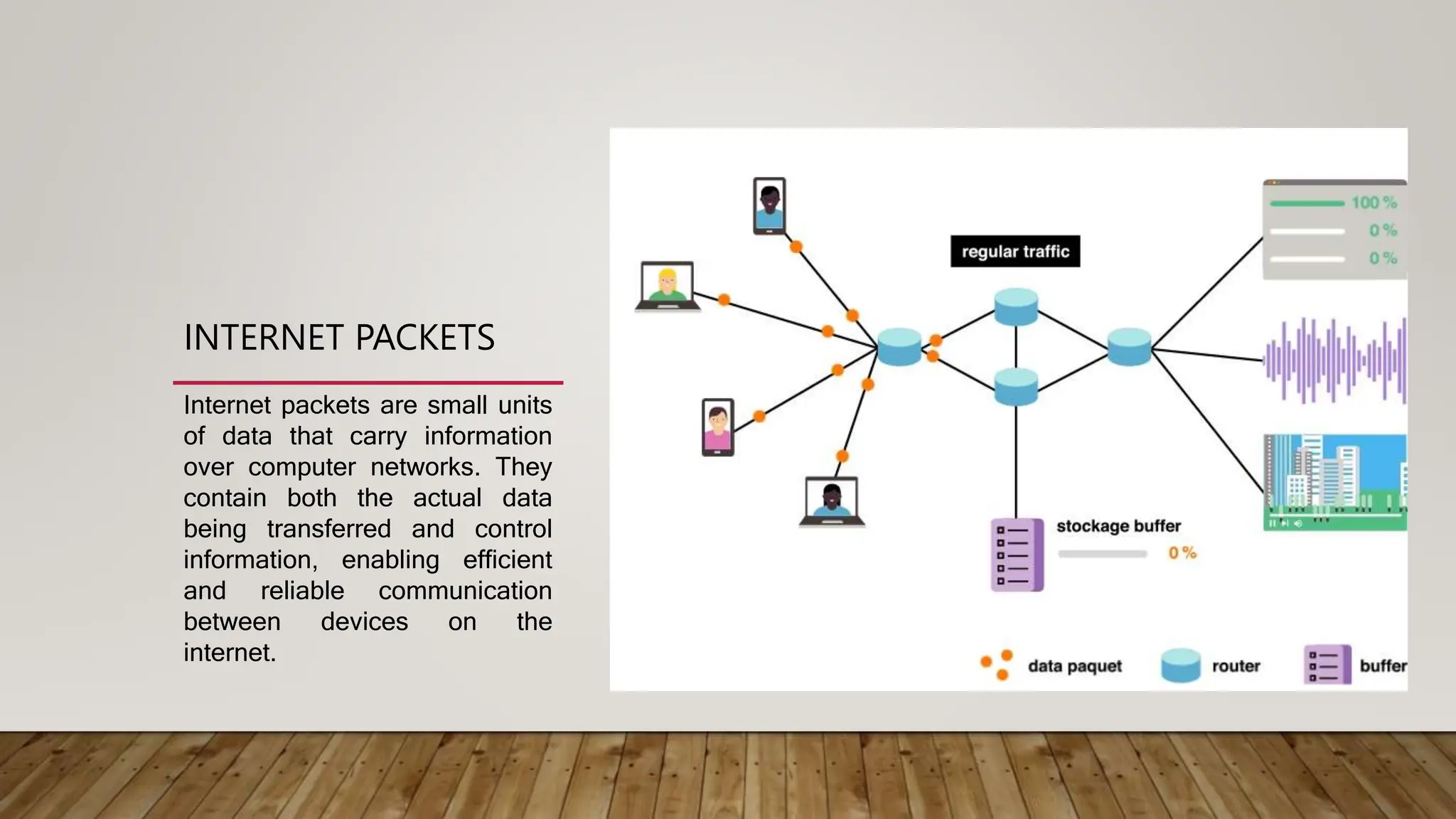
The document provides an overview of the internet and computer networking, including definitions, history, and key technologies. It distinguishes between the internet as a global network and the World Wide Web as a system of interlinked documents accessible via browsers. Additionally, it discusses advantages, disadvantages, limitations, and security issues associated with the internet, emphasizing the need for careful management to ensure a safe digital environment.