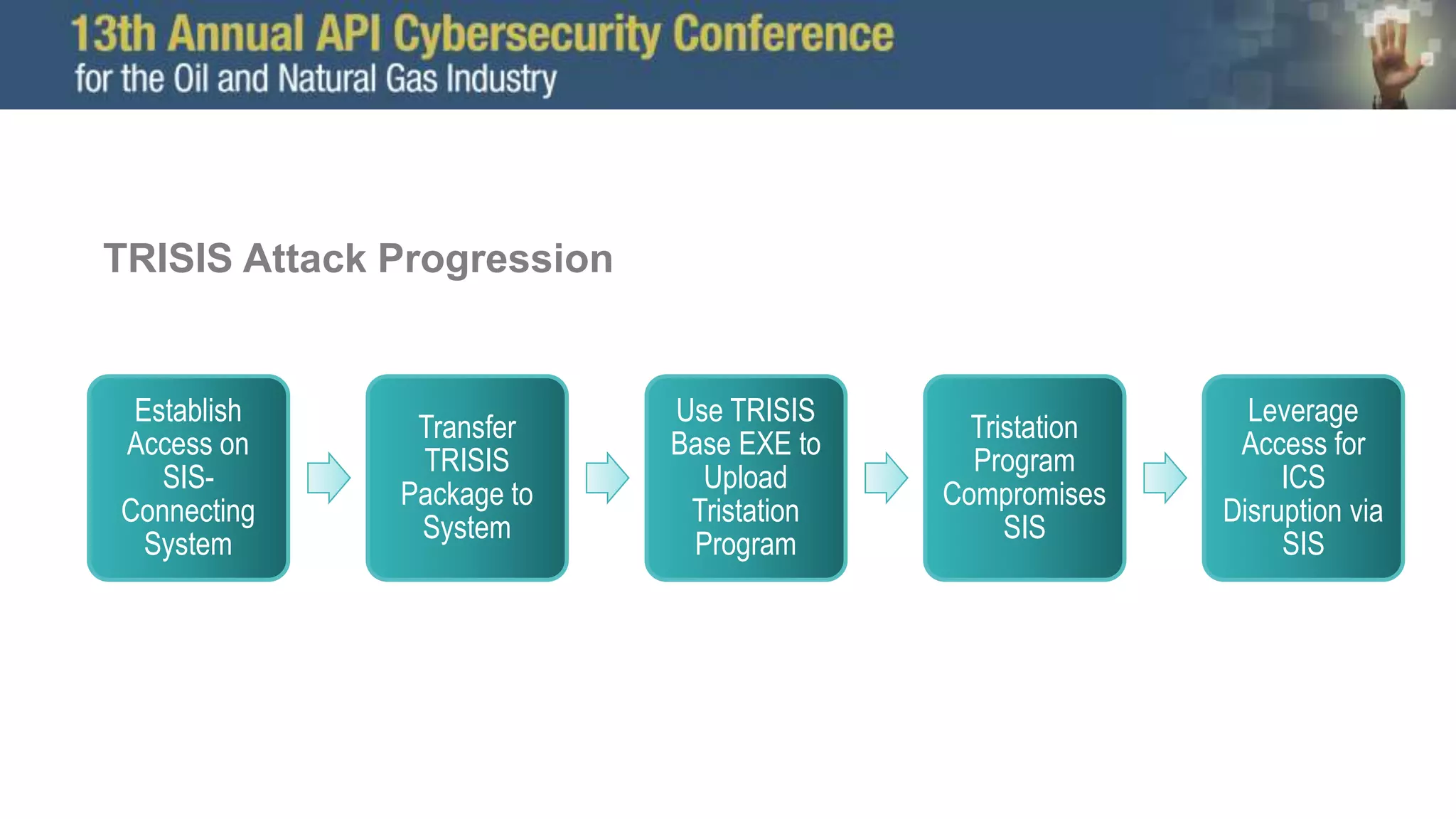
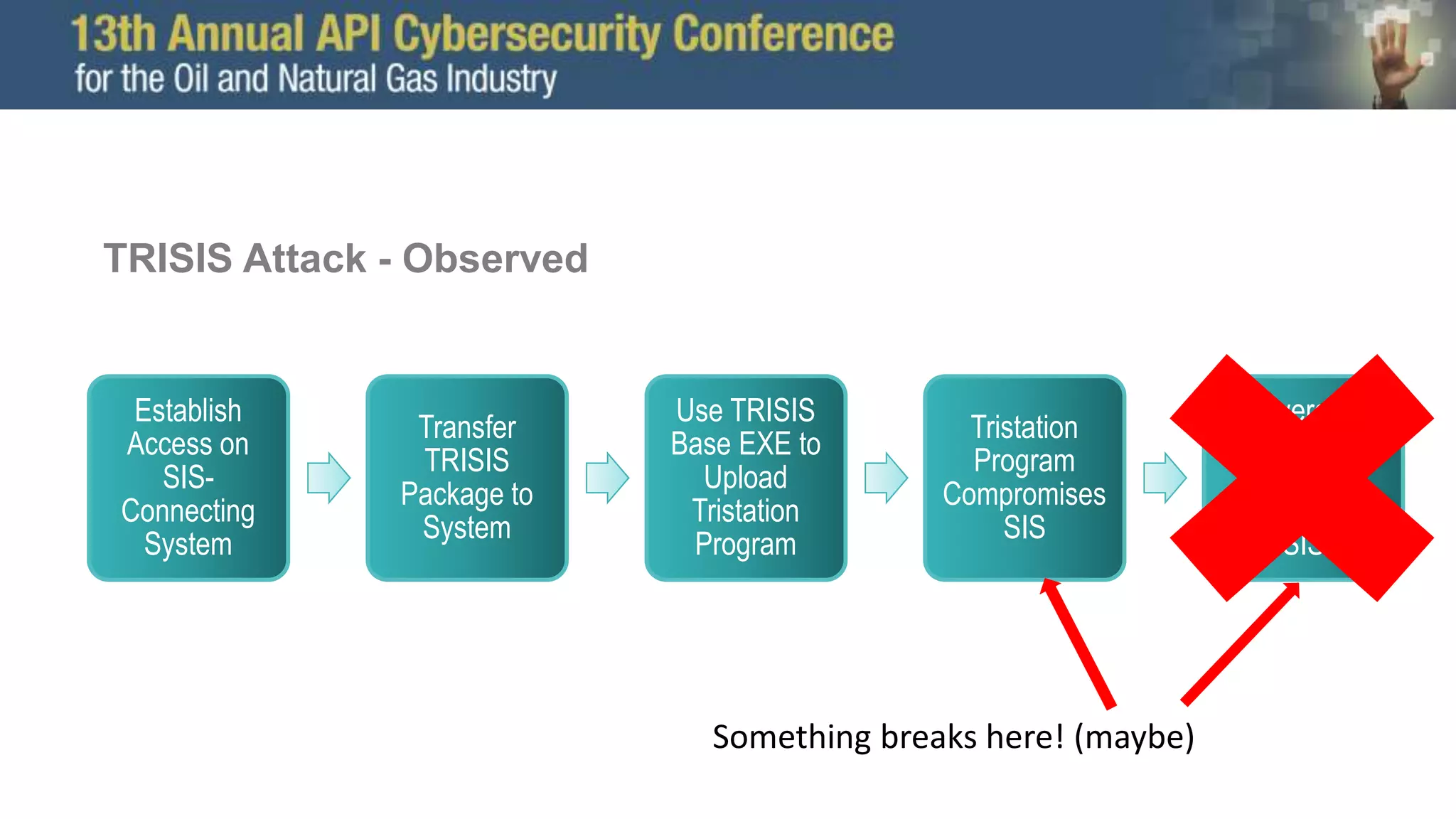
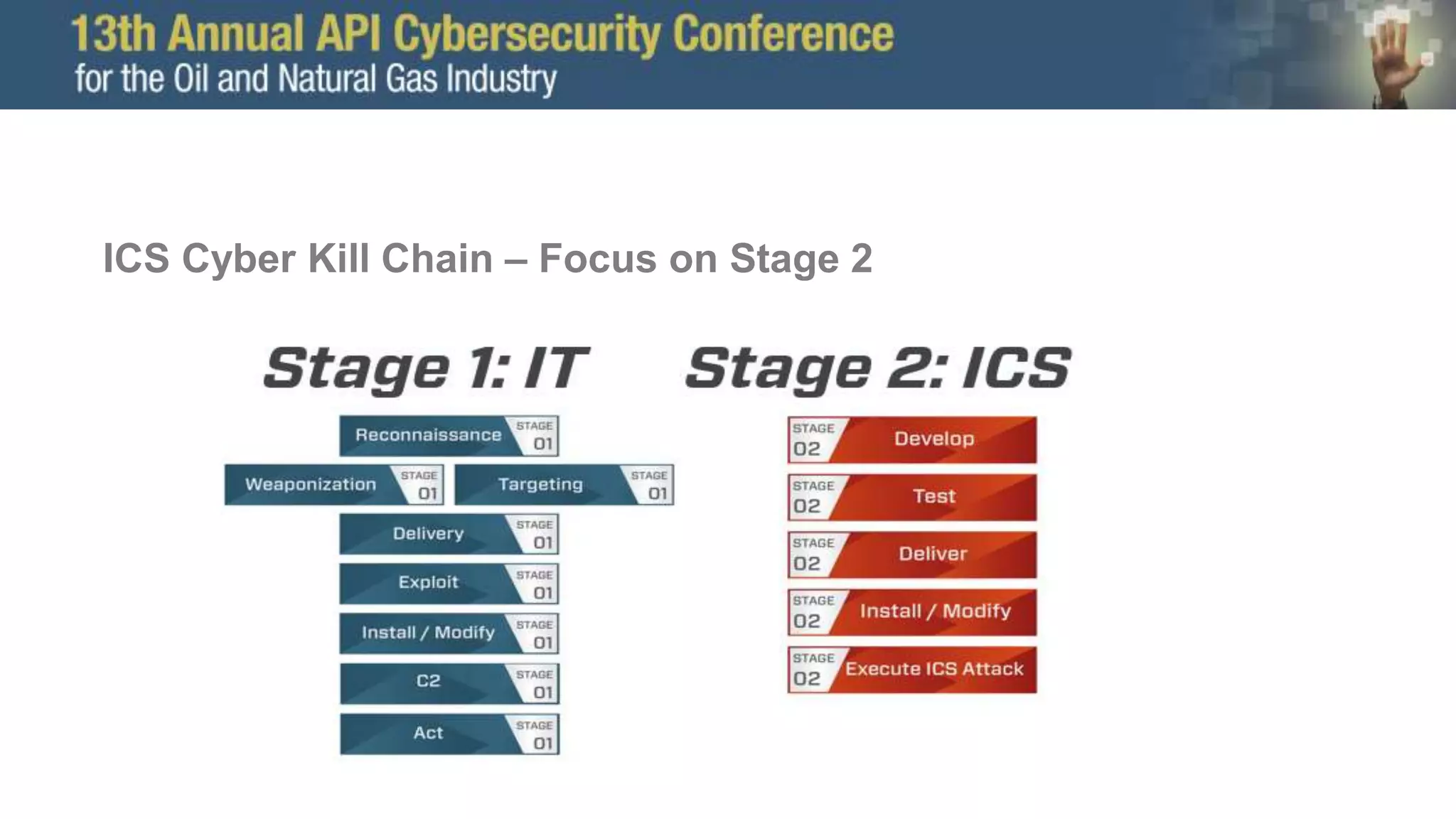
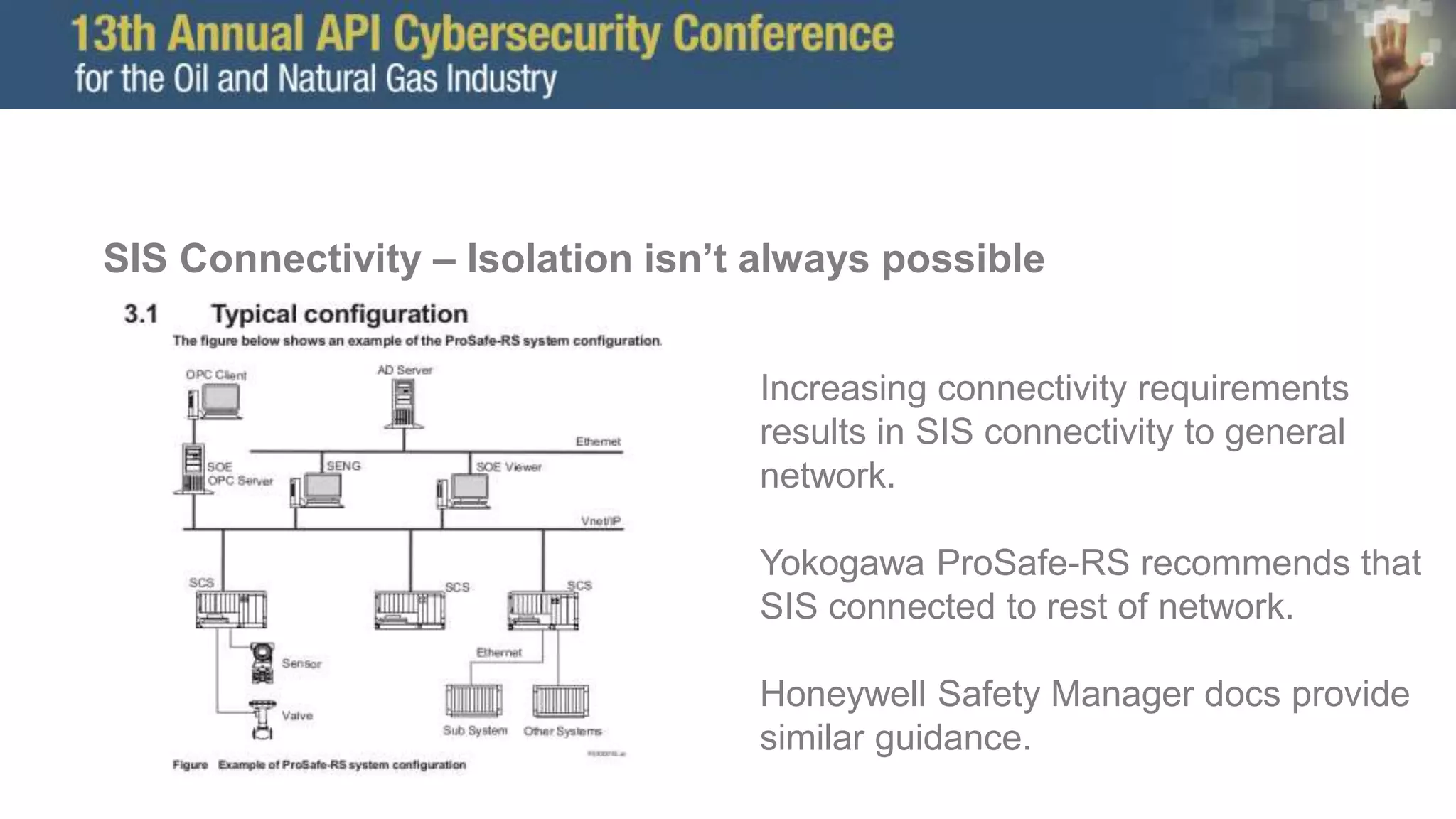
The document discusses the Trisis malware attack on a safety system at a gas facility in Saudi Arabia in 2017, highlighting its impact and the ongoing threat from the Xenotime group which has expanded its targeting. It offers defensive recommendations for industrial control systems (ICS), emphasizing the importance of monitoring, isolation, and robust network defenses against cyber threats. Additionally, it stresses the need for effective incident response capabilities, including forensic analysis and system recovery planning.