This document contains summaries from a presentation on various cybersecurity topics:
1) Windows Firewall configuration is often misconfigured and does not provide detailed logging or filtering capabilities. Firewalls are best used to segment networks and control which processes can communicate internally or externally.
2) Password reuse is common, with variants of company names and numbers often used. Continuous security awareness is needed to mitigate weak passwords.
3) Privileged accounts and service accounts pose risks as their passwords are stored in the registry and accessible offline. User privileges can be higher than expected, allowing access to sensitive system hives.
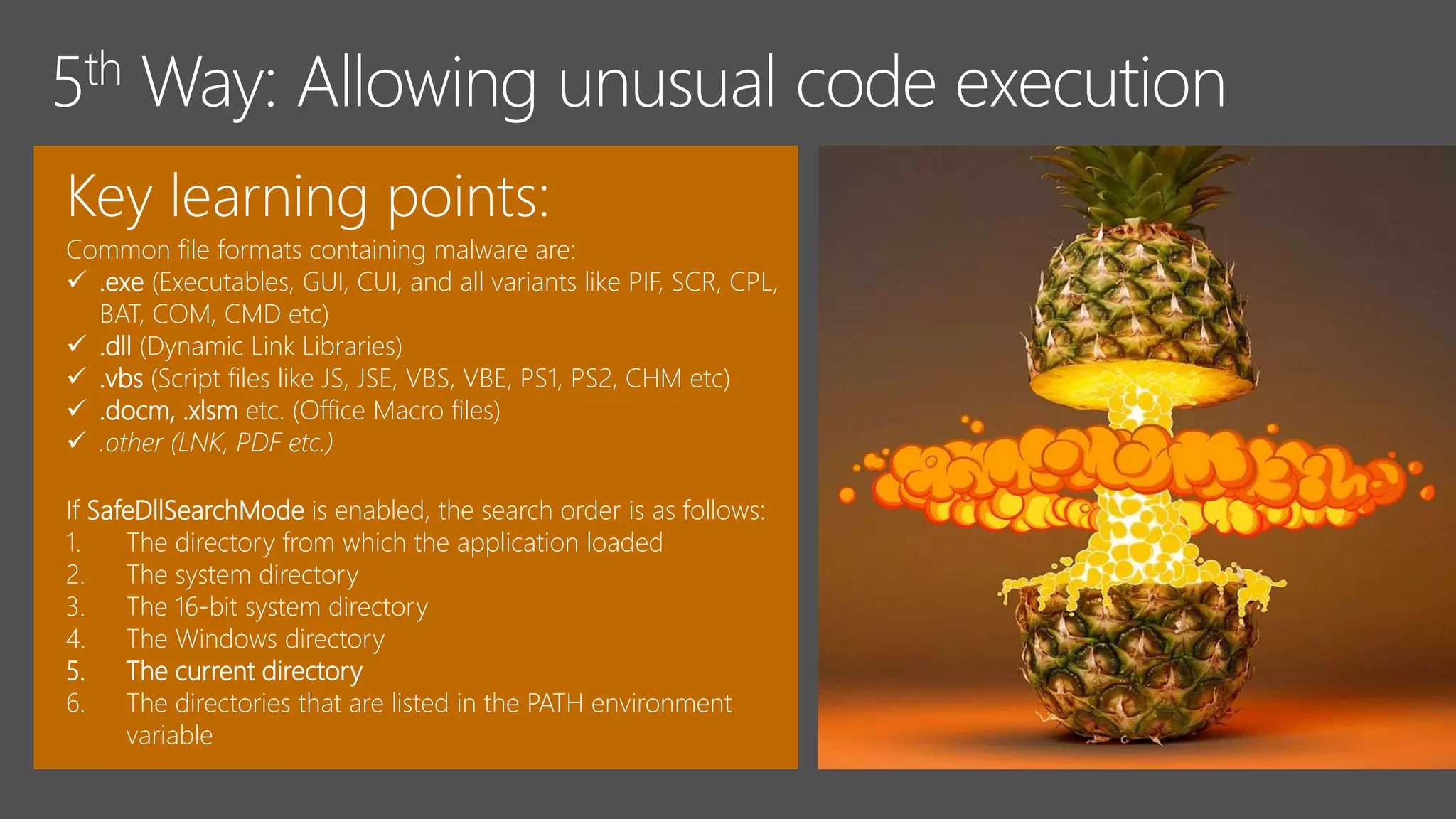
4) Third-party security tools also contain weaknesses that must be understood to ensure effective security. Configuration management