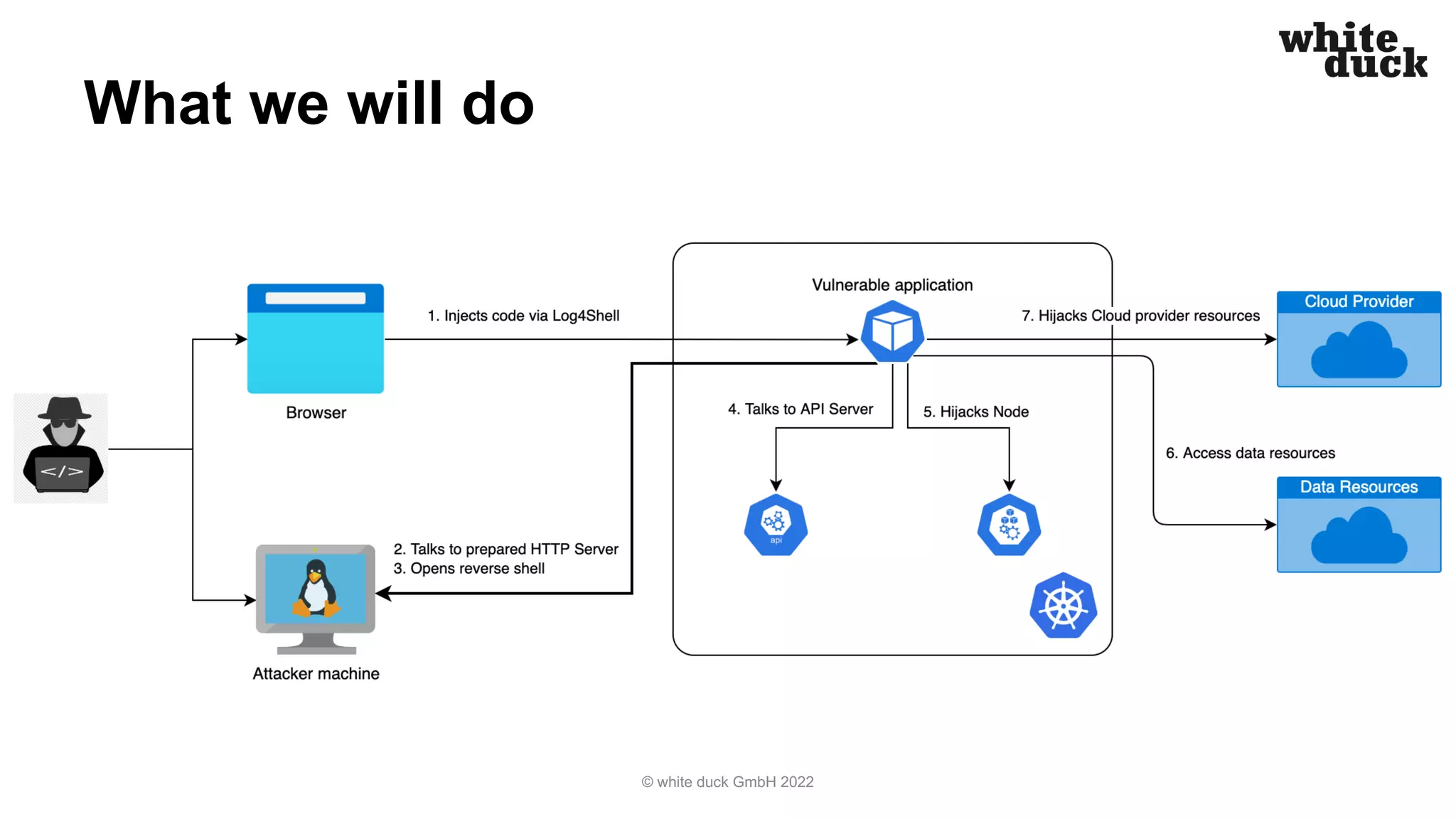
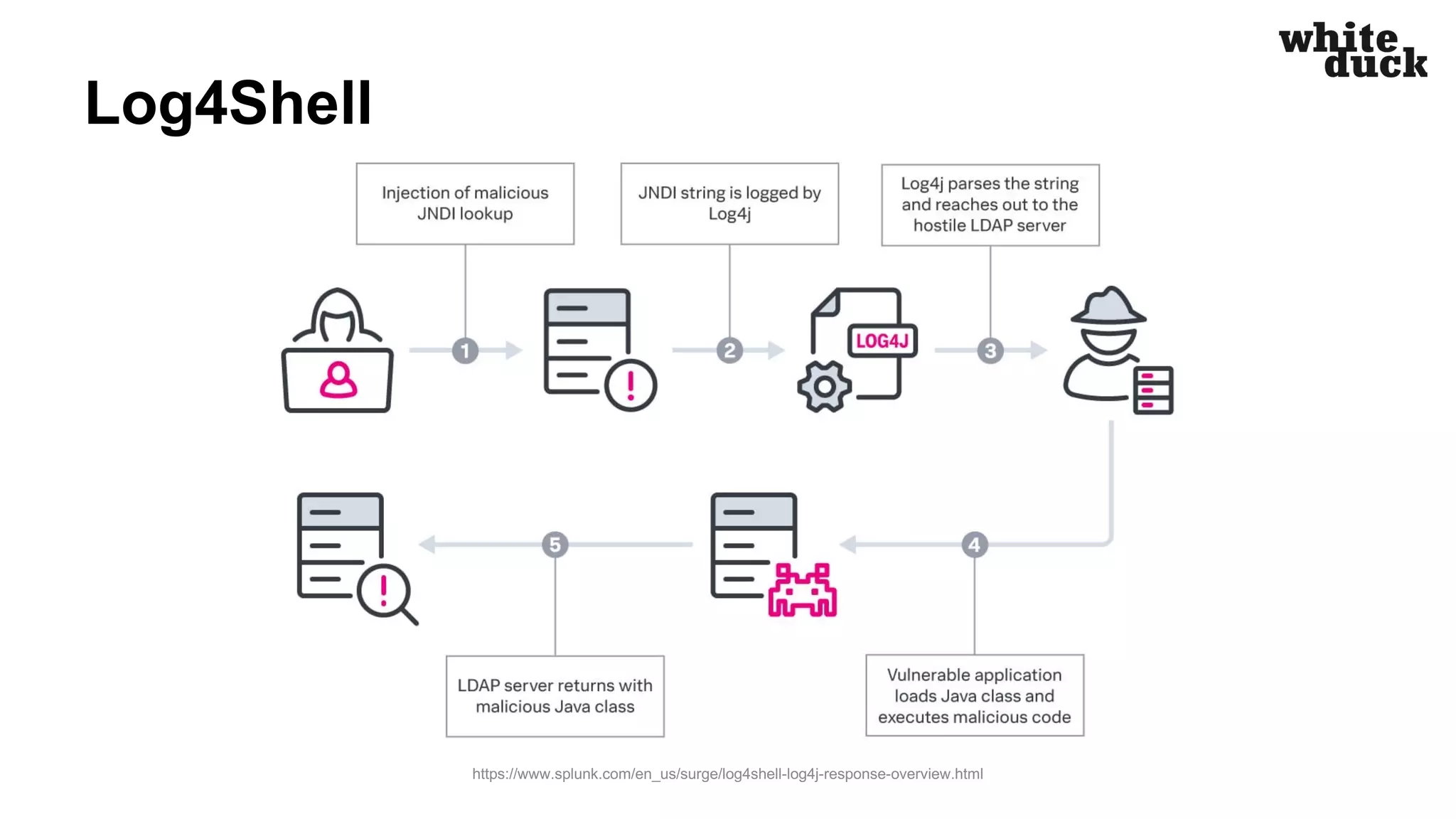
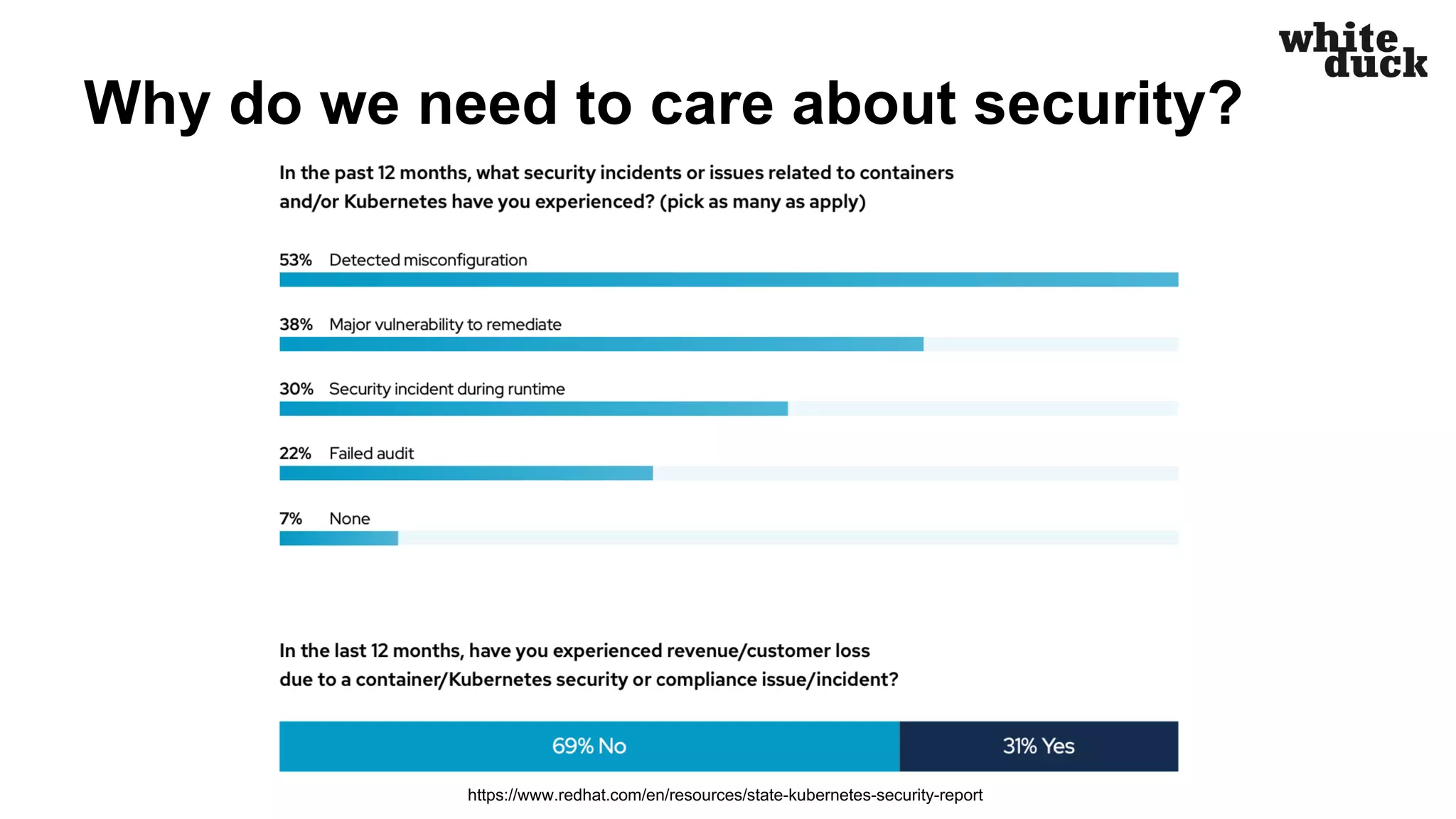
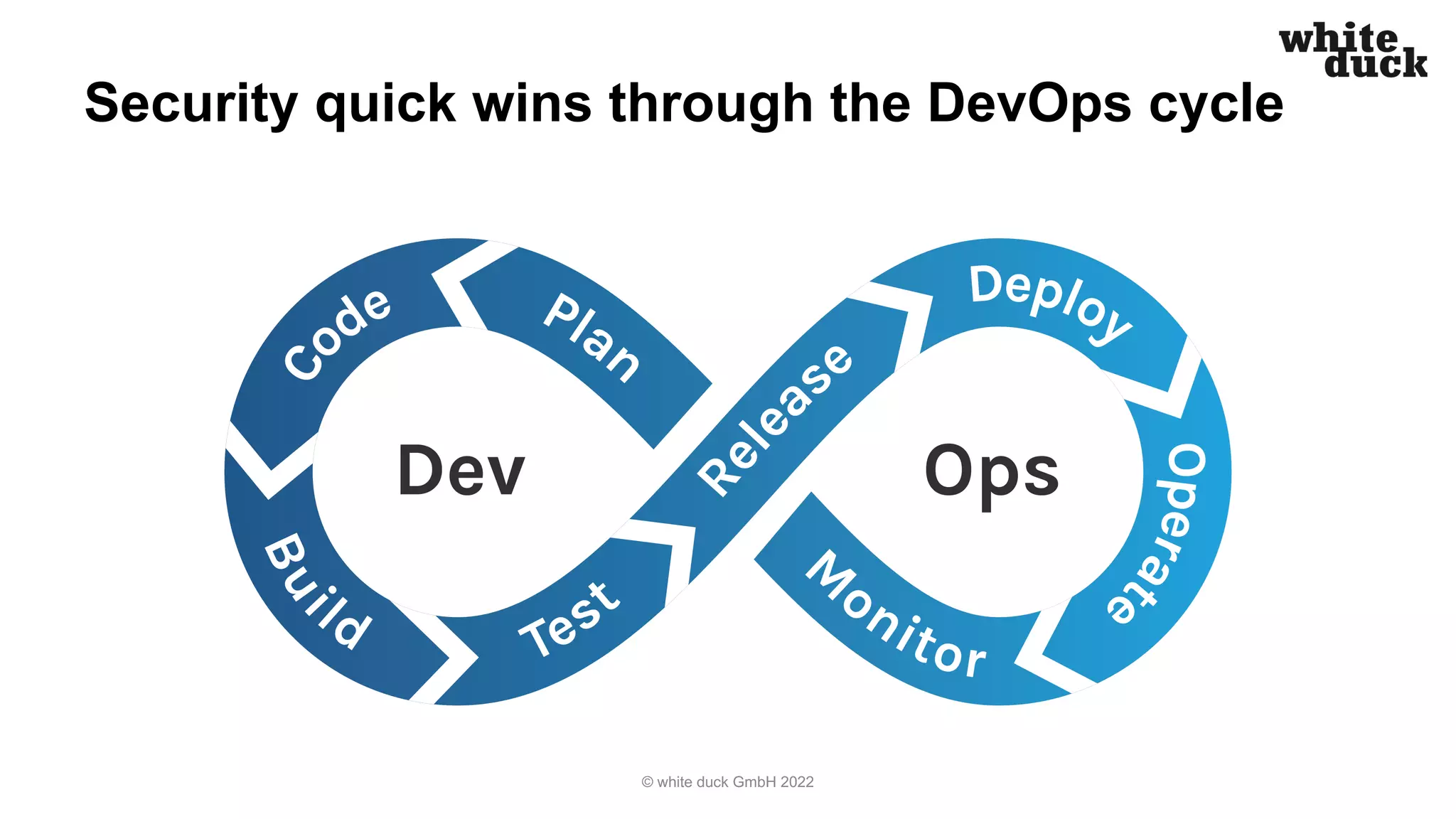
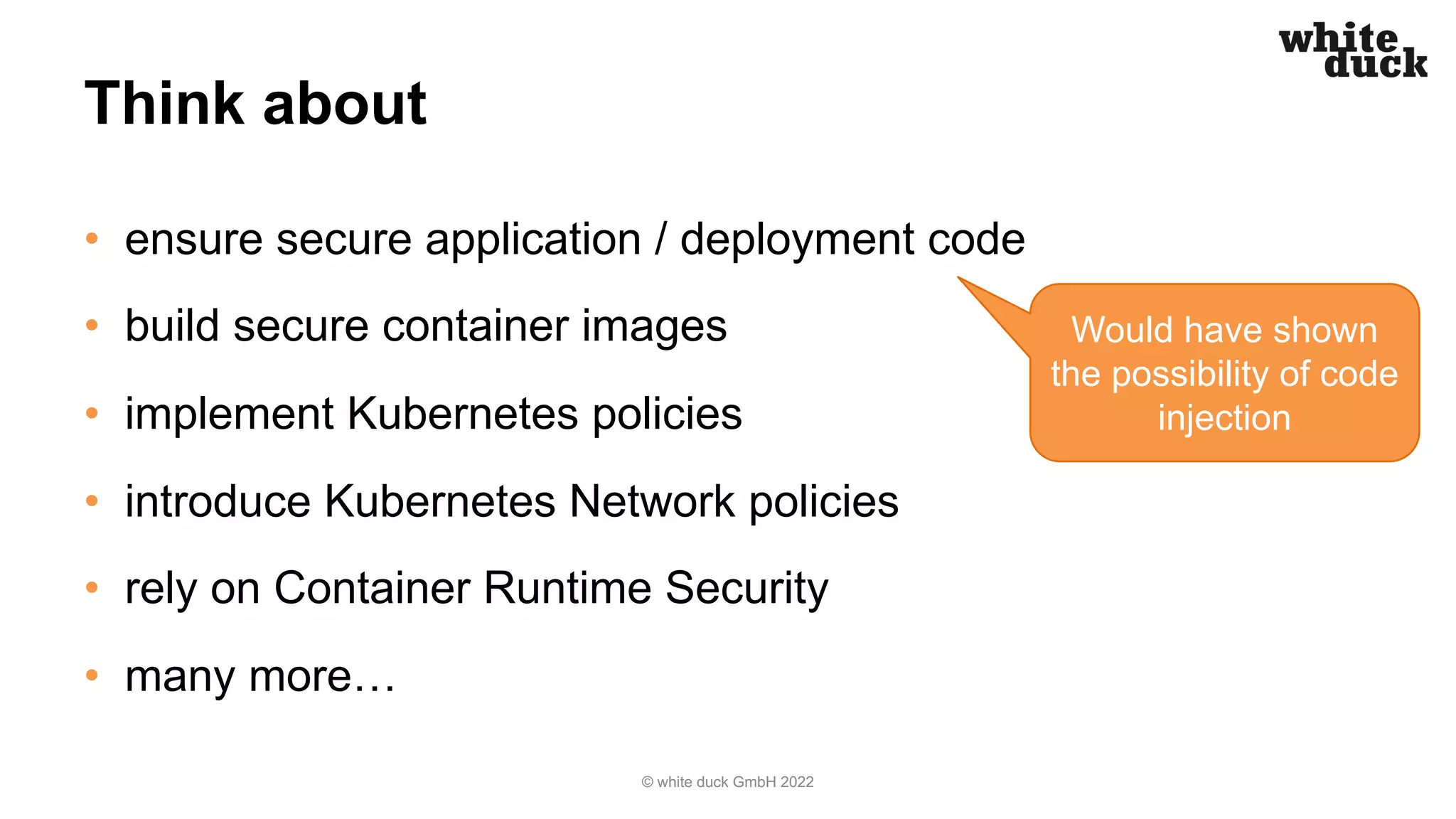
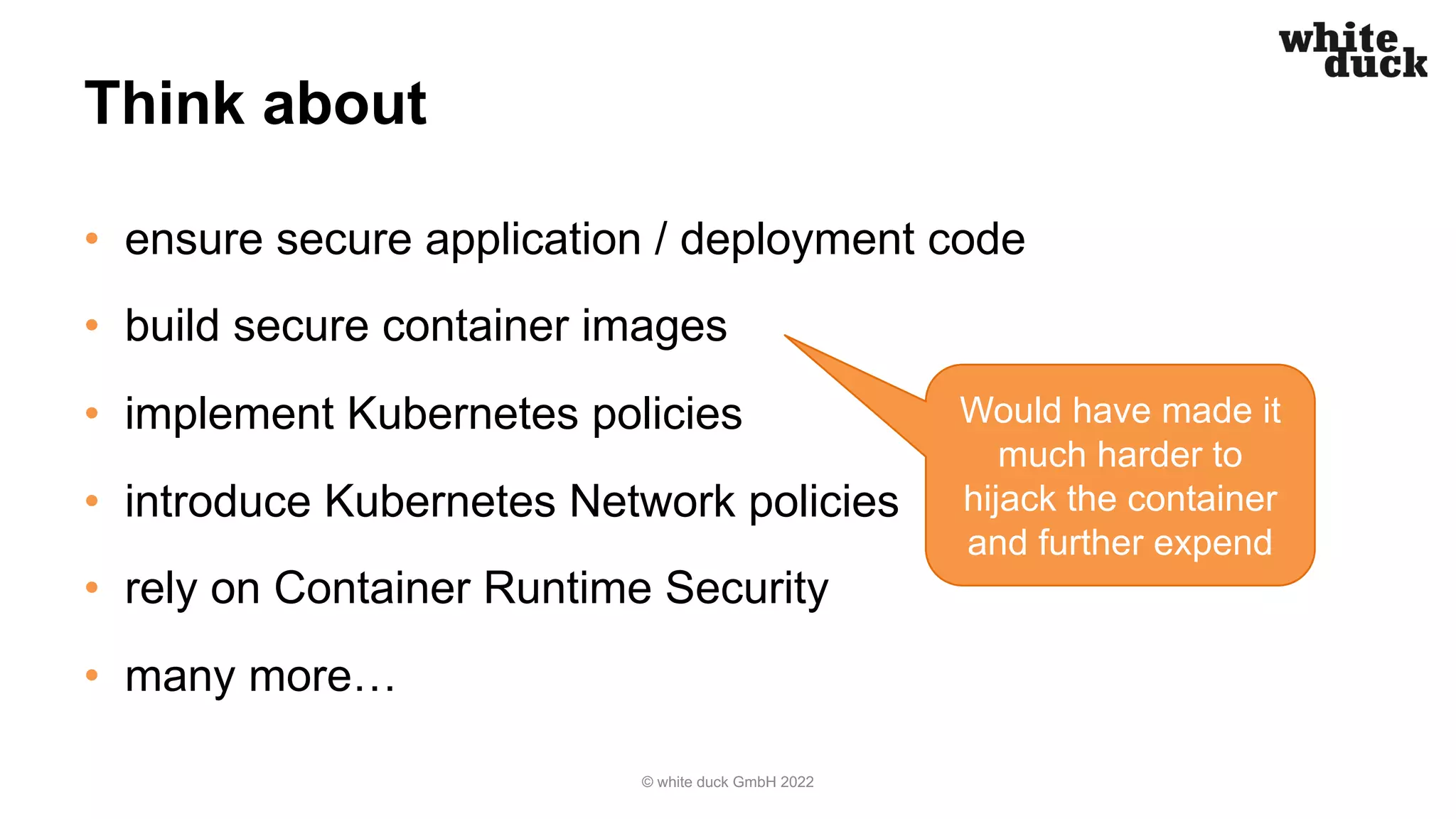
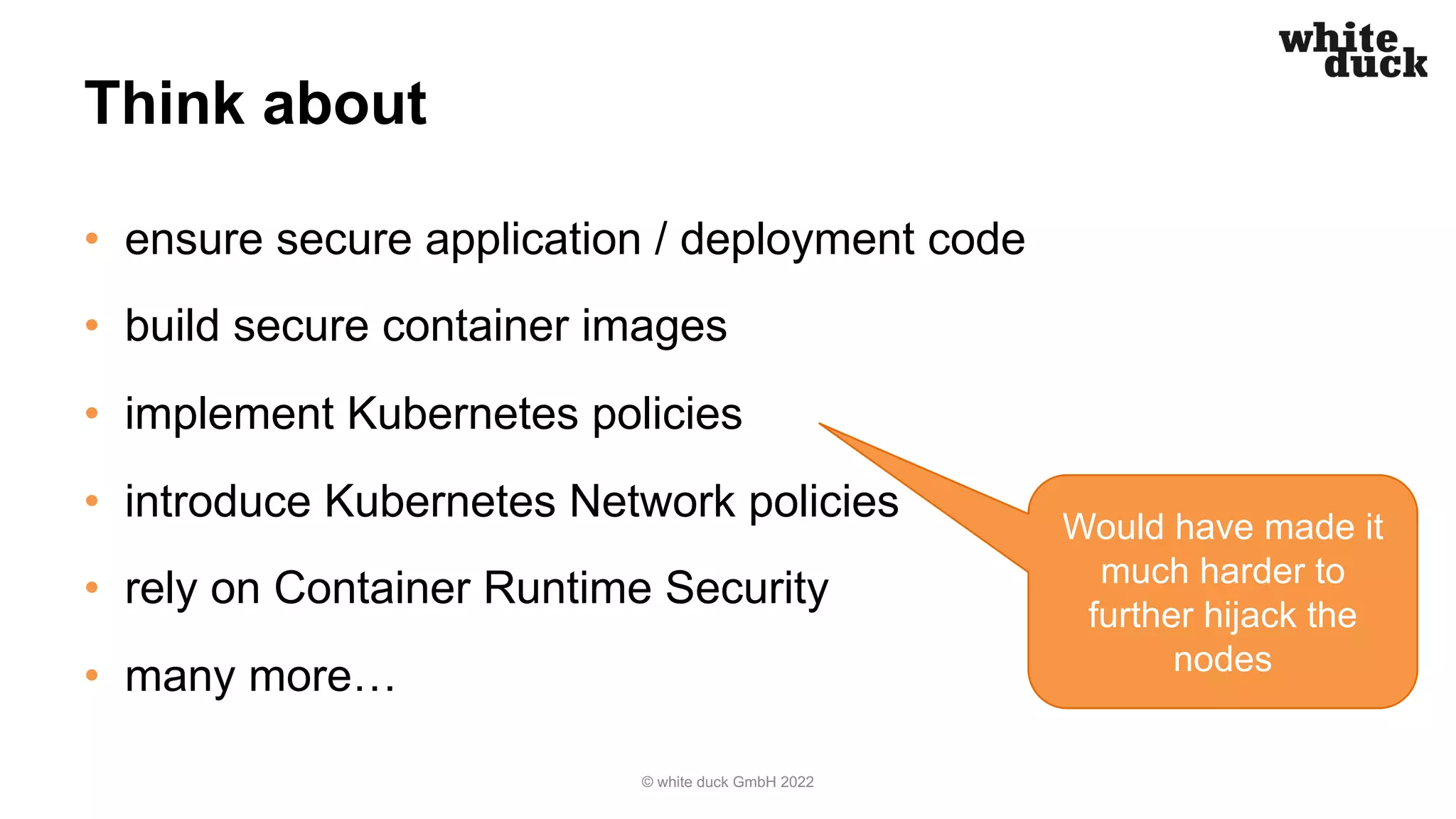
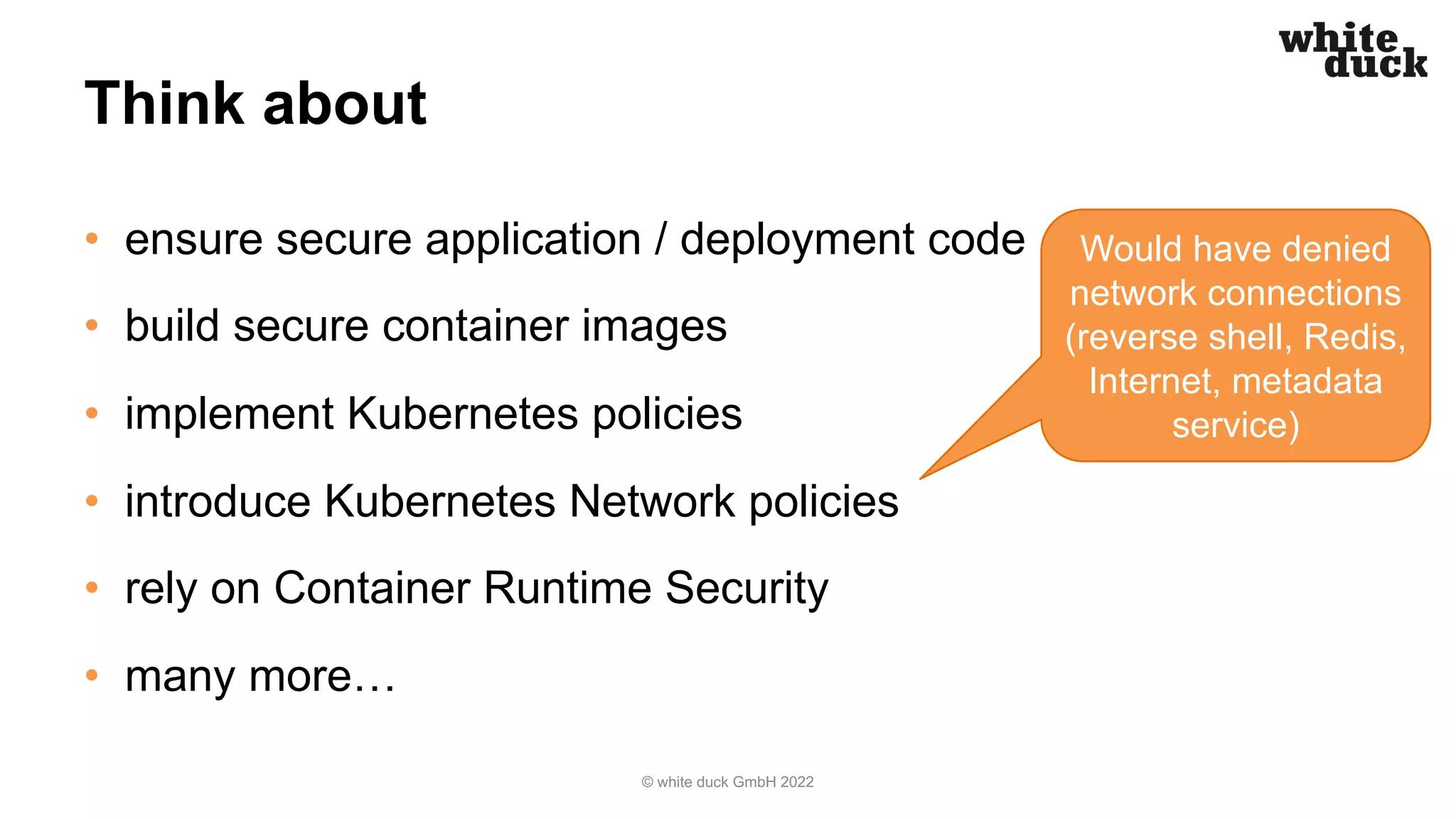
The document summarizes a presentation on how to hijack a Kubernetes cluster in order to demonstrate common attack vectors and prevention best practices. The presentation includes demos of hijacking a cluster and discusses how secure application code, container images, network policies, and container runtime security can prevent hijacking. It encourages attendees to implement such security measures to harden their own Kubernetes clusters.