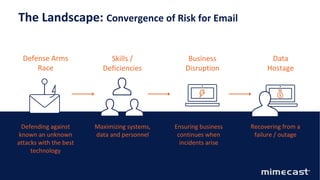
The document discusses the evolving threat landscape in cybersecurity, highlighting significant increases in phishing, spear-phishing, ransomware, and impersonation attacks, with email being the primary attack vector. It emphasizes the need for cyber resilience, integrating information security, business continuity, and data resilience to address these threats effectively. Key strategies include prevention, recovery, and education to strengthen defenses against malicious activities and enhance overall security posture.