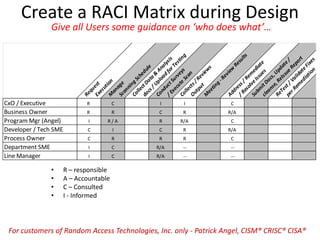
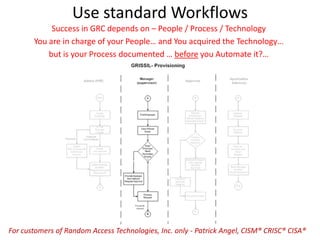
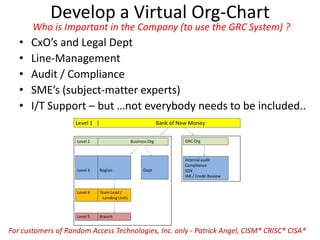
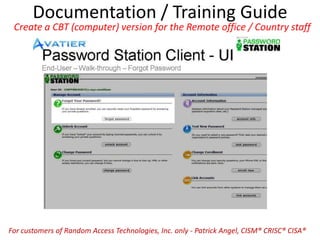
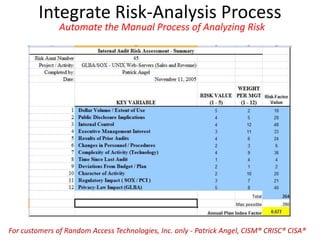
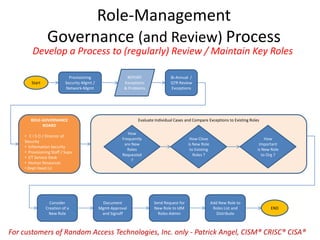
The document outlines a strategy for implementing a Governance, Risk, and Compliance (GRC) software solution, emphasizing the importance of identifying sponsors, executing in phases for quick wins, and establishing clear roles through a RACI matrix. Key steps include ensuring effective communication, data cleansing, using a sandbox for testing, and documenting decisions throughout the implementation process. Success relies on engaging stakeholders, training users, and consistently communicating the benefits and ROI of the new system.