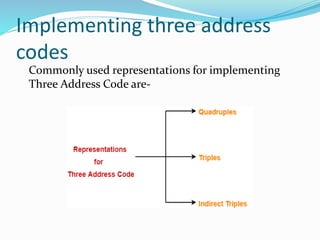
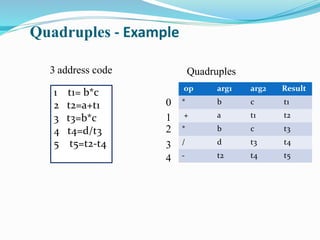
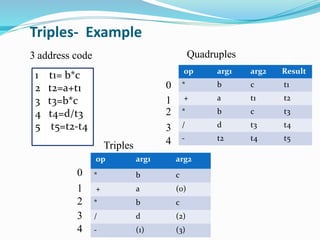
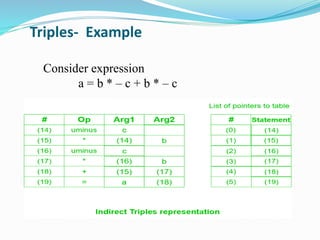
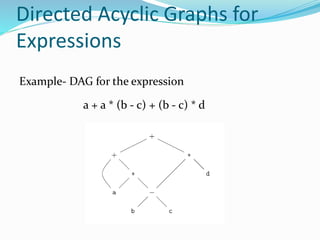
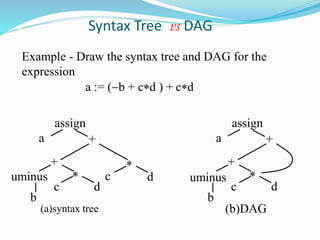
The document discusses different representations of intermediate code in compilers, including high-level and low-level intermediate languages. High-level representations like syntax trees and DAGs depict the structure of the source program, while low-level representations like three-address code are closer to the target machine. Common intermediate code representations discussed are postfix notation, three-address code using quadruples/triples, and syntax trees.






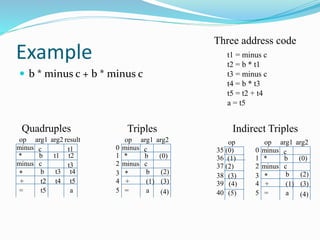
![Three Address Statements
Assignment statements:
x = y op z
x = op y
Indexed assignments:
x = y[i], x[i] = y
Pointer assignments:
x = &y, x = *y
Copy statements:
x = y
Unconditional jumps
goto lab
Conditional jumps:
if x relop y
goto lab
Function call
param x… call p,
n return y](https://image.slidesharecdn.com/icgpart1-200427060343/85/Intermediate-code-generator-16-320.jpg)