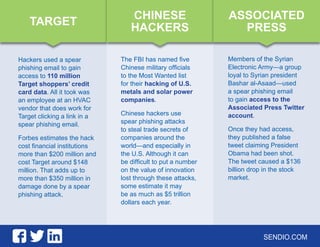
The document discusses spear phishing, an email attack that targets individuals by masquerading as trustworthy sources to gain sensitive information. It recounts a real incident involving Forbes executives, which led to a significant data breach by the Syrian Electronic Army. The text highlights the risks posed by spear phishing and promotes Sendio's email security solutions to prevent such attacks.