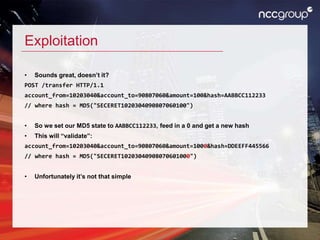
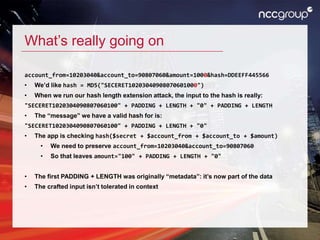
The document discusses hash length extension attacks, detailing how they exploit vulnerabilities in hash algorithms like MD5 and SHA-1 by allowing an attacker to append additional data to a message without knowing the secret prefix. It explains the mechanics of the attack, including how an attacker can construct valid inputs to achieve a valid hash for altered messages. The final thoughts emphasize the potential high impact of such vulnerabilities and suggest that while attacks can be challenging to execute, they remain a serious security concern.