- Dependent types allow types to depend on values, enabling parametrized types like vectors of length n
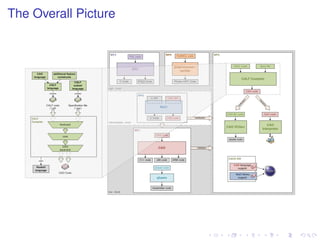
- The CALF language extends CAO with dependent types, polymorphism, and other features to improve safety and flexibility
- CALF translates to CAO by instantiating type parameters with concrete values from a specification file
- This allows verifying properties like out-of-bounds checks directly in CALF before translation to low-level CAO



![CAO Example
AES fragment
typedef GF2 := mod[ 2 ];
typedef GF2N :=
mod[ GF2<X> / X**8 + X**4 + X**3 + X + 1 ];
typedef S
:= matrix[4,4] of GF2N;
def mix : matrix[4,4] of GF2N
{[X], [X+1],[1], [1],
[1], [X], [X+1],[1],
[1], [1], [X], [X+1],
[X+1],[1], [1], [X]};
:=
def MixColumns( s : S ) : S {
def r : S;
seq i := 0 to 3 {
r[0..3,i] := mix * s[0..3,i]; }
return r; }](https://image.slidesharecdn.com/haslab-131120140455-phpapp01/85/Dependent-Types-for-Cryptography-Implementations-4-320.jpg)
![Limitations of CAO
In CAO all type sizes have to be statically determined
In the previous example, the MixColumns function only
works with 4 × 4 matrices
We would like to allow parametrisation of these sizes. For
instance:
typedef S<(n : int)> := matrix[n,n] of GF2N;
def MixColumns<(n : int)>( s : S<(n)> ) : S<(n)> {
def r : S<(n)>;
seq i := 0 to n-1 {
r[0..n,i] := mix * s[0..n,i]; }
return r; }](https://image.slidesharecdn.com/haslab-131120140455-phpapp01/85/Dependent-Types-for-Cryptography-Implementations-5-320.jpg)
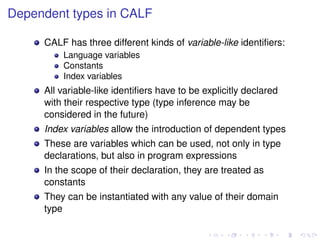
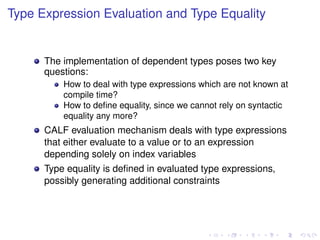
![Dependent types
A dependent type depends on a value belonging to the
realm of program expressions
Can be seen as families of types indexed by values
In polymorphism, the type depends on another type
parameter, e.g.,
∀ α ∈ types . Vector of α
leading to vectors of integers, vectors of booleans, etc.
Using dependent types, the type depends on a value, e.g.,
Π n : Int . Vector[n]
leading to vectors of length 5, vectors of length 13, etc.](https://image.slidesharecdn.com/haslab-131120140455-phpapp01/85/Dependent-Types-for-Cryptography-Implementations-6-320.jpg)







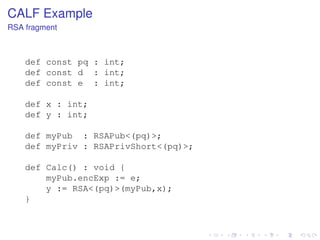
![CALF Example
RSA fragment
typedef RSAPub<(m : int)>
:=
struct [ def encExp : int; ];
typedef RSAPrivShort<(m : int)> :=
struct [ def decExp : int; ];
def RSA<(n : int)>(k : RSAPub<(n)>, m : int ) : int {
def c : mod[n];
c := (mod[n]) m; c := c ** k.encExp;
return (int) c;
}
def RSAInvShort<(n : int)>
(k : RSAPrivShort<(n)>, c : int) : int {
def m : mod[n];
m := (mod[n]) c;
return (int) m;
}
m := m ** k.decExp;](https://image.slidesharecdn.com/haslab-131120140455-phpapp01/85/Dependent-Types-for-Cryptography-Implementations-16-320.jpg)

![CALF Example
Generated CAO code
typedef RSAPub_35 := struct[def encExp_35 : int;];
def RSA_35(k : RSAPub_35, m : int) : int {
def c : mod[35];
c := (mod[35]) m;
c := c ** k.encExp_35;
return (int) c;
}
def myPub : RSAPub_35;
def x : int;
def y : int;
def Calc() : void {
myPub.encExp_35 := 11;
y := RSA_35(myPub, x);
}](https://image.slidesharecdn.com/haslab-131120140455-phpapp01/85/Dependent-Types-for-Cryptography-Implementations-19-320.jpg)