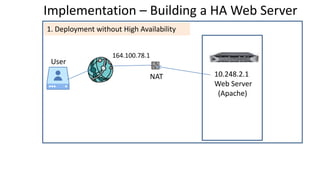
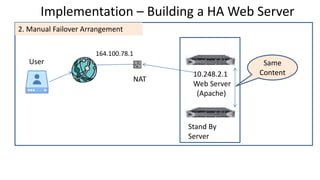
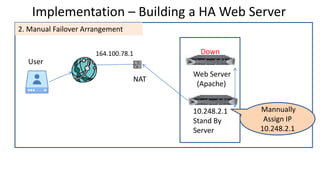
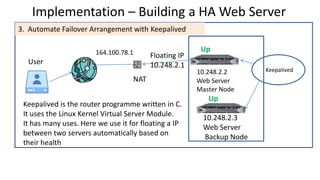
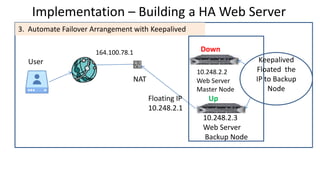
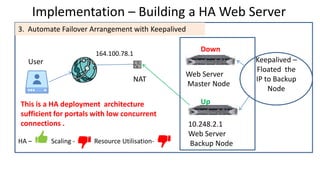
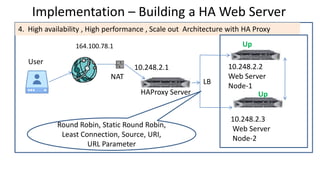
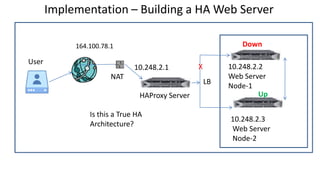
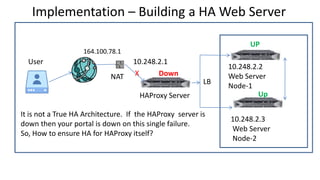
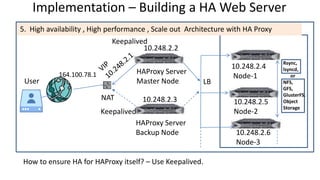
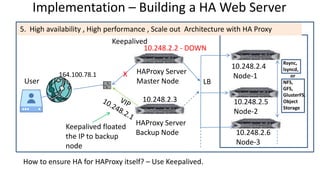
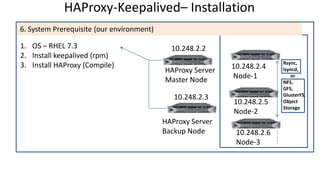
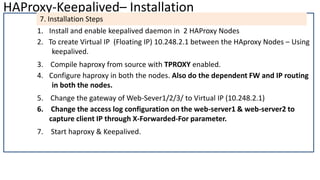
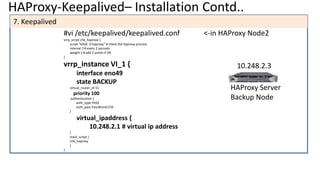
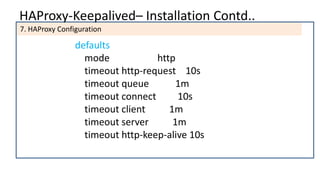
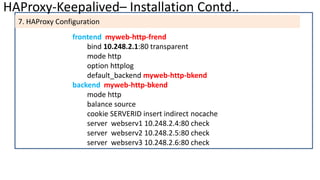
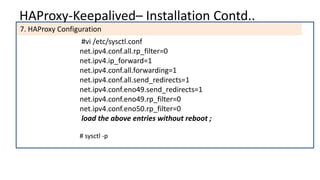
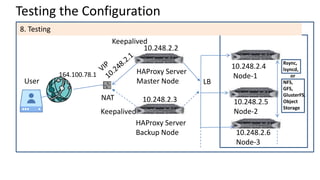
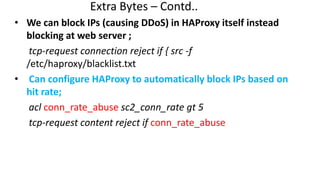
The document discusses the deployment architecture for high availability using HAProxy and Keepalived, emphasizing their roles in load balancing, high performance, and DDoS prevention. It outlines the advantages of HAProxy over alternatives such as NGINX and AWS Elastic LB, while also providing implementation steps and configuration details for setting up a highly available web server environment. The presentation targets participants with minimal server administration experience, aiming to facilitate understanding and implementation in production environments.