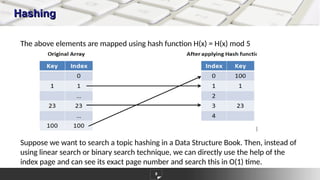
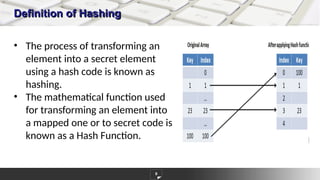
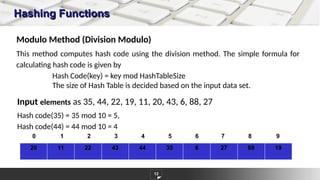
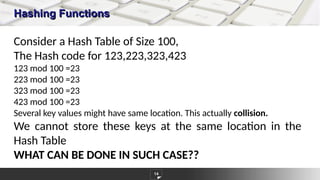
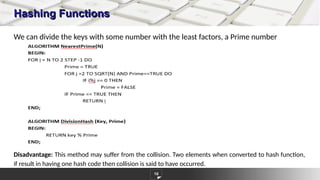
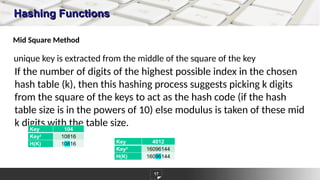
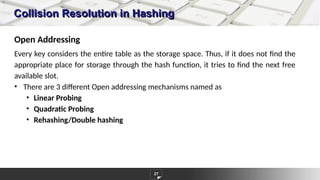
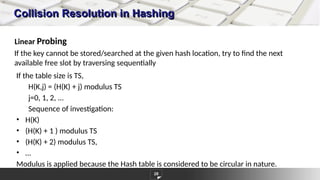
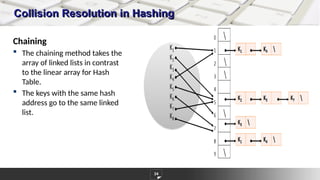
The document discusses hashing as a constant time searching technique, emphasizing its importance in reducing search complexity. It explains various hashing methods, including division, mid-square, and folding methods, each with examples of how they generate hash codes. Additionally, the document covers collision resolution strategies such as open addressing and chaining to handle situations where multiple keys hash to the same location.