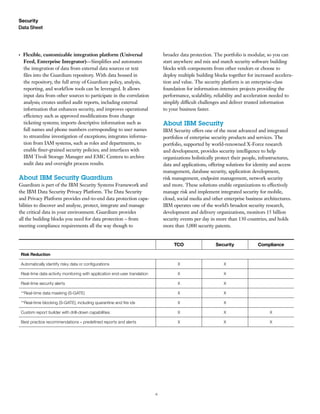
The IBM Security Guardium Data Activity Monitor continuously monitors data access to protect sensitive information across various environments, including databases and cloud systems. It offers real-time security alerts, automated compliance support, and customizable reporting, while minimizing data breach risks through actionable insights and response capabilities. The solution is designed to scale seamlessly, adapting to dynamic IT environments without compromising performance.