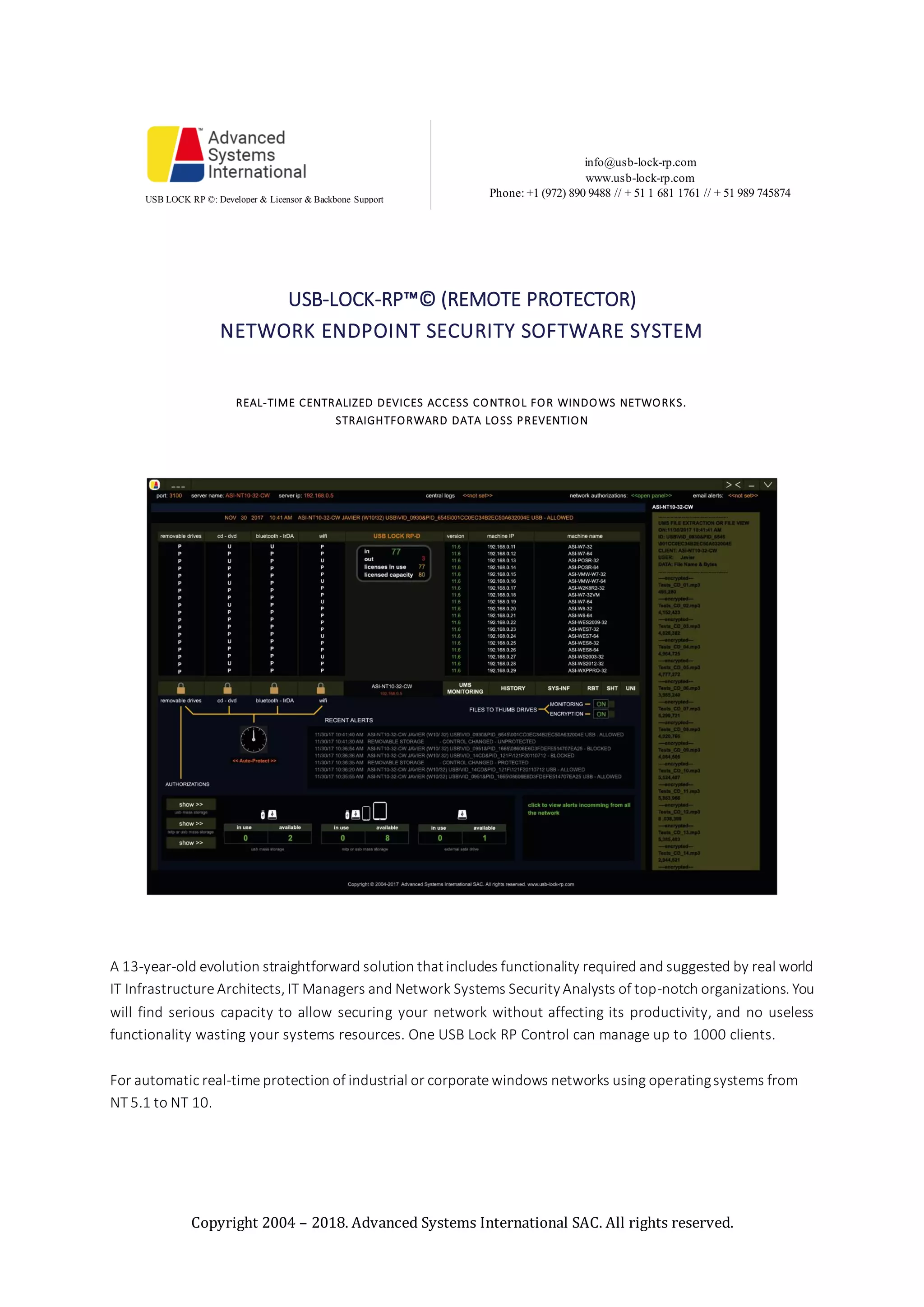
USB LOCK RP is network endpoint security software that provides real-time centralized access control of devices on Windows networks. It allows authorization of up to 60 device groups or specific devices for all network clients. The software automatically logs inserted devices, file transfers, and generates reports. It protects against unauthorized USB devices and software installation/uninstallation on networked Windows PCs and servers from Windows NT 5.1 to 10.