Embed presentation
Downloaded 146 times



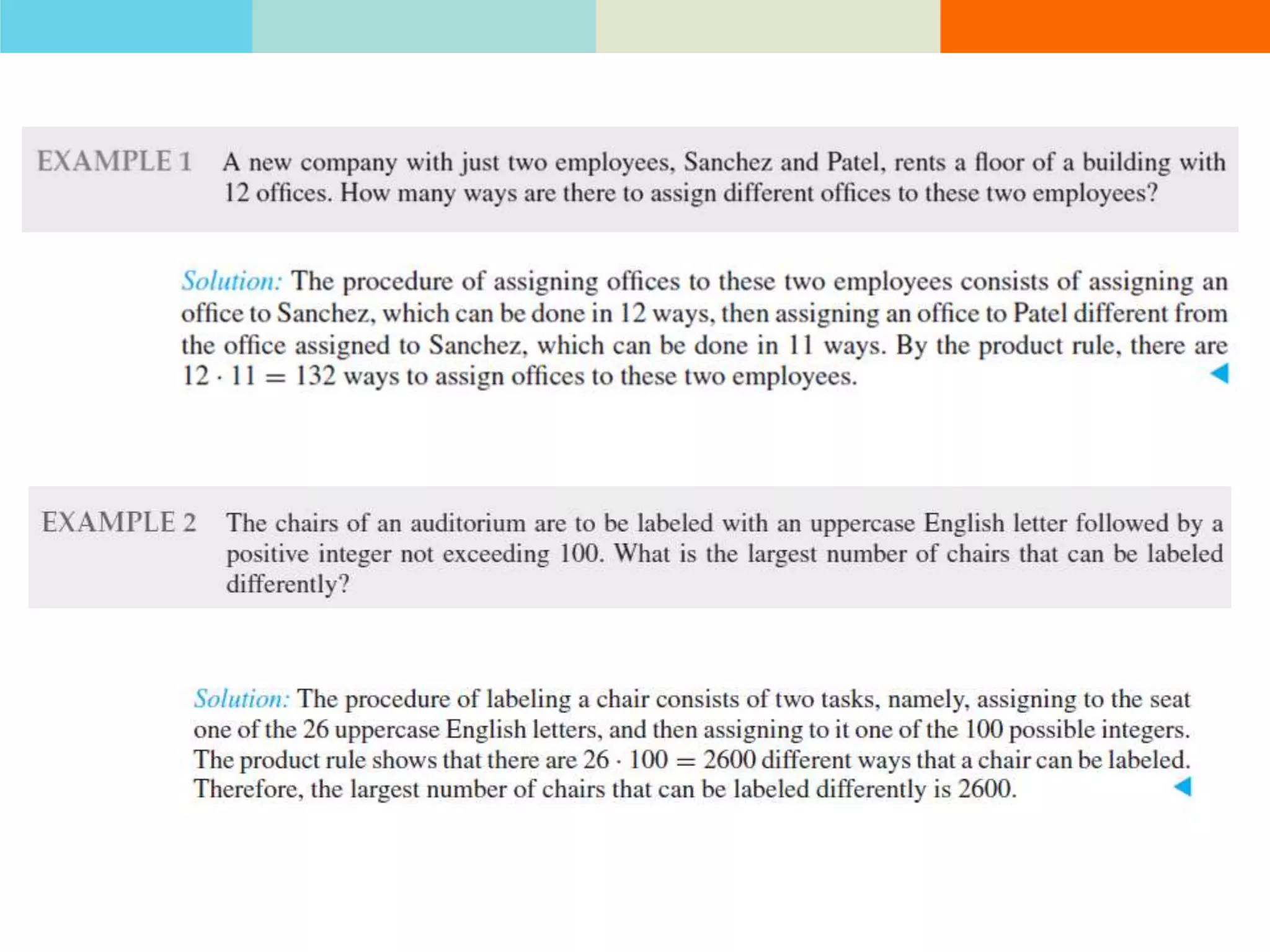
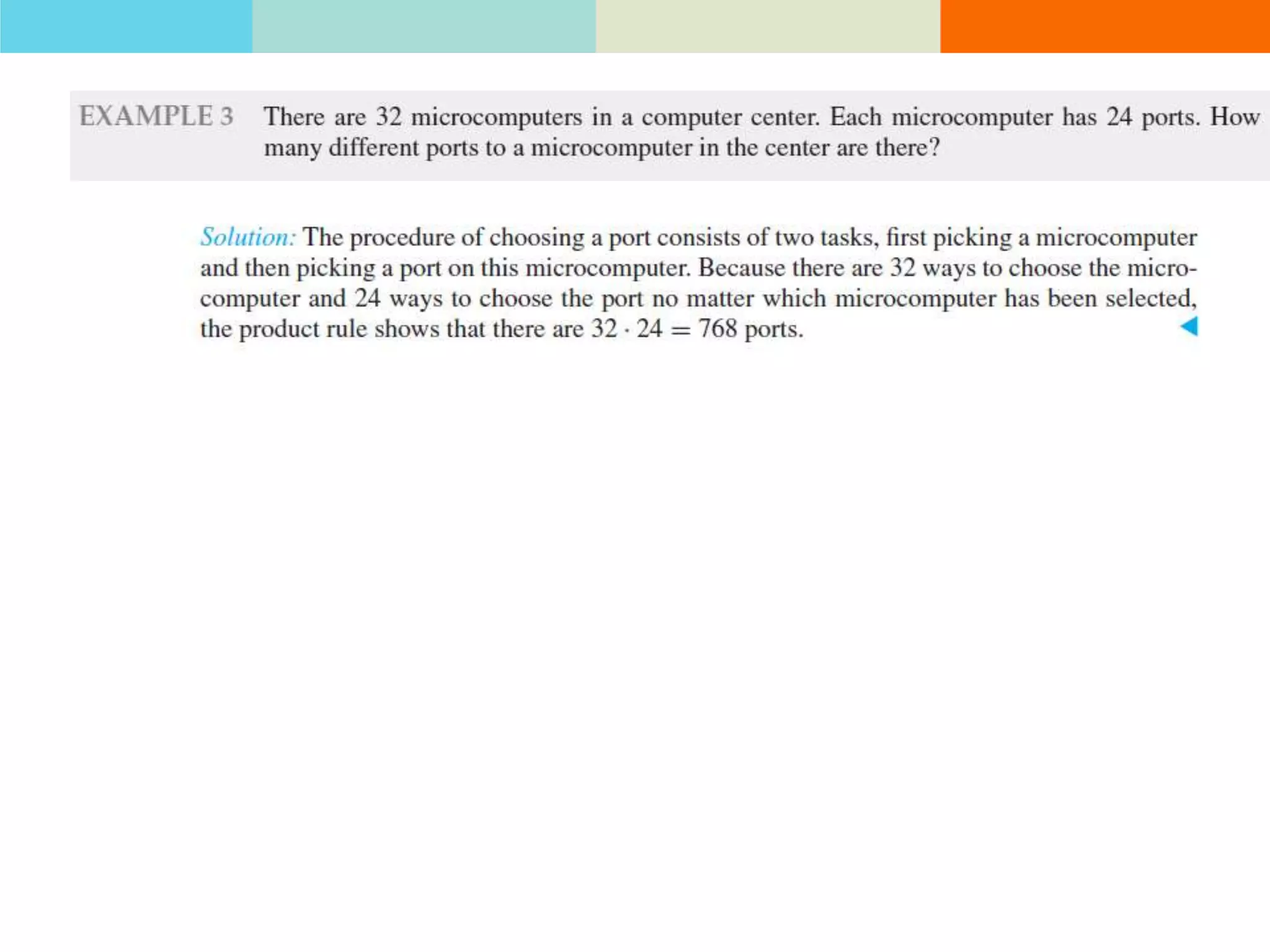
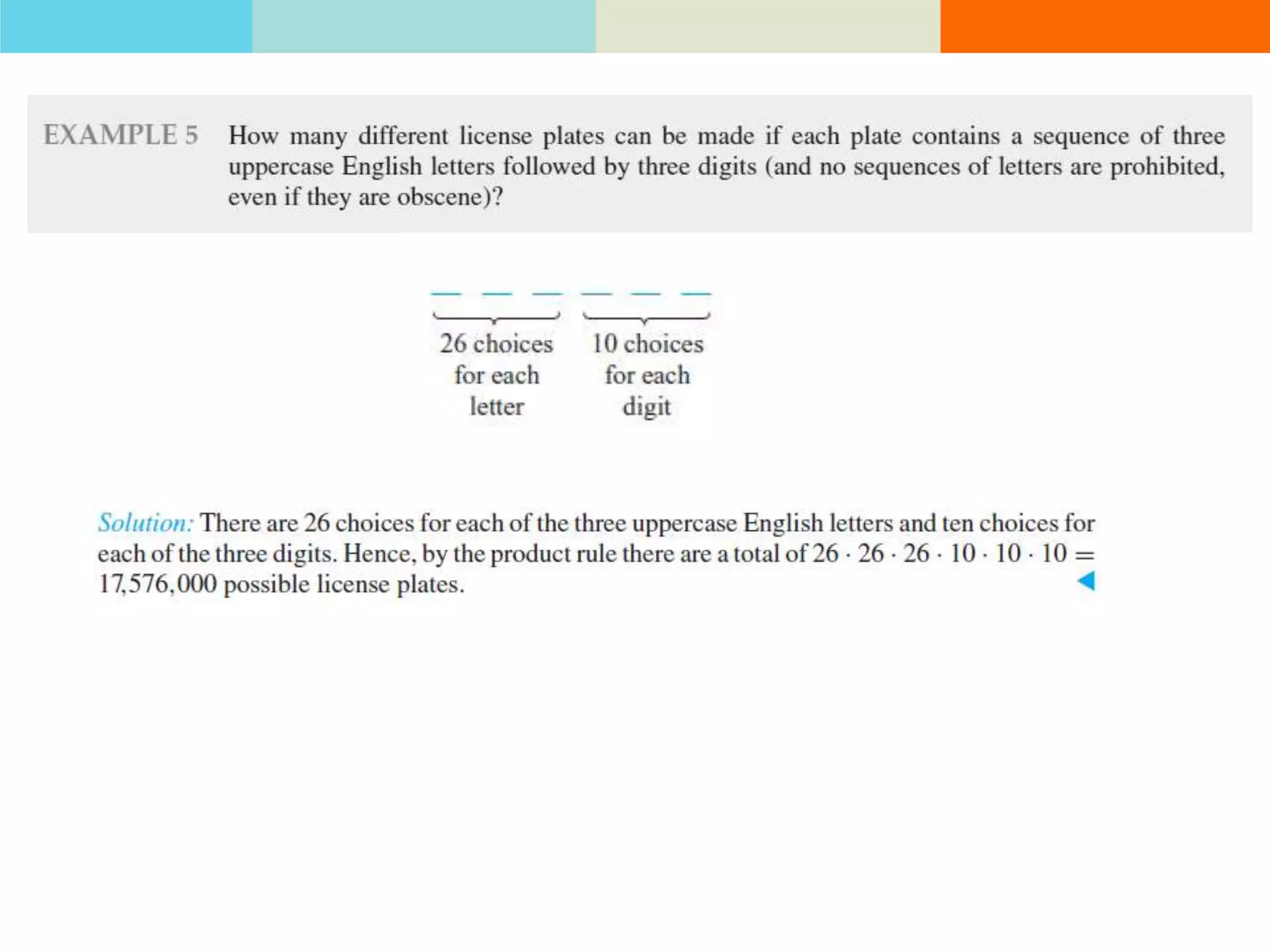
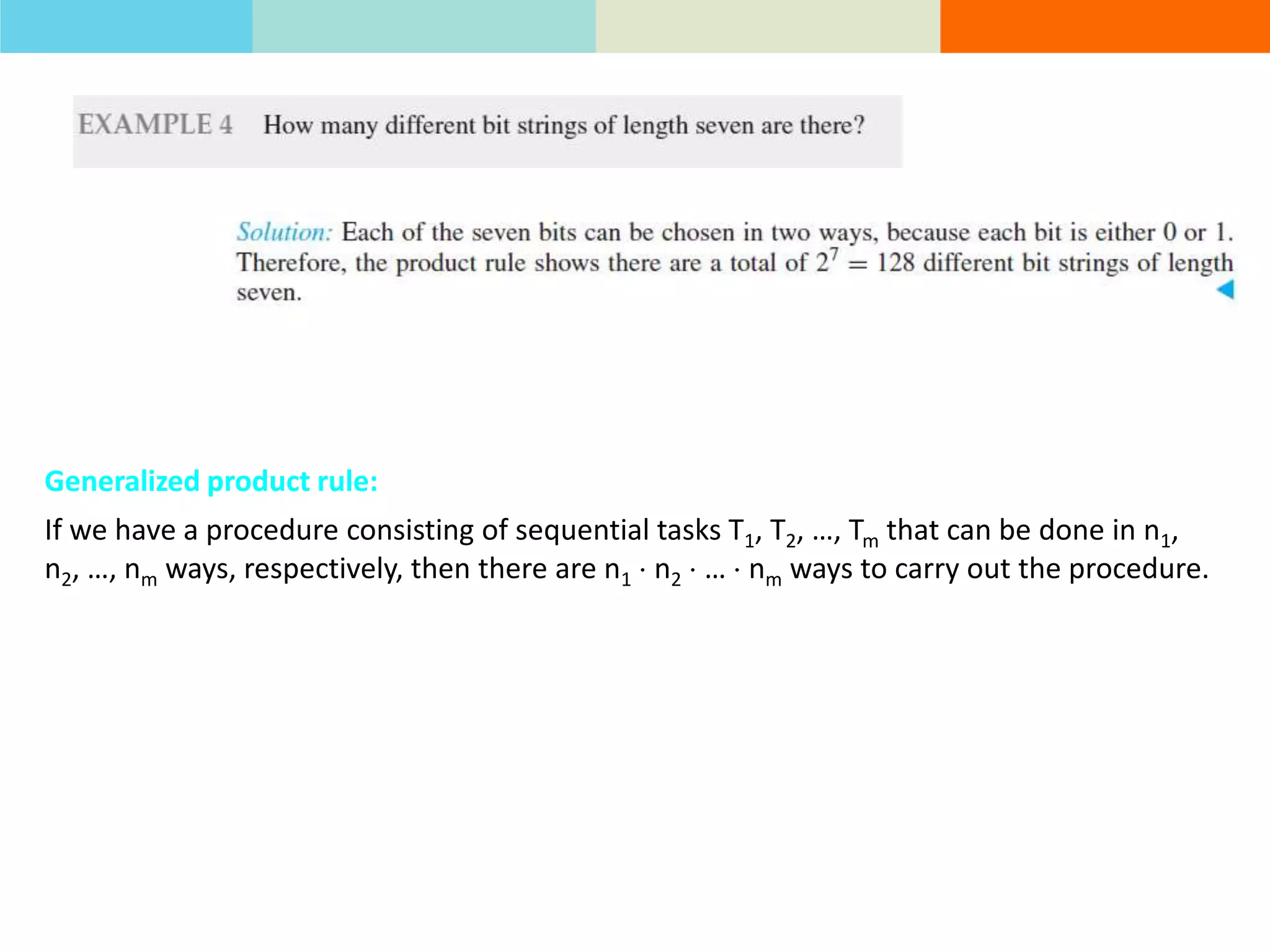
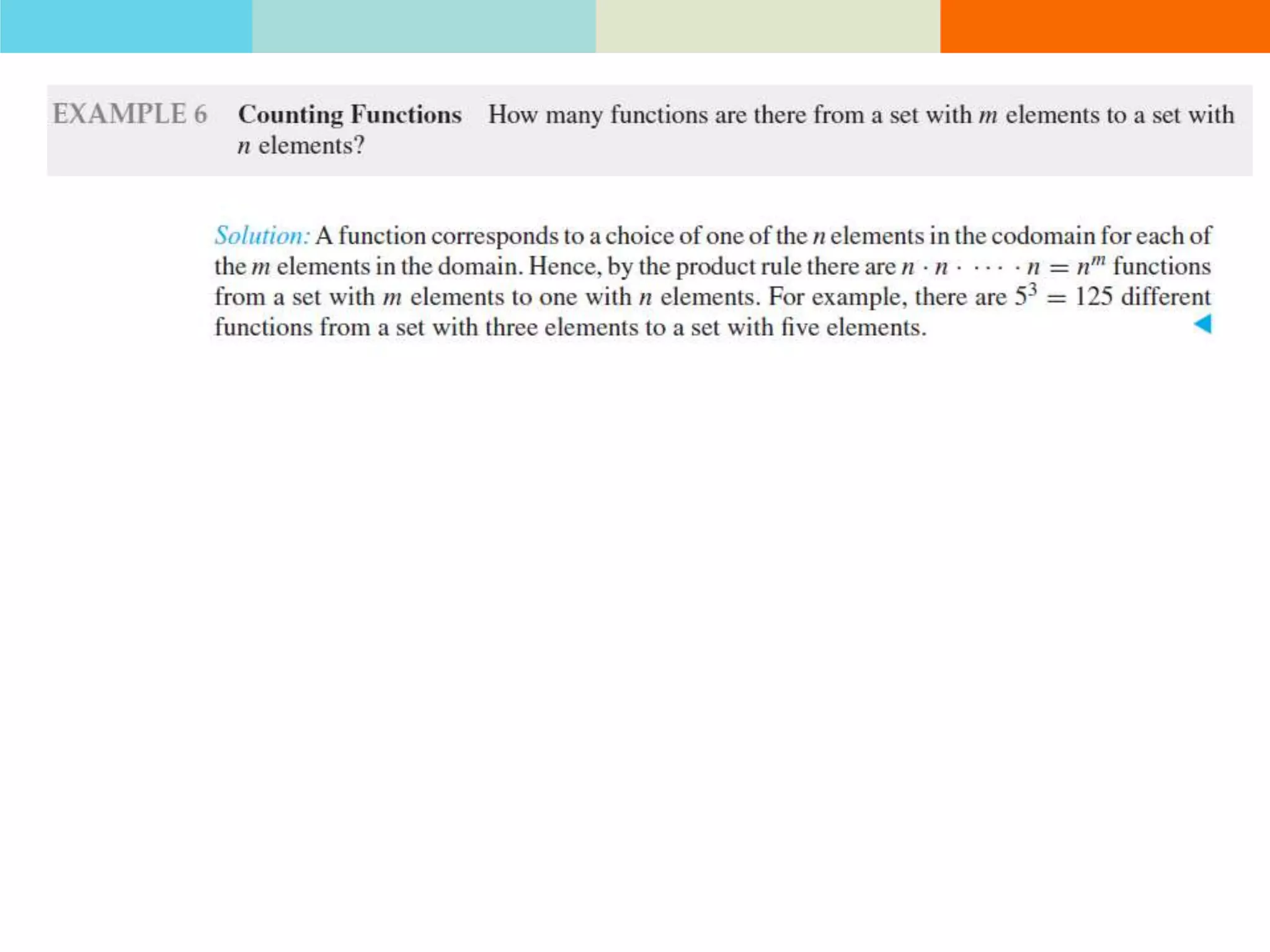

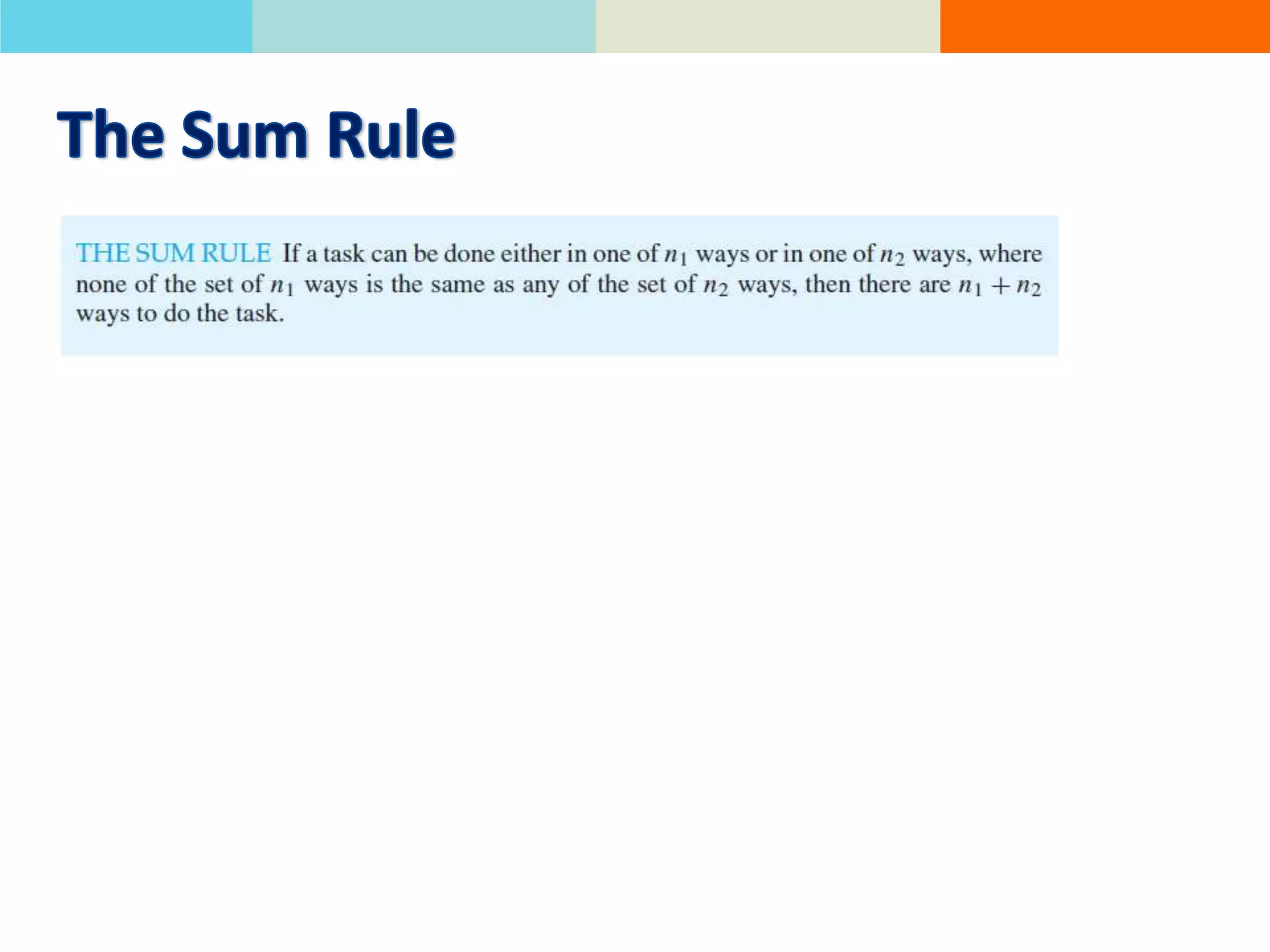
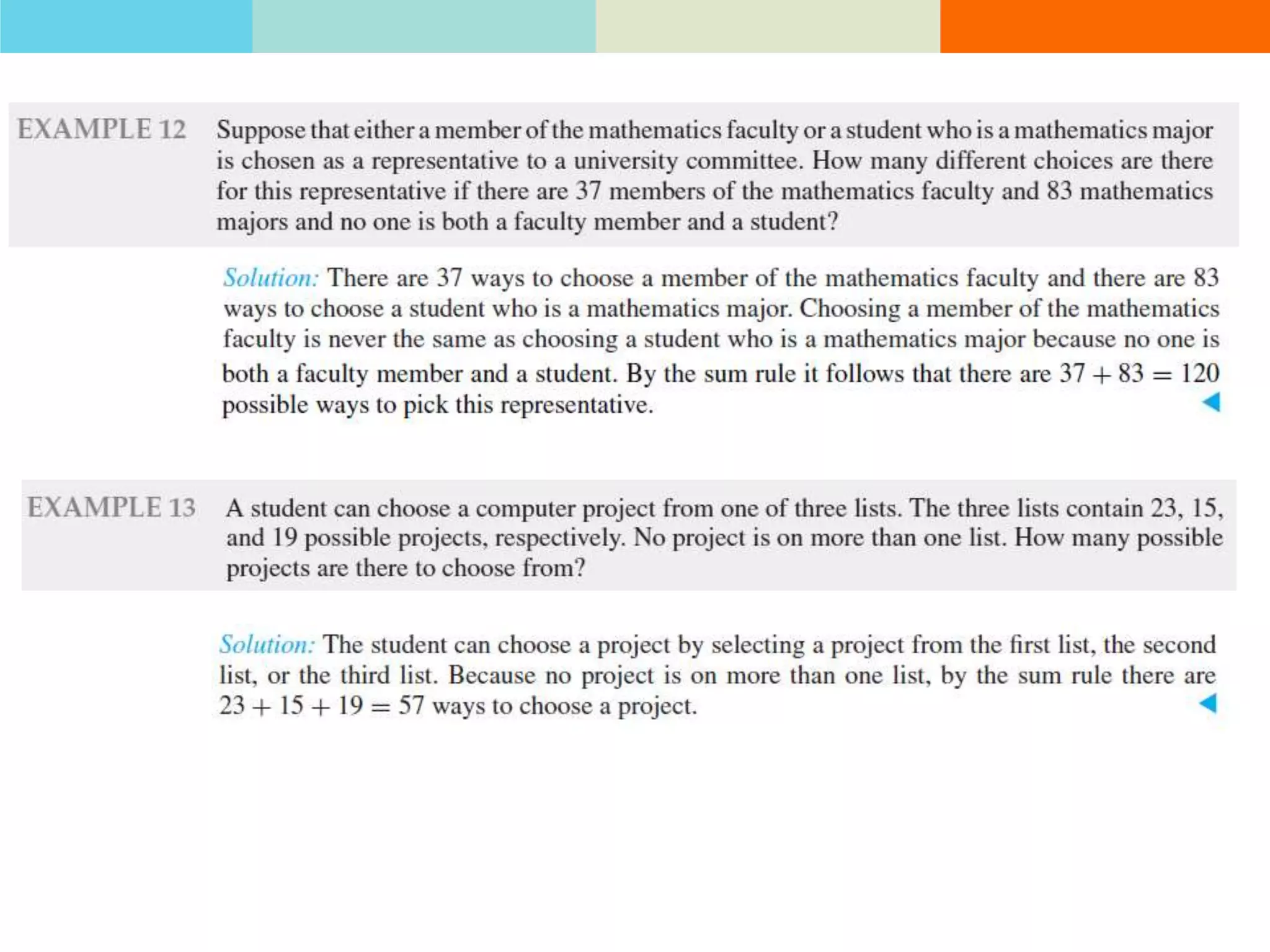


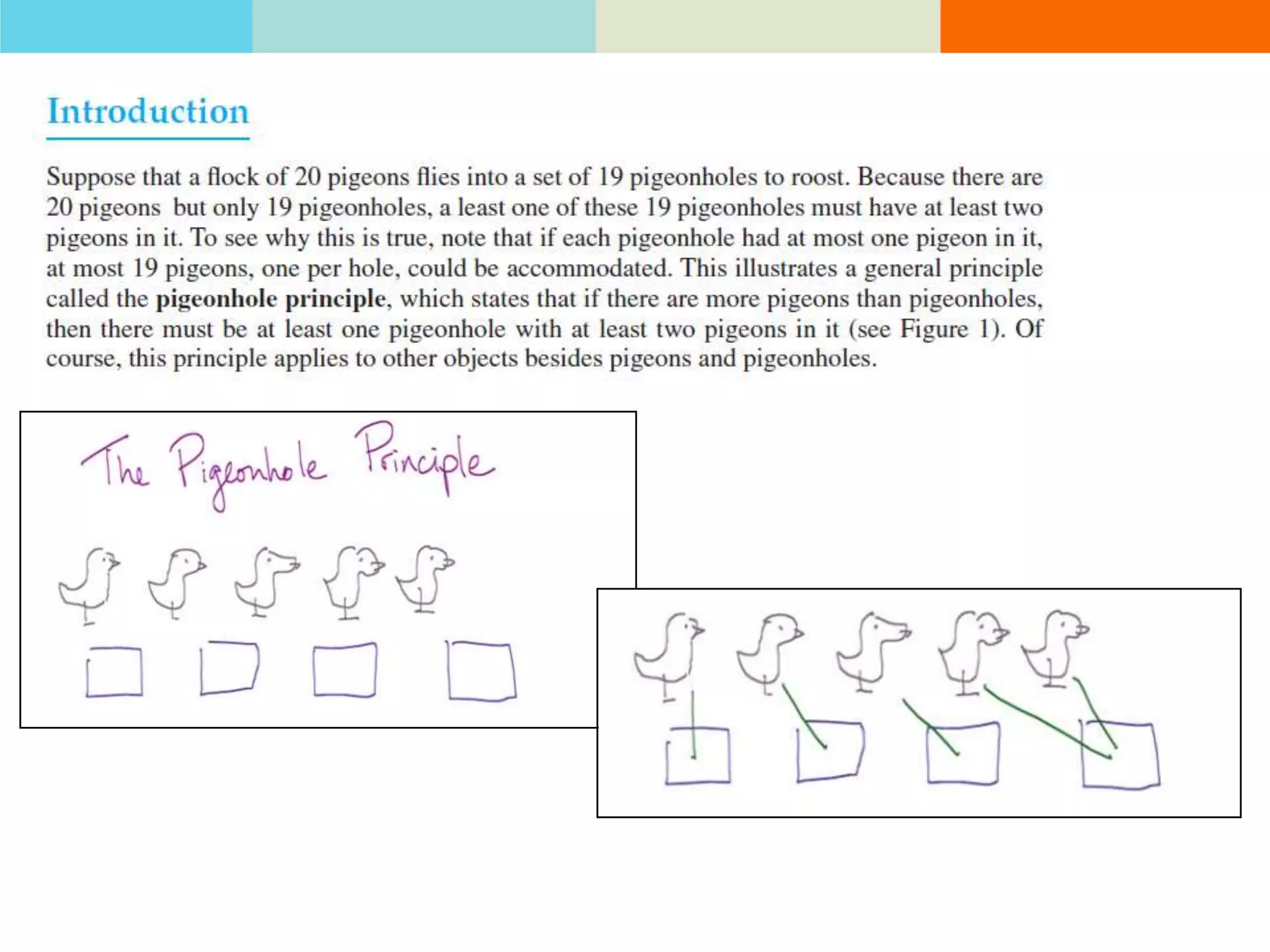

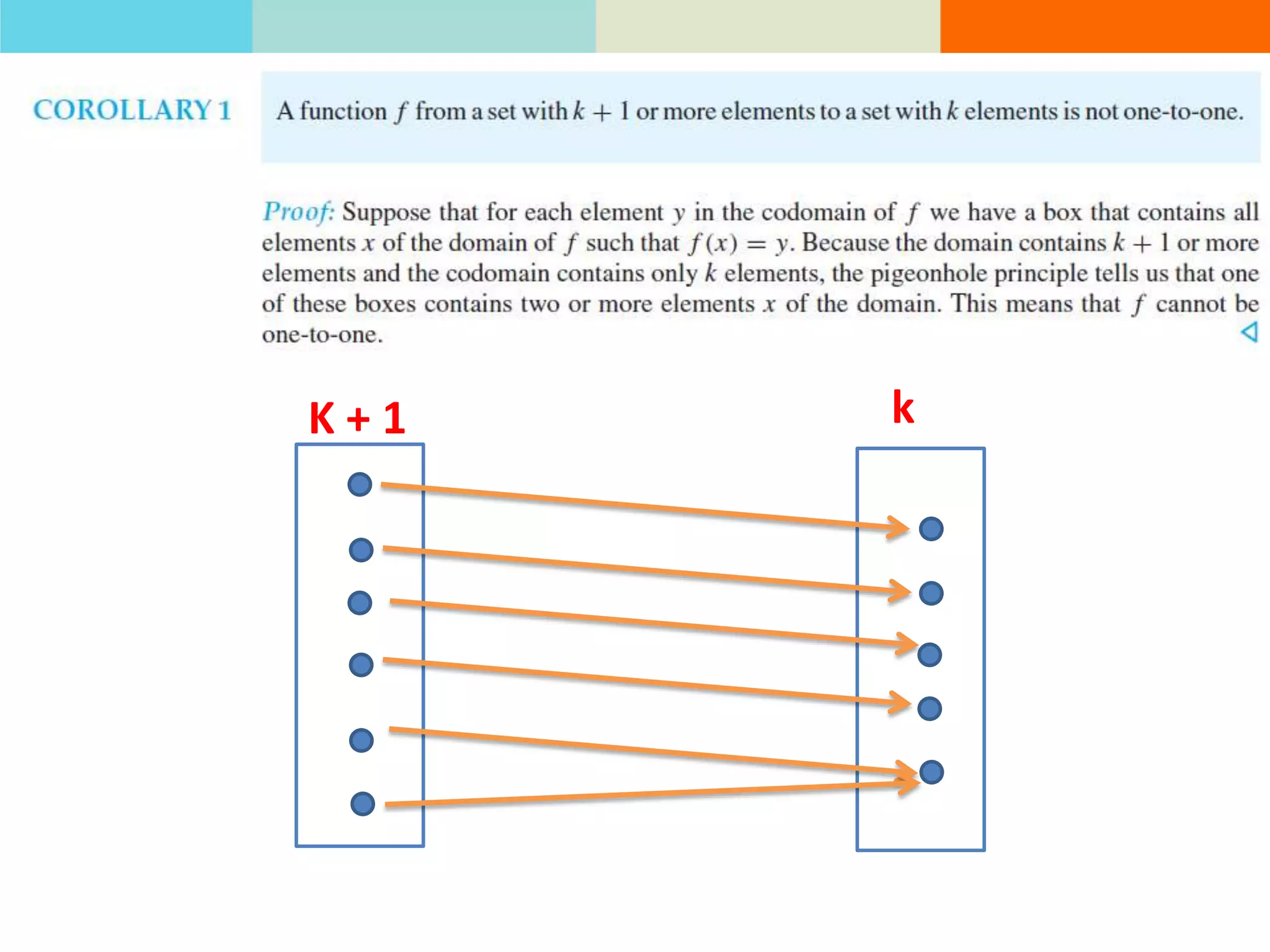
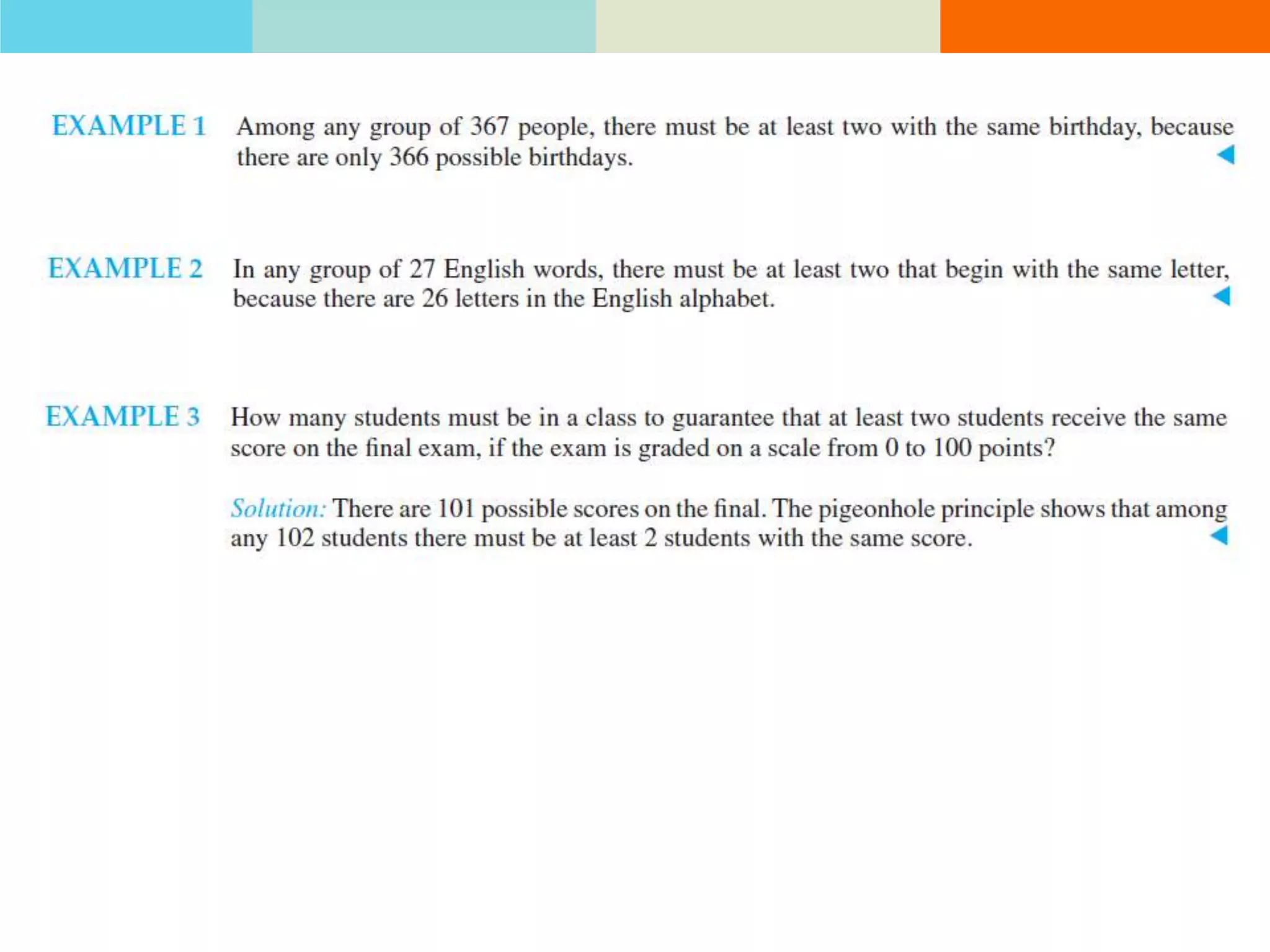
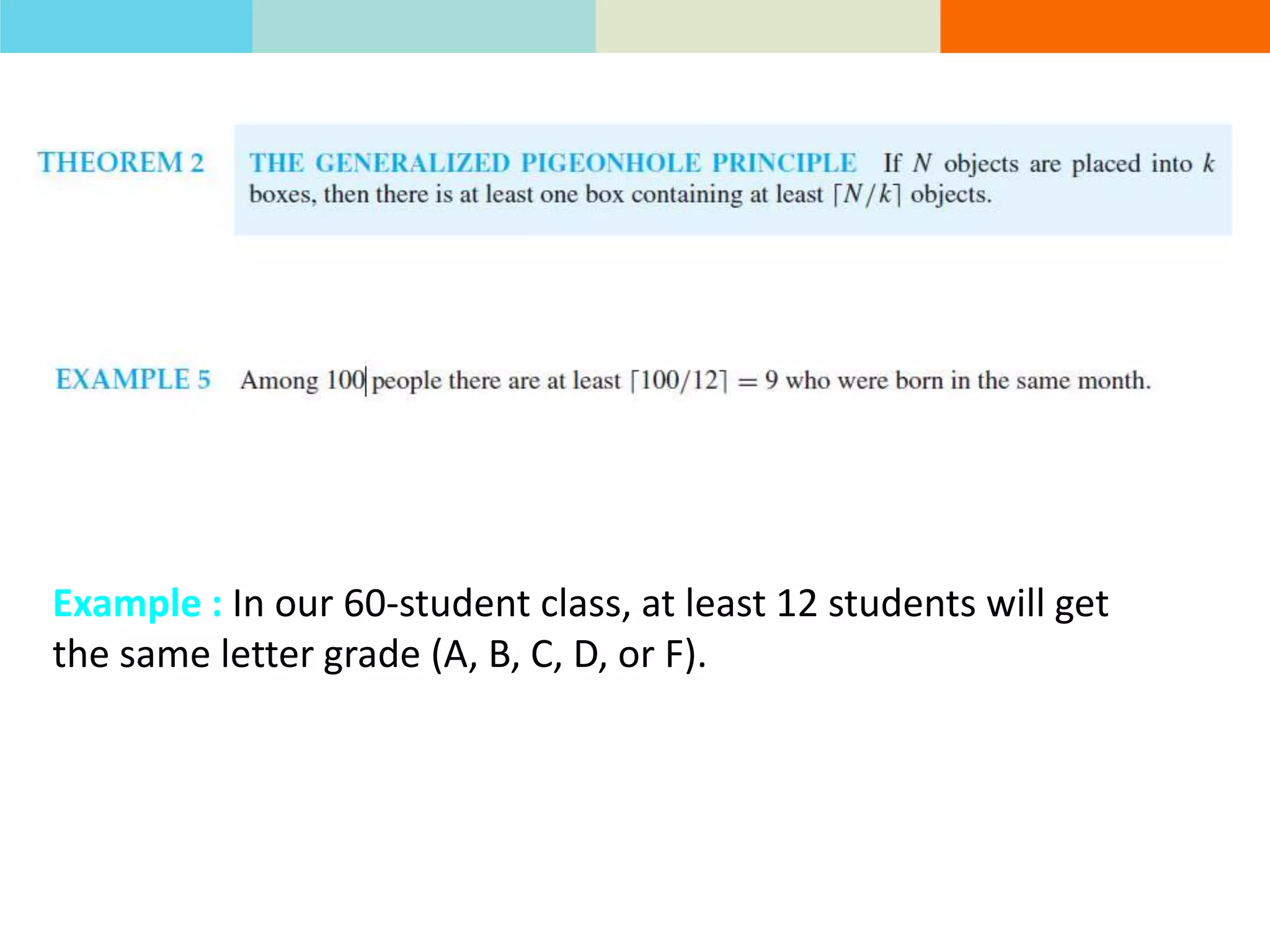


The product rule states that if a procedure consists of sequential tasks that can be completed in varying numbers of ways, the total number of ways to complete the procedure is the product of the number of ways for each individual task. For example, if a class has 60 students and letter grades can be A, B, C, D, or F, with at least 12 students getting each grade, then the number of ways to assign grades to all students is the product of the number of students that can get each grade.



















