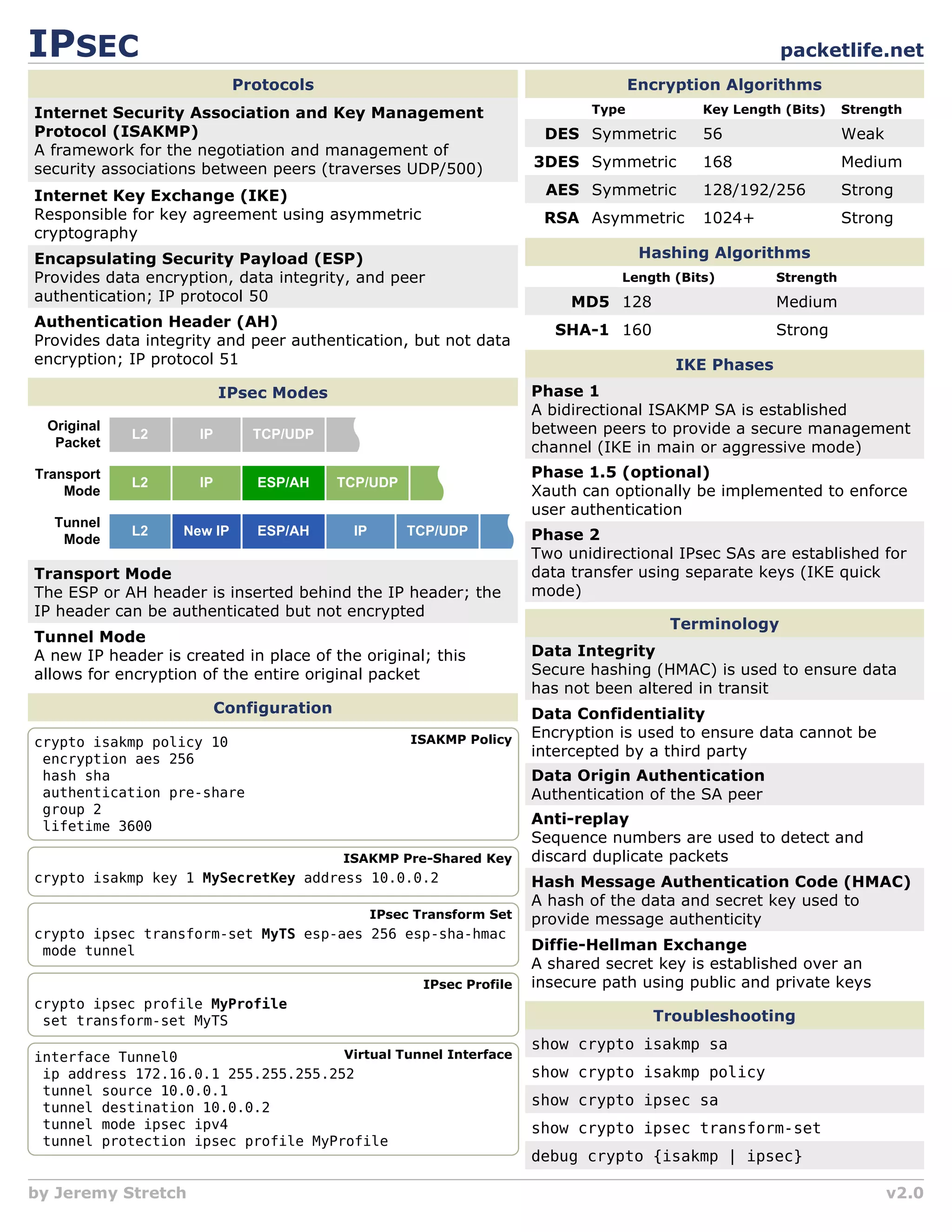
This document summarizes key concepts in IPsec including:
1) It describes the main IPsec protocols - ISAKMP for key negotiation, IKE for key exchange, and ESP and AH for encryption and authentication.
2) It provides an overview of the encryption algorithms, hashing algorithms, and authentication methods used in IPsec like AES, 3DES, SHA-1, and pre-shared keys.
3) It explains the two main IPsec modes - transport which encrypts only payload, and tunnel which encrypts entire packets including headers.