The document describes how to install and use the Verax SNMP Simulator to simulate network devices. It includes instructions to install the simulator, extract SNMP data from physical devices, add simulated devices to the simulator, start the simulator, and add simulated devices to the Verax NMS.





![How to simulate network devices using the Verax SNMP Simulator (Linux/Windows)
2. Extracting SNMP record files from a physical device
Extracting SNMP record files from a physical device can be done using the snmpwalk command. Therefore,
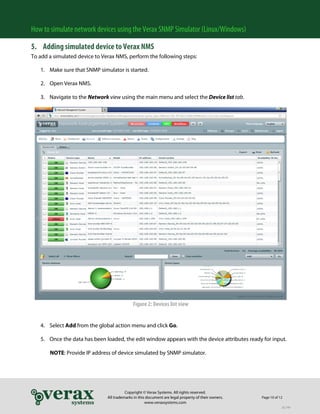
in order to extract SNMP record files from an existing device, the SNMP tools allowing for executing
snmpwalk command should be installed, e.g. NET-SNMP.
NET-SNMP can be downloaded for free from: http://sourceforge.net/projects/net-snmp
1. Open the Command Line and go to the NET-SNMP installation directory (e.g. C:userbin).
2. If running on Linux, open the terminal window (shell).
3. If running on Windows, open the Command Line and go to the NET-SNMP installation directory (e.g.
C:userbin).
4. In order to prepare SNMP record file reflecting actual SNMP agent available at given IP address, use
the SNMP tools and issue the following command:
snmpwalk -On -Oe -OU -v2c -c public address > [destination folder]filename.txt
e.g.
snmpwalk -On -Oe -OU -v2c -c public 192.168.100.8 > C:”Program Files”vxsnmpsimulatordevice
cisco-snmprecordfile.txt
5. The cisco-snmprecordfile.txt file containing OIDs of the real device will be stored in the device
directory.
Copyright © Verax Systems. All rights reserved.
All trademarks in this document are legal property of their owners.
www.veraxsystems.com
Page 6 of 12
DL749](https://image.slidesharecdn.com/how-to-simulate-network-devices-131112211620-phpapp02/85/How-to-simulate-network-devices-6-320.jpg)


![How to simulate network devices using the Verax SNMP Simulator (Linux/Windows)
3. The Management Console will ask for connection details (it may connect to multiple simulators). By
default, the simulator service process is running on the same server as the Management Console – in
such a case confirm the default parameters by pressing “y” at the prompt:
Do you want to connect to default simulator server? [y/n]
The default connection parameters are 127.0.0.1:43500 (localhost as the host name and 43500 for
TCP port).
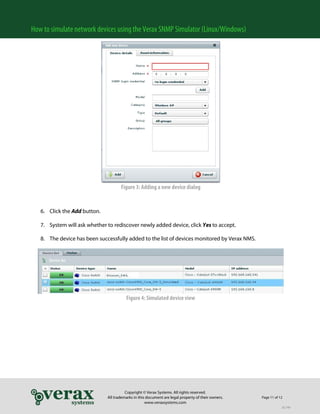
4. Use the SHOW command to list simulated devices.
5. A list of simulated devices is displayed.
Figure 1: List of simulated devices
6. Make sure your simulated devices are in the “Running” state. If not, check if the simulator is able to
bind the interface or examine the log file.
Copyright © Verax Systems. All rights reserved.
All trademarks in this document are legal property of their owners.
www.veraxsystems.com
Page 9 of 12
DL749](https://image.slidesharecdn.com/how-to-simulate-network-devices-131112211620-phpapp02/85/How-to-simulate-network-devices-9-320.jpg)