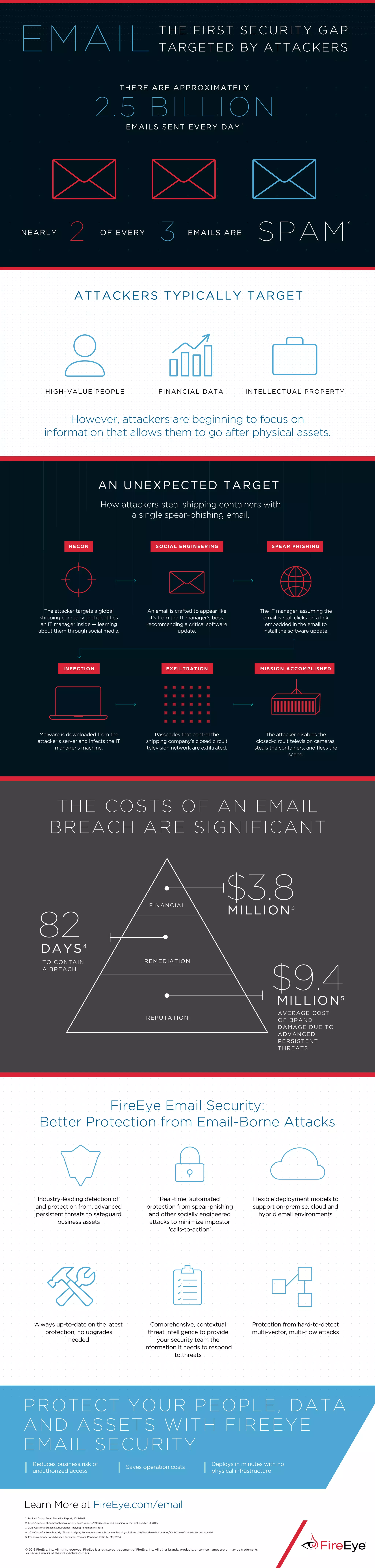
FireEye Email Security provides advanced protection against email-borne attacks, significantly reducing the risk of unauthorized access and operational costs. It features industry-leading detection of threats, real-time protection from socially engineered attacks, and flexible deployment models for various email environments without the need for upgrades. The document also includes a notable example of a spear-phishing attack that led to substantial financial damage and data loss, highlighting the critical need for effective email security solutions.