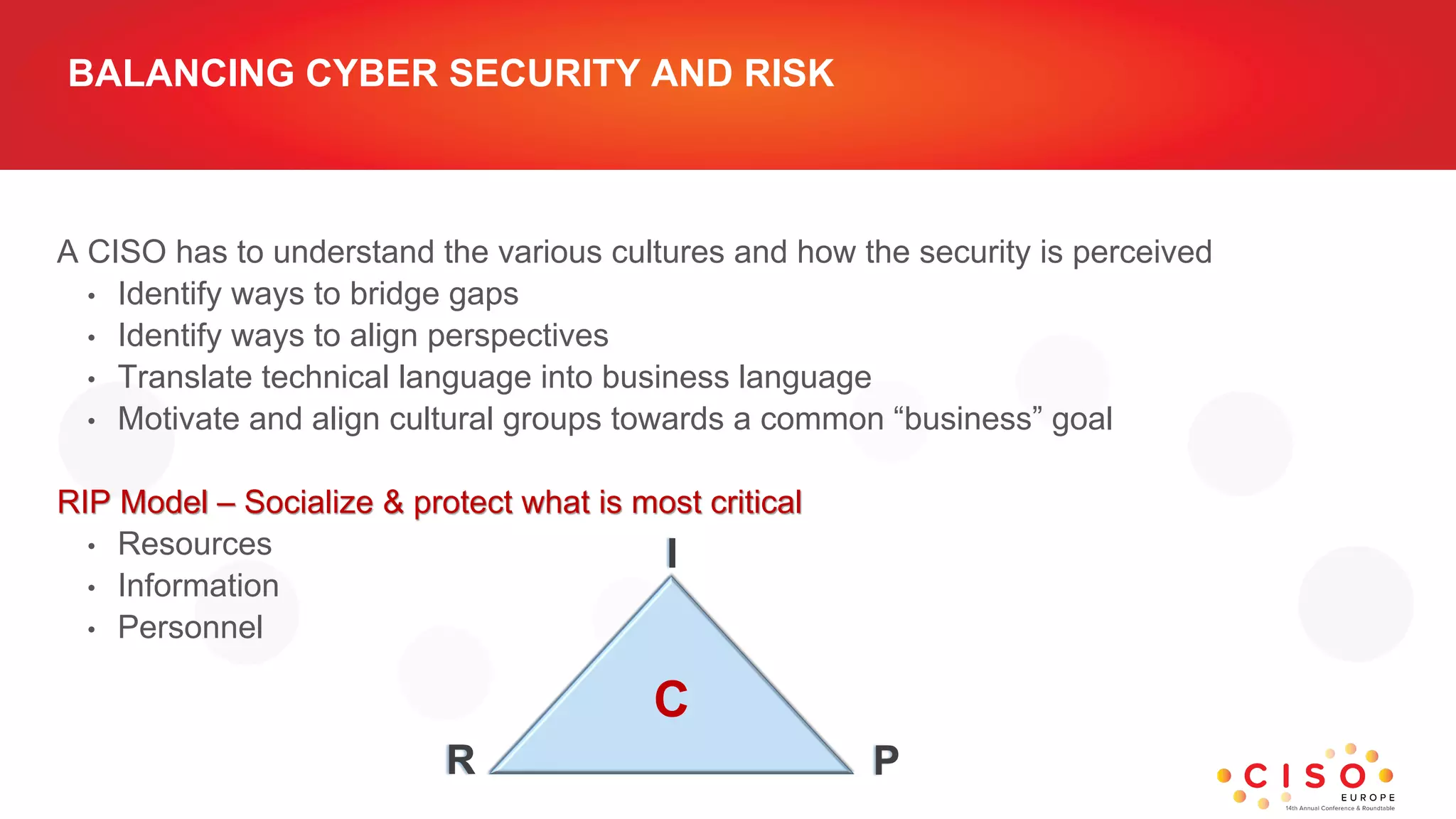
The document analyzes the global shortage of cybersecurity professionals, highlighting cultural differences in workforce perspectives and the necessity for improved education and training programs. It discusses the importance of effective communication and collaboration between IT and business units to cultivate a strong cybersecurity culture while addressing skill gaps. Additionally, it emphasizes the need for CISOs to bridge cultural divides, align perspectives, and ensure that cybersecurity training is integrated with operational IT service delivery.