This document discusses machine assisted verification tools for cryptography. It describes the Computer Aided Cryptography Engineering project which aims to develop tools for cryptographic software engineering. The author's group is responsible for the formal verification and validation work package. This involves adapting techniques like formal verification to cryptographic software using languages like CAO and CALF. CAO is a domain specific language for cryptography while CALF provides more powerful abstraction. The document outlines the deductive verification approach used on CAO programs as well as work on a compiler from CALF to CAO.



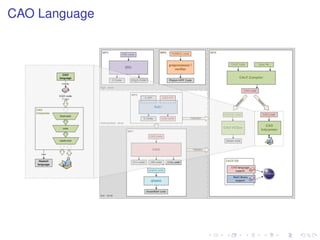

![CAO Language Example (AES fragment)
typedef GF2 := mod[ 2 ];
typedef GF2N :=
mod[ GF2<X> / X**8 + X**4 + X**3 + X + 1 ];
typedef S
:= matrix[4,4] of GF2N;
def mix : matrix[4,4] of GF2N
{[X],[X+1],[1],[1],
[1],[X],[X+1],[1],
[1],[1],[X],[X+1],
[X+1],[1],[1],[X]};
:=
def MixColumns( s : S ) : S {
def r : S;
seq i := 0 to 3 {
r[0..3,i] := mix * s[0..3,i]; }
return r; }](https://image.slidesharecdn.com/net-scip-131120134342-phpapp02/85/Machine-Assisted-Verification-Tools-for-Cryptography-6-320.jpg)


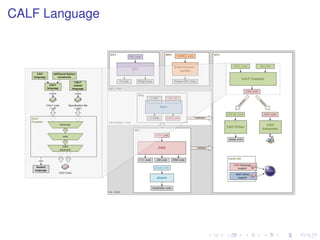


![CALF Language Example (RSA fragment)
typedef RSAPub<(n : int)> :=
struct [ def e : int; ];
def RSA<(n : int)>(k : RSAPub<(n)>, m : int ) : int
{
def c : mod[n];
c := (mod[n]) m;
c := c ** k.e;
return (int) c;
}](https://image.slidesharecdn.com/net-scip-131120134342-phpapp02/85/Machine-Assisted-Verification-Tools-for-Cryptography-13-320.jpg)
