Embed presentation
Download to read offline



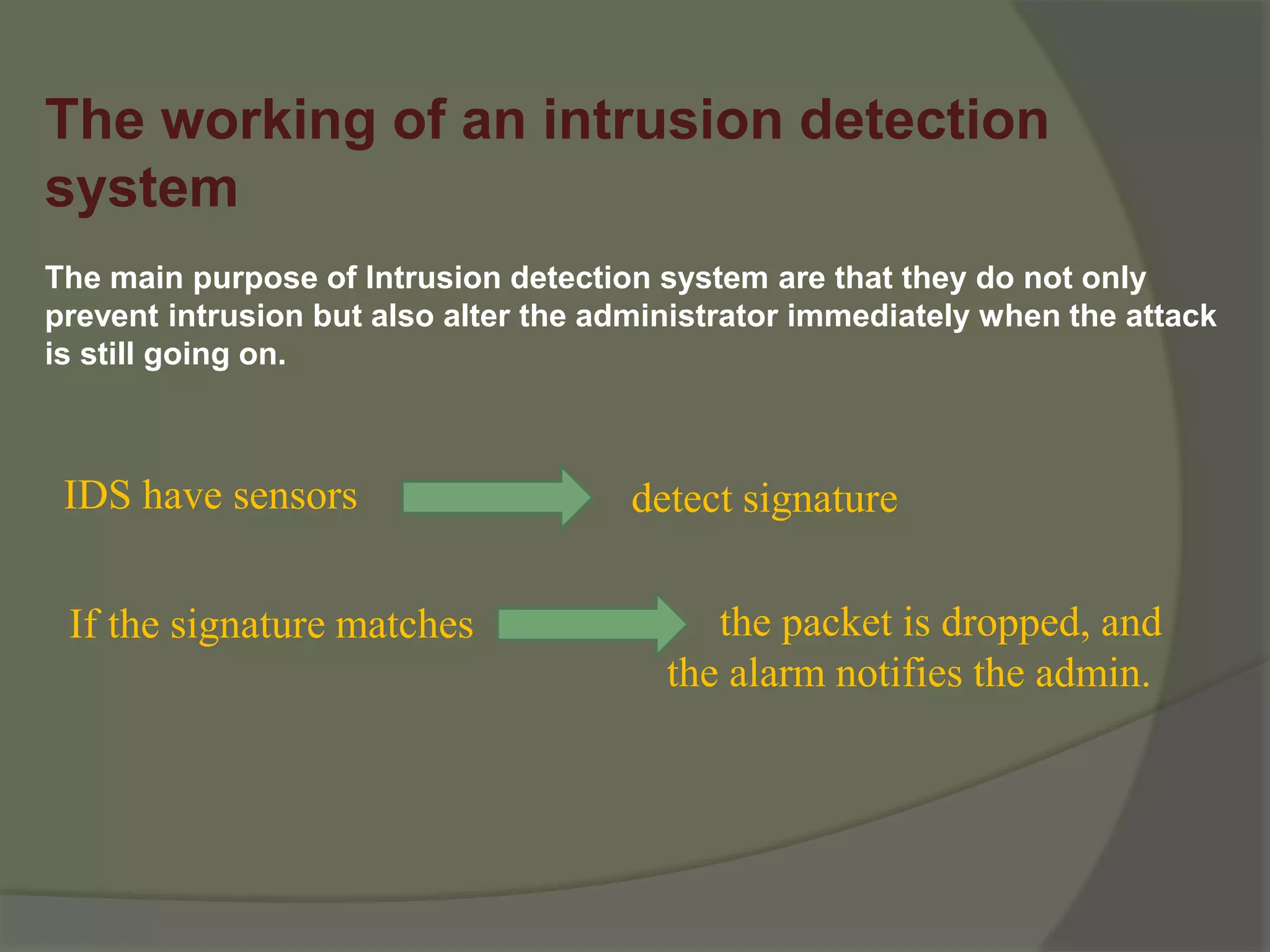

An intrusion detection system (IDS) is a security tool that monitors network or system activities for malicious actions and policy violations. It gathers and analyzes data, acts as a packet sniffer, and alerts administrators of potential intrusions in real-time. IDS can utilize techniques like signature detection and anomaly detection to identify threats and respond accordingly.





