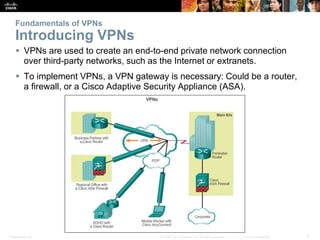
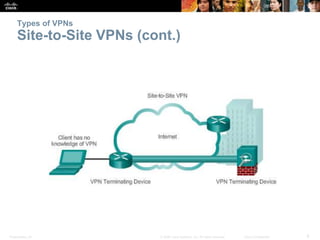
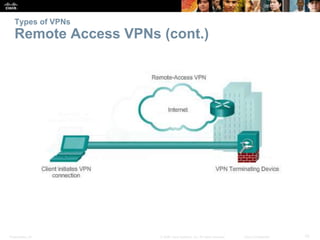
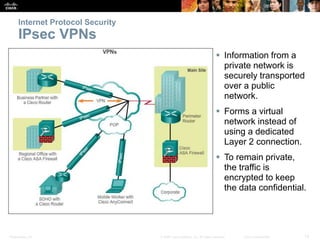
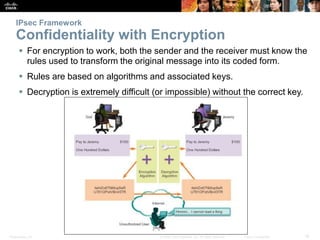
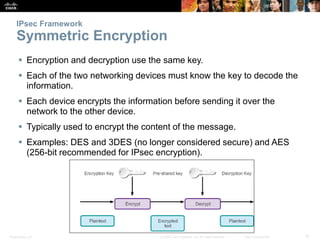
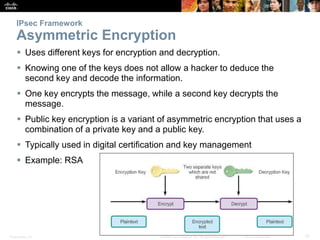
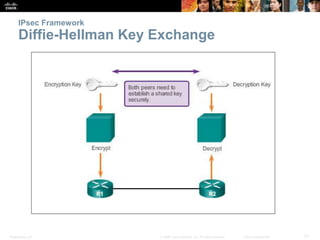
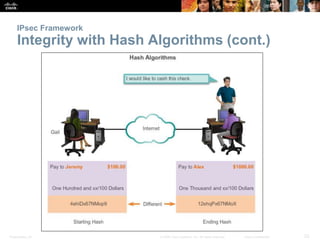
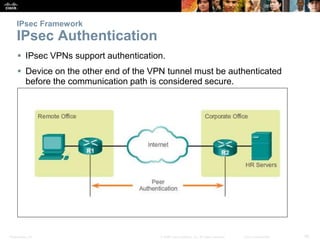
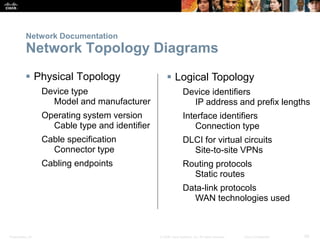
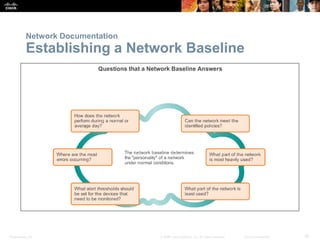
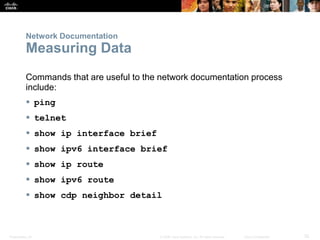
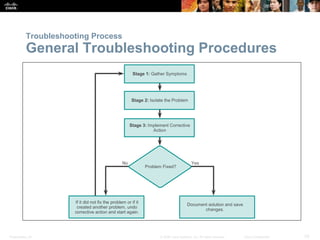
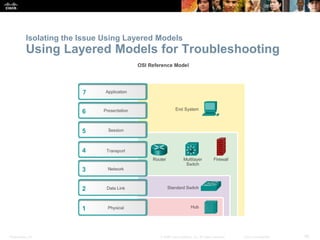
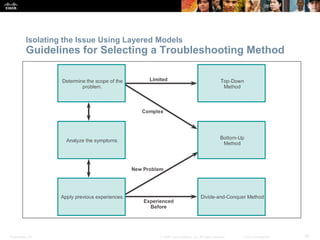
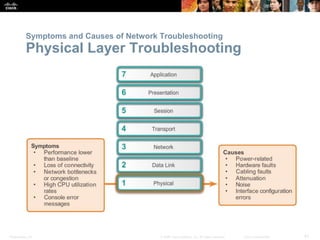
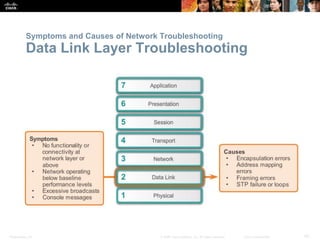
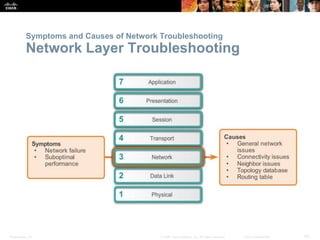
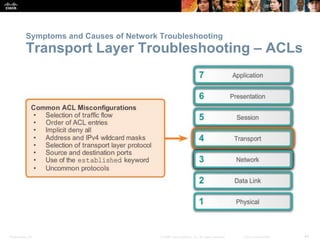
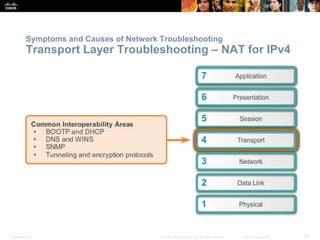
This document discusses VPN fundamentals and IPsec VPNs. It defines VPNs as private network connections over public networks like the Internet, requiring VPN gateways. VPNs provide benefits like cost savings, scalability, compatibility with broadband, and security. The document describes site-to-site and remote access VPN types. It then focuses on IPsec VPNs, outlining how IPsec provides data confidentiality, integrity, and authentication at the network layer using encryption, hash algorithms, and techniques like Diffie-Hellman key exchange and HMAC.