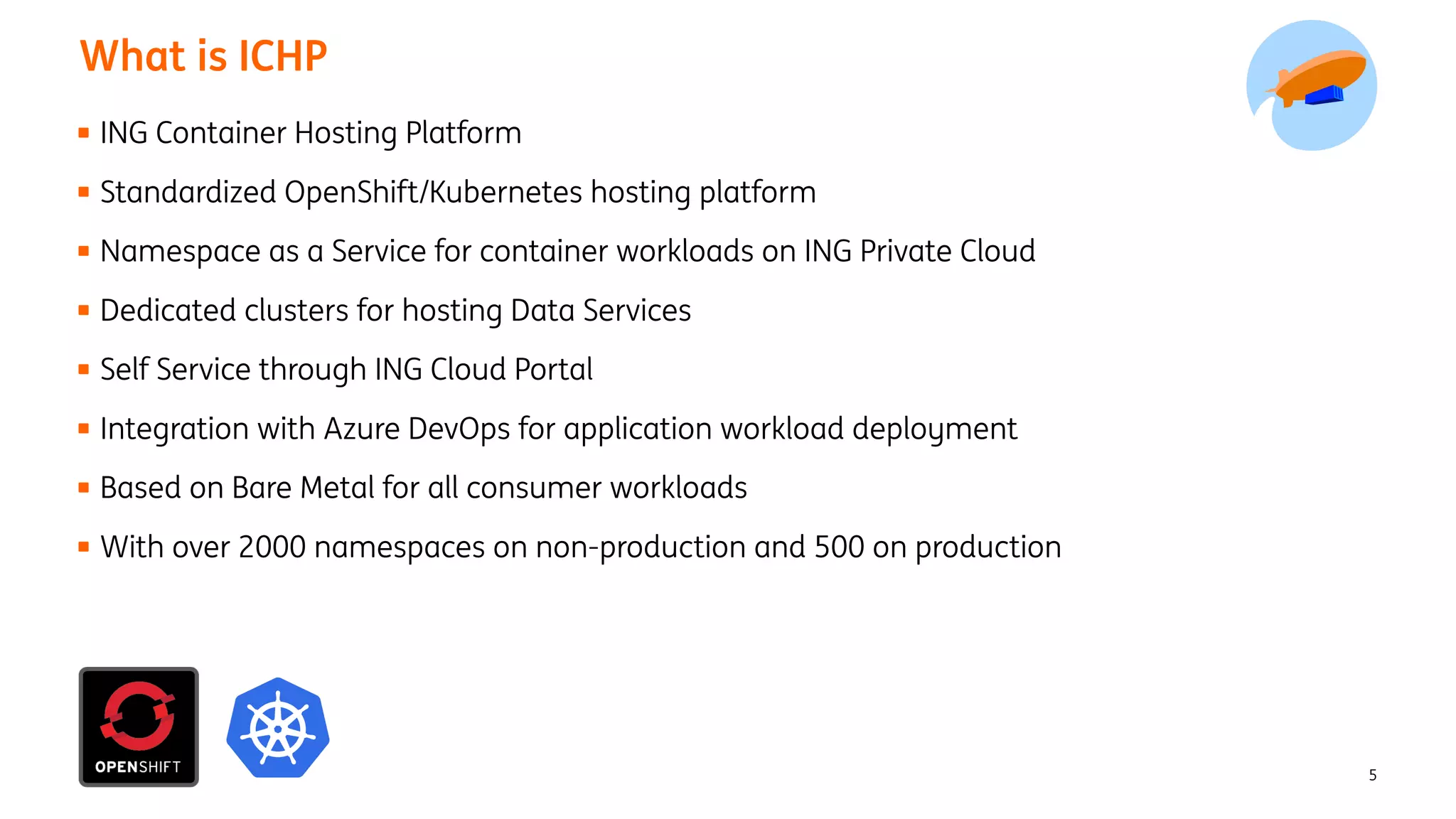
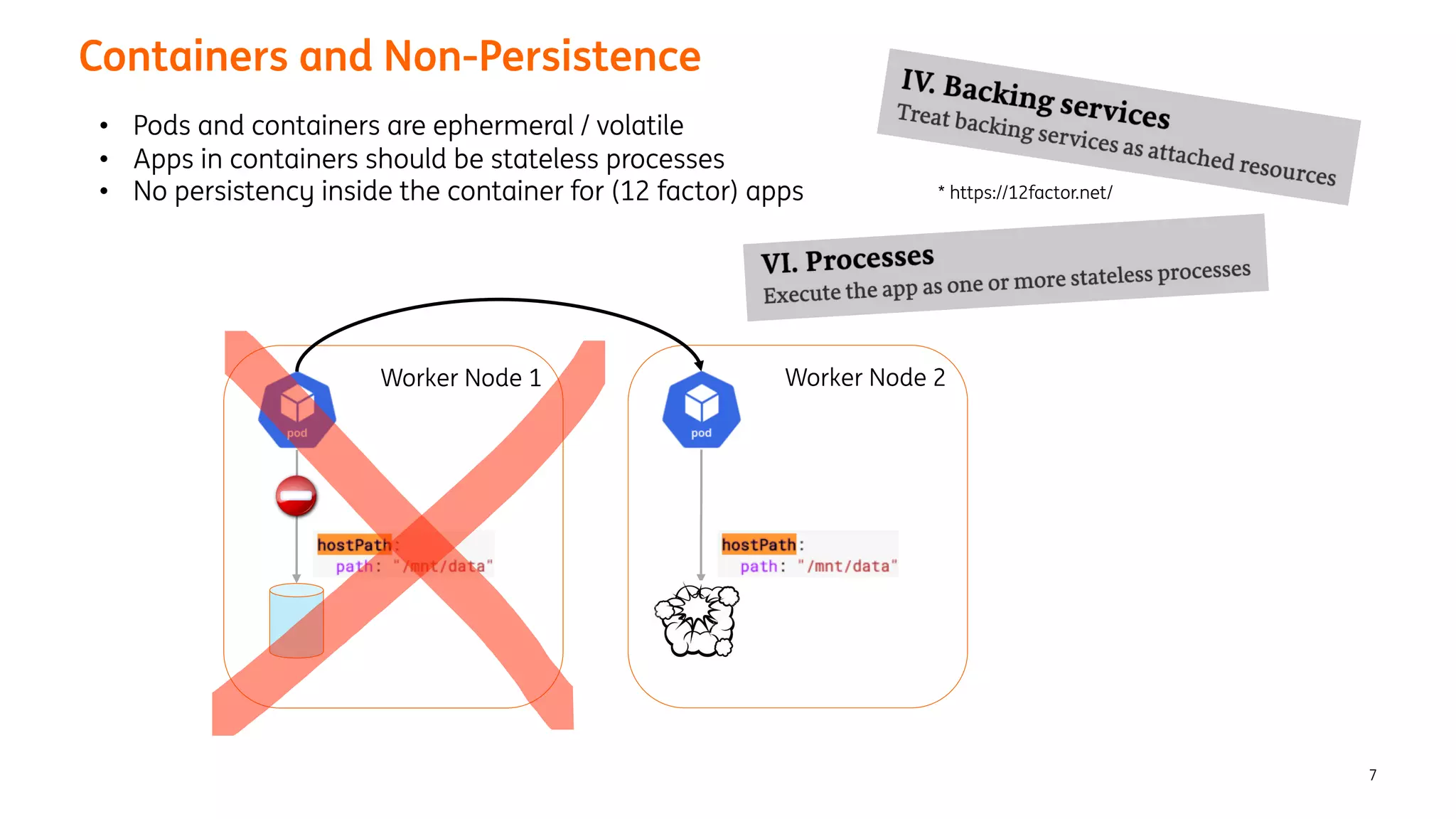
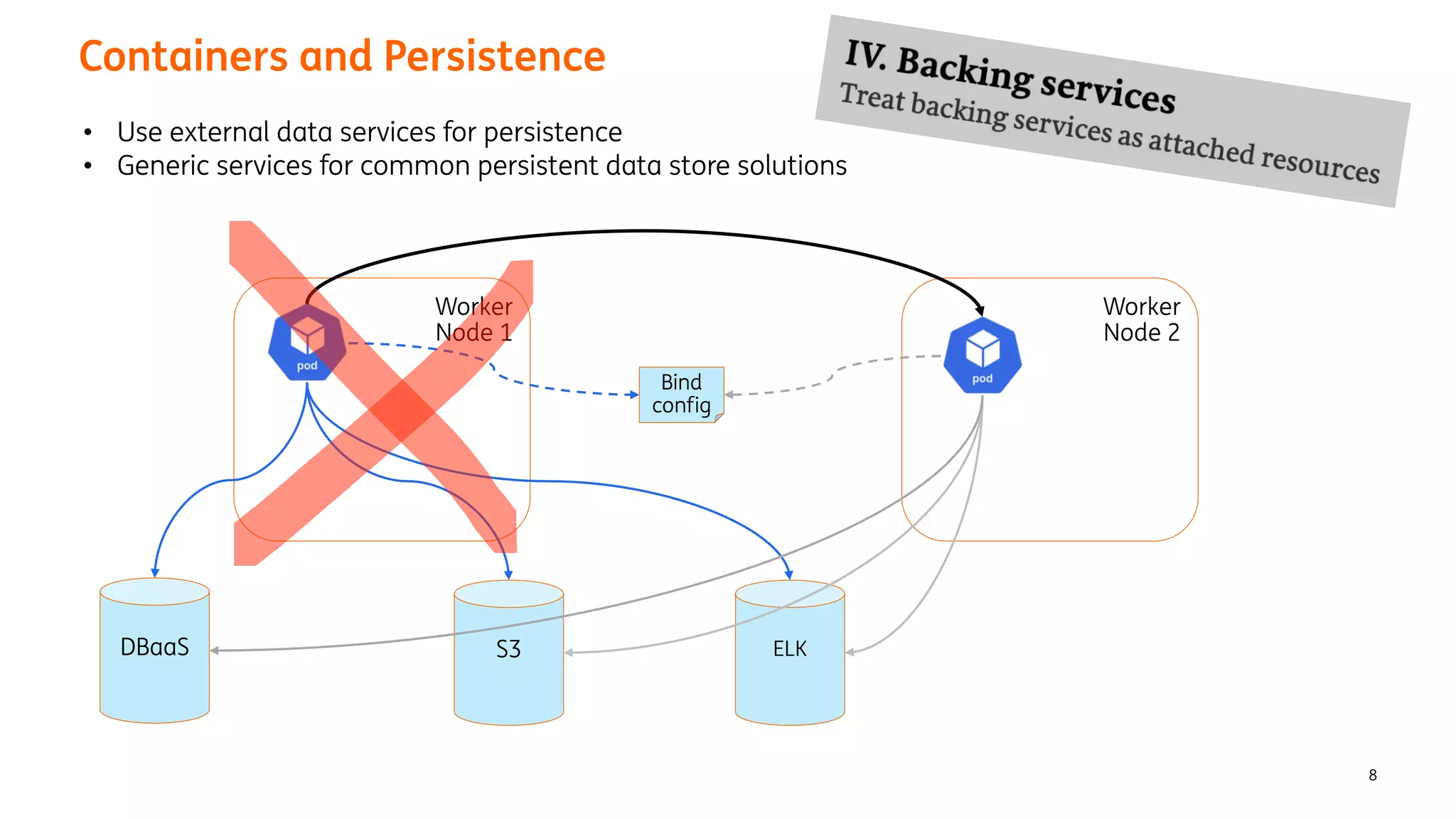
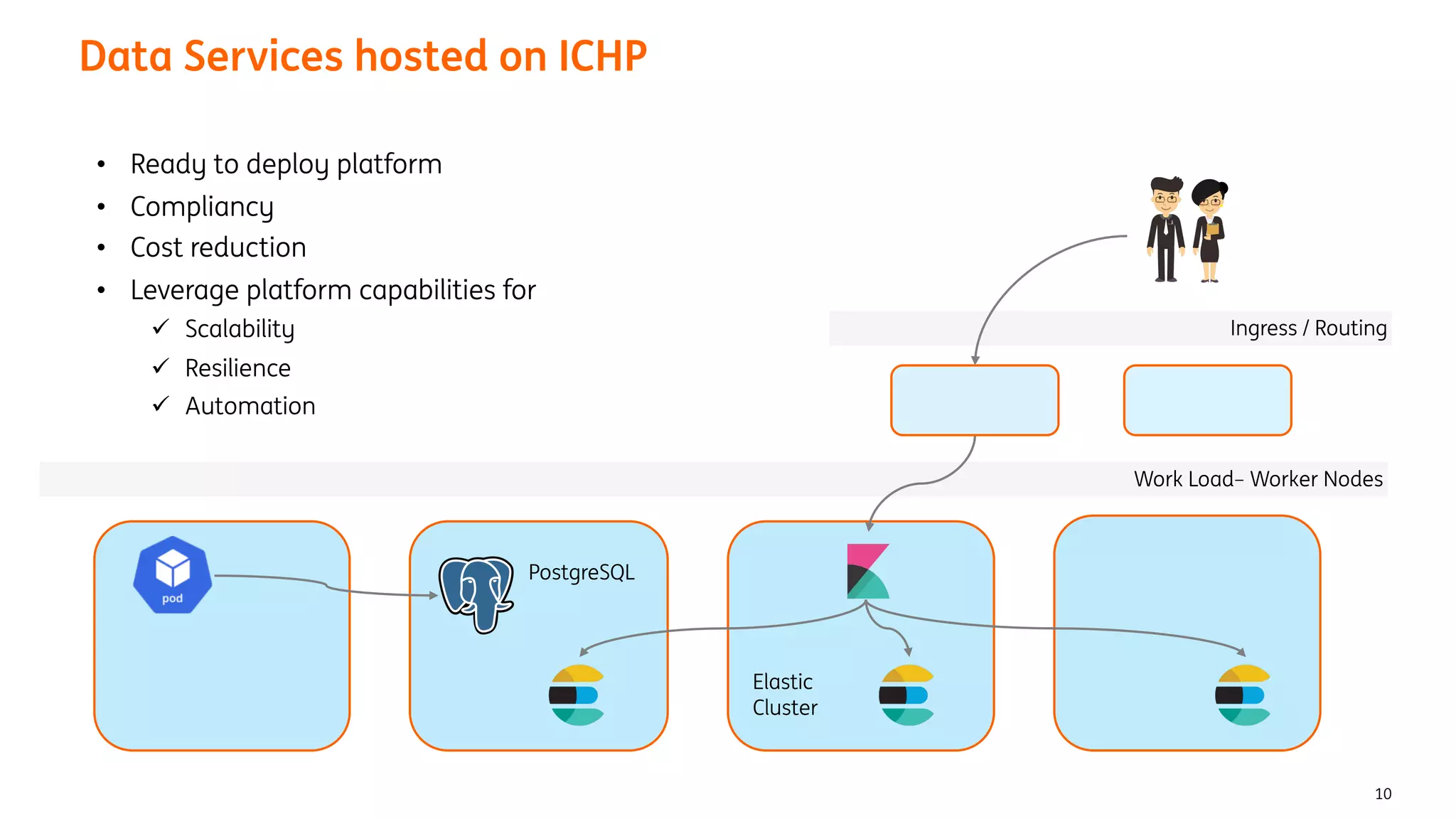
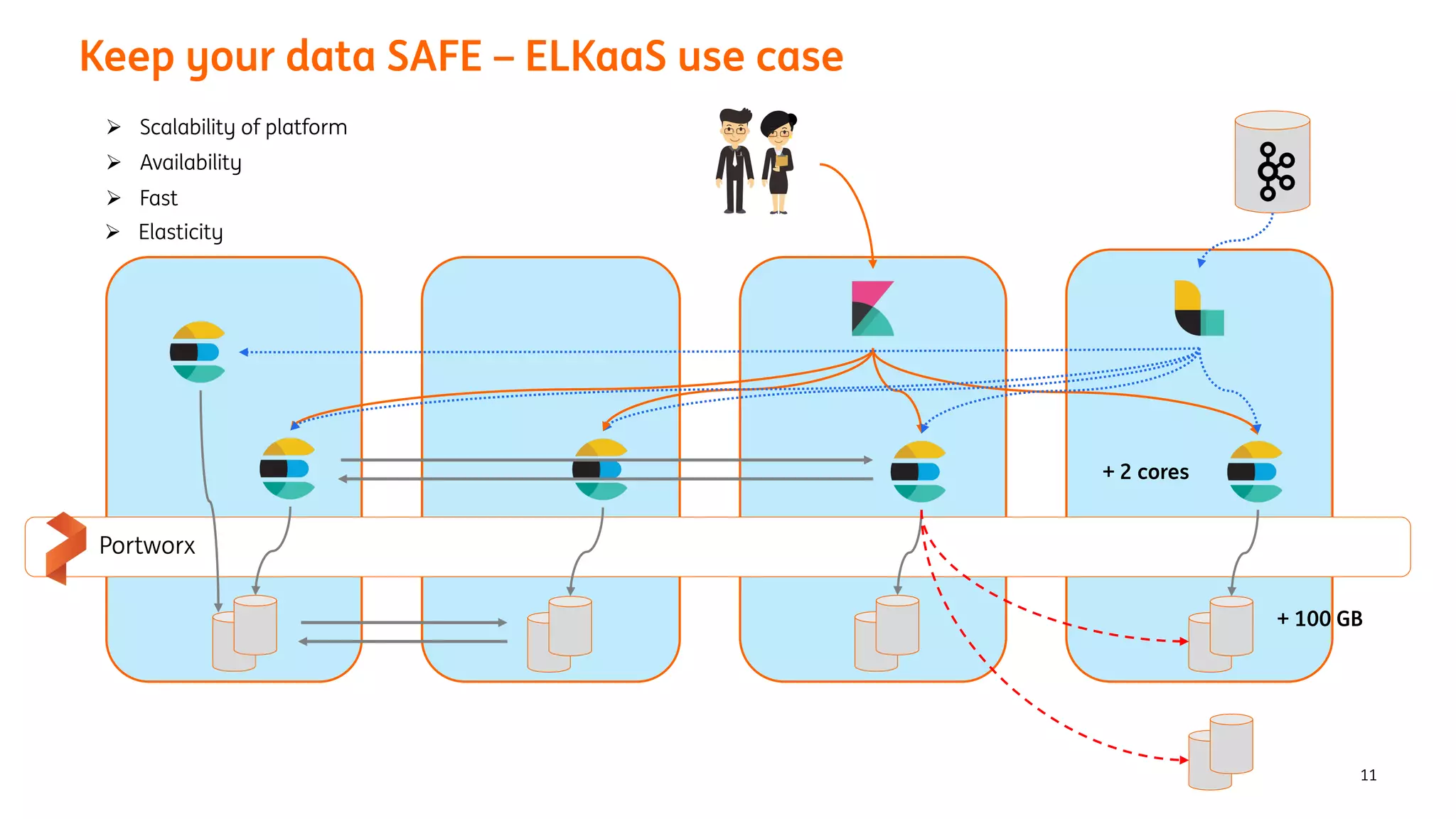
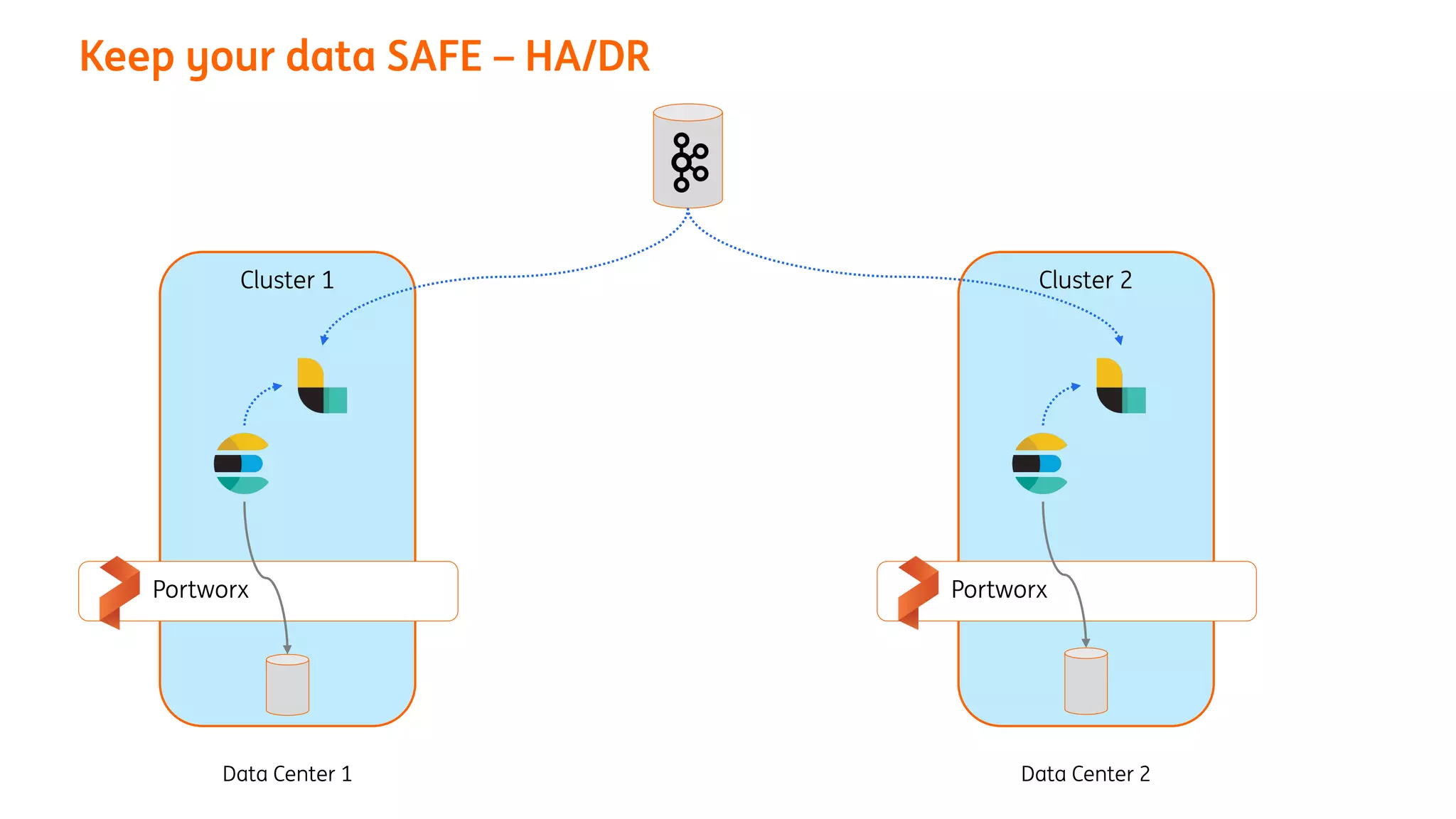
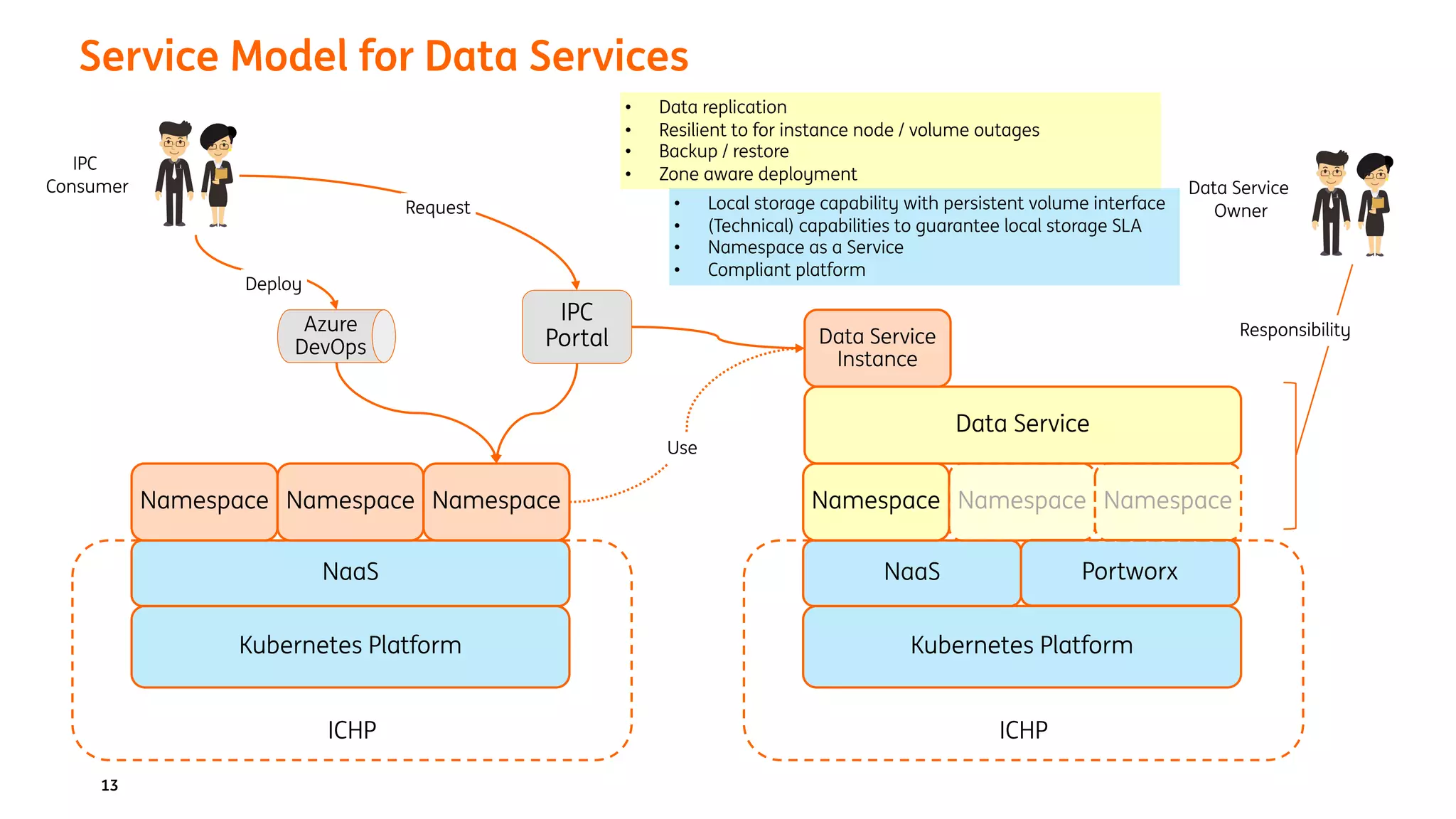
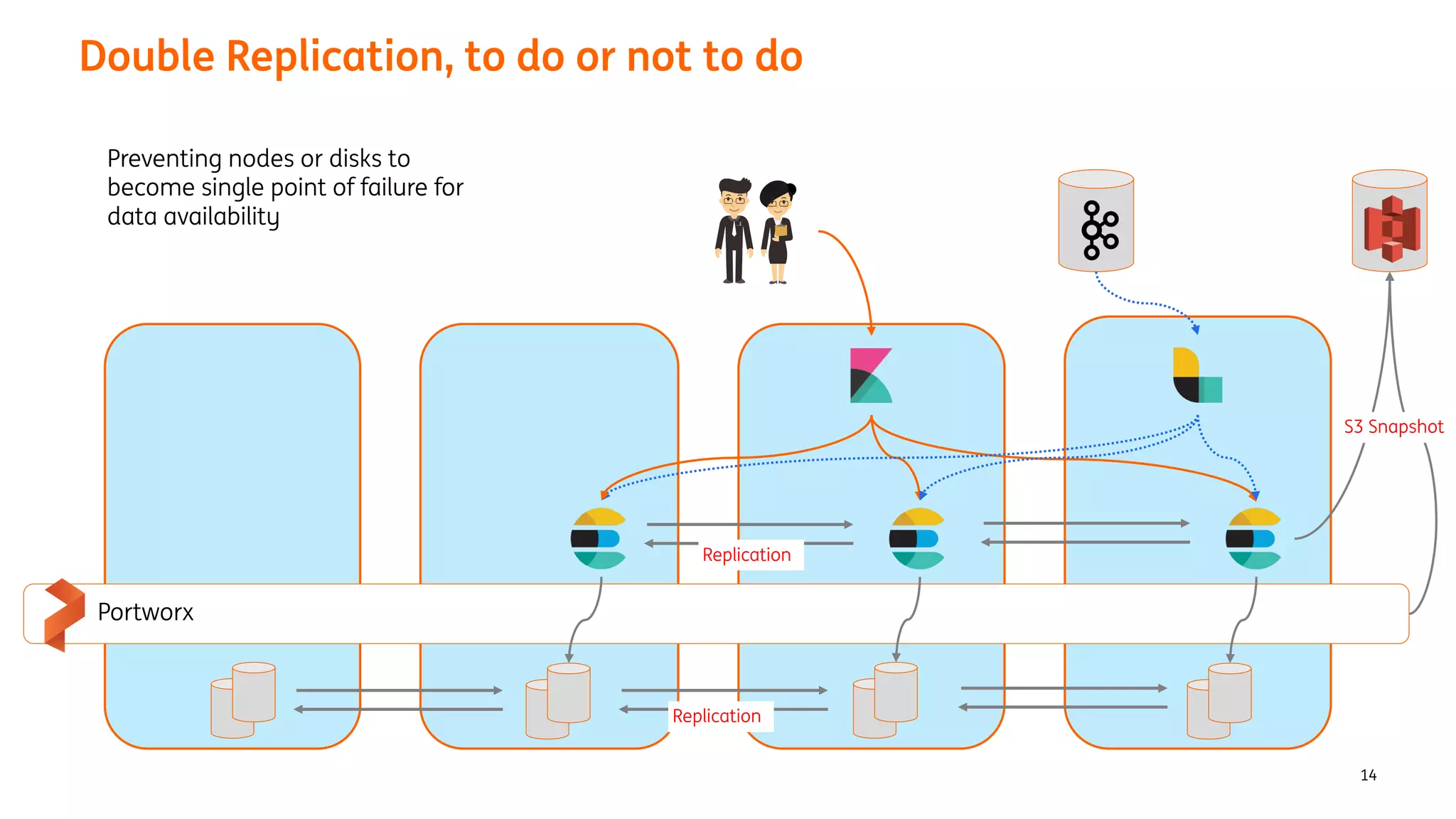
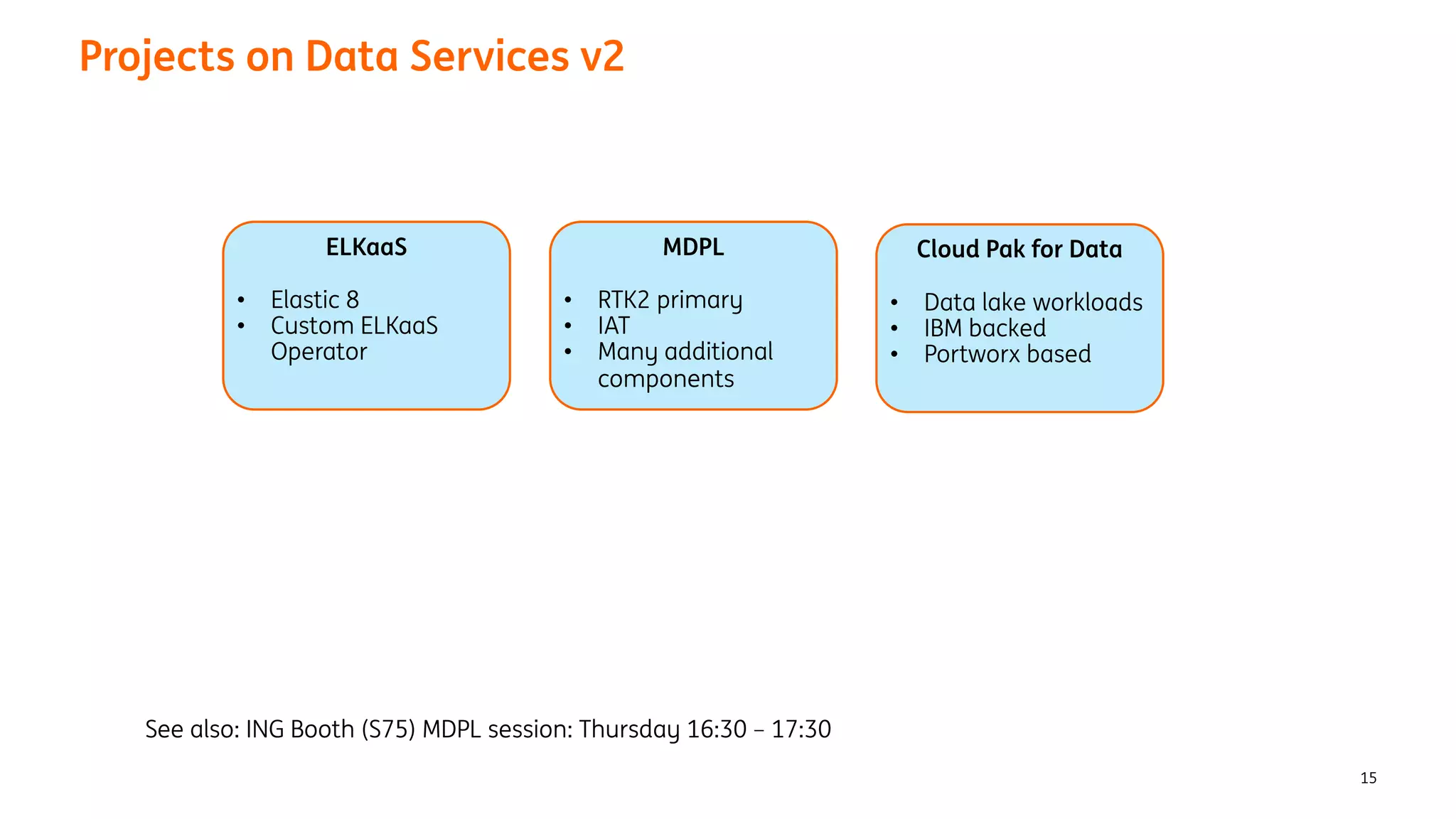
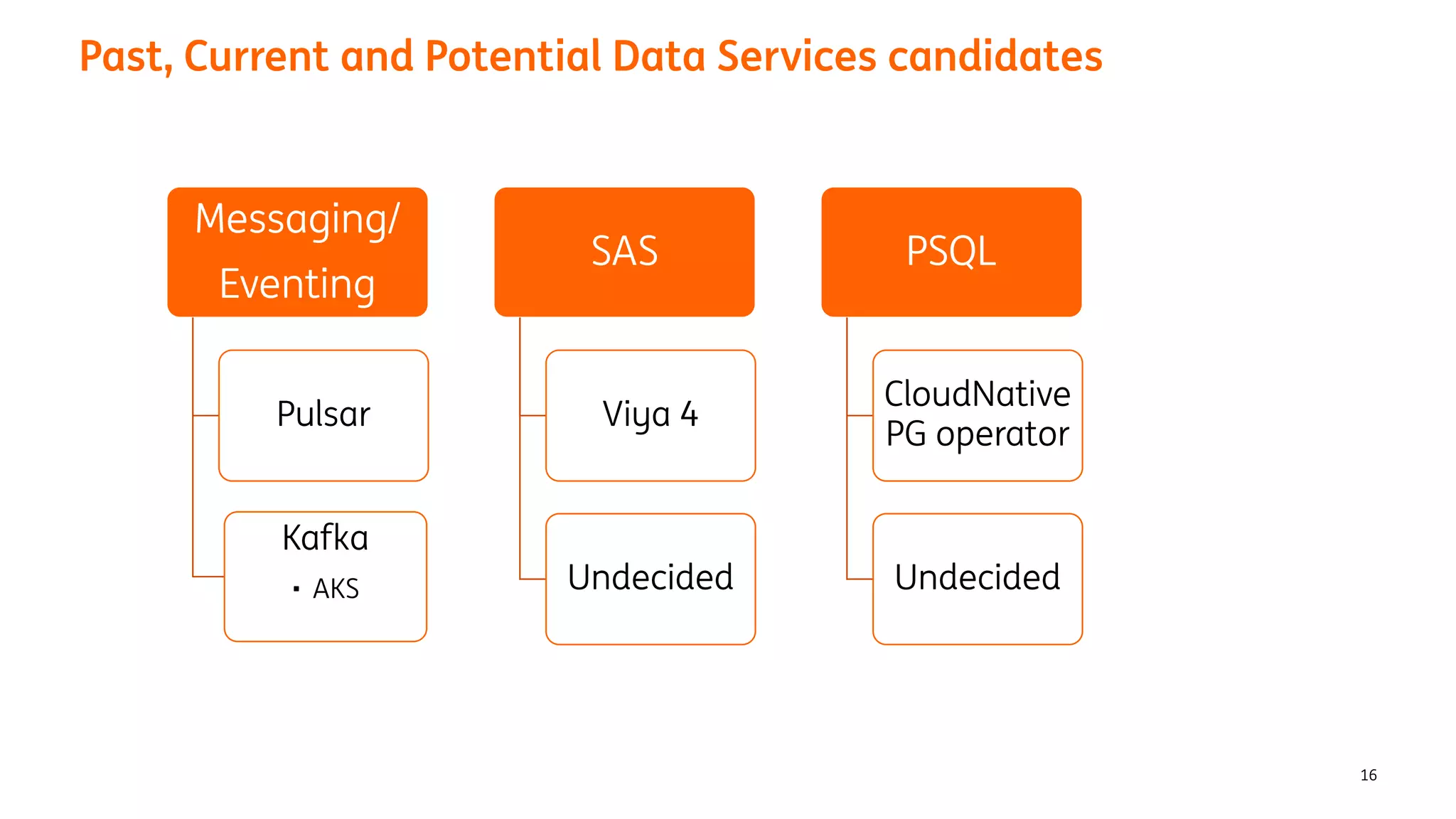
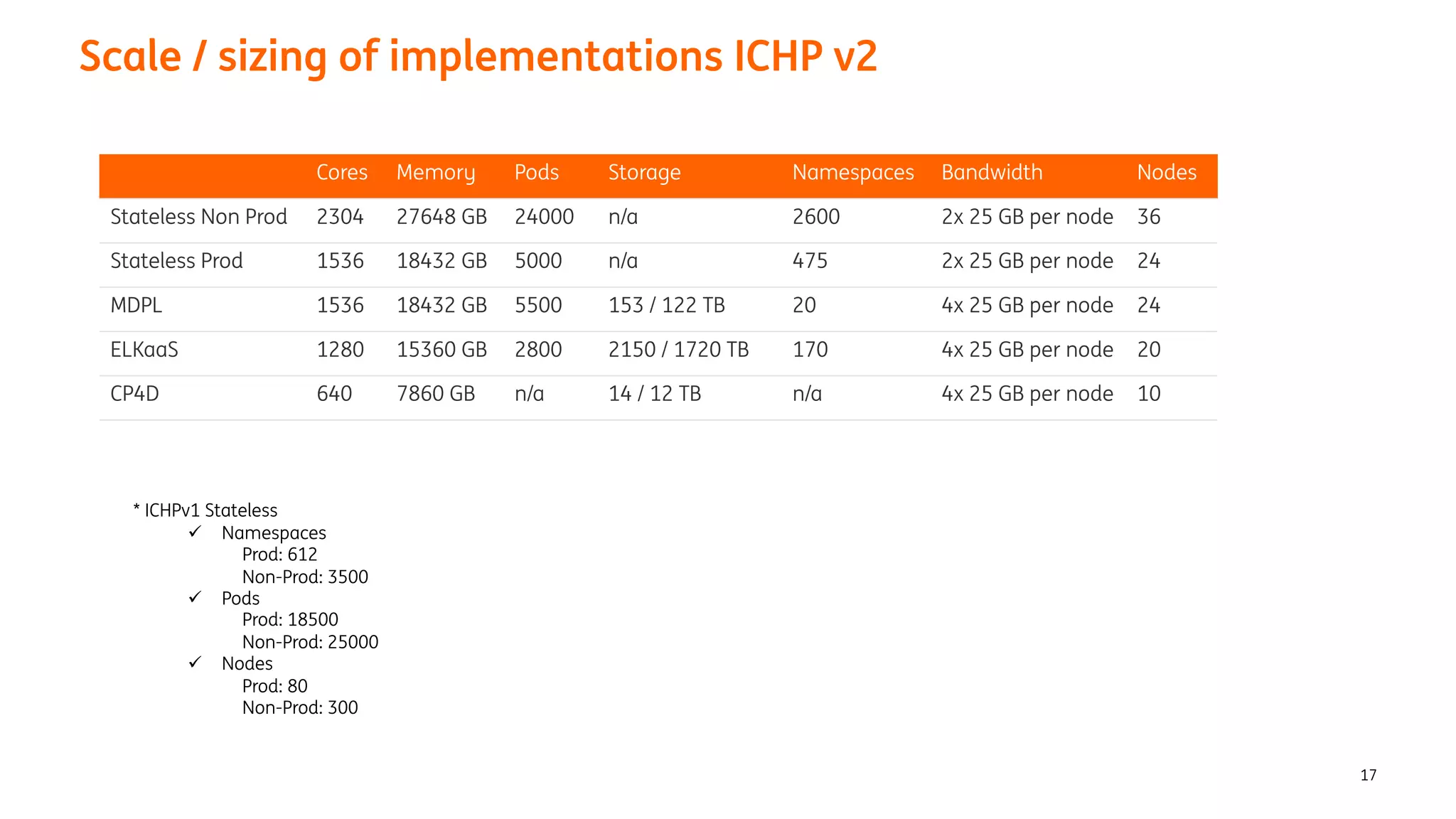
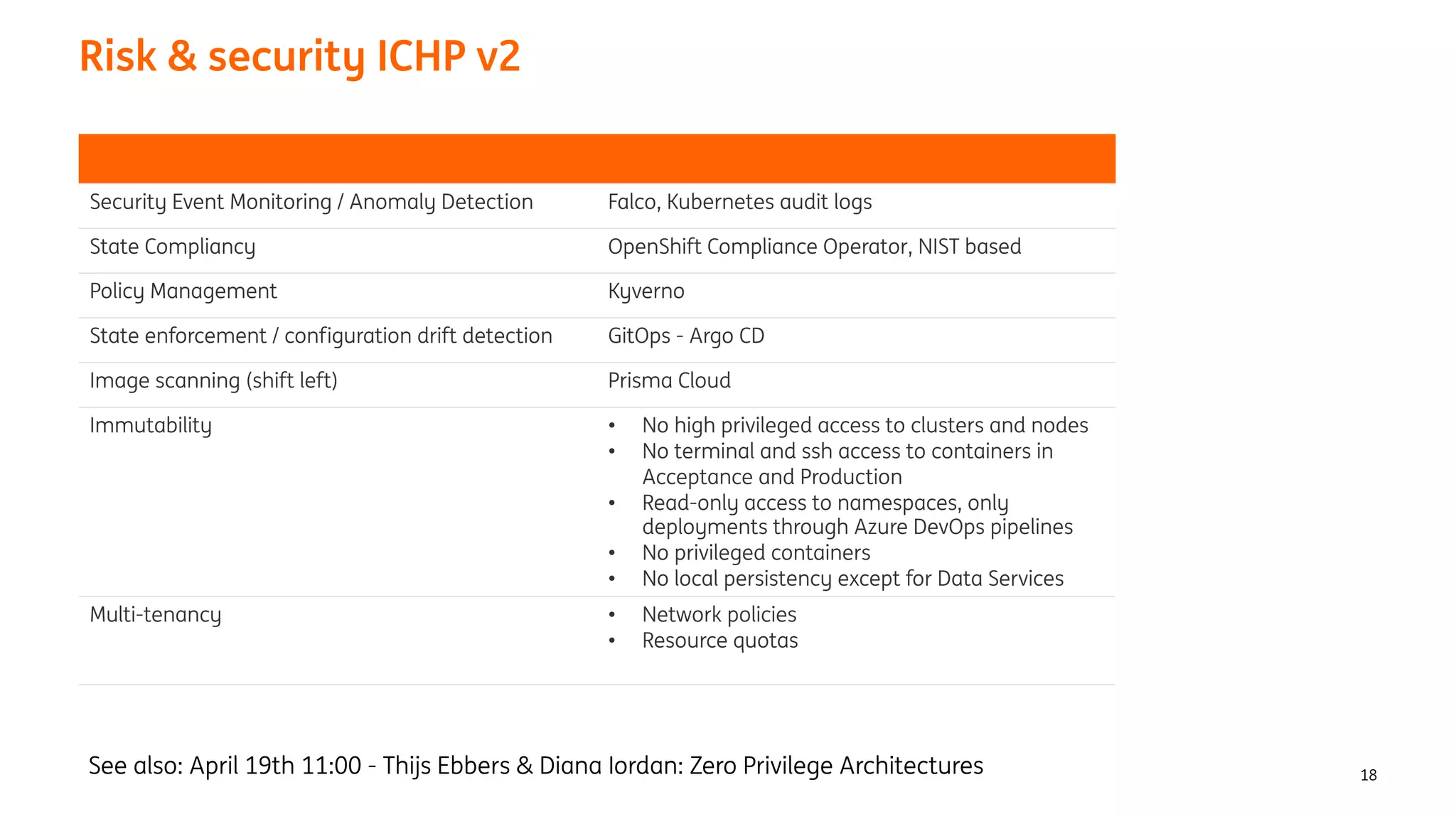
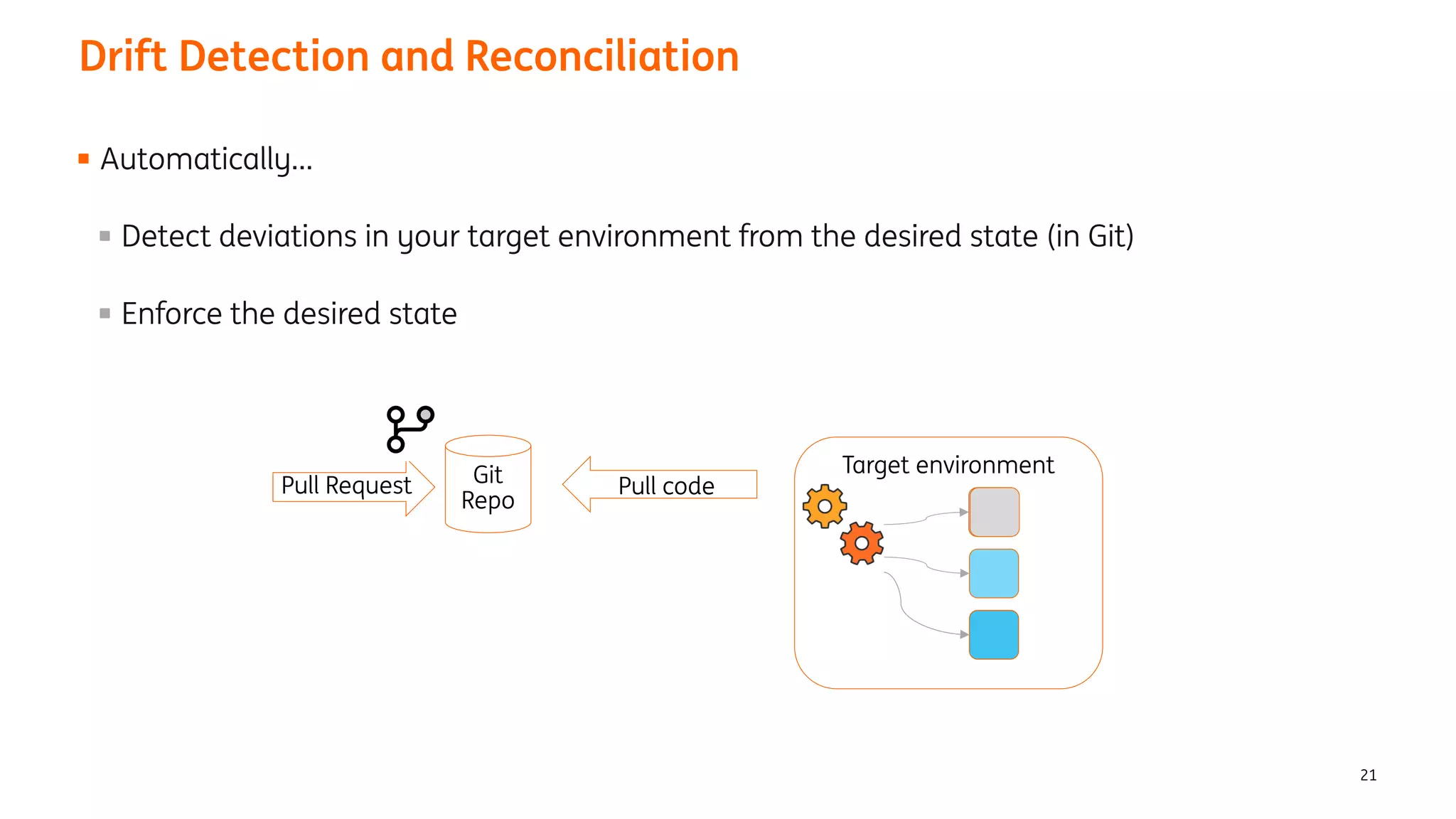
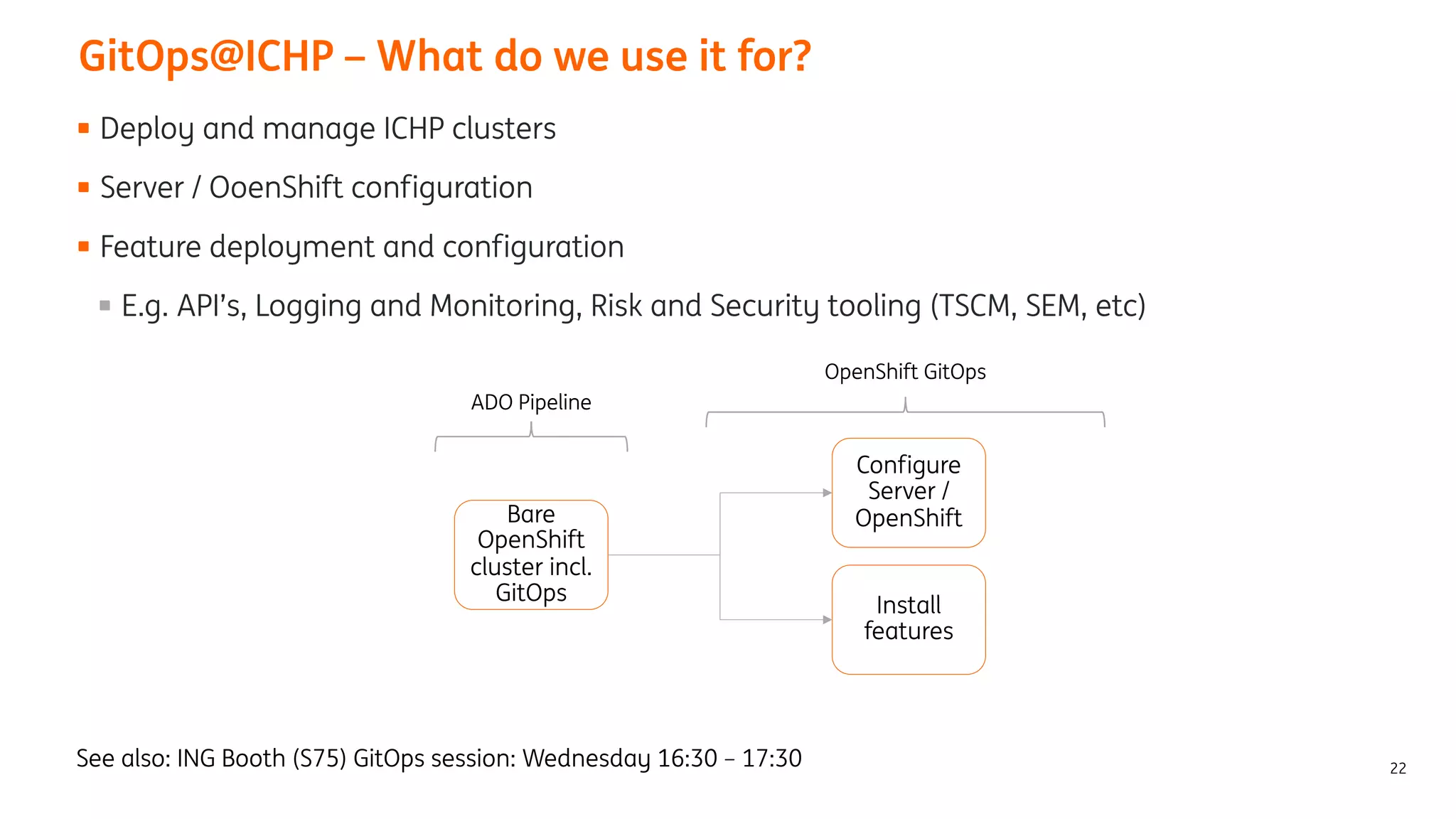
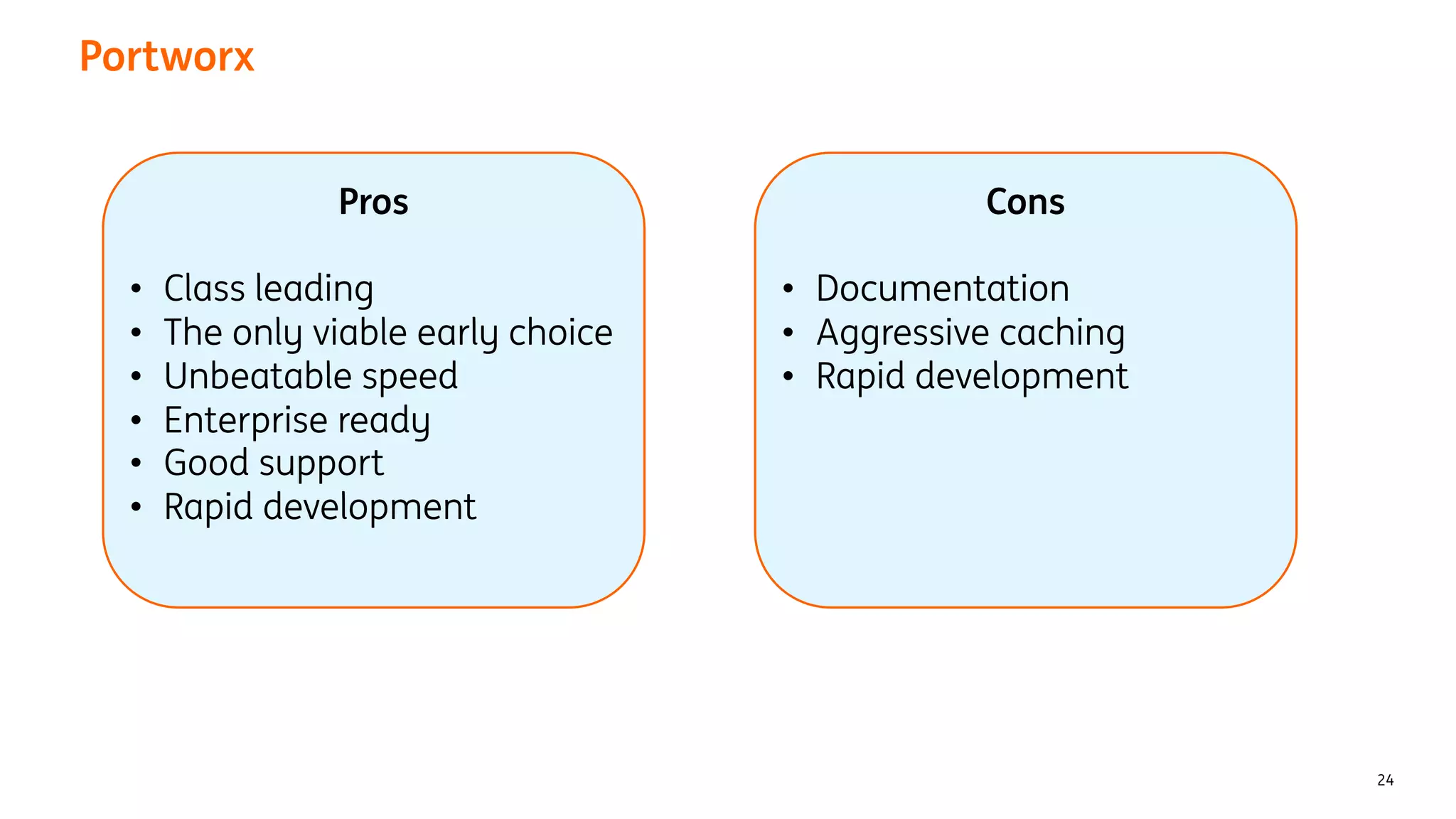
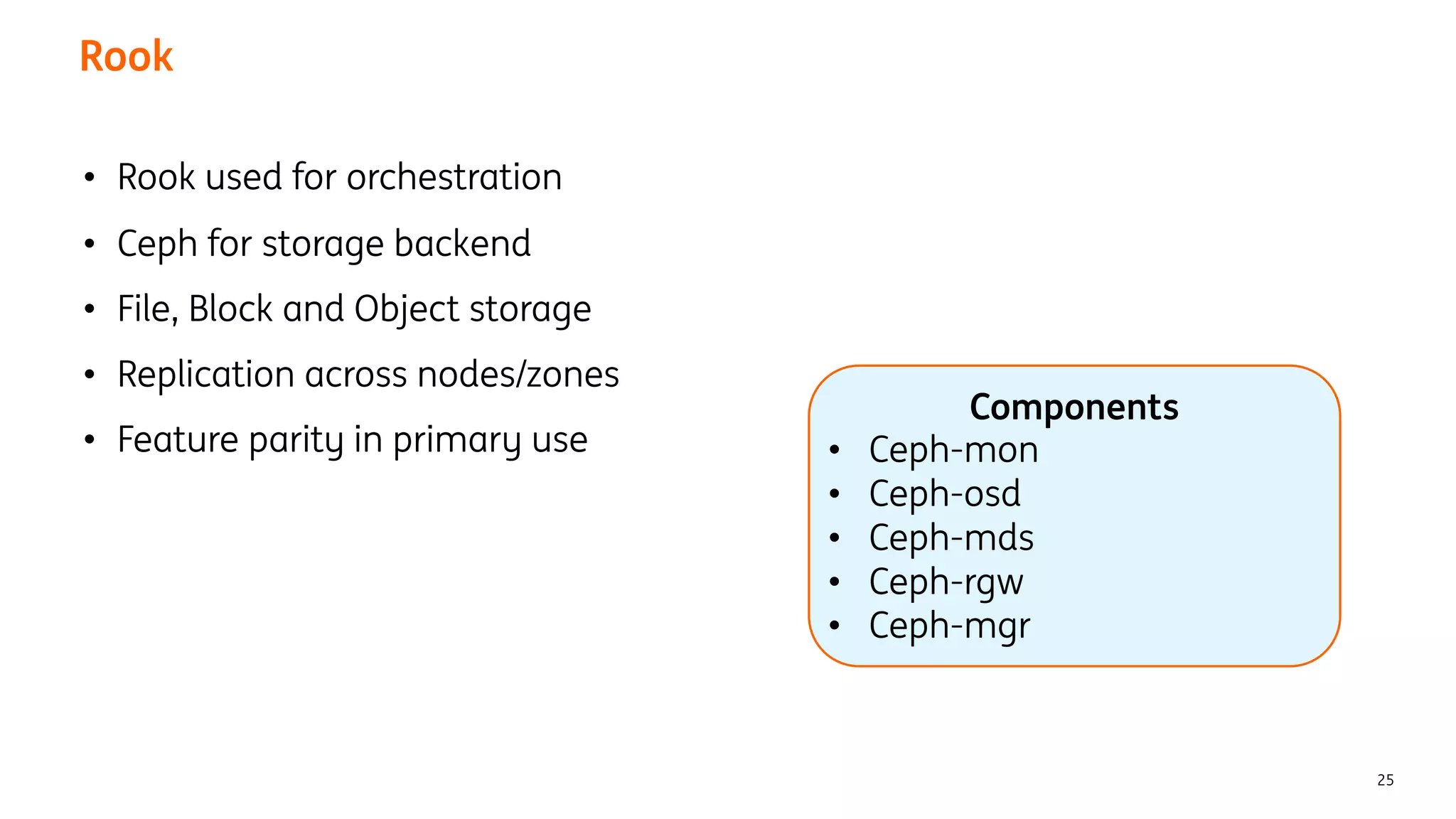
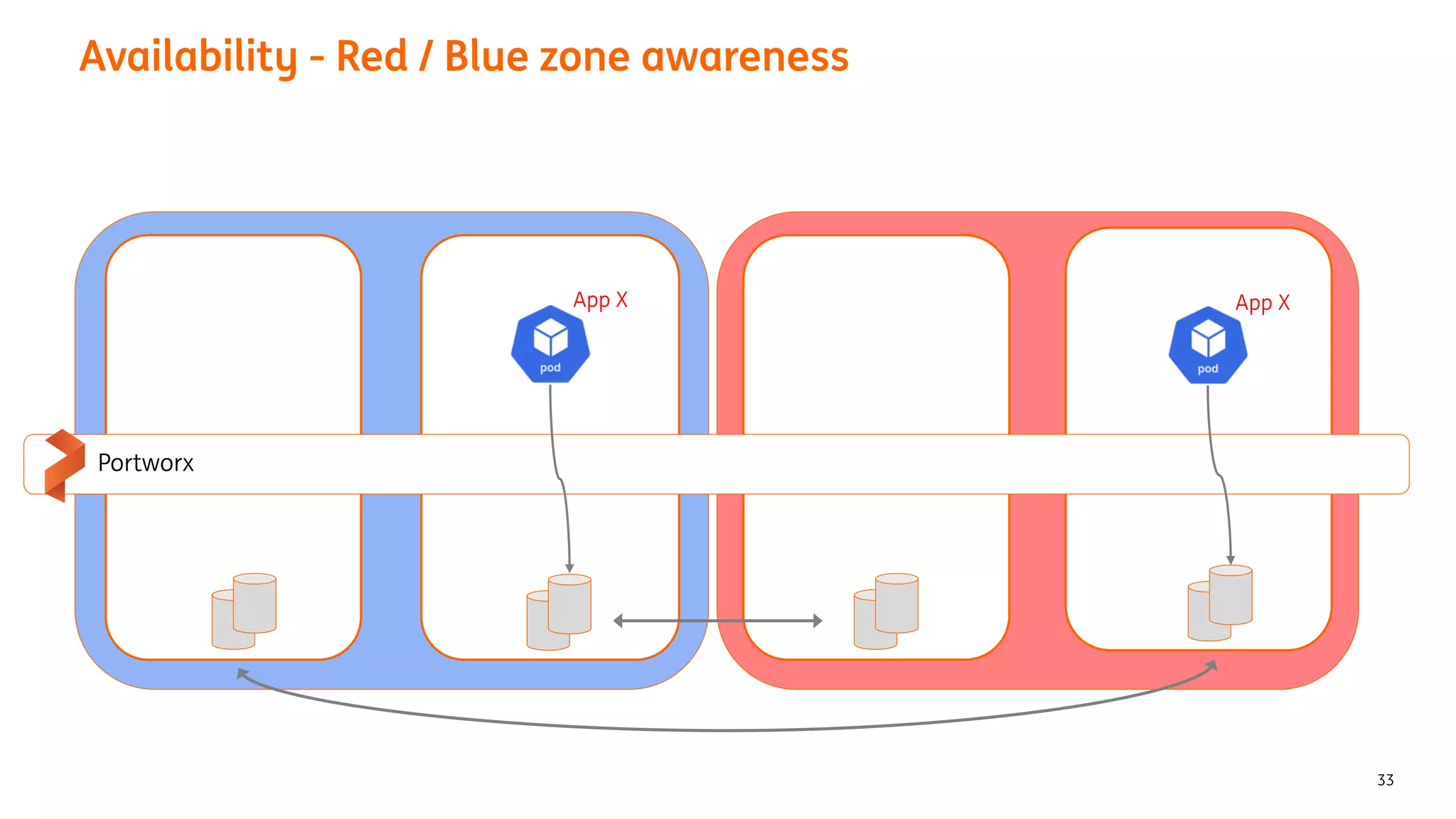
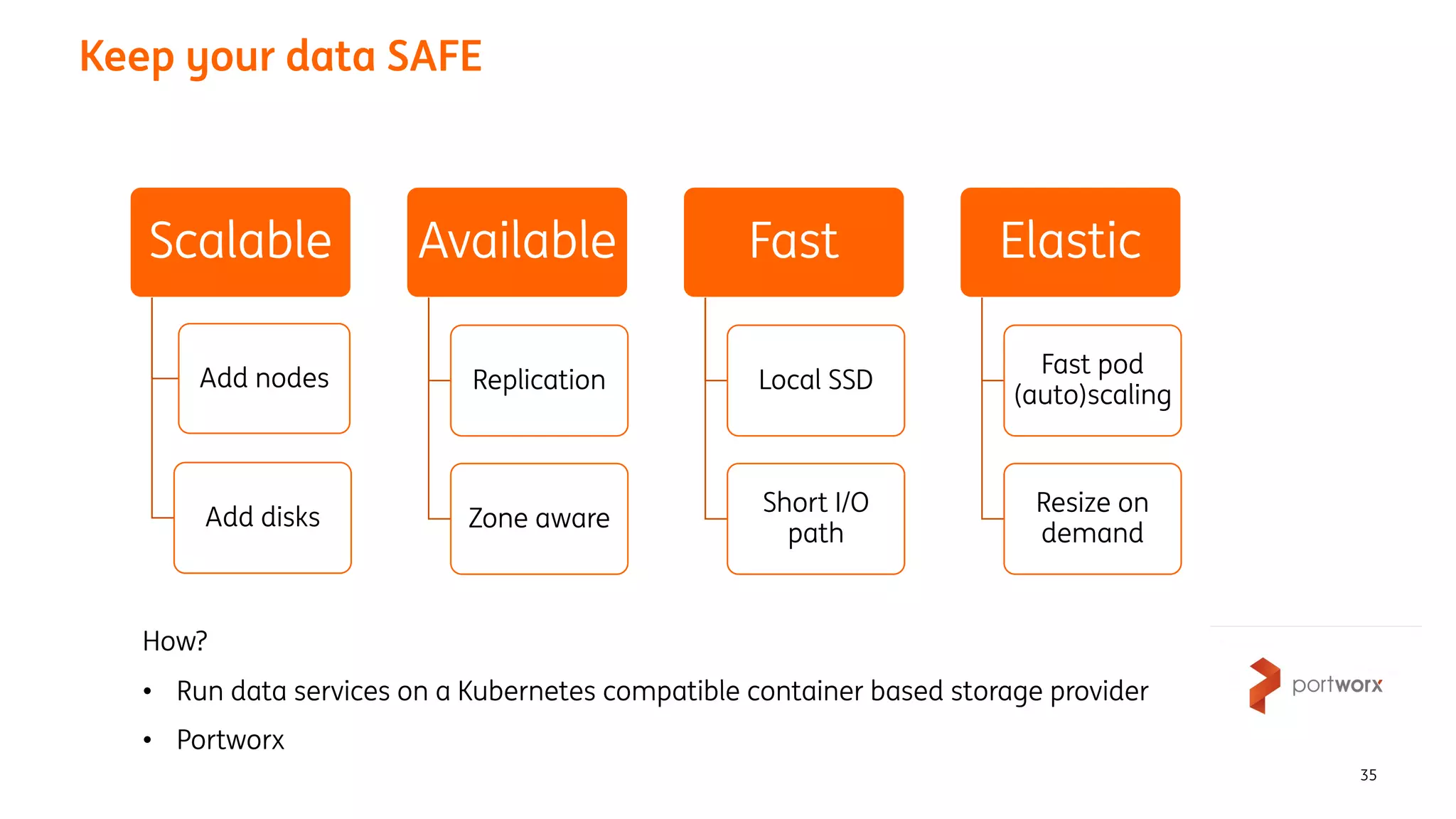
The document provides an overview of the ING Container Hosting Platform (ICHP) and its data services, emphasizing the platform's features such as scalability, compliance, and automation. It compares ICHP v1 and v2, highlighting improvements in infrastructure provision, security measures, and deployment processes. Additionally, it discusses various storage layer options and data service responsibilities to optimize persistent data management within containerized environments.