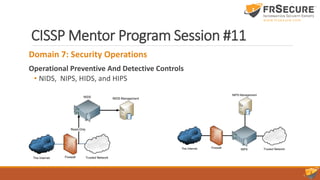
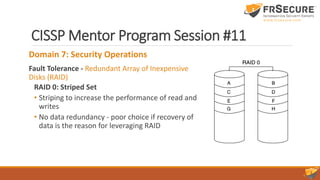
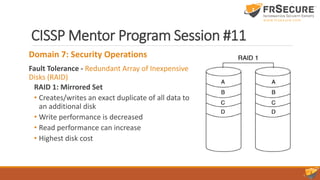
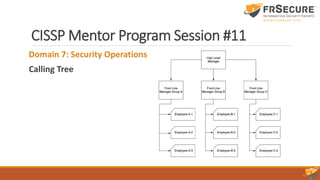
The document outlines the content of the 11th session of the CISSP mentor program, focusing on identity and access management, security assessment, and incident response management. Key topics covered include access control methodologies, phishing attacks, penetration testing, and incident response steps from detection to reporting. Additionally, the importance of vulnerability management, change management, and service level agreements in enhancing organizational security are emphasized.