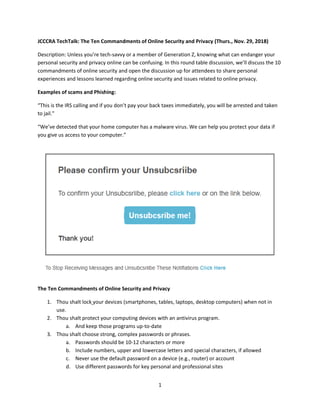
Notes to The Ten Commandments of Online Security and Privacy
- 1. 1 JCCCRA TechTalk: The Ten Commandments of Online Security and Privacy (Thurs., Nov. 29, 2018) Description: Unless you’re tech-savvy or a member of Generation Z, knowing what can endanger your personal security and privacy online can be confusing. In this round table discussion, we’ll discuss the 10 commandments of online security and open the discussion up for attendees to share personal experiences and lessons learned regarding online security and issues related to online privacy. Examples of scams and Phishing: “This is the IRS calling and if you don’t pay your back taxes immediately, you will be arrested and taken to jail.” “We’ve detected that your home computer has a malware virus. We can help you protect your data if you give us access to your computer.” The Ten Commandments of Online Security and Privacy 1. Thou shalt lock your devices (smartphones, tables, laptops, desktop computers) when not in use. 2. Thou shalt protect your computing devices with an antivirus program. a. And keep those programs up-to-date 3. Thou shalt choose strong, complex passwords or phrases. a. Passwords should be 10-12 characters or more b. Include numbers, upper and lowercase letters and special characters, if allowed c. Never use the default password on a device (e.g., router) or account d. Use different passwords for key personal and professional sites
- 2. 2 i. Financial ii. Health iii. Social Security/Medicare iv. Credit Card e. You can generate passwords at http://passwordsgenerator.net/ f. Use a password vault (mSecure, Norton Password Manager, Browser password vault?) g. Change your passwords regularly 4. Thou shalt regularly review privacy settings. a. For Facebook: https://www.facebook.com/help/325807937506242 and https://www.facebook.com/help/securitytips b. For Google: https://myaccount.google.com/privacy c. For Apple Store: https://www.apple.com/privacy/manage-your-privacy/ d. For your browser: Chrome https://support.google.com/chrome/answer/114836, Edge https://privacy.microsoft.com/en-us/windows-10-microsoft-edge-and-privacy, Firefox https://support.mozilla.org/en-US/products/firefox/privacy-and-security and Internet Explorer https://support.microsoft.com/en-us/help/17441/windows-internet-explorer- change-reset-settings#1TC=windows-7 e. Twitter: https://help.twitter.com/en/safety-and-security/account-security-tips 5. Thou shalt always ensure your internet connection is safe and secure. a. Use a virtual private network (VPN) when on public WifI i. https://www.f-secure.com/en_US/web/home_us/freedome $$4.17-$6.67 monthly or $49.99-$79.99 yearly charge (depending on number of devices: 3-7) ii. https://us.norton.com/wifi-privacy $7.99 monthly, $39.99 yearly (jumps to $79.99 after first year) iii. 10+ Free VPN Software Programs https://www.lifewire.com/vpn-client-and- server-software-downloads-818192 b. Install and use a firewall on all computing devices i. A firewall is a barrier or shield that is intended to protect your PC, tablet, or phone from the data-based malware dangers that exist on the Internet. ii. Windows, Norton and most anti-virus programs include a firewall iii. Be sure your firewall is enabled (Windows XP by default is not) c. If a company (e.g., credit card) offers login or activity notifications, enroll! 6. Thou shalt practice safe browsing. a. Be careful how much personal information you post online b. Avoid click bait and dubious websites c. Be wary of links in unsolicited email and posts (very risky) d. Be wary of unanticipated file attachments from friends, financial institutions, credit card companies and so on i. Do not click links in email messages from companies or financial institutions ii. Instead go to their known web address e. Using a banking app is typically safer than using their website 7. Thou shalt make online purchases only from secure sites.
- 3. 3 a. Look for https:// prefix to web addresses b. Look for the locked padlock icon preceding the web address in your browser c. An unlocked padlock means communications are not secure and protected by a secure sockets layer (SSL). d. SSL means communications between your web browser and the web server is encrypted 8. Thou shalt use great discretion when downloading files, apps and documents. a. Download apps from Google Play or the Apple App Store only b. Exceptions: apps from secure and known sites 9. Thou shalt use two-factor authentication when available. a. Microsoft: https://support.microsoft.com/en-us/help/12408/microsoft-account-how-to- use-two-step-verification b. Google: https://support.google.com/a/answer/175197 c. Facebook: https://www.facebook.com/help/148233965247823 d. Apple: https://support.apple.com/en-us/HT204915 e. Most financial institutions offer it f. Many online accounts offer it 10. Thou shalt actively keep abreast of online scams and keep your guard up. Definitions Phishing: A scam by which an Internet user is duped (as by a deceptive e-mail message) into revealing personal or confidential information which the scammer can use illicitly. A common phishing scam involves sending e-mails that appear to come from banks requesting recipients to verify their accounts by typing personal details, such as credit card information, into a Web site that has been disguised to look like the real thing. Malware = Malicious Software: Software designed to interfere with a computer's normal functioning. Ransomware: Malware that requires the victim to pay a ransom to access encrypted files. In September of 2013, security for small accounting offices changed forever with the appearance of a new class of threats called ransomware. … you open a file attached to an innocent-looking e-mail, and the program encrypts key files and drives so they cannot be accessed. The files are locked until you pay a ransom. — Dave Mcclure With ransomware, a hacker (electronically) slips into a system, then puts encryption controls in place that locks users out. The hackers then demand money to "unlock" the data. — Elizabeth Millard Notes Many phishing schemes start with something looking very innocent and official but lead unassuming users to websites designed to collect the personal information from you. If you receive an email from
- 4. 4 any websites asking for personal information, open a new tab and go direct to known web address for the company instead of clicking links within the email. Legitimate online services should never ask you for your login credentials (username and password), social security number, Medicare number, or other personal data (address, maiden name, mother’s maiden name, and so on). Sources https://usa.kaspersky.com/resource-center/preemptive-safety/top-10-internet-safety-rules-and-what- not-to-do-online https://securingtomorrow.mcafee.com/consumer/consumer-threat-notices/10-tips-stay-safe-online/ https://securingtomorrow.mcafee.com/ https://www.webroot.com/blog/2014/08/06/8-tips-stay-safe-online/ https://blog.f-secure.com/10-things-we-can-all-do-to-make-a-safer-internet/ https://www.fbi.gov/scams-and-safety common fraud schemes, on the Internet e-scams, about protecting your kids https://blog.f-secure.com/online-banking-tips-3-security-essentials-you-need-to-know/ https://blog.f-secure.com/at-least-5-things-you-shouldnt-share-on-the-internet/ Definitions from https://www.merriam-webster.com https://staysafeonline.org/stay-safe-online/managing-your-privacy/privacy-tips-teens/ https://staysafeonline.org/stay-safe-online/managing-your-privacy/privacy-tips-older-adults/
