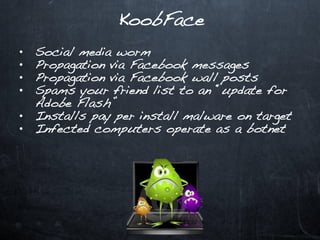
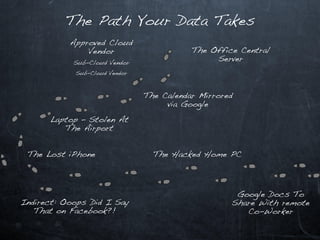
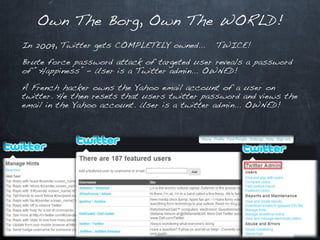
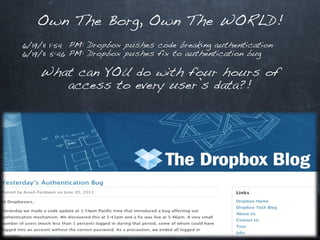
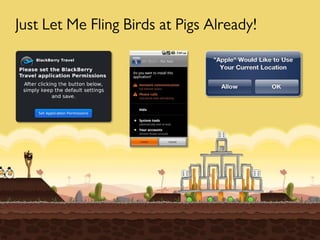
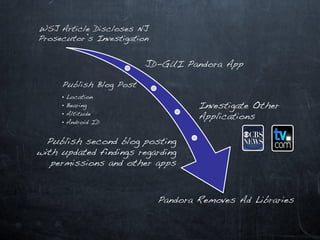
This document discusses emerging security challenges in an increasingly mobile, social, and cloud-based computing landscape. It notes that traditional perimeter-based security is ineffective as computing becomes more ubiquitous and decentralized. Mobile applications and social networks provide fertile ground for malware propagation. Cloud services mean data can take complex, indirect paths outside of a user's control. Passwords are often trivial to guess. Code from third parties and libraries may introduce vulnerabilities. A new security paradigm is needed to address these challenges, as permissions alone will not suffice. Users must think differently about security in this new environment.