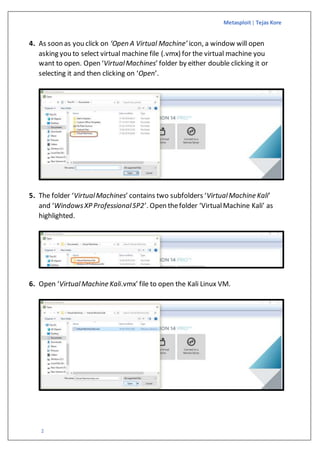
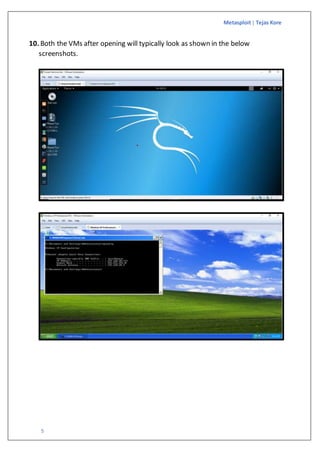
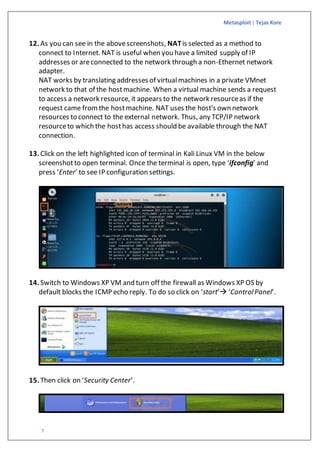
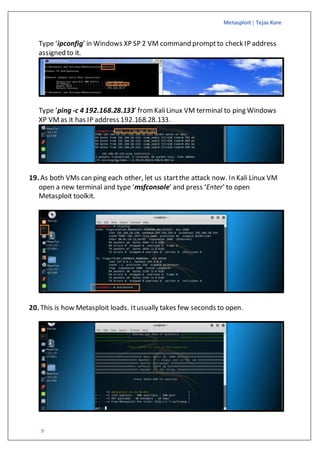
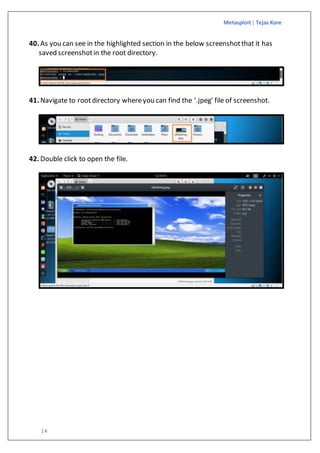
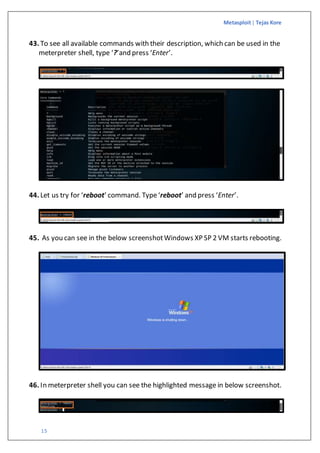
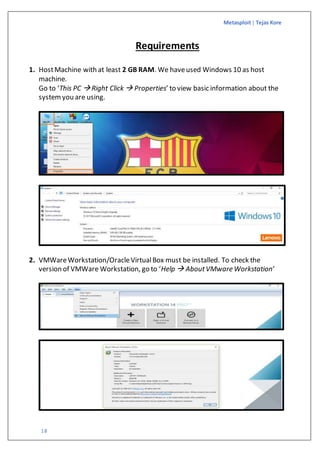
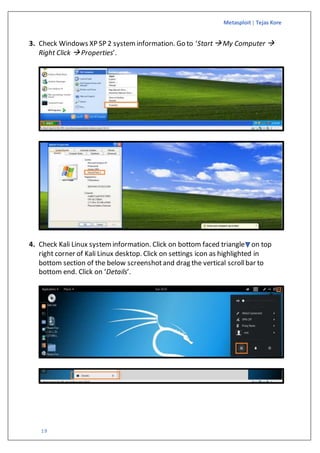
The document is a guide on exploiting Windows XP SP2 using Metasploit within a virtual environment set up on VMware Workstation. It details the steps to configure virtual machines, check network settings, and execute exploits, specifically focusing on the ms08_067_netapi module. Additionally, it covers requirements for the host machine and provides download links for necessary software and resources.