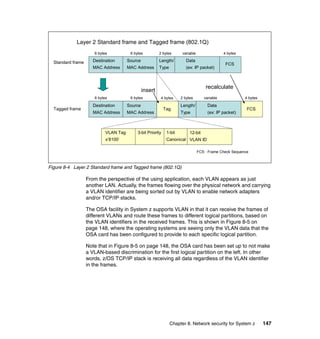
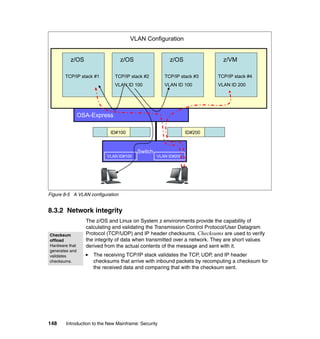
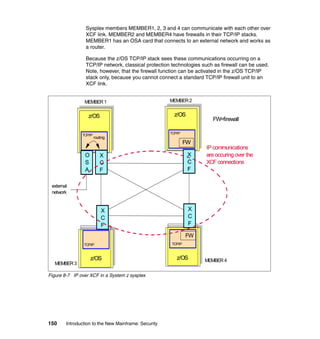
This document provides an introduction to security on mainframe systems. It discusses fundamental security concepts like confidentiality, integrity and availability. It also covers security elements such as identification, authentication, authorization, encryption and auditing. Additionally, it examines the System z architecture and how the hardware and operating system provide security features. The document uses a case study about securing an online bookstore to illustrate how these concepts apply in a business context. It is intended to help readers understand mainframe security.





























































































































































































![202 Introduction to the New Mainframe: Security
POSIX.1 Definitions identified by Part 1: System Application
Program Interface (API) [C Language] (P1003.1)
POSIX.2 Definitions identified by Part 2: Shells and Utilities
(P1003.2)
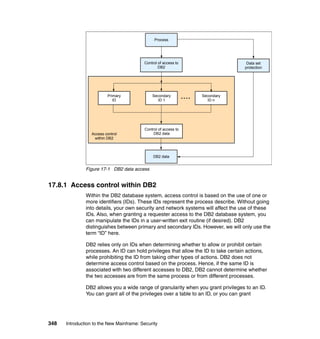
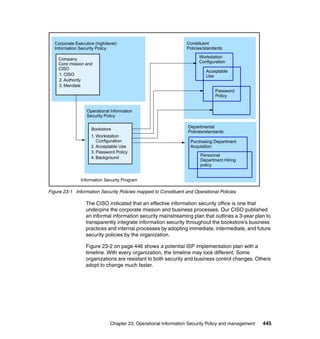
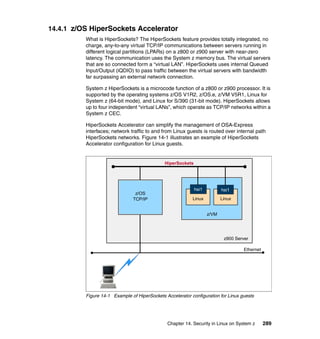
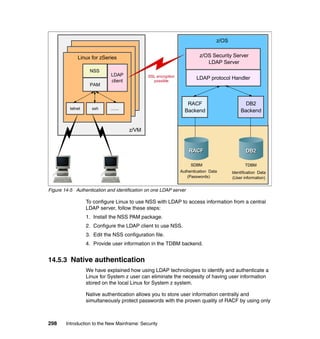
11.3 Roles and responsibilities
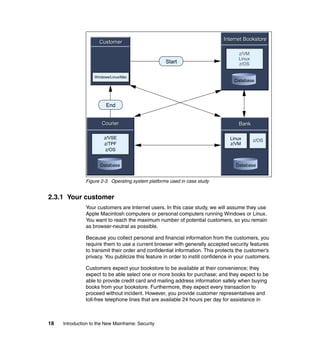
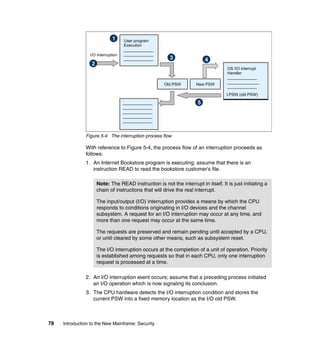
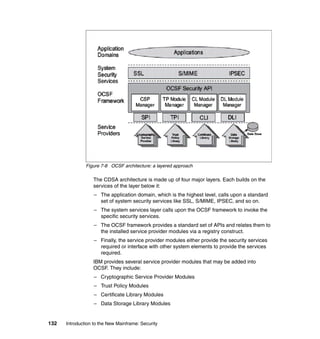
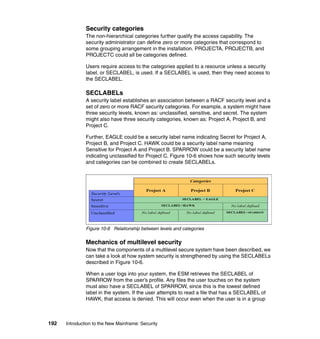
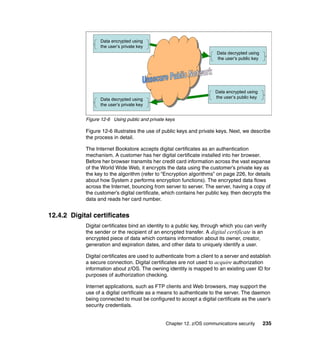
As previously discussed, and as shown in Figure 11-2, there are typical roles for
mainframe support and the concept of separation of duties, as described in 4.4,
“Roles and separation of duties” on page 51.
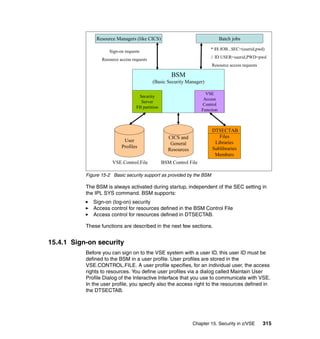
Figure 11-2 Typical mainframe roles
Here we provide brief descriptions of the typical roles and responsibilities for a
mainframe support organization as related to z/OS UNIX.
Application developer
An application developer designs, builds, tests, and delivers mainframe
applications to a company’s end users and customers. Application developers
use the development tools and utilities that are installed on the mainframe to
perform their job responsibilities.](https://image.slidesharecdn.com/sg246776-150502075816-conversion-gate02/85/Sg246776-224-320.jpg)







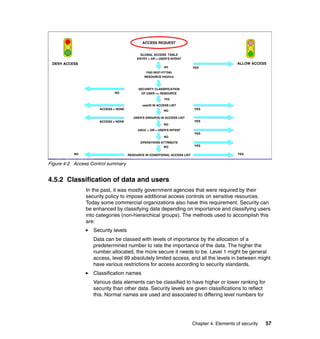
![Chapter 11. Security in z/OS UNIX 211
Obviously, there is not much granularity available to the system administrator
when restricting or granting access to files and directories using UNIX
permissions. To address this problem, ACLs were invented.
The ACL is used to set up a default permission list for directories and files, much
like the original UNIX permissions settings. The benefit, however, is that
individual users or groups of users can then be placed into the ACL, either
restricting or granting privileges as required, to individual users or groups of
users.
This allows much finer control over the list of users and groups of users that have
permissions over the file or directory entry. The use of ACLs removes the
restriction that a single user or single group is allowed to have privileges to a file
or directory. With ACLs, you simply set the default permissions the way you want
and then build the access list with as many users or groups as necessary to meet
your security needs.
The ACL is administered with the setfacl command. Using the setfacl
command, you may:
Set (replace) the entire ACL
Delete (remove) the entire ACL
Add, delete, or modify existing entries within the ACL
The extended ACL entries have the following format:
[d[efault]: | f[default]:]u[ser]:uid:[+|^]perm
[d[efault]: | f[default]:]g[roup]:gid:[+|^]perm
where:
d[efault] If specified, then this extended ACL refers to the directory default
ACL.
f[default] If specified, then this extended ACL refers to the file default ACL.
u[ser] This extended ACL refers to a particular numeric user ID (UID) or
user name.
g[roup] This extended ACL refers to a particular numeric group ID (GID) or
group name.
uid User name or numeric user ID (UID).
gid Group name or numeric group ID (GID).
perm The permissions specified in either absolute form (string rwx or
with a dash (-) as a placeholder) or in relative form using the plus
(+) sign or carat (^) modifiers.
For the relative format, only one of + or ^ is allowed per ACL entry.
Also, when using the relative format, you must specify at least one](https://image.slidesharecdn.com/sg246776-150502075816-conversion-gate02/85/Sg246776-233-320.jpg)
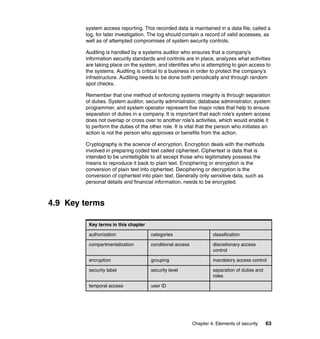
![212 Introduction to the New Mainframe: Security
of r, w, or x. For example: +rw means to add read and write
privileges to the ACL entry.
When using the relative format of the ACL permissions, if the ACL entry does not
already exist, the relative permissions are assigned as though they were given in
absolute form, and any permissions not specified default to no permission.
For example, you intend to update a ACL entry using the following extended ACL
entry:
user:tot184:+rw
However, the ACL entry does not yet exist, so the permissions are converted to
absolute permissions and any permissions that are not specified will default to no
permission, resulting in the following ACL entry:
user:tot184:rw-
Similarly, if you attempt to remove permissions for an ACL entry that does not
exist, the resulting permissions are:
user:tot184:---
To establish or maintain ACL entries, you must:
Be the owner of the file or directory
Be the superuser or have access to the class FACILITY
SUPERUSER.FILESYS profile
11.5.3 Extended permissions
In addition to the standard UNIX file and directory permissions, z/OS UNIX
includes several extended permission bits that are unique to z/OS UNIX.
To display the extended permission settings, you need to add the -E option to the
ls command, for example ls -E. Example 11-4 illustrates a directory listing that
shows the extended permission bits on a z/OS UNIX system:
Example 11-4 Directory listing, extended permissions
$ ls -E
total 11
-rwxr--r-- --sl 1 ROOT SYS1 640 Mar 12 19:33 abc
-rwxr--r-- ap-l 1 ROOT SYS1 572 Mar 12 19:32 foo
Note: In the preceding text, the square brackets [ ] are used to show that the
text between the brackets is optional and not required. The brackets are not
part of the commands.](https://image.slidesharecdn.com/sg246776-150502075816-conversion-gate02/85/Sg246776-234-320.jpg)












![226 Introduction to the New Mainframe: Security
z/OS provides a set of SSL C/C++ APIs that, when used with the z/OS Sockets
APIs, provide the functions required for z/OS applications to establish secure
sockets communications.
Transport Layer Security (TLS) is the latest in the continuing evolution of SSL.
TLS 1.0 might as readily have been titled “SSL 3.1”. In fact, when negotiating a
TLS handshake, the client and server hello messages use version specification
3.1 (SSL 3.0 uses version specification 3.0).
Finally, TLS 3.1 is a protocol designed with the intent of allowing enhancements
for future improvements to privacy over TCP connections.
The RFC for TLS 3.1 includes support for extensions which:
Allow TLS clients to provide to the TLS server the name of the server they are
contacting.
Allow TLS clients and servers to negotiate the maximum fragment length to
be sent.
Allow TLS clients and servers to negotiate the use of client certificate URLs.
Allow TLS clients to indicate to TLS servers which CA root keys they possess.
Allow TLS clients and servers to negotiate the use of truncated MACs.
Allow TLS clients and servers to negotiate that the server sends the client
certificate status information (for example, an Online Certificate Status
Protocol (OCSP) [OCSP] response) during a TLS handshake.
SSL does not provide for such enhancements.
Encryption algorithms
An encryption algorithm is a mathematical procedure for converting a plaintext
message into ciphertext. Through the use of an algorithm, information is made
into meaningless cipher text and requires the use of a key to transform the data
back into its original form. There are several algorithms, each with its own
advantages and drawbacks. DES, 3DES, and AES are examples of encryption
algorithms; refer to 7.2.1, “The symmetric algorithms” on page 107, for more
information about this topic.
Session keys
Session keys are the seeds to the cryptographic algorithms used to encipher the
data that flows between parties over a public network. The algorithms are well
known, but the session keys are known only to the applications at the ends of the
conversation.](https://image.slidesharecdn.com/sg246776-150502075816-conversion-gate02/85/Sg246776-248-320.jpg)




































































































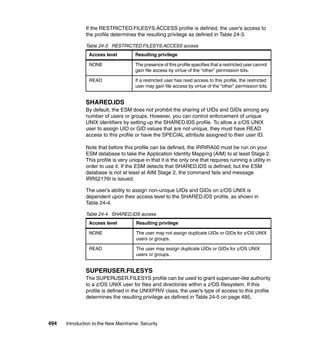
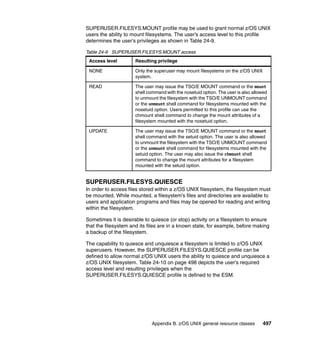
![Chapter 17. Data management security 345
primary difference between the types of VSAM data sets is the way their
records are stored and accessed.
17.6.1 Protecting VSAM files with passwords
VSAM files can be protected using passwords. The problem with this is that you
may need to use a large number of passwords. To use password protection
effectively, you need to understand the difference between operations on a
catalog and operations on a data set represented by a catalog entry, as
explained here:
Referring to a catalog entry when new entries are defined (ALLOCATE or
DEFINE), or existing entries are altered (ALTER), deleted (DELETE), or listed
(LISTCAT).
Using the data set represented by a catalog entry when it is connected to a
user's program (OPEN), or disconnected (CLOSE).
OPEN and CLOSE operations on a data set can be authorized by the
password pointed to by the PASSWD parameter of the ACB macro.
Different passwords might be needed for each type of operation. Operations
on a catalog can be authorized by the catalog's password or, sometimes, by
the password of the data set defined in the catalog. The following are
examples of passwords required for defining, listing, and deleting
non-system-managed catalog entries:
Defining a non-system-managed data set in a password-protected catalog
requires the catalog's update (or higher) password.
Listing, altering, or deleting a data set's catalog entry requires the appropriate
password of either the catalog or the data set. However, if the catalog (but not
the data set) is protected, no password is needed to list, alter, or delete the
data set's catalog entry.
17.6.2 Protecting VSAM files with RACF
The parameter PROTECT=YES in the DD statement indicates that the file will be
RACF protected. Note that with SMS, the DD SECMODEL parameter overrides
the PROTECT=YES parameter. The SECMODEL parameter, with SMS only,
specifies SECMODEL=(profile-name [GENERIC]), where profile-name is the
name of a model profile and GENERIC when the model is a generic profile. Both
specify a RACF profile to be used for a new data set.
The SECMODEL parameter is used to specify the name of an existing RACF
data set profile that is copied to the discrete data set profile that RACF builds for
the new data set.](https://image.slidesharecdn.com/sg246776-150502075816-conversion-gate02/85/Sg246776-367-320.jpg)