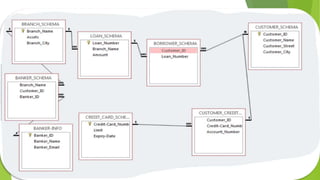
A database management system (DBMS) is system software that allows for the creation, management, and use of databases, making it easier to create, retrieve, update and manage large amounts of data in an organized manner. The document discusses the definition, importance, implementation, requirements, and challenges of a DBMS, as well as entity relationship diagrams, modeling, and security concepts related to databases. In conclusion, a DBMS is an effective system for systematic data management that is widely used around the world.