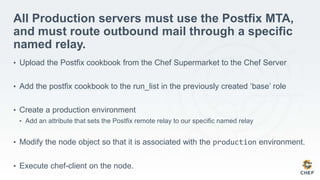
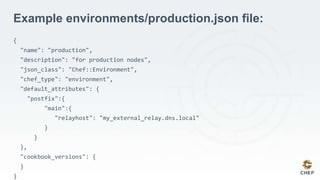
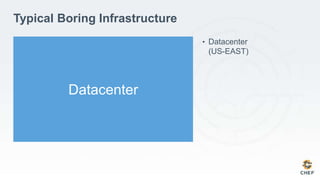
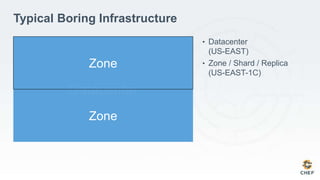
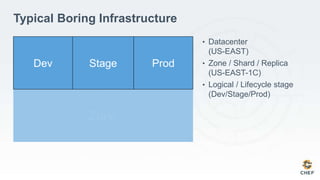
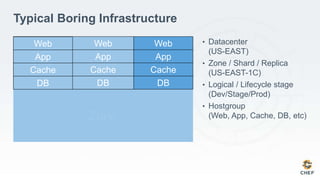
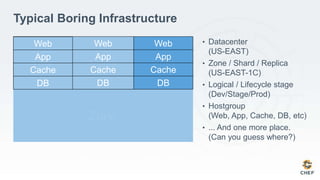
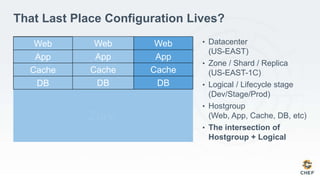
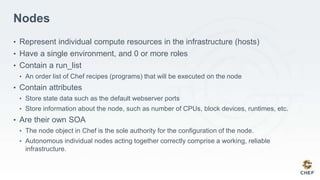
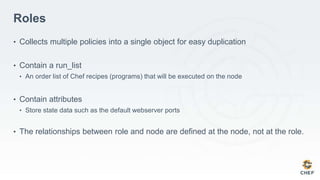
The document discusses how infrastructure configuration is typically modeled across multiple layers including datacenters, zones, logical stages, hostgroups, and their intersections. It introduces Chef as a tool that can be used to model these layers and intersections through primitives like organizations, nodes, roles, environments, data bags, and cookbooks. Examples are given of how policies like restricting SSH access and configuring a mail relay can be implemented in Chef roles and environments to enforce the policies across the infrastructure.















![All hosts must deny remote-root logins via SSH.
• Upload the OpenSSH cookbook from the Chef Supermarket to the Chef Server
• Create a “base” role that will be applied to all hosts as a default set of
configuration, regardless of environment
• Include “recipe[‘openssh::default’] in the role run_list
• Add an attribute to the role that sets the OpenSSH permitRootLogin value to ‘no’
• Modify the node object so that role[‘base’] is the first item in the run_list.
• Execute chef-client on the node.](https://image.slidesharecdn.com/infrastructuremodelingwithchef-150203165940-conversion-gate02/85/Infrastructure-modeling-with-chef-26-320.jpg)
![Example roles/base.json file:
{
"name":"base",
"description":"Default run_list for the Krustylu Studios”,
"chef_type": "role”,
"default_attributes":{
"openssh":{
"server":{
"permit_root_login": "no"
}
}
},
"run_list":[
"recipe[openssh]"
],
}](https://image.slidesharecdn.com/infrastructuremodelingwithchef-150203165940-conversion-gate02/85/Infrastructure-modeling-with-chef-27-320.jpg)