This document provides an overview of cyber ethics, including:
- Defining cyber ethics as the study of the impact of computer technology on ethics and the design of policies for its ethical use.
- Describing the evolution of cyber ethics in four phases from the 1950s to the present.
- Explaining that cyber technology has unique ethical aspects due to its logical malleability and the unintentional power embedded in its design.
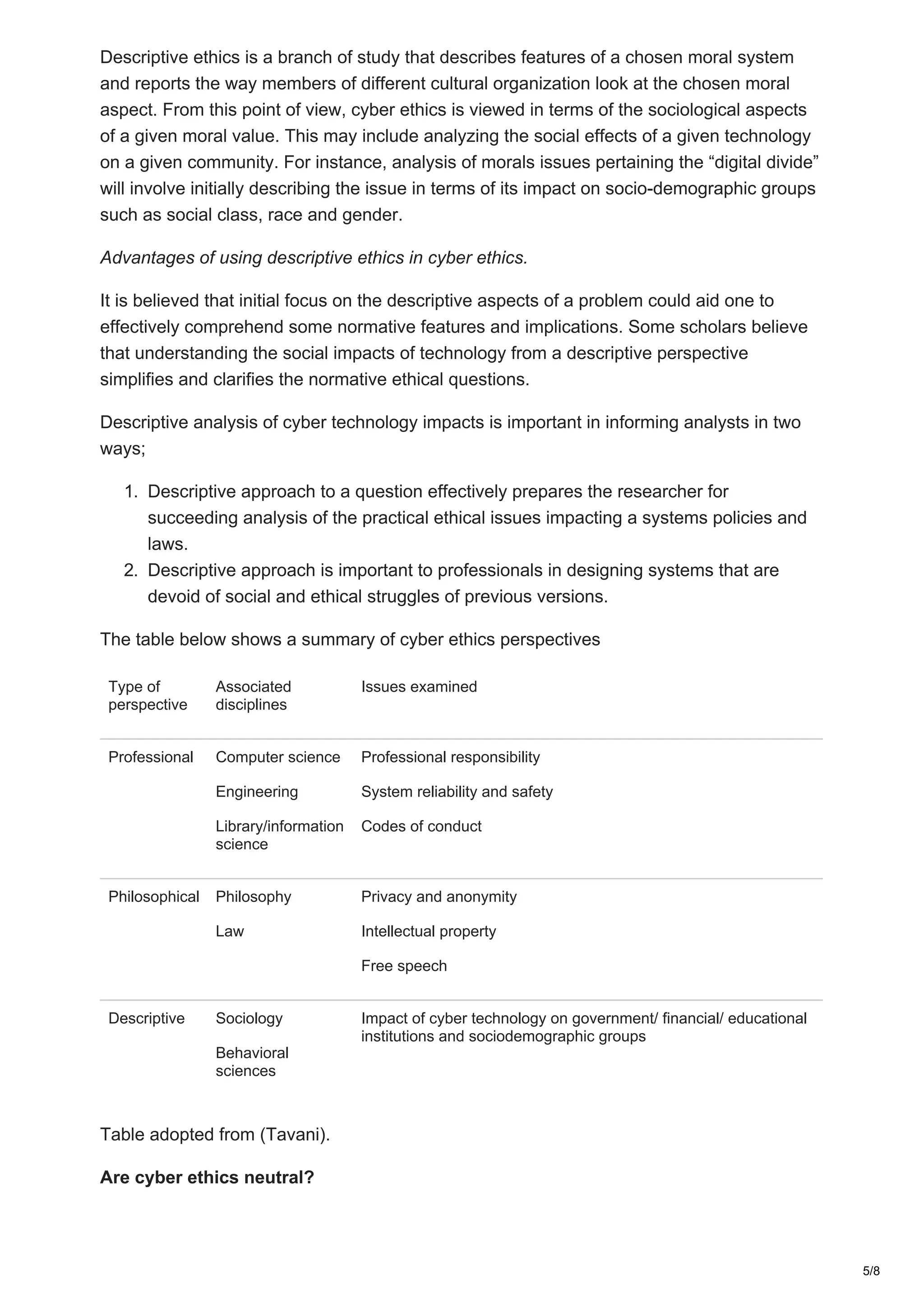
- Outlining three perspectives that cyber ethics can be viewed from: as a field of professional ethics, philosophical ethics, or descriptive ethics.
- Highlighting some key ethical issues in cyber technology like privacy, accuracy, intellectual property, and access.
- Providing a strategy