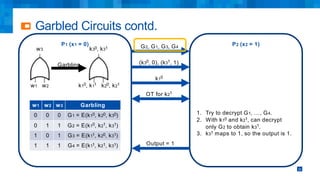
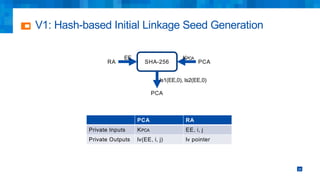
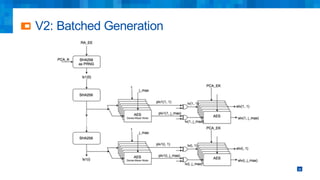
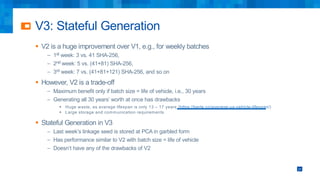
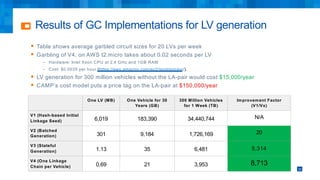
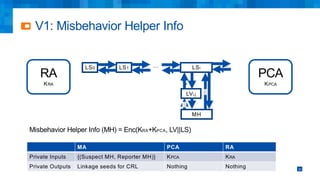
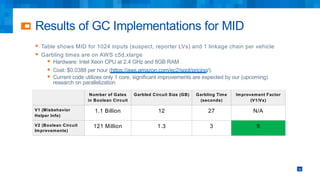
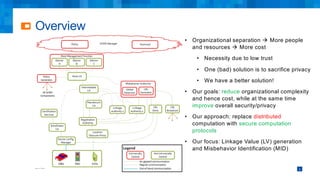
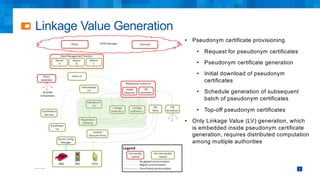
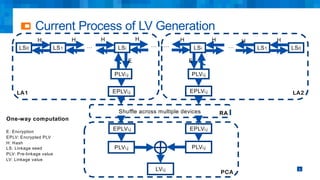
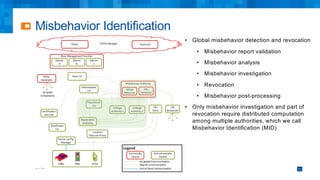
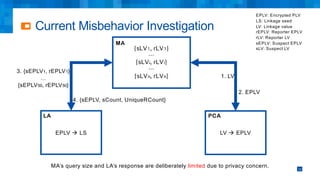
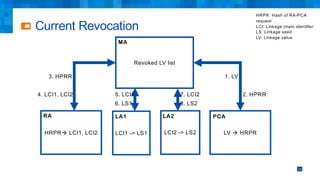
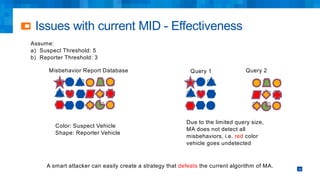
The document discusses the simplifications and security improvements in Secure Computation Management Systems (SCMS) through the use of secure computation protocols, focusing on linkage value (LV) generation and misbehavior identification (MID). It outlines the vulnerabilities of current distributed computation models and presents a novel approach that merges functionalities to enhance privacy and reduce costs while addressing malicious insider threats. The proposed solutions show significant improvements in efficiency and effectiveness in both LV generation and MID, ensuring better security and privacy outcomes.












![Secure Computation
§ Parties P1, P2, …, Pn with private inputs x1, x2, …, xn can jointly
compute any arbitrary function f(x1, x2, …, xn), s.t.
– Correctness: Output is guaranteed to be correct.
– Privacy: Inputs are guaranteed to remain private.
– …
§ [Yao ’82] achieved this for n = 2.
§ [Goldreich-Micali-Wigderson ’87] achieved this for n ≥ 2.
§ Active area of cryptographic research.
20](https://image.slidesharecdn.com/scmsgarbledcircuits-180618175258/85/Garbled-Circuits-for-Secure-Credential-Management-Services-20-320.jpg)
![Garbled Circuits [Yao ’82]
21
f(x1, x2)](https://image.slidesharecdn.com/scmsgarbledcircuits-180618175258/85/Garbled-Circuits-for-Secure-Credential-Management-Services-21-320.jpg)