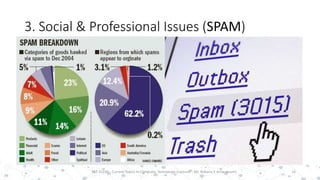
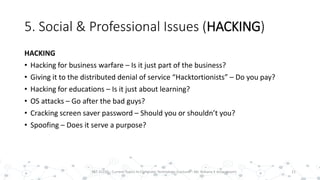
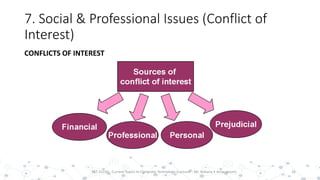
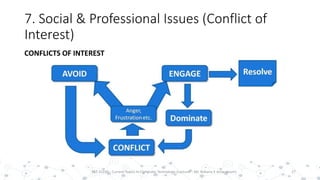
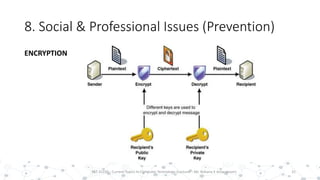
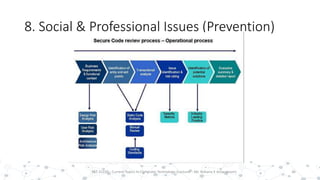
This document discusses various social and professional issues in information technology, including ethics, vulnerability disclosure, spam, email scams, hacking, viruses, and conflicts of interest. It addresses how organizations can evaluate their ethics and culture and examines approaches to vulnerability disclosure like non-disclosure, full disclosure, and responsible disclosure. It also outlines common email scams and discusses hacking activities and the development of viruses and worms.