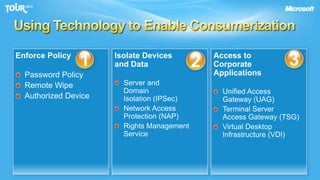
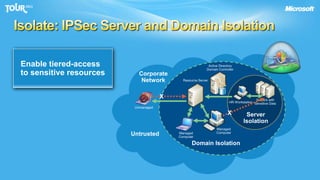
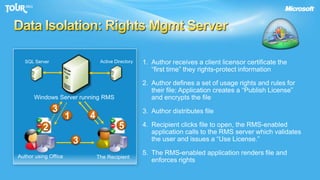
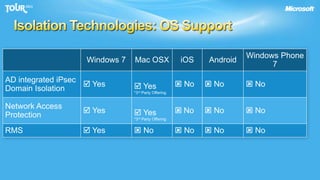
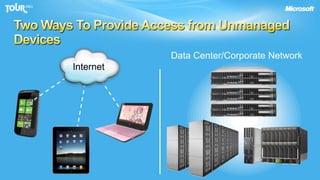
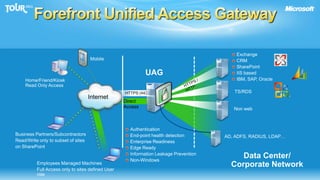
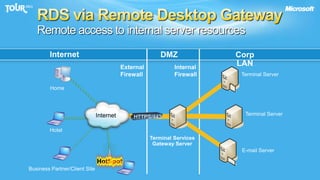
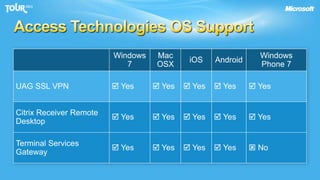
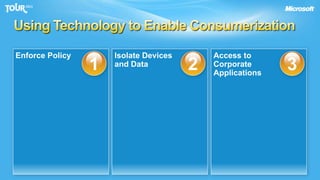
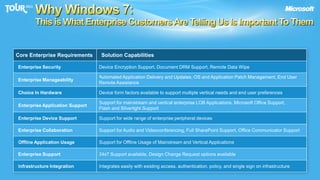
The document discusses enabling consumerization in the enterprise by allowing employees to use personal devices for work. It outlines challenges like ensuring security and compliance when devices are unmanaged. It then presents strategies for isolating devices and data, providing access to corporate applications, and enforcing policies. These include virtualization, mobile device management through Exchange, and using technologies like Network Access Protection and Rights Management to isolate networks and protect sensitive data.