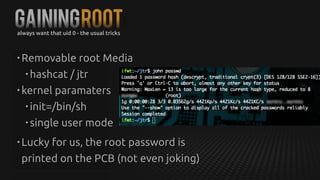
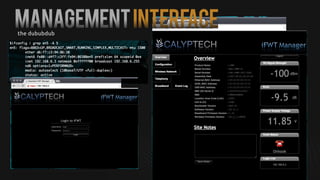
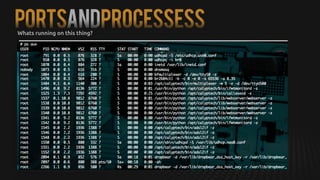
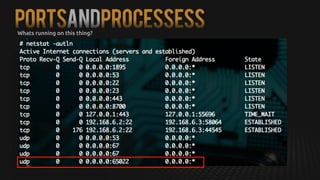
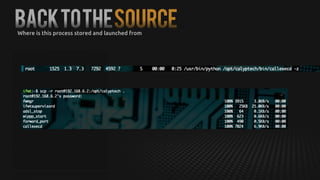
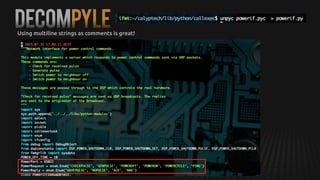
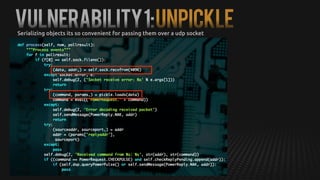
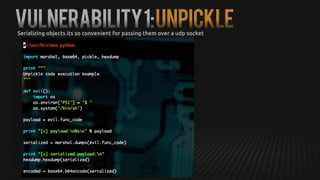
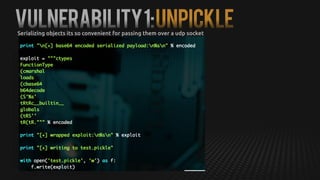
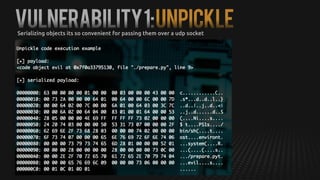
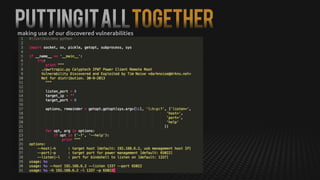
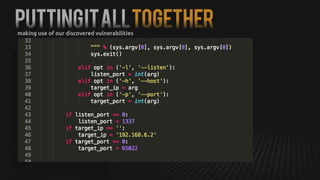
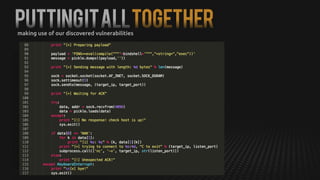
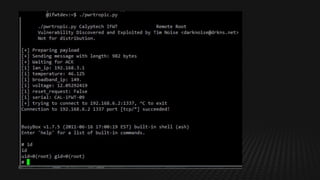
This document summarizes how to exploit vulnerabilities in fixed wireless terminals to remotely root the devices. It describes examining the hardware components and boot process to find entry points. Exploits discussed include using removable media to gain root access, cracking weak passwords, and exploiting unpickle serialization and remote code execution via eval. A demonstration shows using these techniques to remotely root a terminal via its management interface and UDP vulnerabilities. Potential further attacks discussed include installing backdoors, intercepting data and calls, and creating botnets.