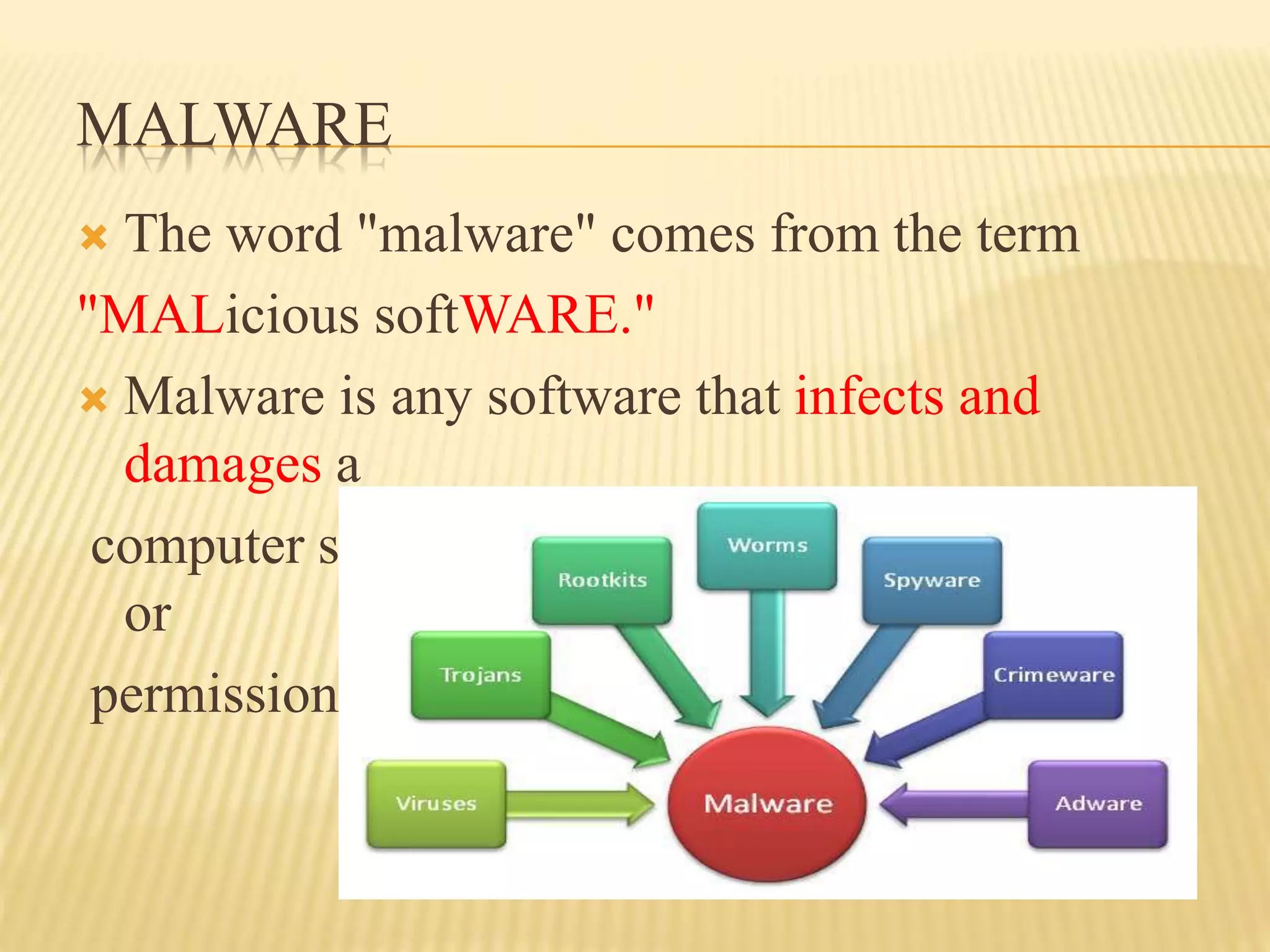
This document discusses cyber security. It defines cyber security as the technologies and processes used to protect computers, networks, and data from unauthorized access and attacks online. It notes that cyber security is important for protecting financial information, safeguarding systems from viruses, and preventing identity theft and online fraud. Some major cyber security threats include viruses, hackers, malware, and password cracking. The document also provides India's ranking in cyber security and examples of cyber attacks in 2017.