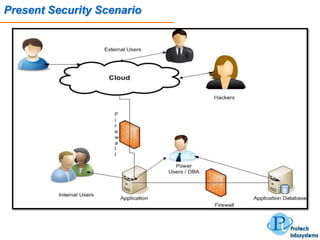
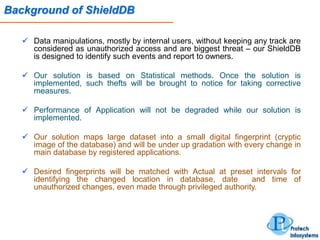
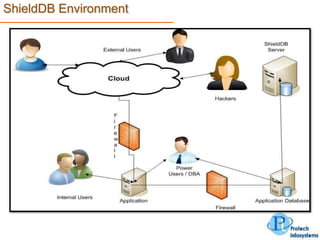
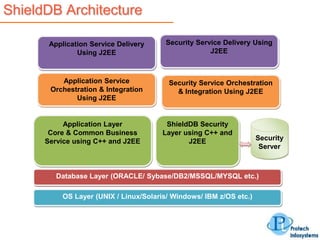
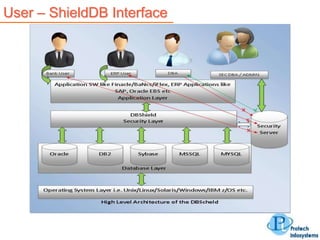
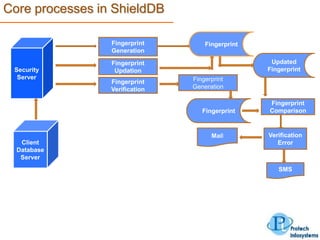
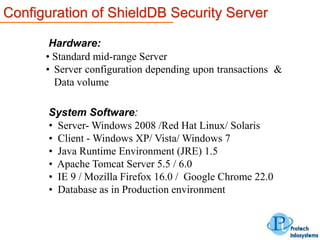
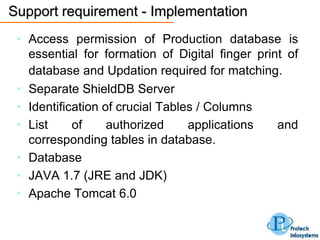
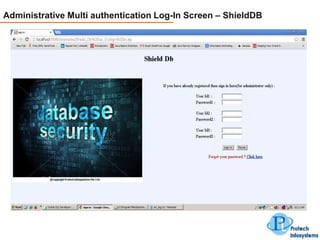
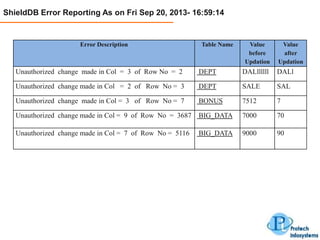
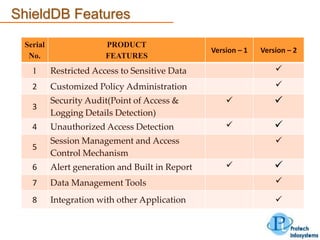
This document describes a database security solution called ShieldDB developed by Protech Infosystems Pvt. Ltd. ShieldDB uses statistical methods to generate fingerprints of databases and detect unauthorized modifications by comparing fingerprints over time. It aims to address issues like data theft, identity theft, and modification of critical data. The solution monitors databases without degrading performance and reports security breaches and related details through email/SMS.