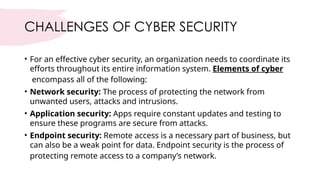
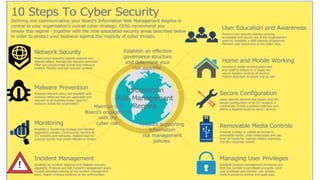
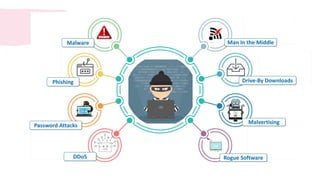
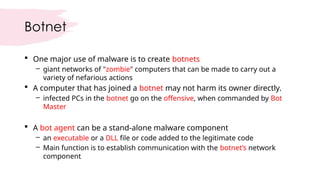
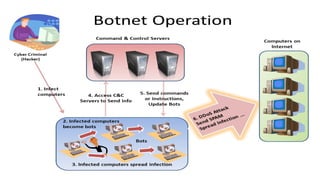
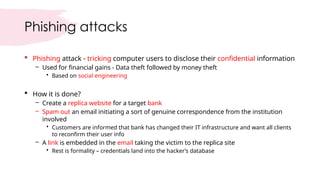
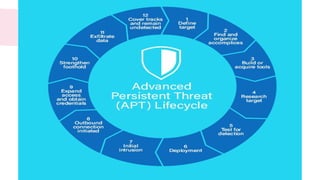
Cybersecurity encompasses technologies, processes, and practices to protect networks, devices, and data from unauthorized access and attacks. It is crucial in today's technology-driven world to prevent data theft and ensure business continuity amid an increase in cyber threats. The document outlines various sub-domains of cybersecurity, the types of cyber threats, and the importance of user education in developing a robust security posture.