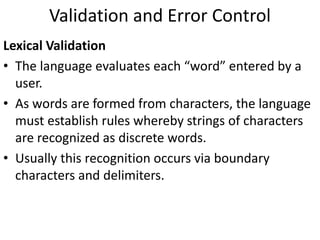
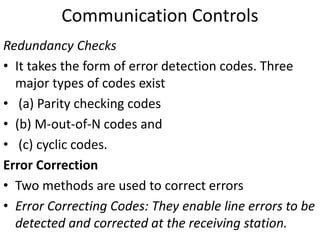
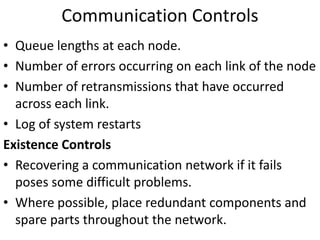
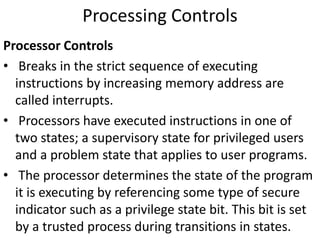
This document discusses various methods for capturing input data and instructions into a computer system, including document-based, direct entry, and hybrid capture methods. It also describes common input devices like point-of-sale terminals and ATMs, and examines controls over data codes, source document design, and ensuring quality of instruction input. Controls are needed to prevent errors and unauthorized changes to input.
![Input Controls: Data and Instruction
Input
Components in the input subsystem are responsible
for bringing information into a system. This
information takes two forms: first, it may be raw
data to be processed; second, it may be instructions
to direct the system to execute particular processes,
update or interrogate particular data, or prepare
particular types of output. This chapter examines
controls over the capture, preparation, and entry of
data and instructions into a system. Allen[1977]
studied 156 cases of computer fraud and found that
108 of the cases involved addition, deletion, or
alteration of an input transaction.](https://image.slidesharecdn.com/applicationcontrolframework-240312131533-44a0b5e5/75/Information-systems-application-control-Framework-ppt-1-2048.jpg)