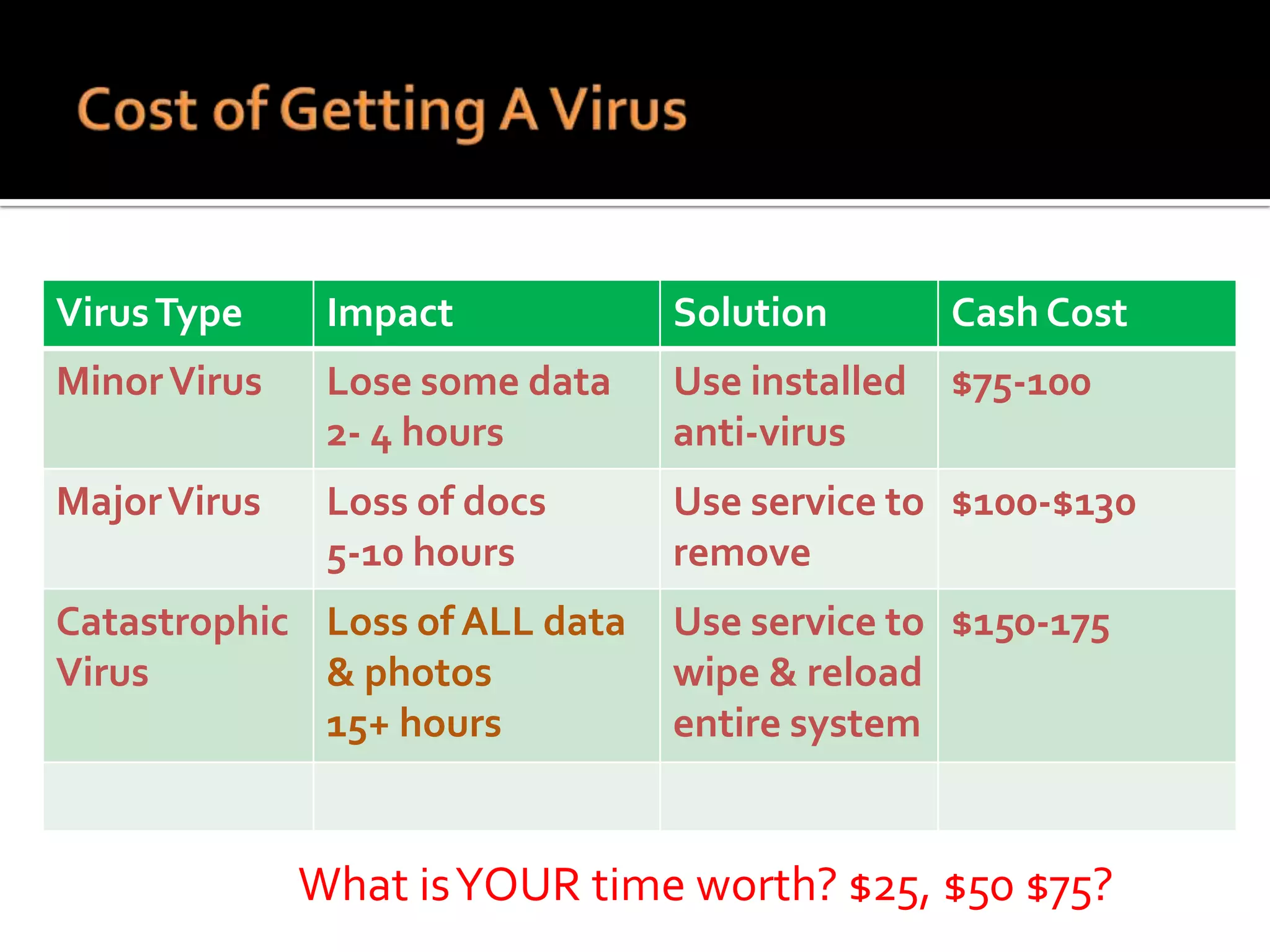
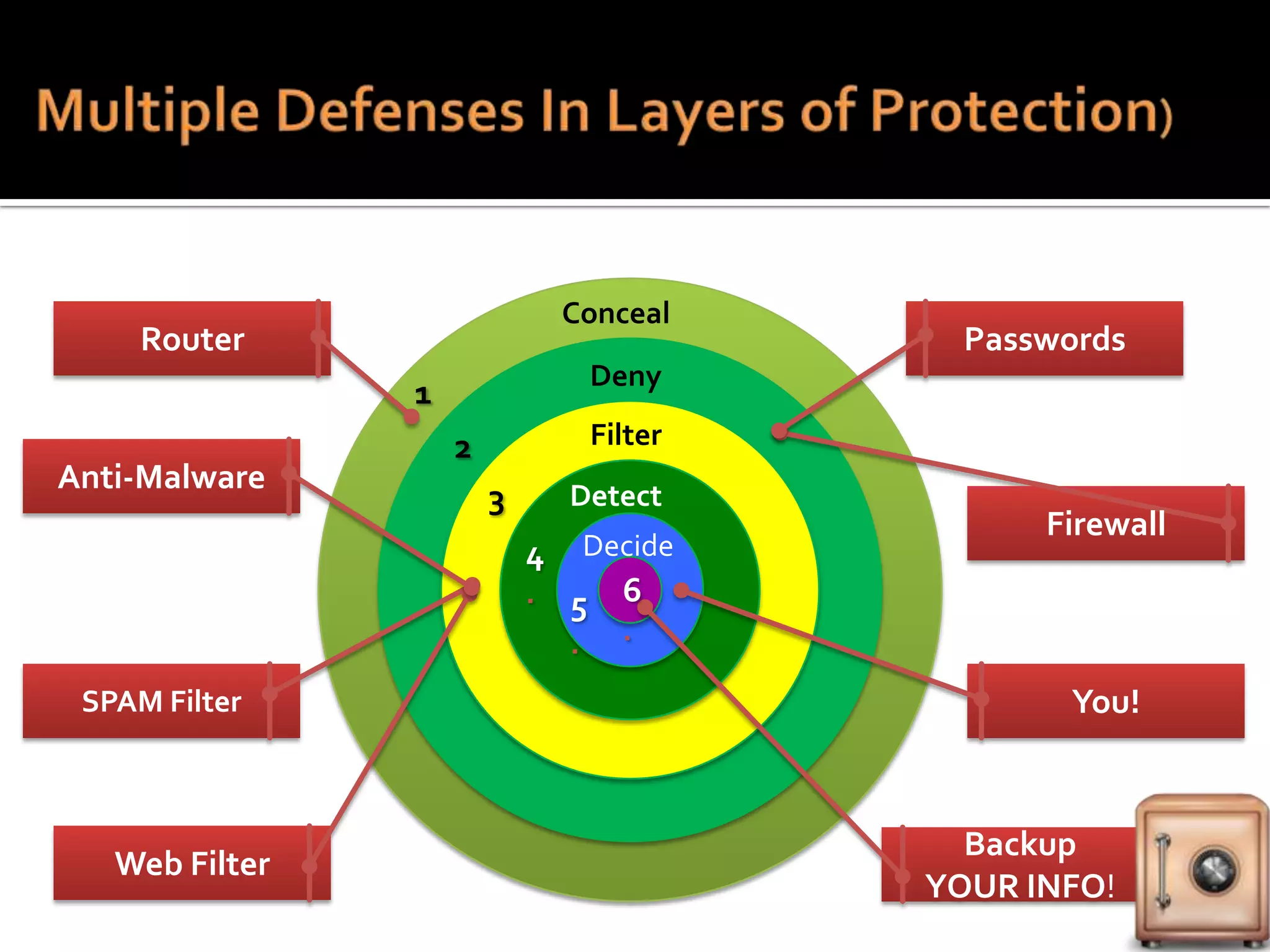
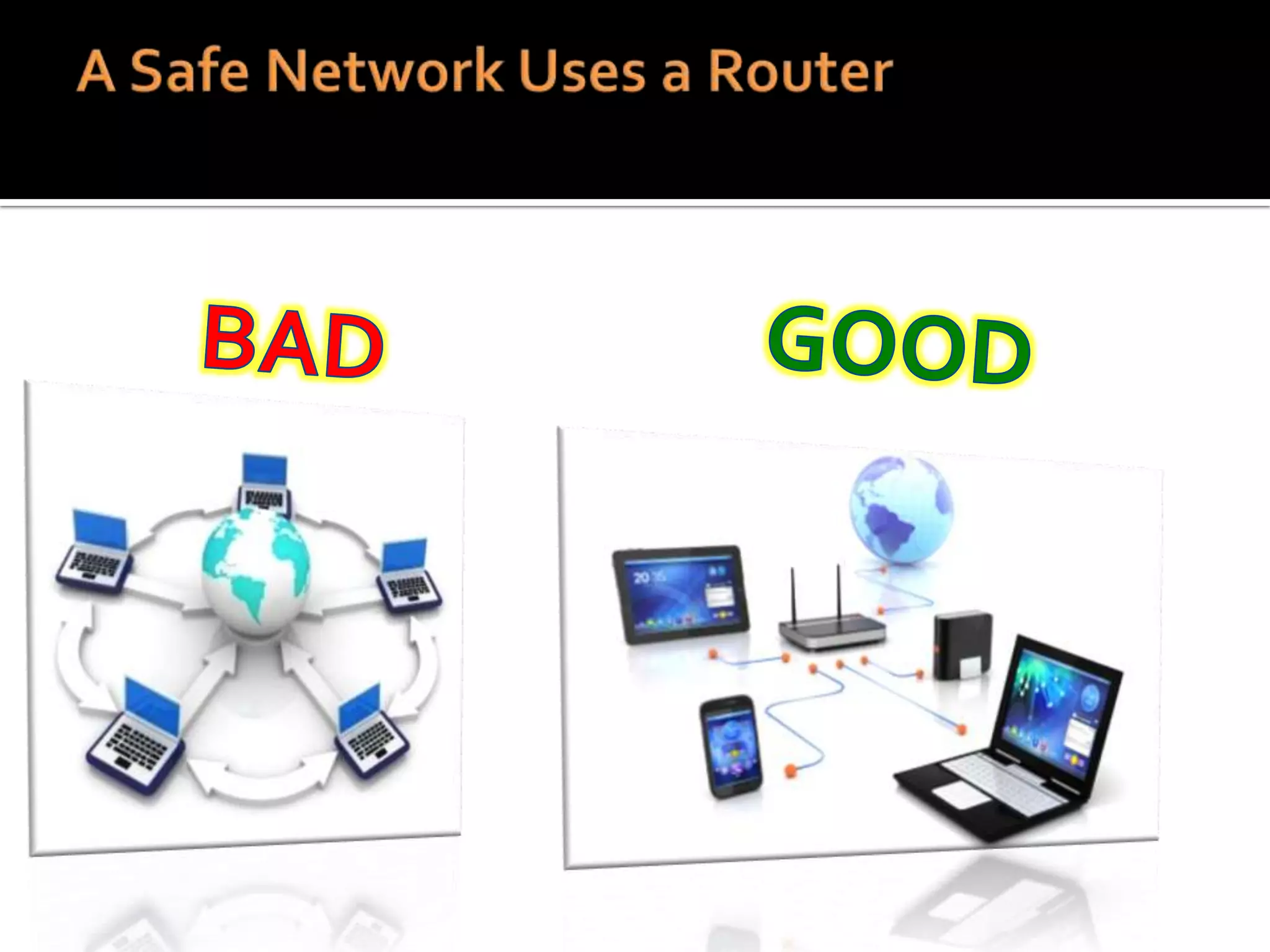
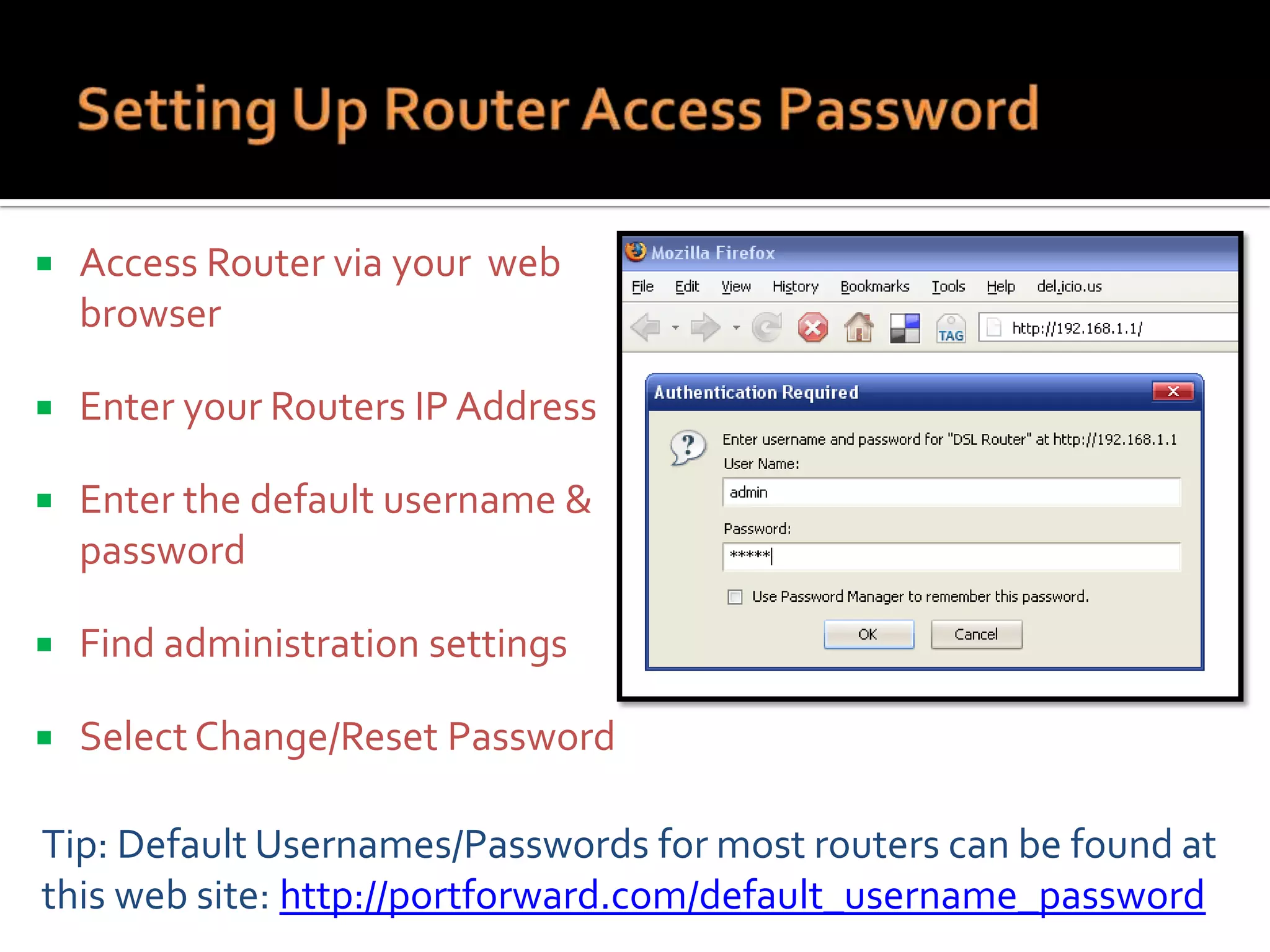
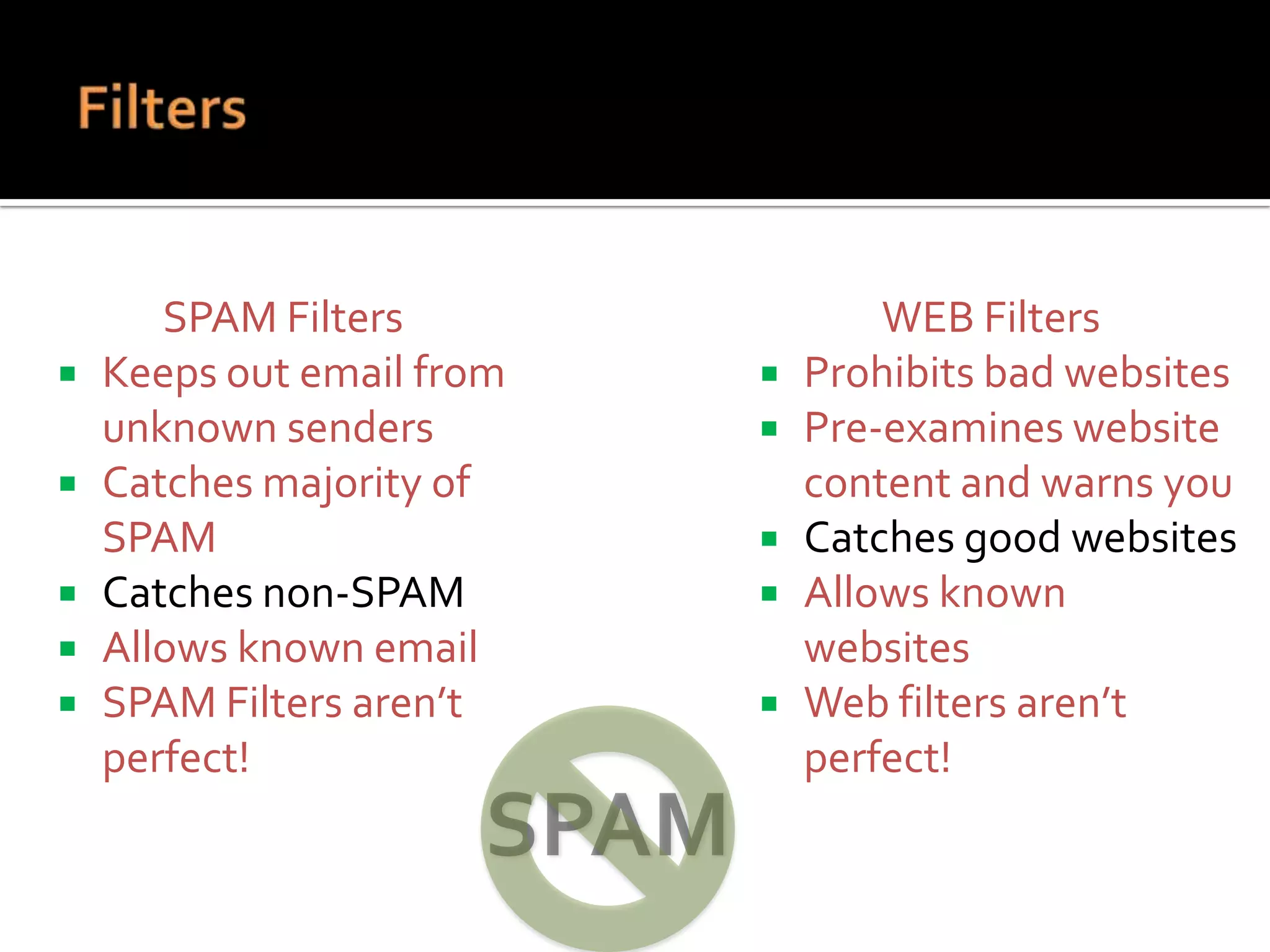
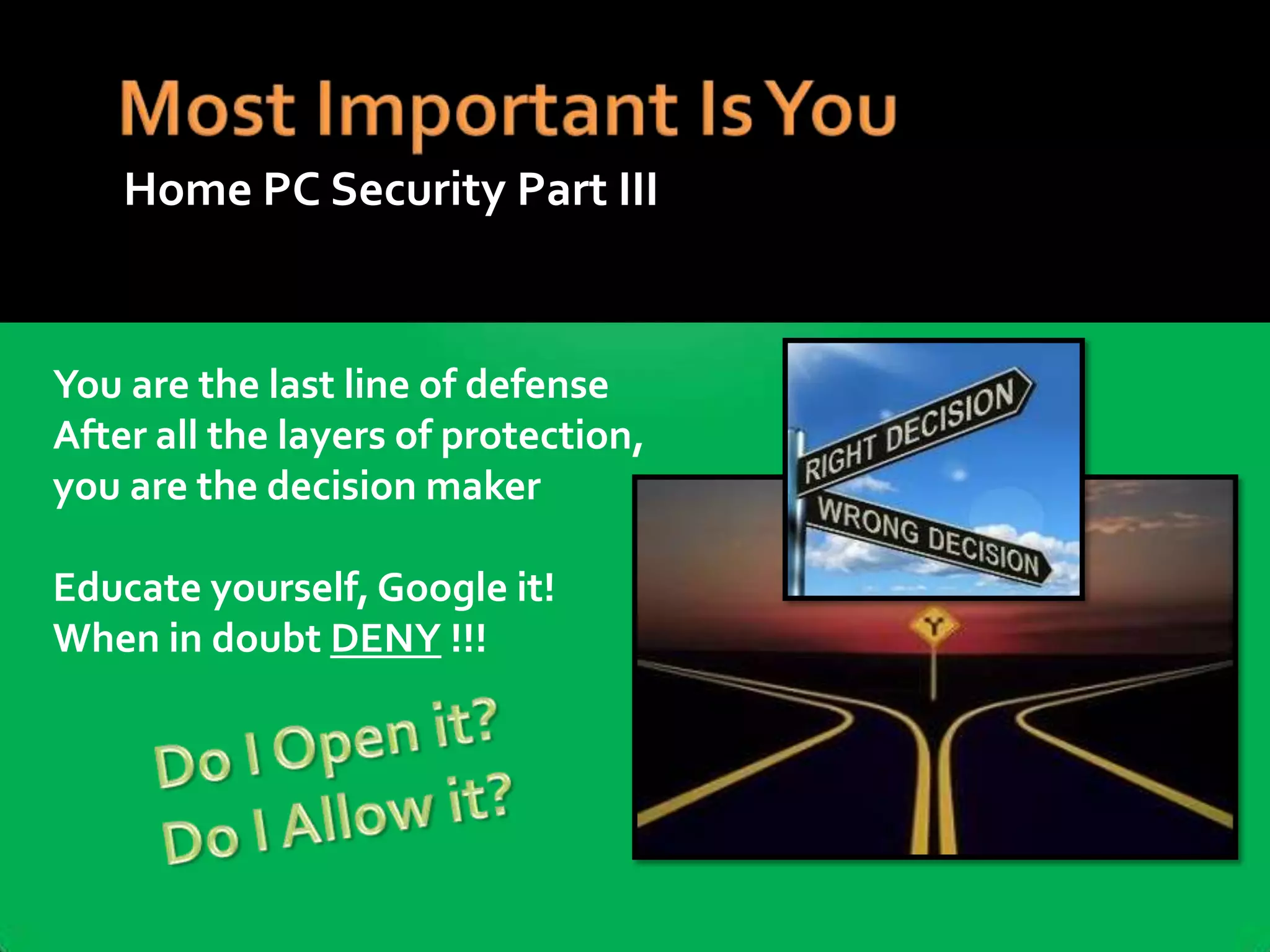
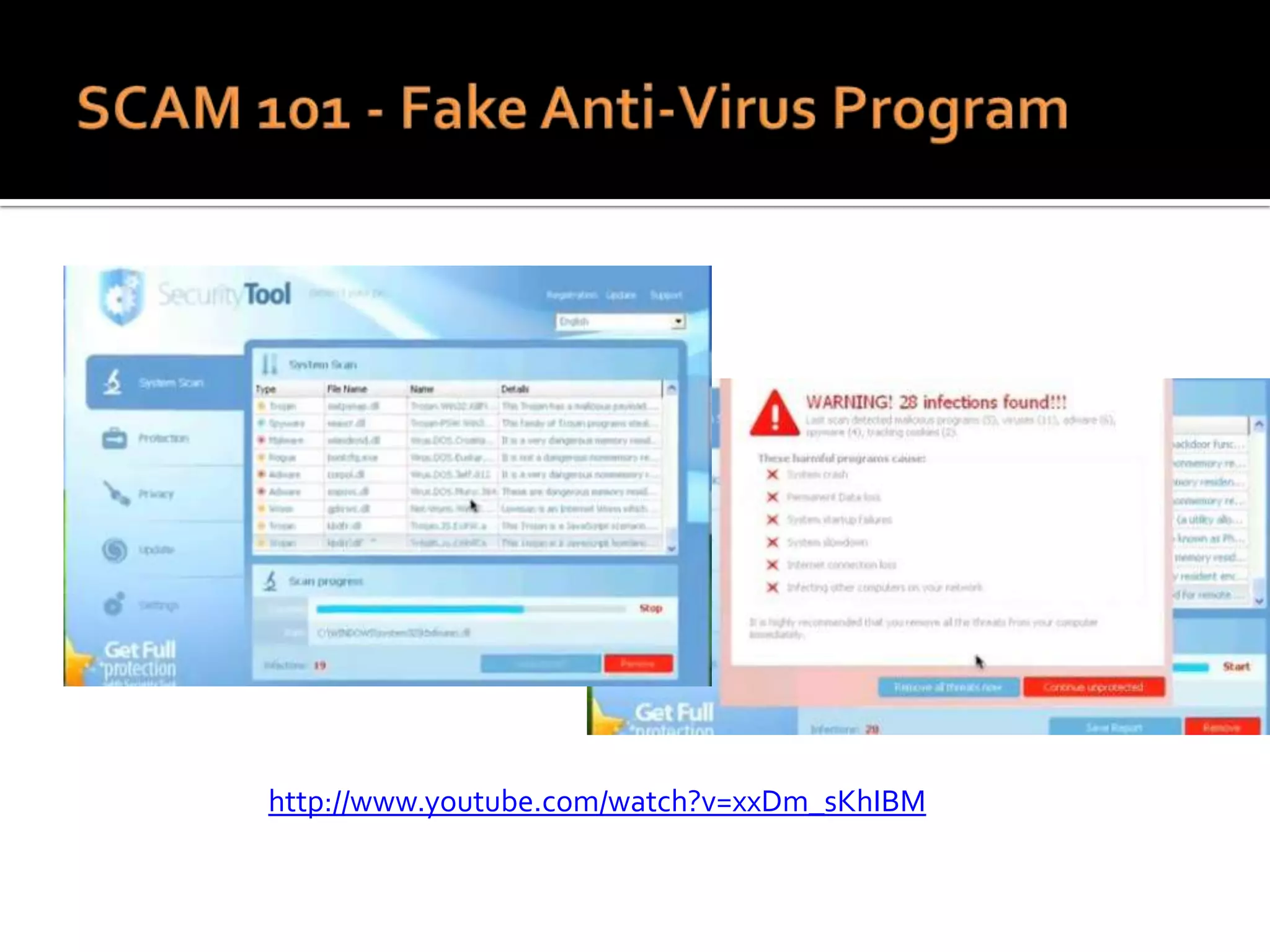
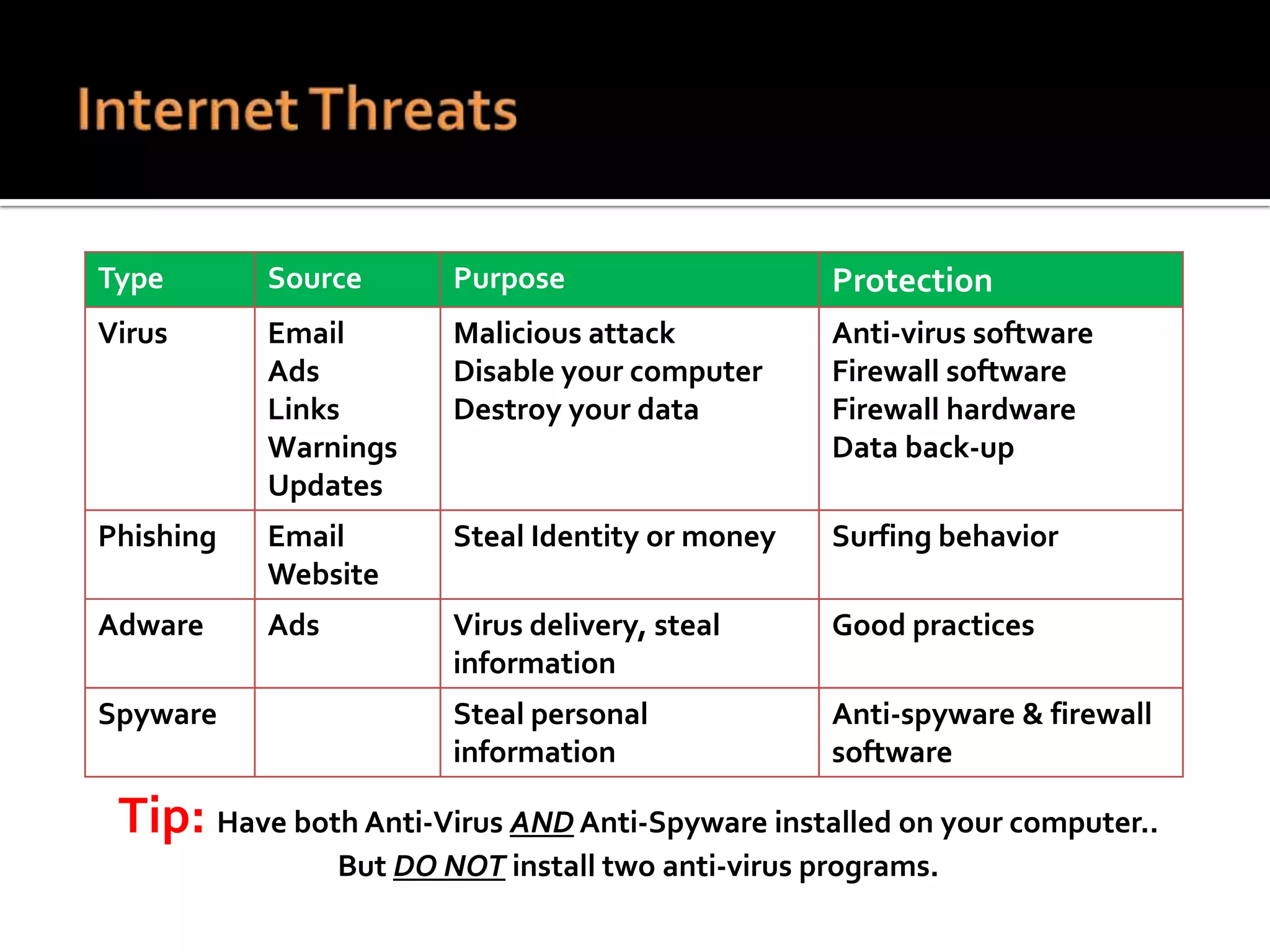
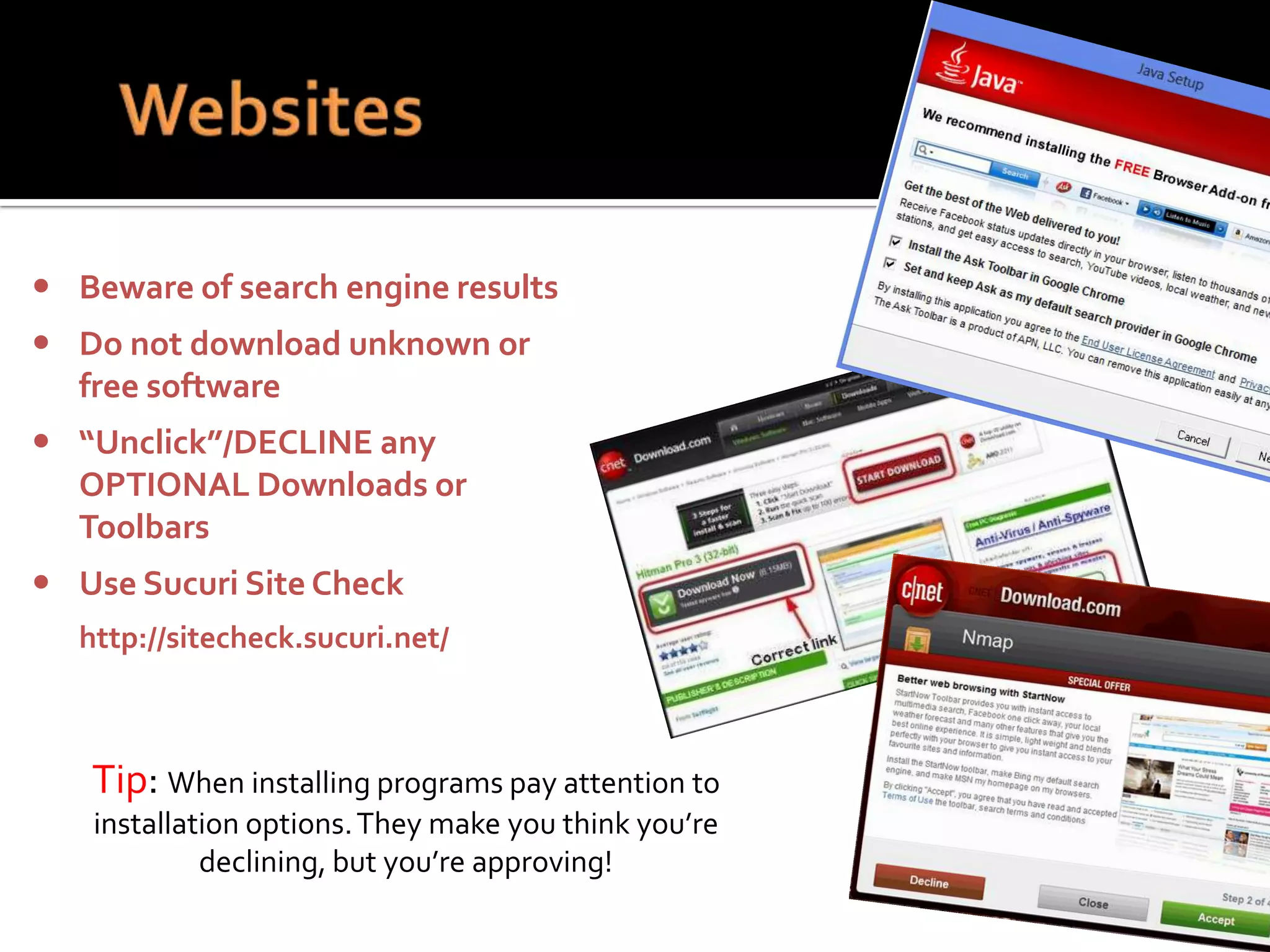
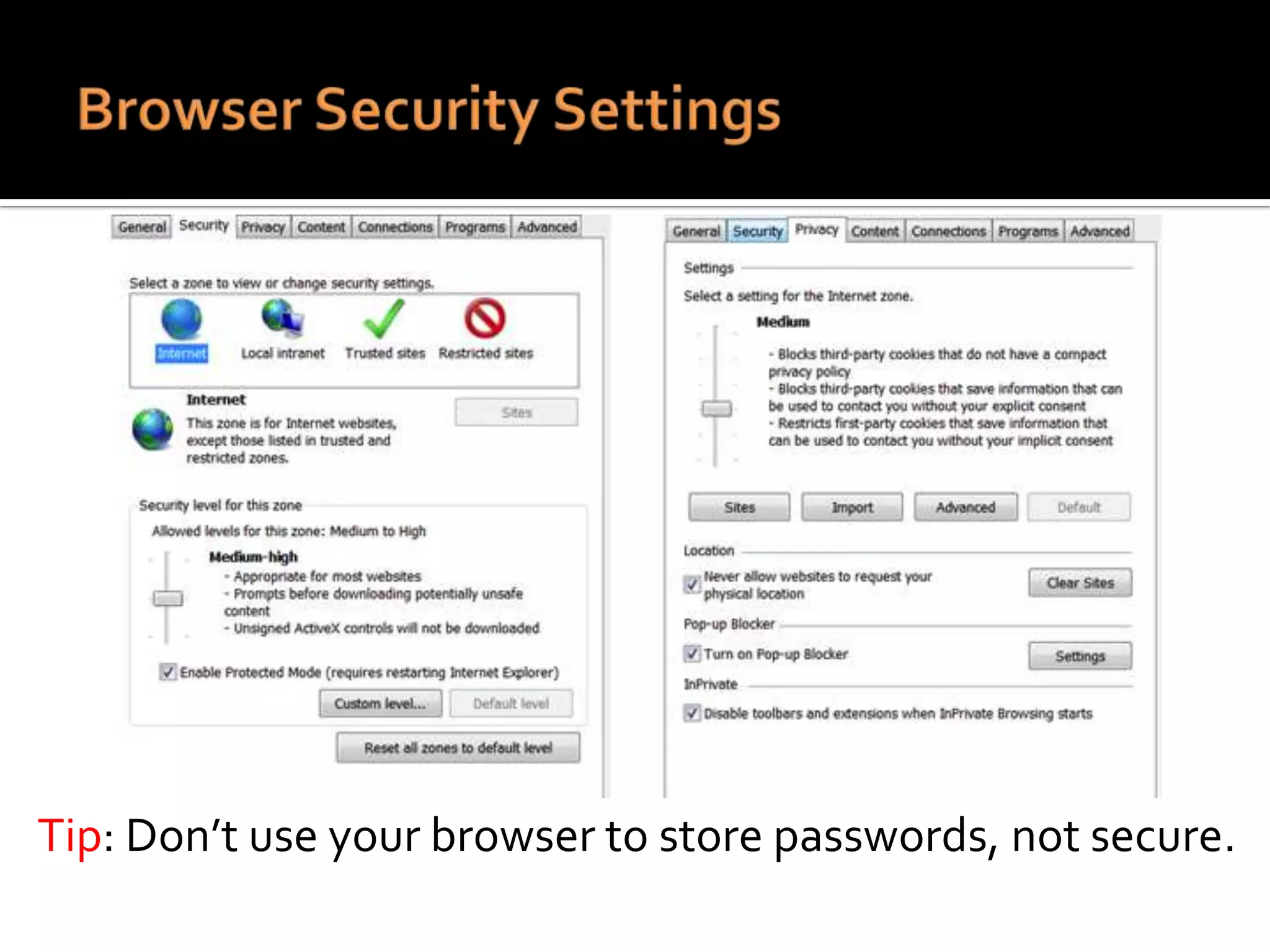
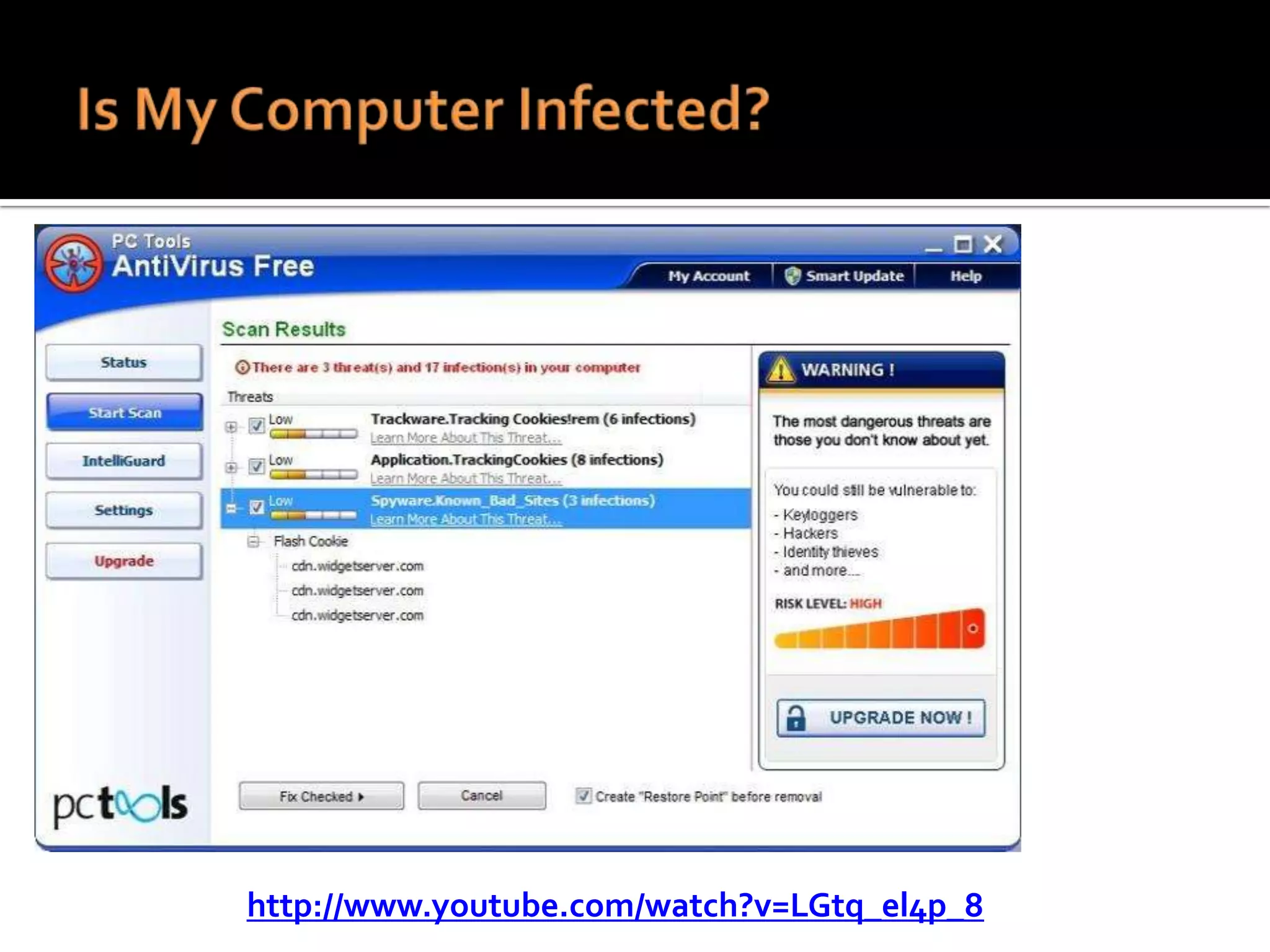
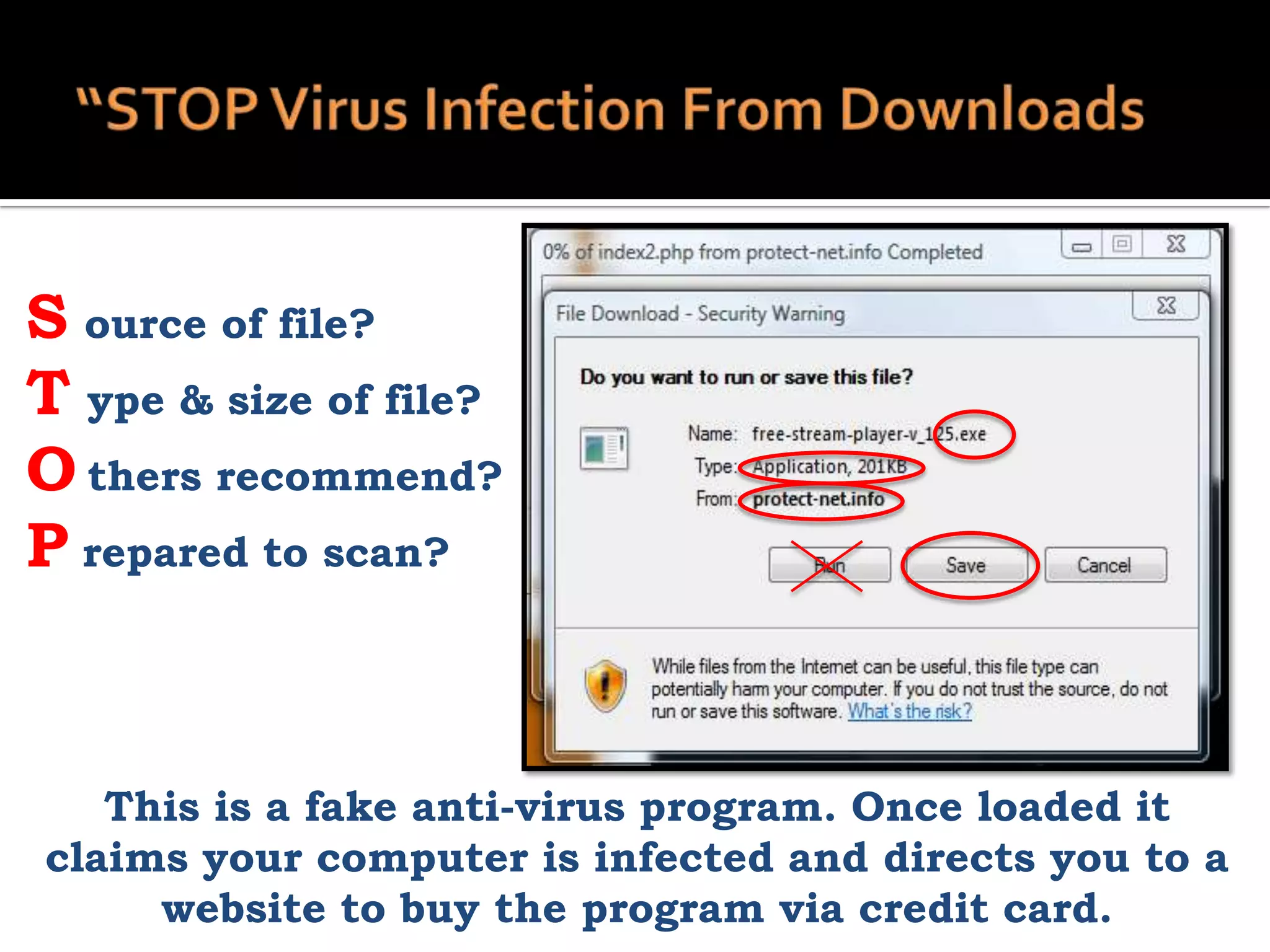
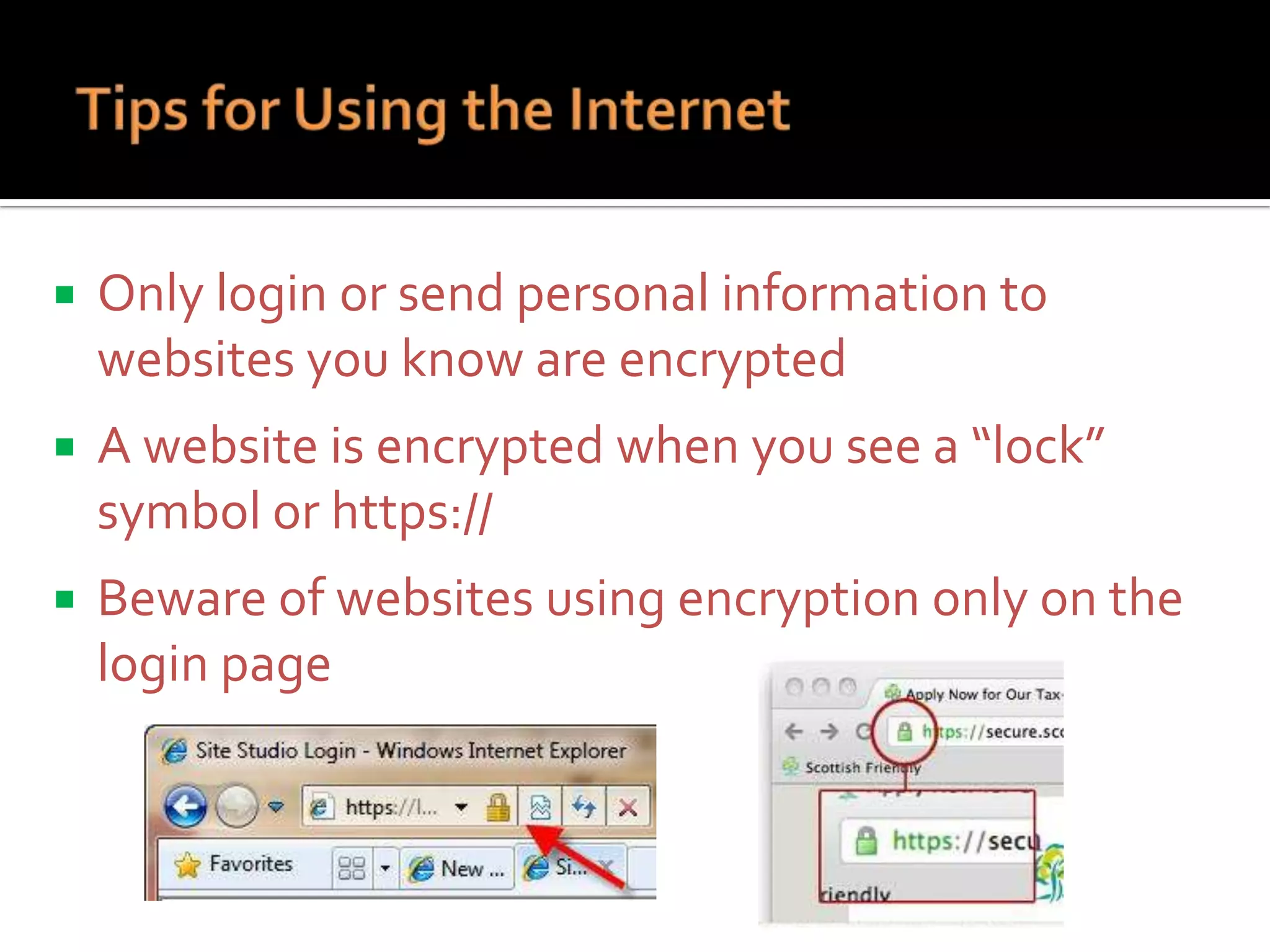
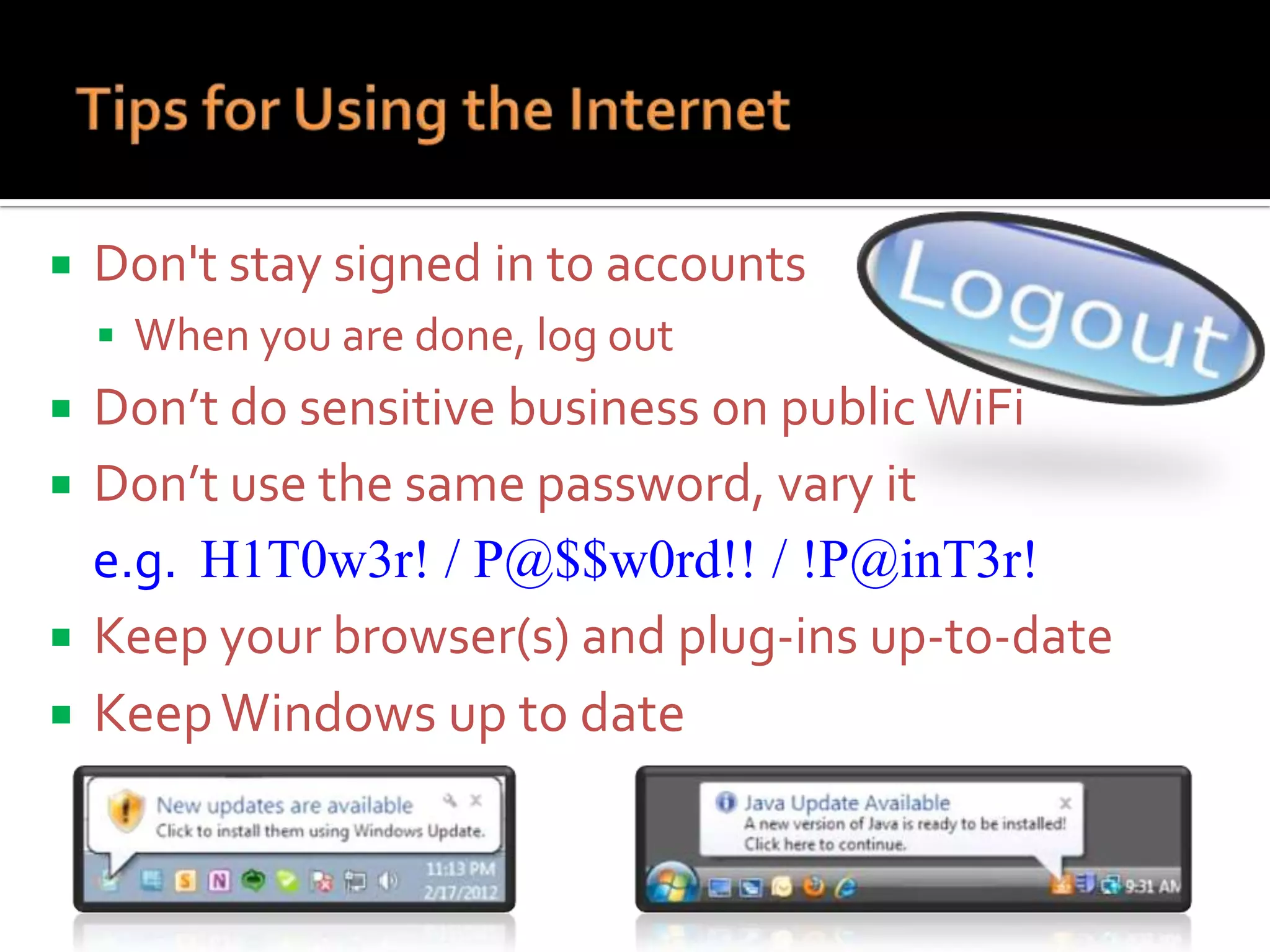
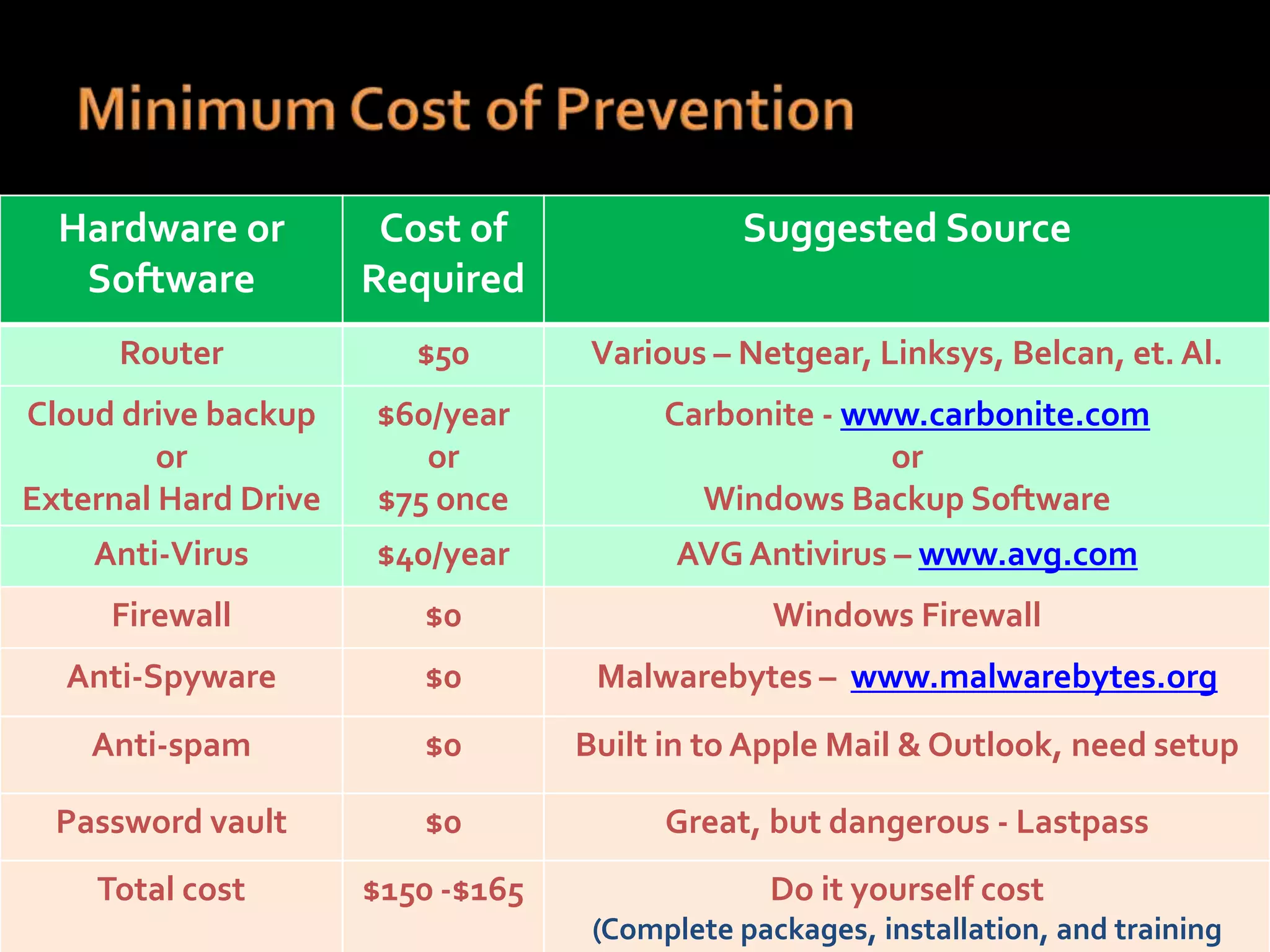
The document provides practical tips for protecting personal information, computers, and networks from cyber threats, emphasizing the importance of cybersecurity measures like strong passwords, updated software, and regular backups. It outlines various types of threats, such as viruses and phishing, and suggests appropriate protective actions, including using firewalls, anti-virus software, and password management tools. The content underscores the user's responsibility as the last line of defense against cybercrime and provides resources for further education and security measures.