This book introduces the 20 most critical security controls that any organization must implement to defend against modern cyber attacks. It discusses insider and outsider threats, common security standards from the US government, and how to audit controls to ensure they are effective. The document provides details on technical controls for network equipment, laptops, web servers, and more to help organizations implement the 20 critical security controls and protect their data.





























































































![94 | P a g e
Relevant Features for Full Disk Encryption Product Comparison
1. Hidden containers: Whether hidden containers (an encrypted container (A) within another
encrypted container (B) so the existence of container A cannot be established) can be
created for deniable encryption. Note that some modes of operation like CBC with a plain
IV can be more prone to watermarking attacks than others.
2. Pre-boot authentication: Whether authentication can be required before booting the
computer, thus allowing one to encrypt the boot disk.
3. Custom authentication: Whether custom authentication mechanisms can be implemented
with third-party applications.[clarification needed]
4. Multiple keys: Whether an encrypted volume can have more than one active key.
5. Passphrase strengthening: Whether key strengthening is used with plain text passwords to
frustrate dictionary attacks, usually using PBKDF2.
6. Hardware acceleration: Whether dedicated cryptographic accelerator expansion cards can
be taken advantage of.
7. Trusted Platform Module: Whether the implementation can use a TPM cryptoprocessor.
8. Filesystems: what Filesystems are supported?
9. Two-factor authentication: Whether optional security tokens (hardware security modules,
such as Aladdin eToken and smart cards) are supported (for example using PKCS#11)
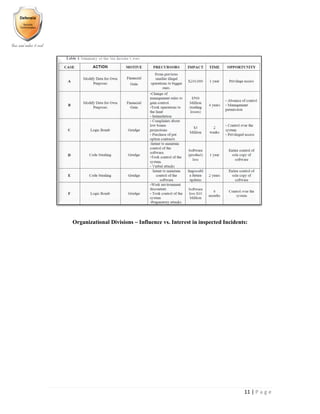
Product Feature Comparison Table
Name
Hidden
container
s
Pre-boot
authenticatio
n
Custom
authenticatio
n
Multipl
e keys
Passphrase
strengthenin
g
Hardware
acceleratio
n
TP
M
Filesystems
Two-factor
authenticatio
n
BestCrypt OS
Bloombase ? ?
Check Point FDE ? ? ? ?
FileVault 2 HFS+
PGPDisk ? ? ?
McAfee
Endpoint
OS
SafeGuard Ent. OS
SecureDoc ?
Symantec Endpoi
nt
NTFS,FAT3
2
TrueCrypt
only on
Windows
OS ](https://image.slidesharecdn.com/implementingandauditingsecuritycontrols-part1-170328160745/85/Implementing-and-auditing-security-controls-part-1-95-320.jpg)


































































![163 | P a g e
o Hostname(config-if)# switchport private-vlan mapping 101 201-202,301
Use the show interface private-vlan mapping command and the show interface [interface-id]
switchport command to verify the configuration.
Upgrading Router/Switch Firmware
Write Unsaved configurations
ciscorouter# write memory
Building configuration…
[OK]
Check space on Flash Memory
ciscorouter# show flash
Backup Startup Configuration
Setup a TFTP server in the same IP range as the Cisco device to back up the config, IOS image and also for
later to upload the new IOS image.
ciscorouter# copy startup-config tftp
Address or name of remote host []? 192.168.1.50
Destination filename [startup-config]?](https://image.slidesharecdn.com/implementingandauditingsecuritycontrols-part1-170328160745/85/Implementing-and-auditing-security-controls-part-1-164-320.jpg)
![164 | P a g e
!!
1278 bytes c opied in 0.100 secs
Backup Current IOS Image
ciscorouter# copy flash: tftp:
Source filename []? xxxxx-xx-xx.121-x.XB
Address or name of remote host []? 192.168.1.150
Destination filename [xxxxx-xx-xx.121-x.XB]?
Now, we are all set. Load the new IOS image from the TFTP onto the flash
ciscorouter# copy tftp: flash:
Address or name of remote host []? 192.168.1.150
Source filename []? xxxxx-xx-xx.121-x.XB
Destination filename [xxxxx-xx-xx.121-x.XB]?
%Warning:There is a file already existing with this name
Do you want to over write? [confirm]
Accessing tftp://192.168.1.150/xxxxx-xx-xx.121-x.XB…
Erase flash: before copying? [confirm]
Erasing the flash filesystem will remove all files! Continue? [confirm]
Erasing device… eeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeee
ee …erased
Erase of flash: complete
Loading xxxxx-xx-xx.121-x.XB from 192.168.1.150 (via Ethernet0): !!!!!!!!!!!!!!!!!!!!
…..
….
…
..
[OK - 3802992/7605248 bytes]
Verifying checksum… OK (0x1ABC)
3802992 bytes copied in 68.236 secs (65568 bytes/sec)
This may error if there isn't enough memory in which case, you need to delete the existing image and copy
the newer image onto the router or switch.
On a Cisco Catalyst 3560
ciscorouter# delete /force /recurssive flash:/c3560-ipbase-mz.122-35.SE5
ciscorouter#sh flash:
Directory of flash:/
3 -rwx 1216 Mar 1 1993 00:10:27 +00:00 config.text
4 -rwx 5 Mar 1 1993 00:10:27 +00:00 private-config.text
15998976 bytes total (15995904 bytes free)
That deletes the existing image and the show command just show that.
Now copy the newer image onto the flash](https://image.slidesharecdn.com/implementingandauditingsecuritycontrols-part1-170328160745/85/Implementing-and-auditing-security-controls-part-1-165-320.jpg)
![165 | P a g e
ciscorouter#copy tftp: flash:
Address or name of remote host []? 10.10.10.2
Source filename []? c3560-ipbasek9-mz.122-40.SE.bin
Destination filename [c3560-ipbasek9-mz.122-40.SE.bin]?
Accessing tftp://10.10.10.2/c3560-ipbasek9-mz.122-40.SE.bin…
Loading c3560-ipbasek9-mz.122-40.SE.bin from 10.10.10.2 (via Vlan1):
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!
[OK - 8295106 bytes]
8295106 bytes copied in 124.571 secs (66589 bytes/sec)
Check if the version is upgraded
ciscorouter# sh flash
Update the system config to boot with new image.
ciscorouter(config)#boot system flash:/c3560-ipbasek9-mz.122-40.SE.bin
If it looks ok. Reload the Cisco Router
ciscorouter# reload
When is back online check if the cisco device has booted with the new Cisco IOS image.
ciscorouter# sh ver
Buying new equipment, new security features
The main reasons to buy new network equipment such as switches and routers are:
1. Today’s network equipment is faster, better, more secure by default, supports latest
security and networking technologies and provides better services.
2. Most of the security features previously discussed is mostly supported on switches from
2007 forward. (BDPU Guard, IP Source Guard, DHCP Snooping, Dynamic ARP
Inspection)
3. The current switches provide better remote management features that are required by
third party security controls such as NAC (Network Access Control) and SIEM (Security
Information Event Management)
4. Latest routers also support SECURE MANAGEMENT with SNMP v3, encrypted
connection requiring username and password to manage the network.](https://image.slidesharecdn.com/implementingandauditingsecuritycontrols-part1-170328160745/85/Implementing-and-auditing-security-controls-part-1-166-320.jpg)






