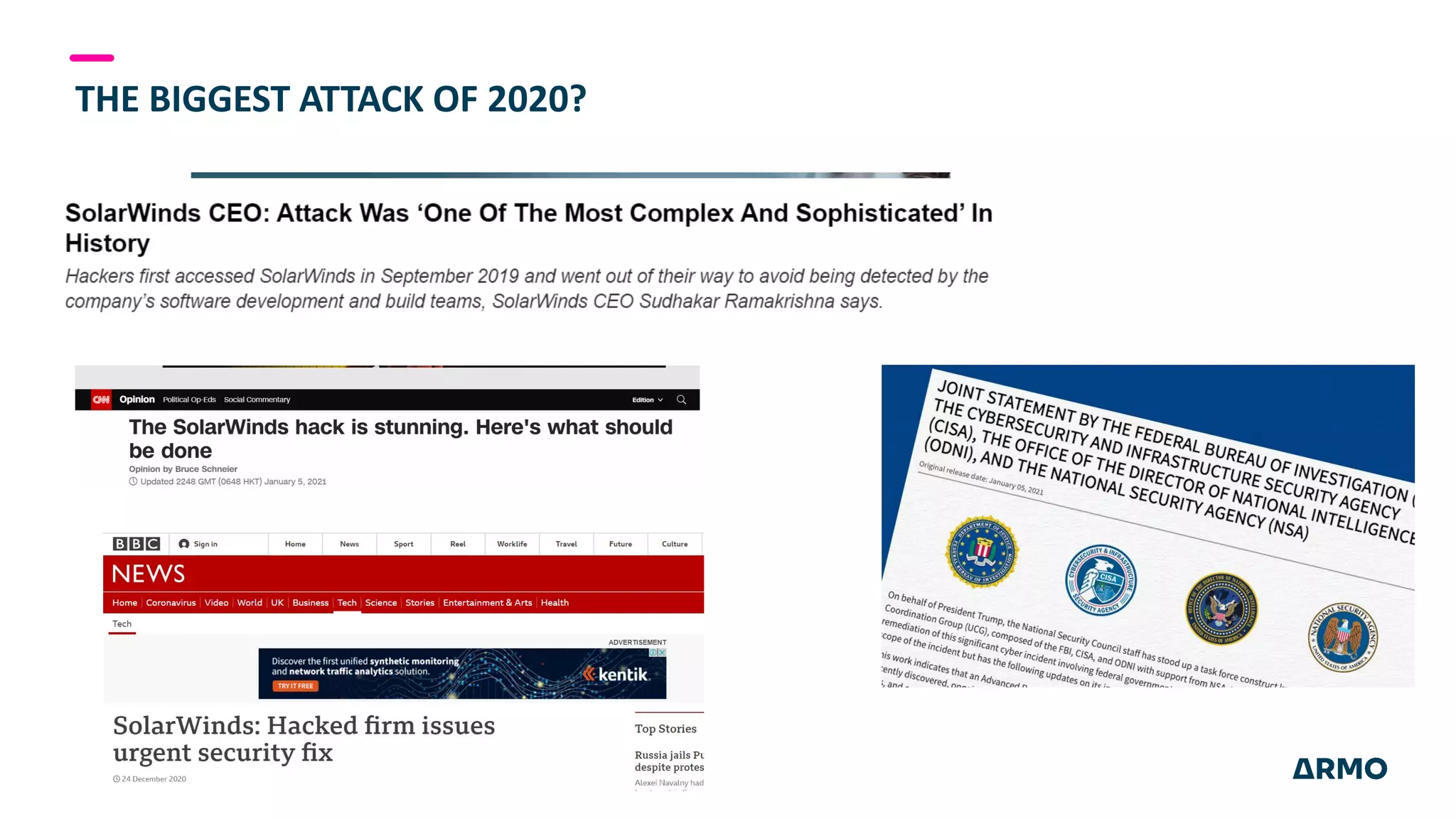
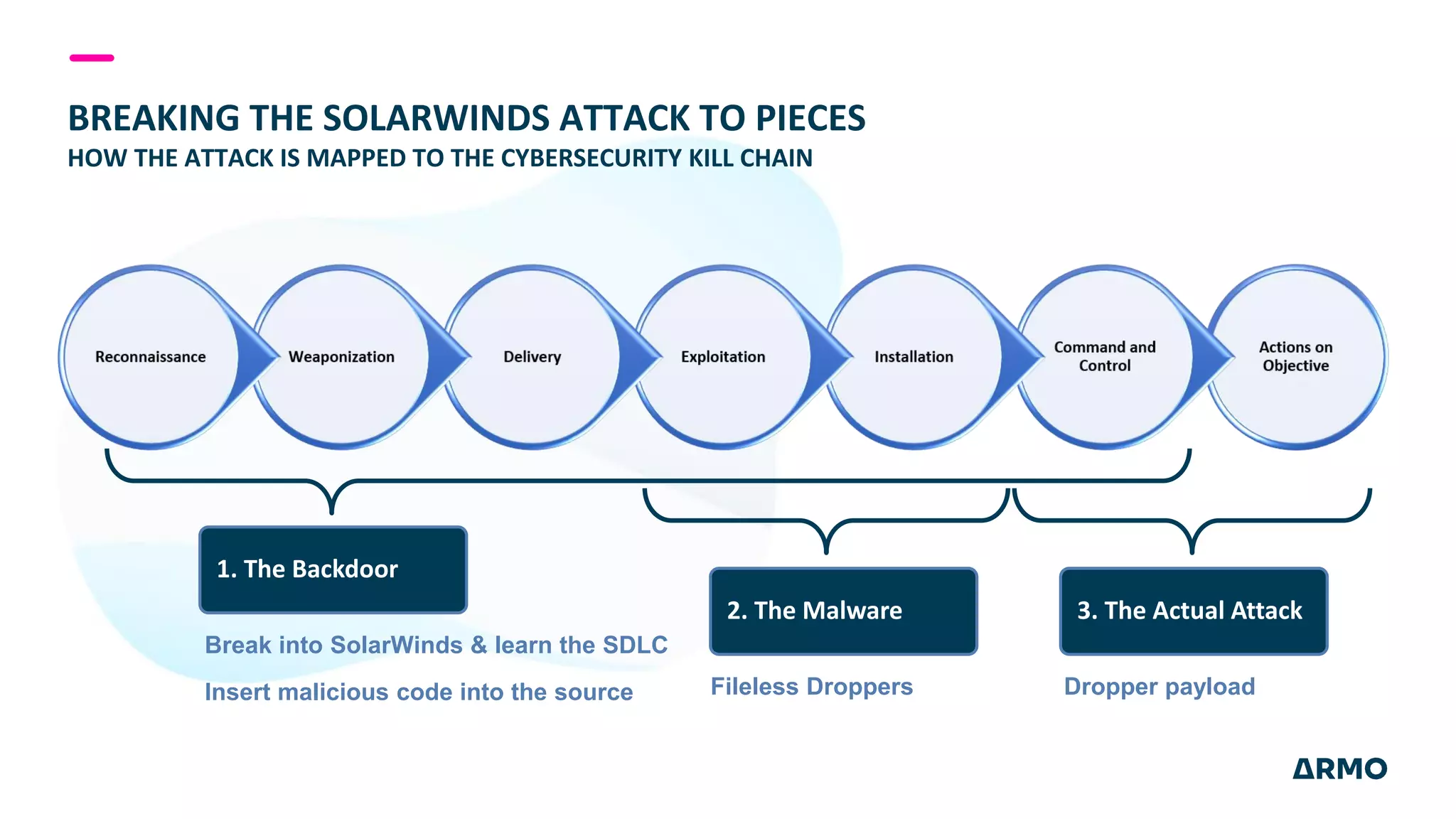
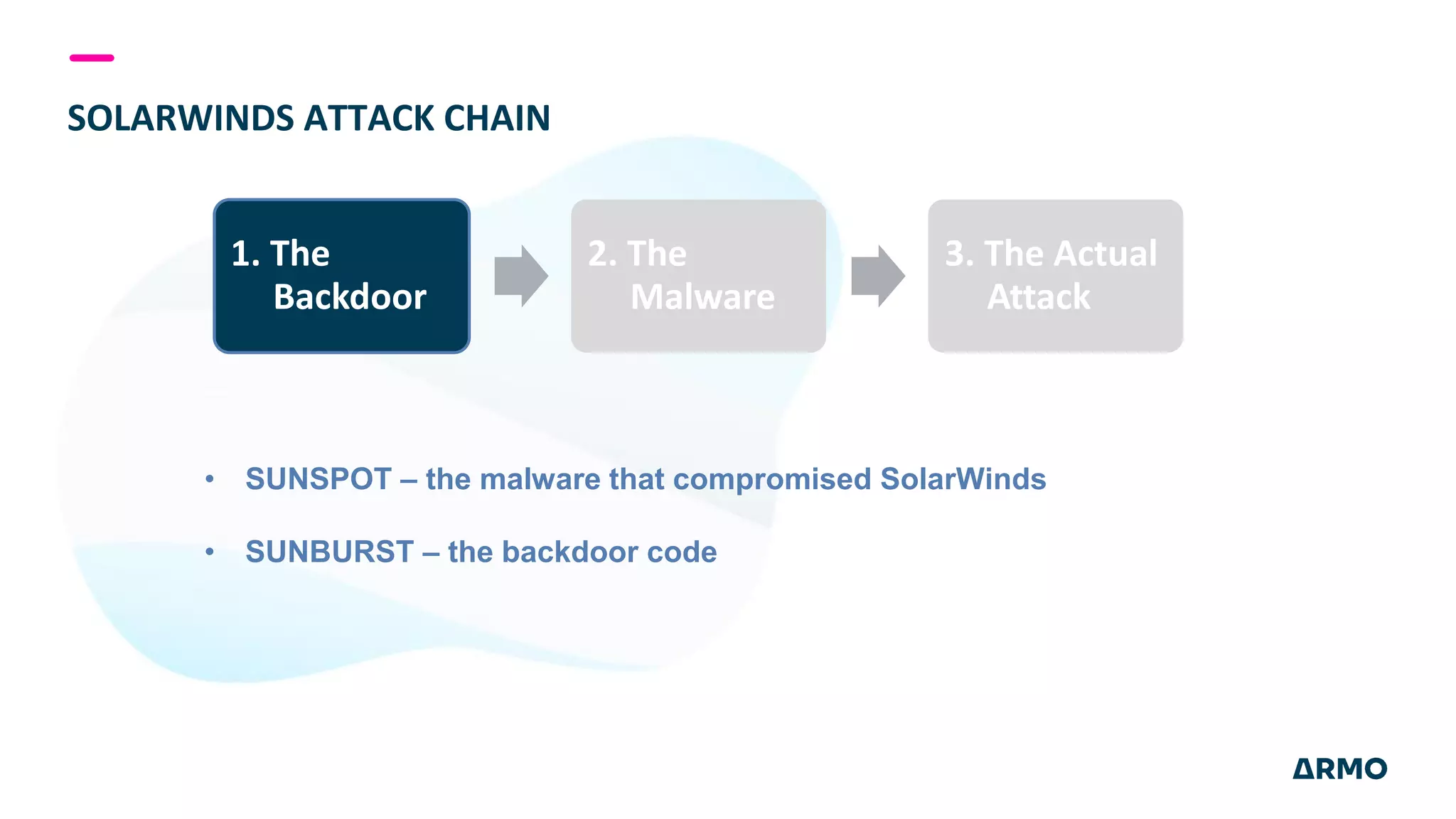
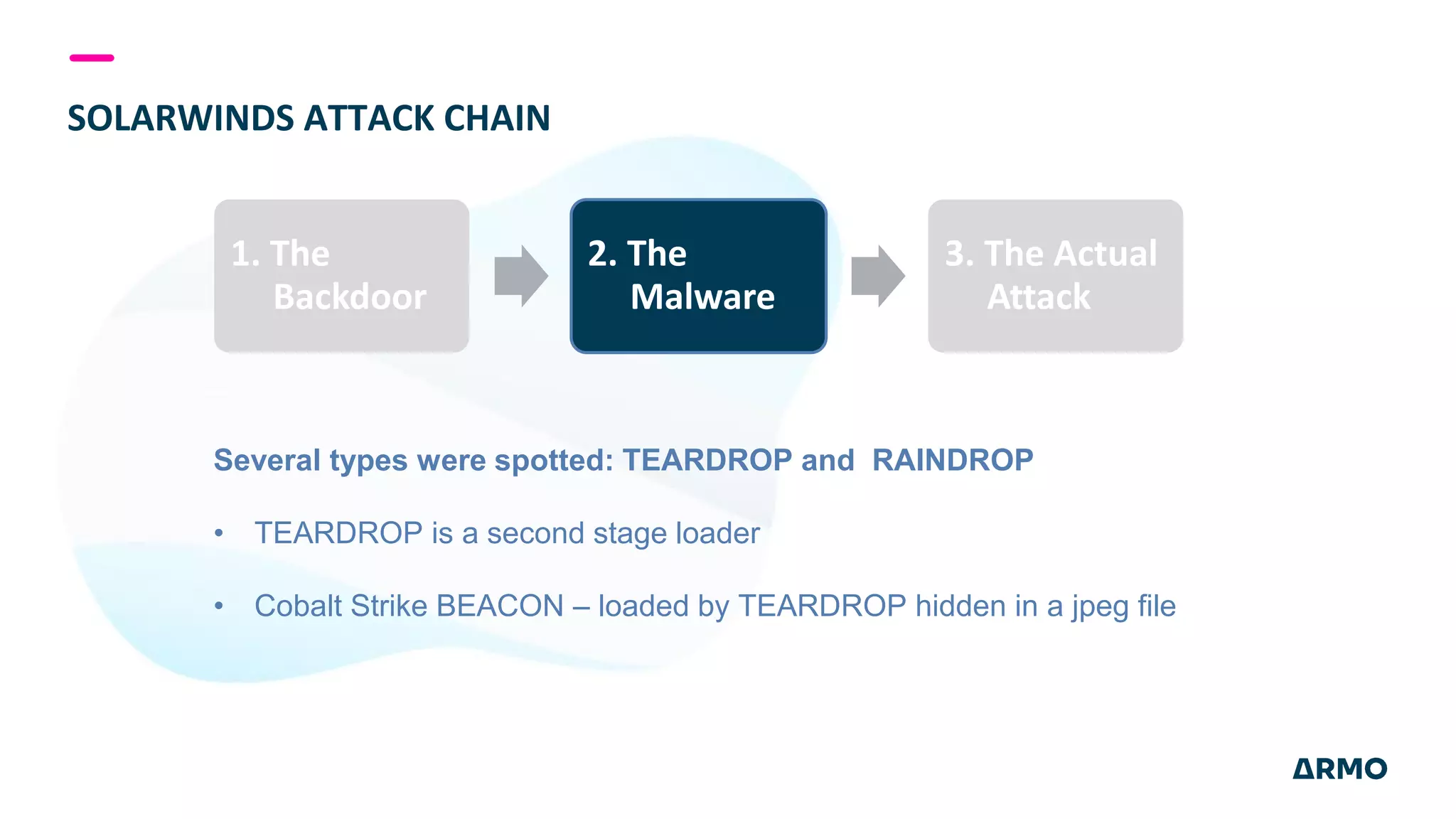
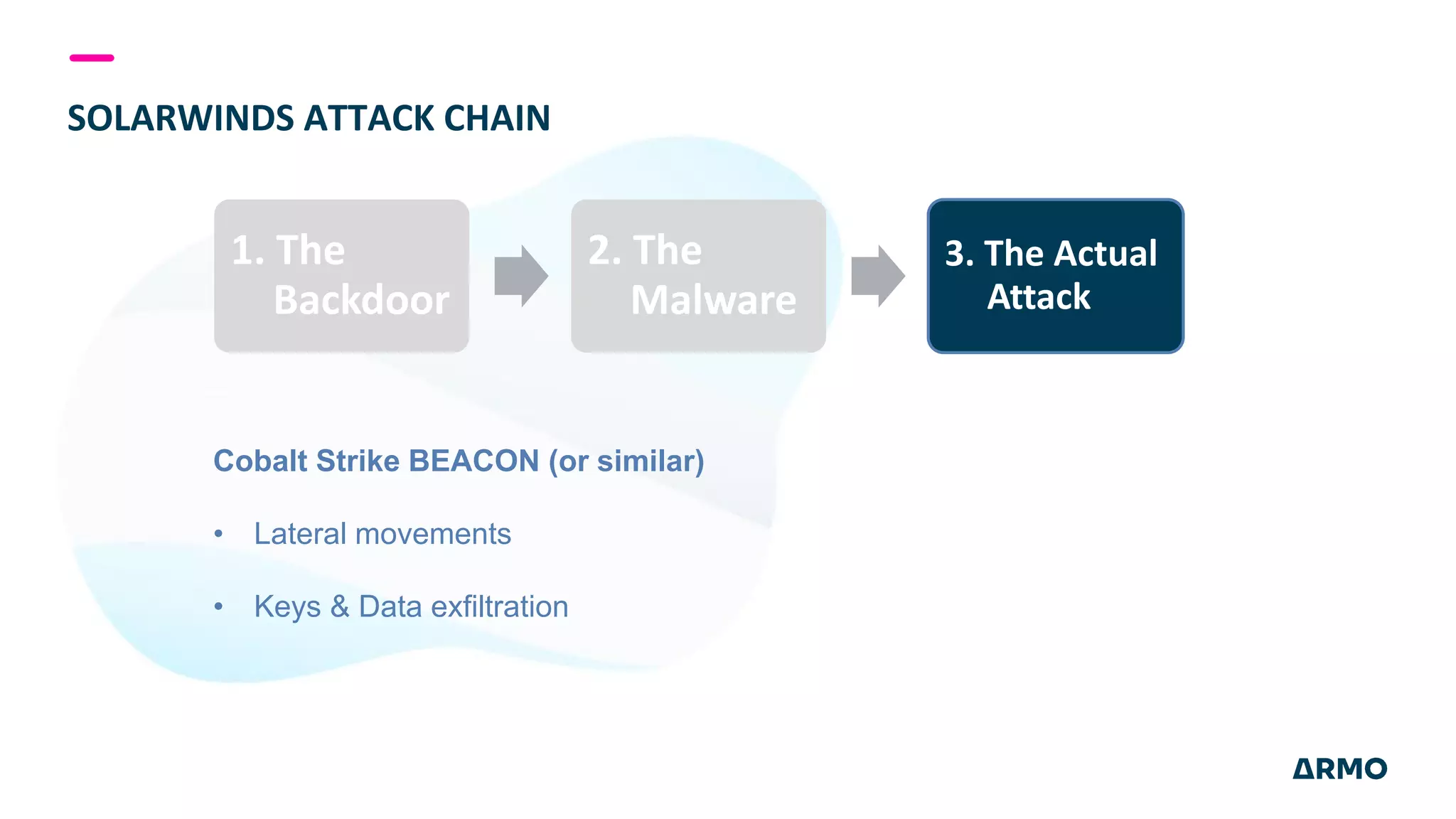
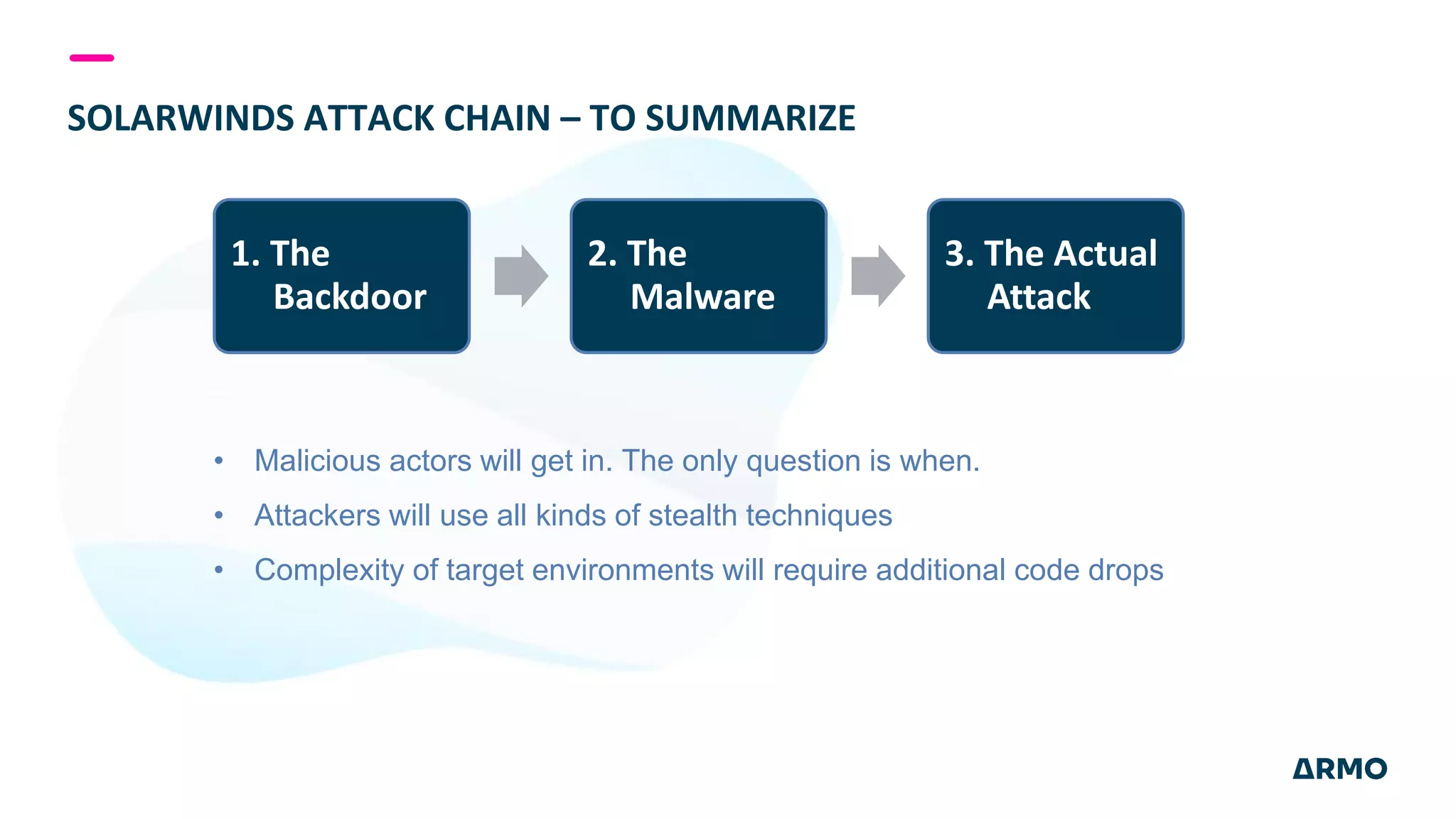
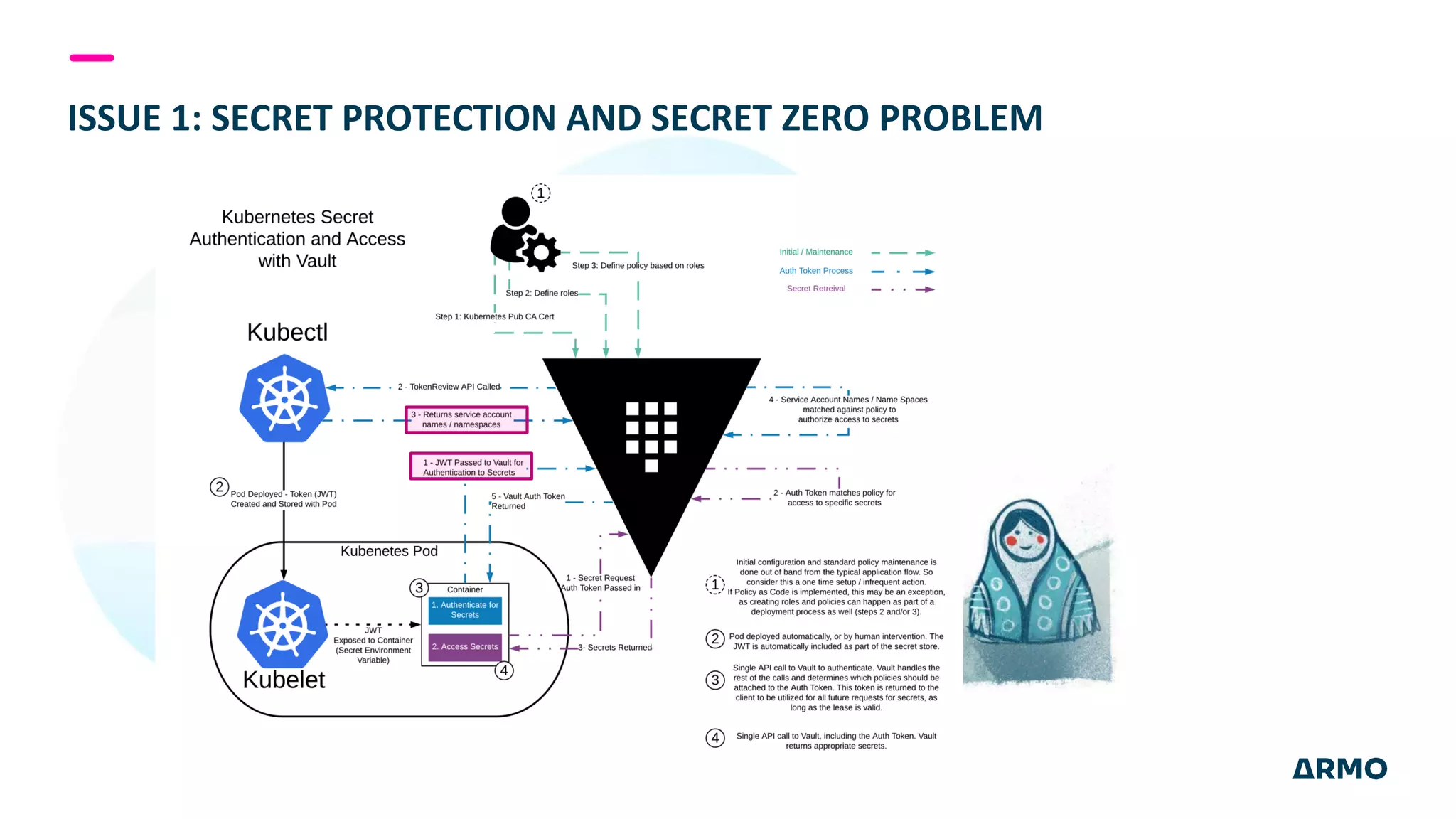
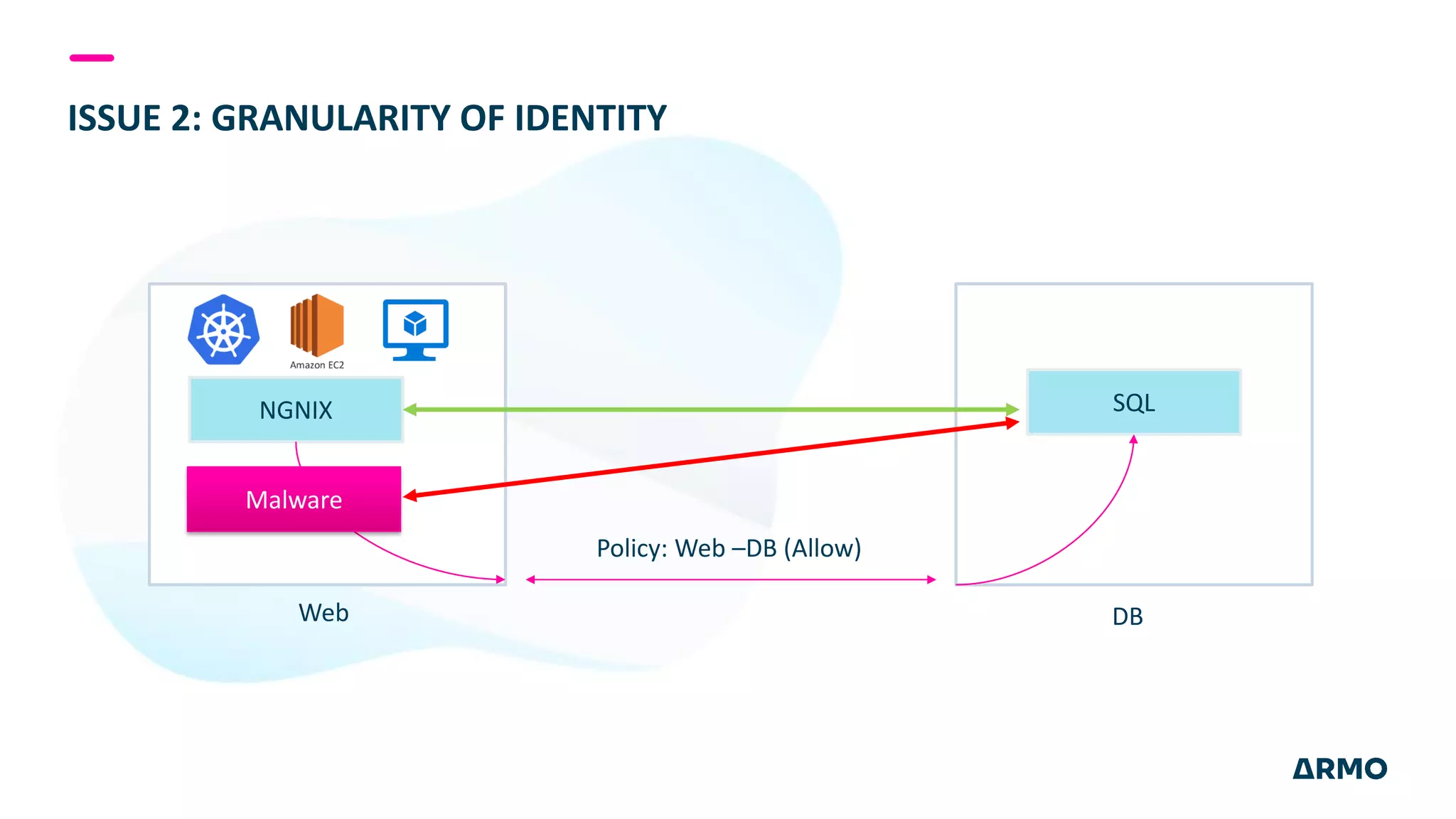
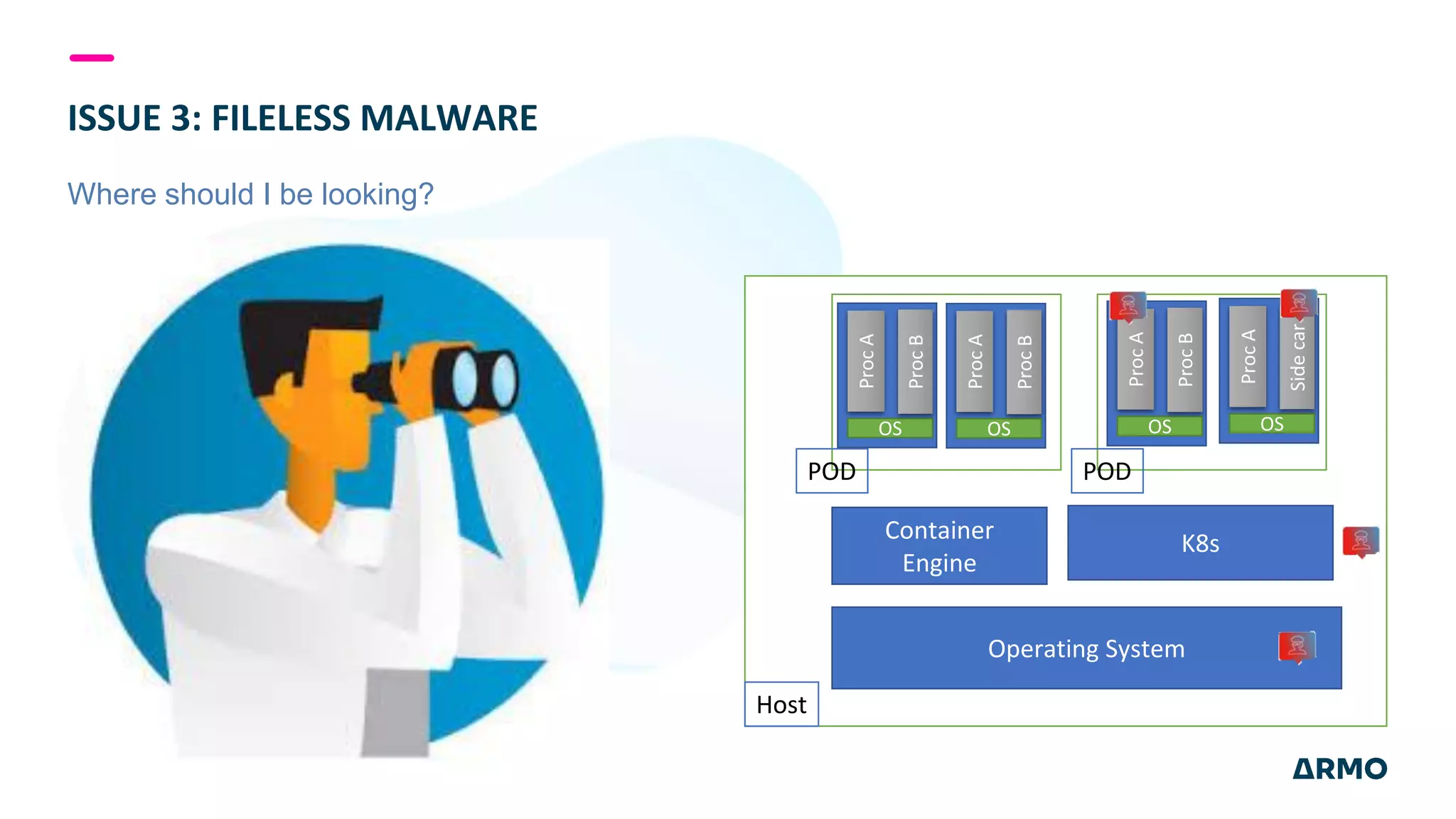
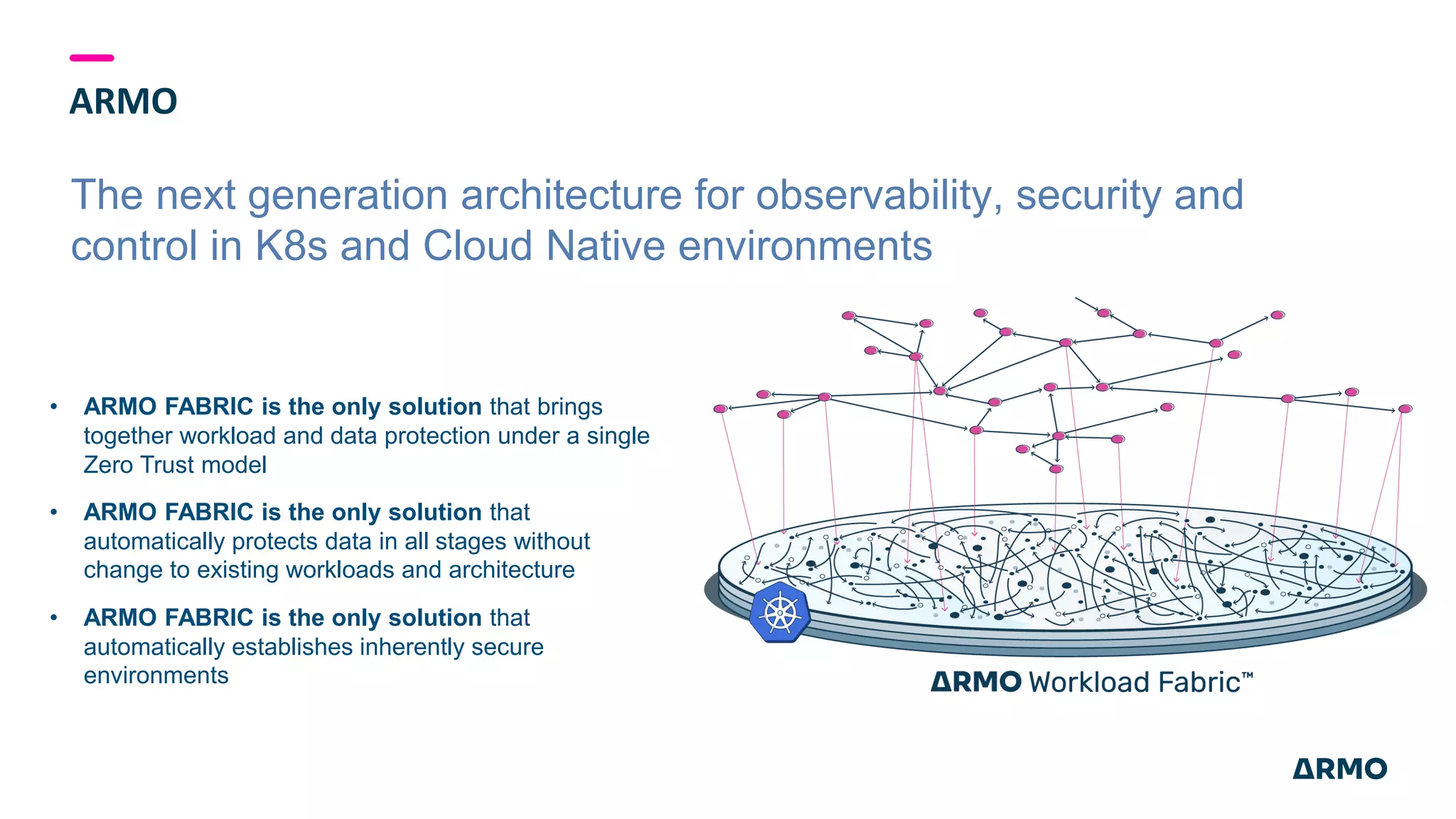
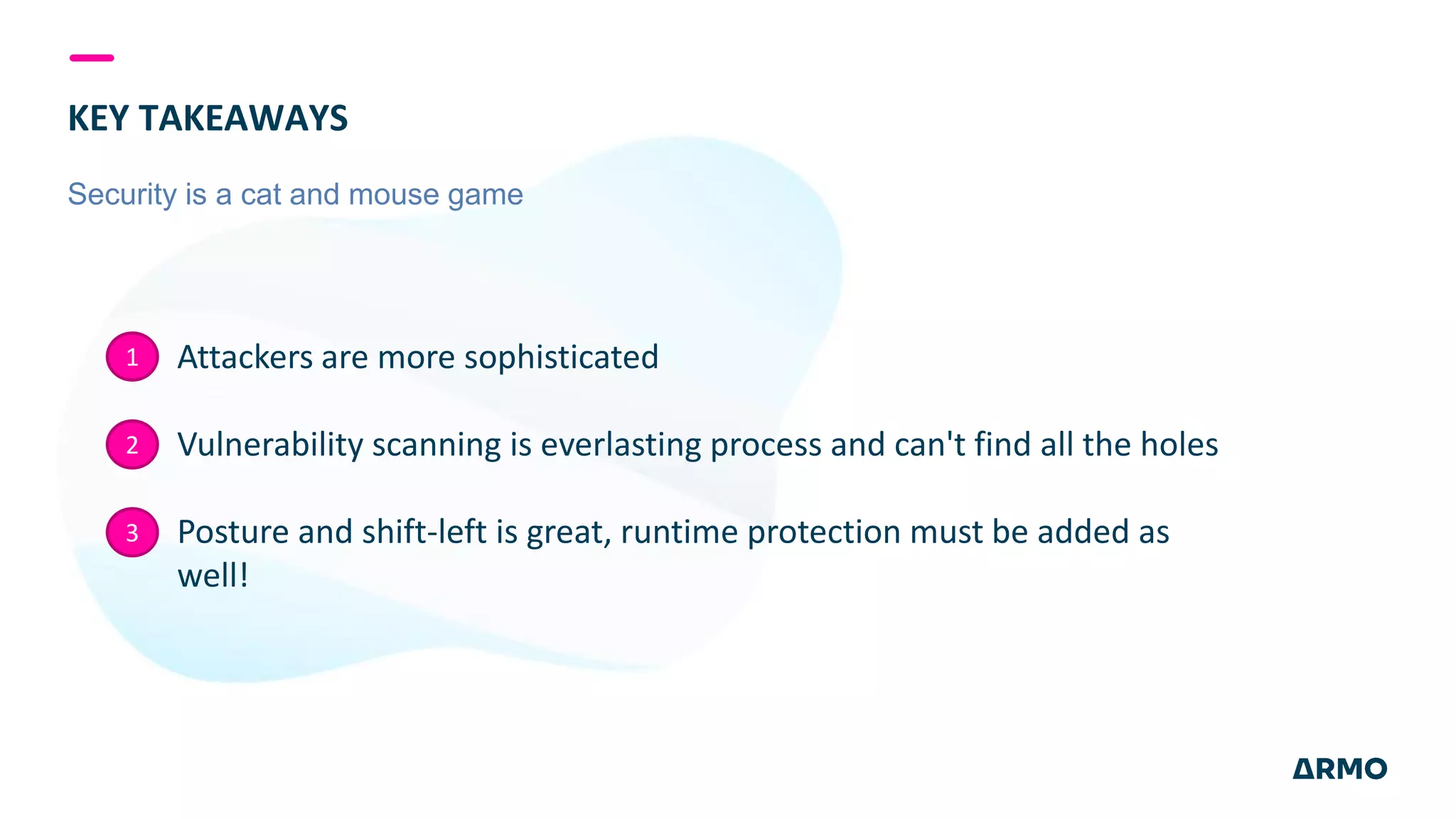
The document discusses the SolarWinds attack and lessons learned for cloud security. It begins by outlining the attack chain used, including how the attackers broke into SolarWinds' software development lifecycle and inserted malicious code. It then discusses issues like secret protection, granular identity management, and detecting fileless malware. The presentation recommends rethinking cloud security strategy to address weaknesses in these areas and provide runtime protection in addition to vulnerability scanning and secure development practices.