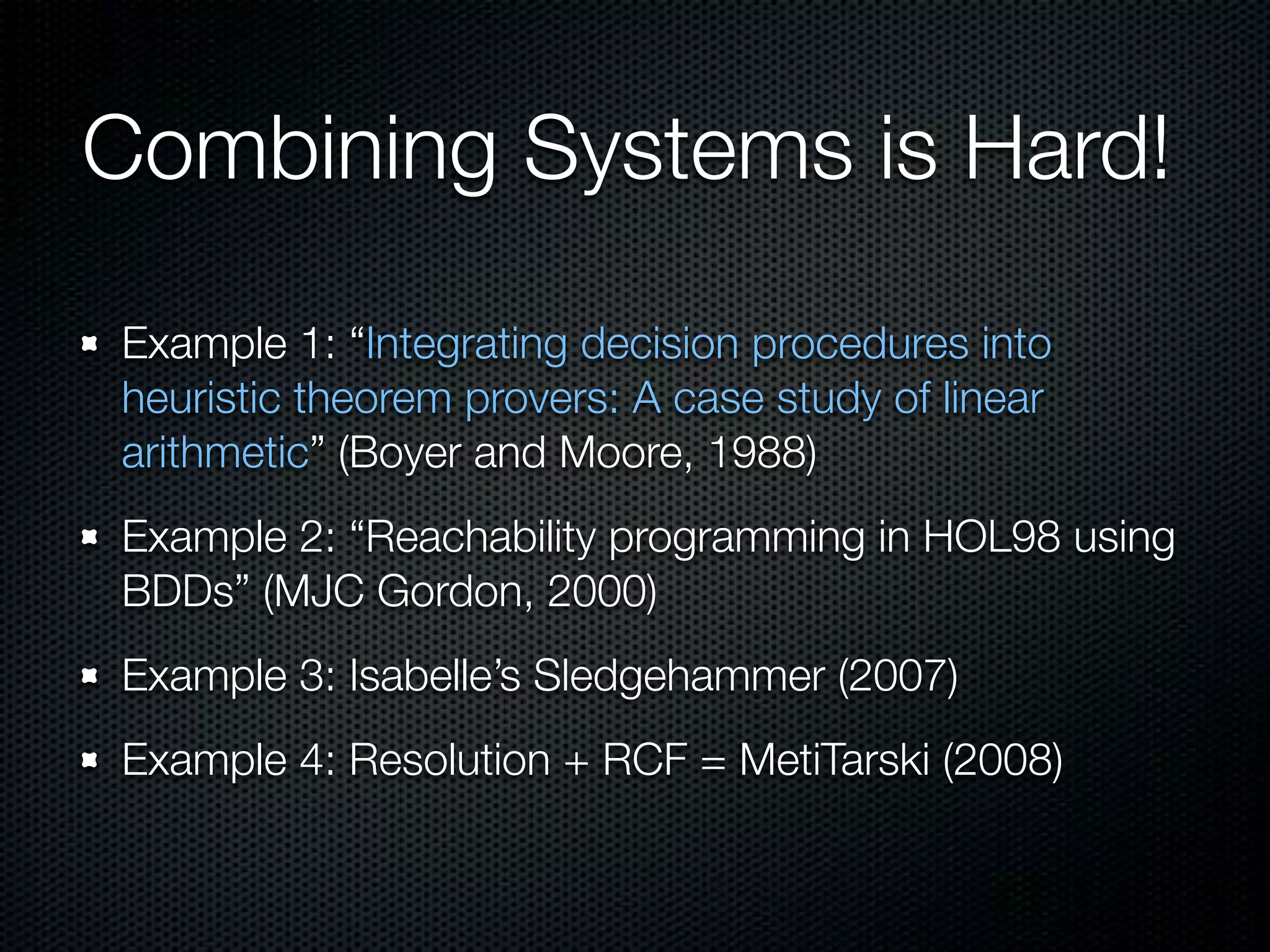
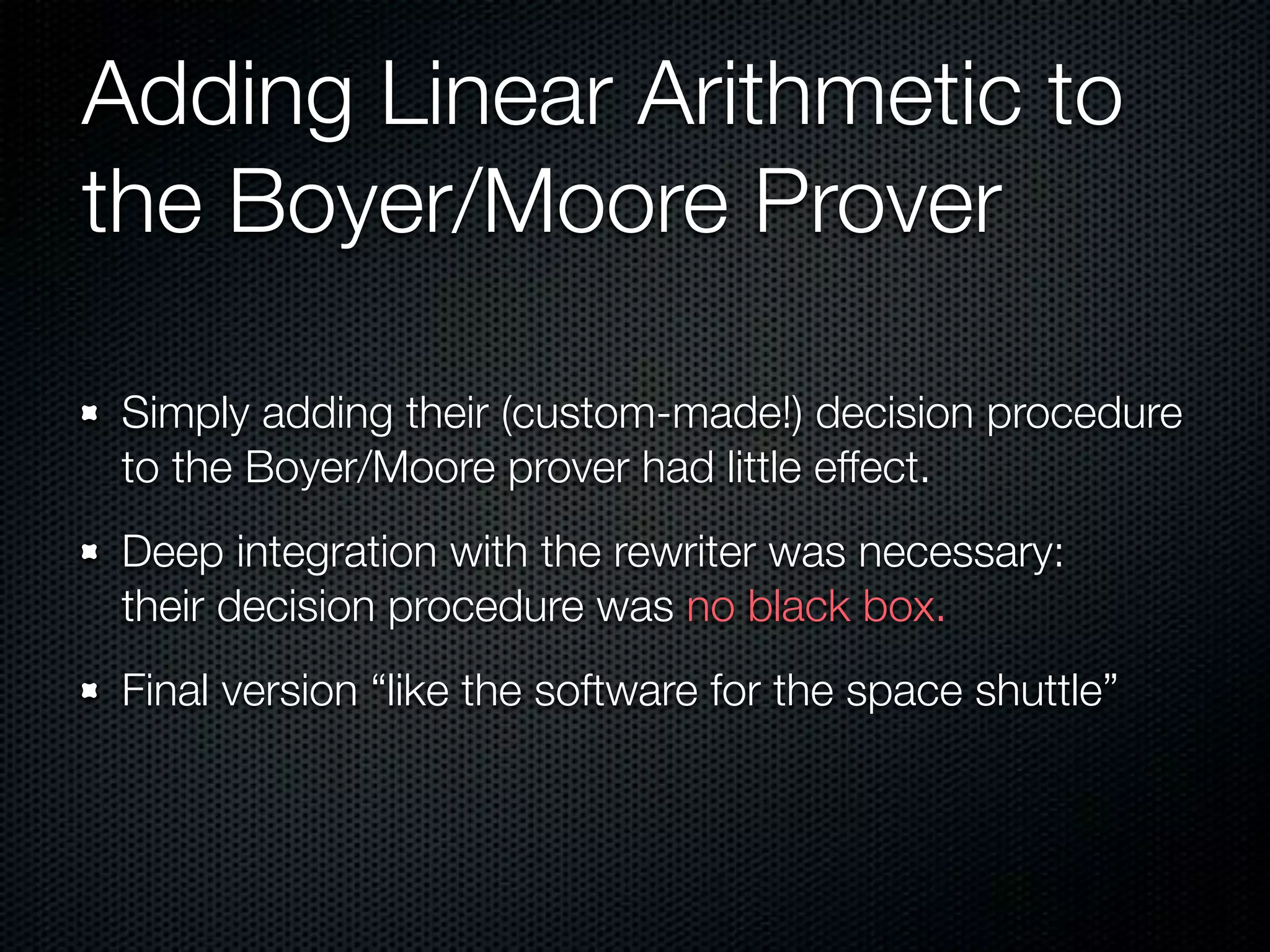
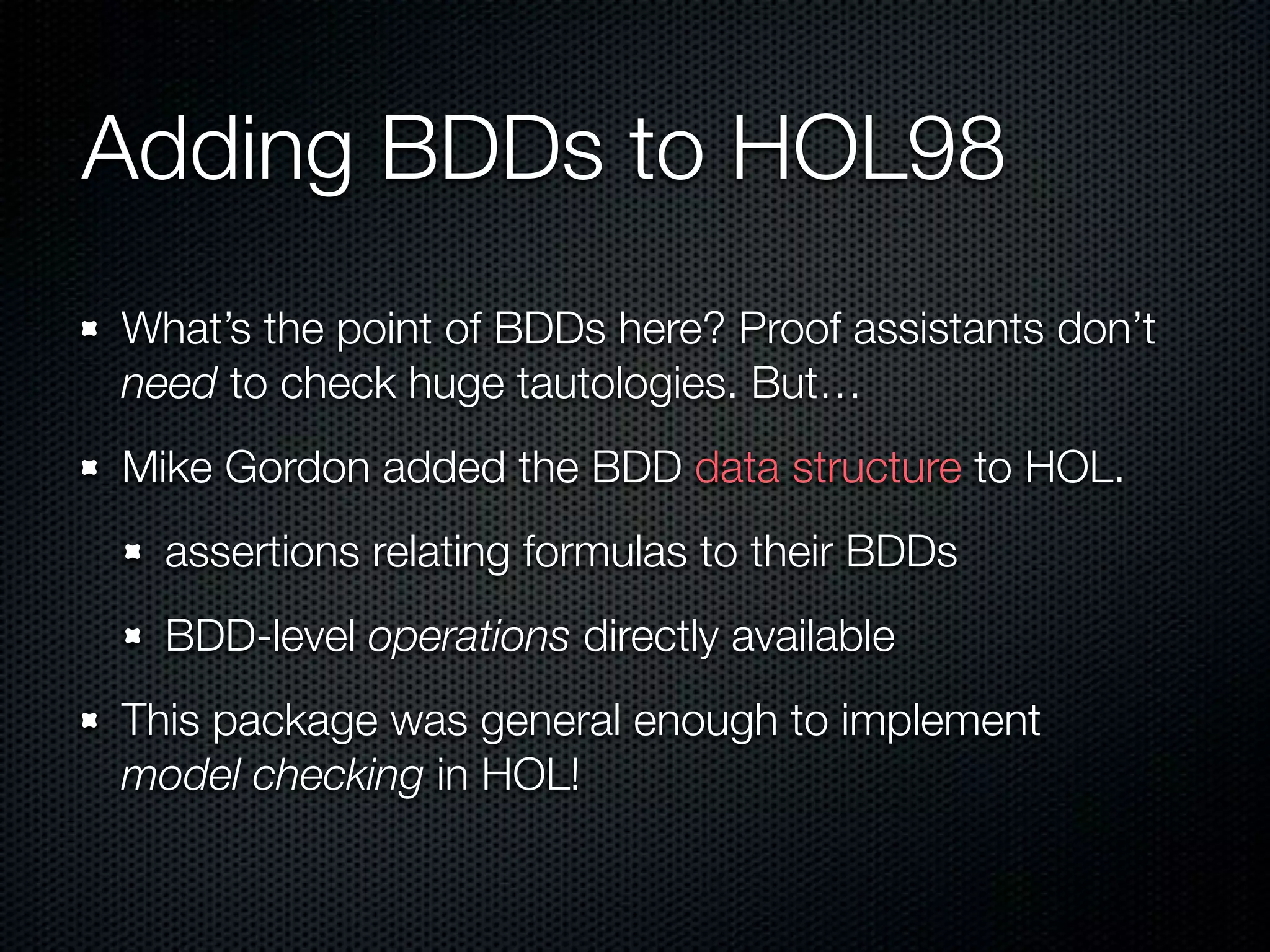
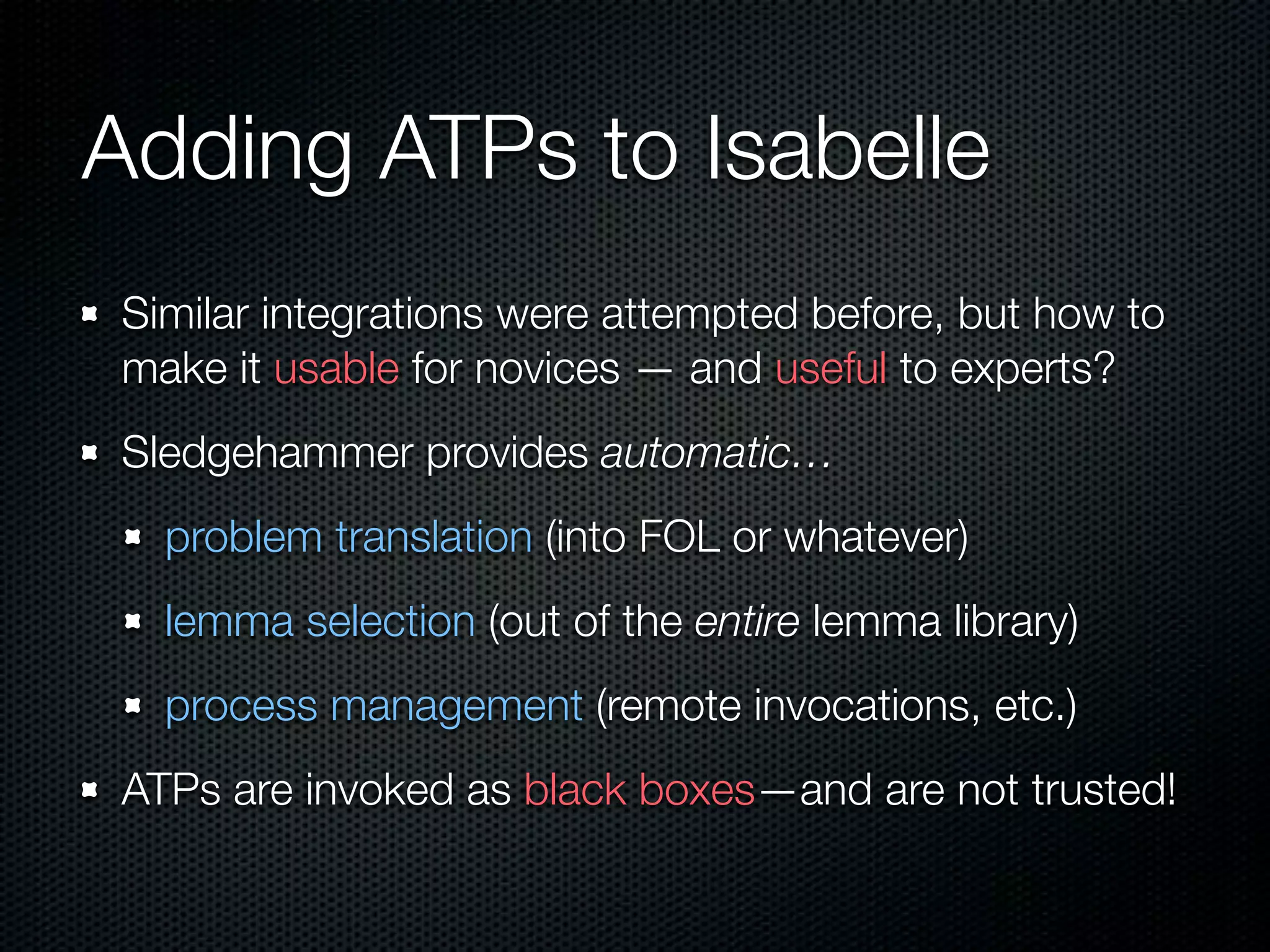
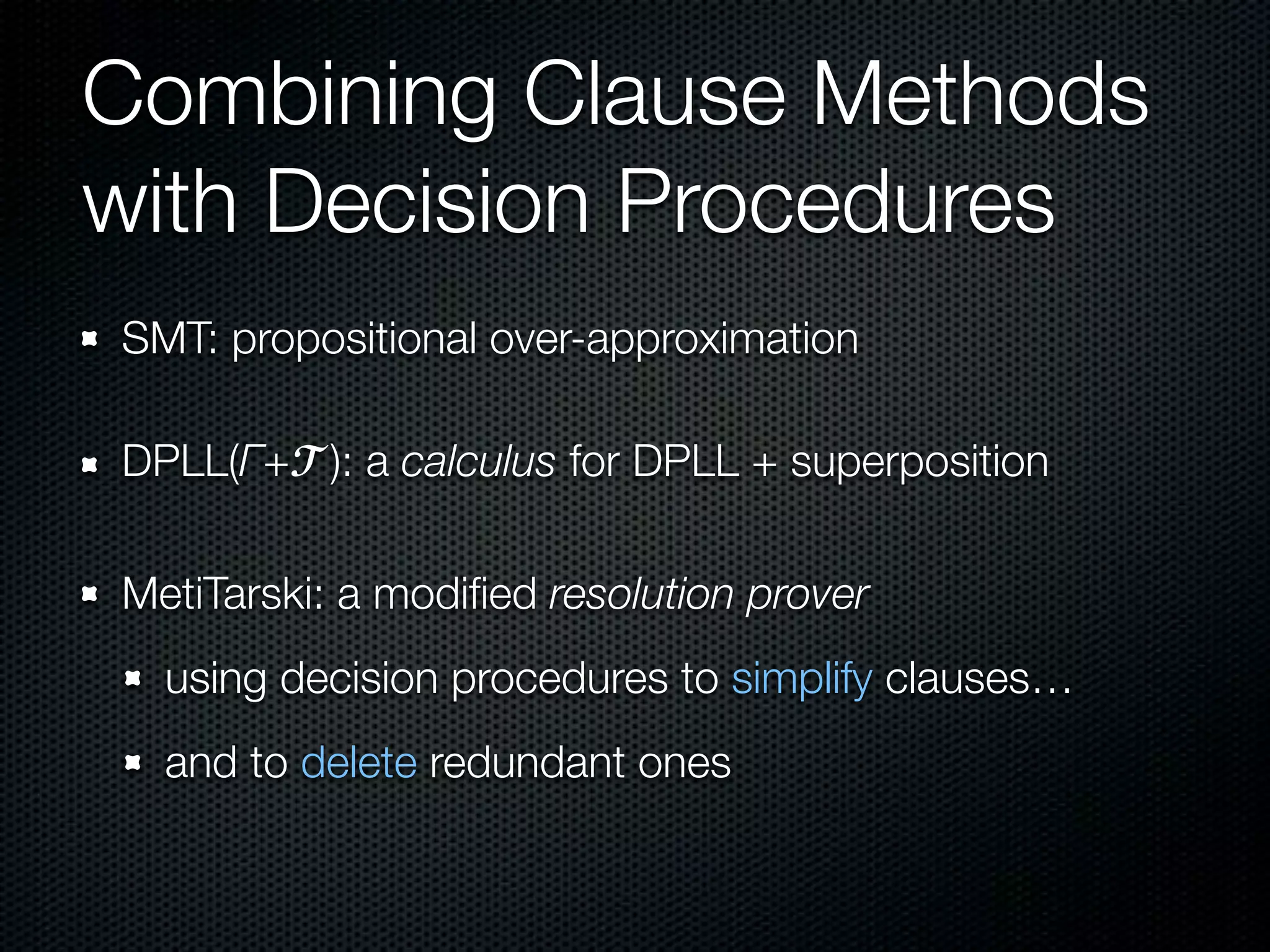
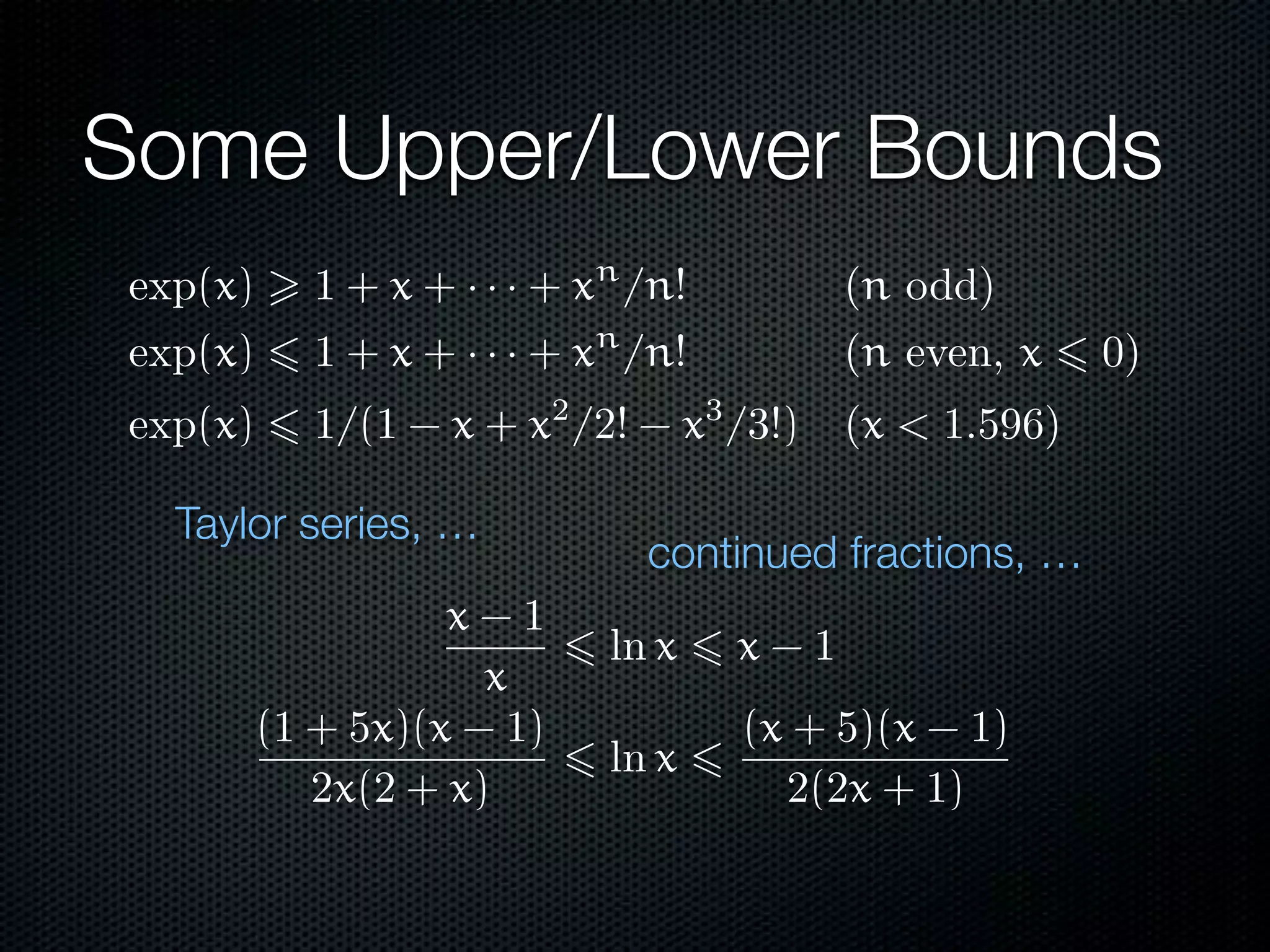
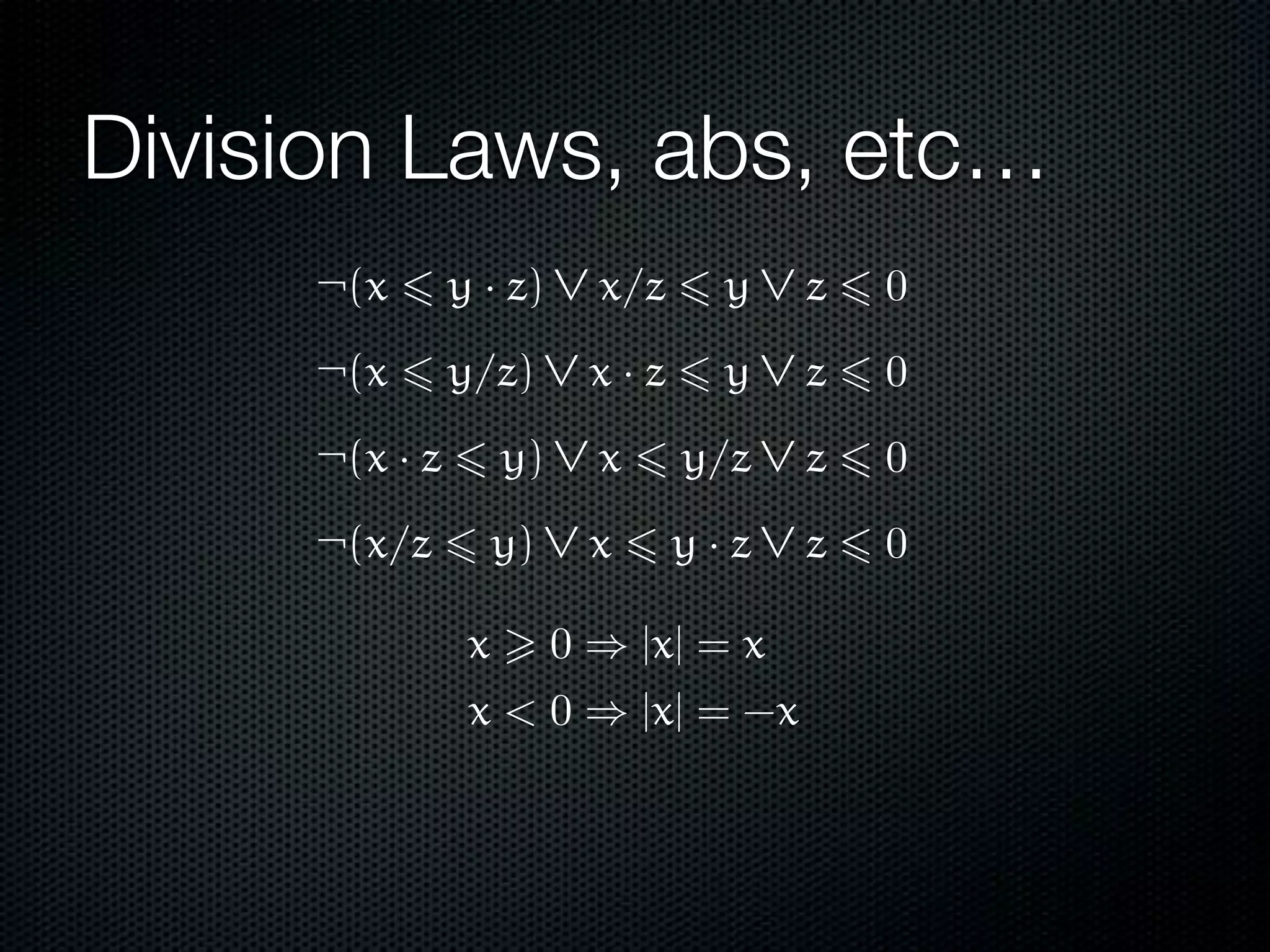
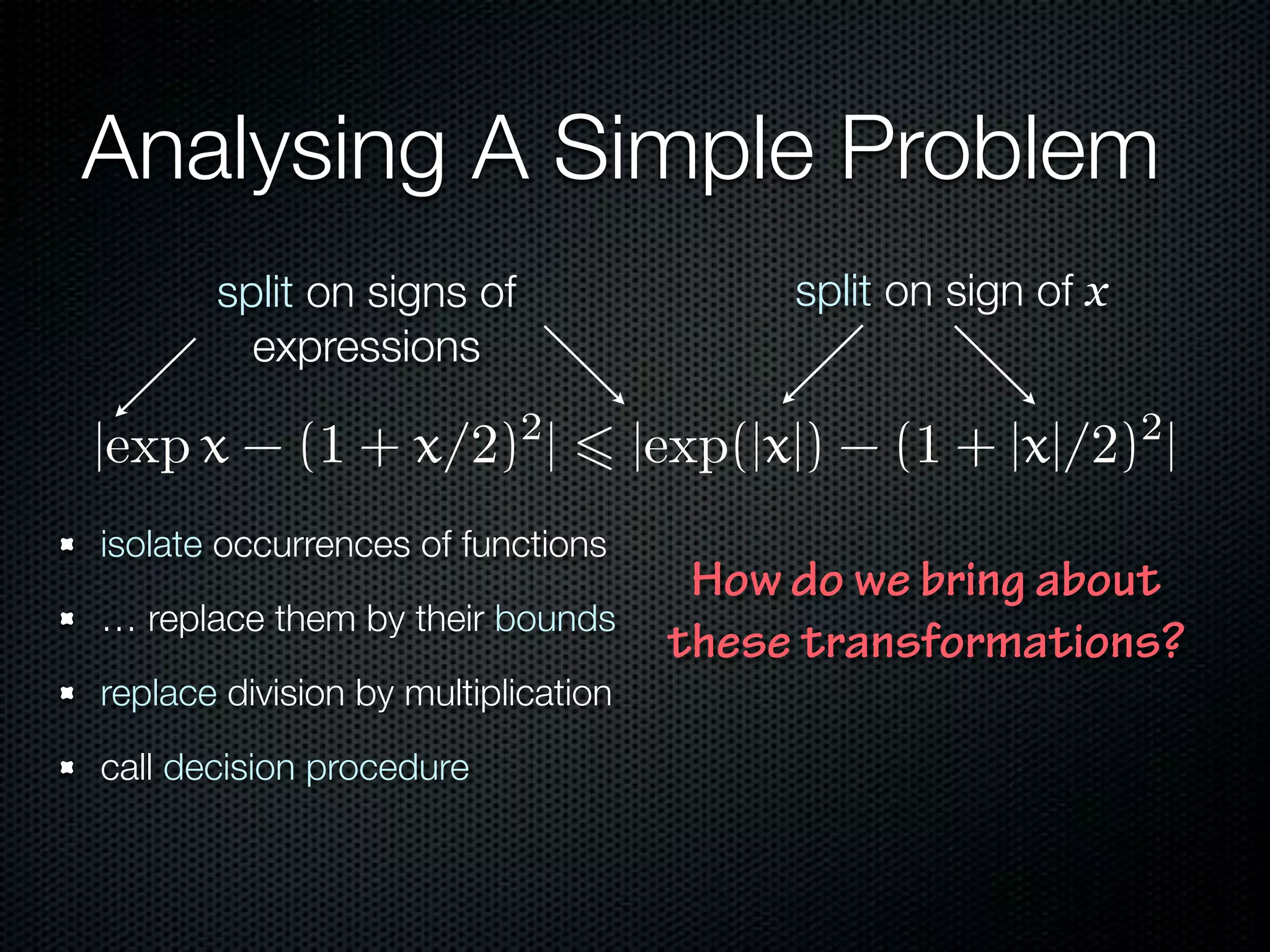
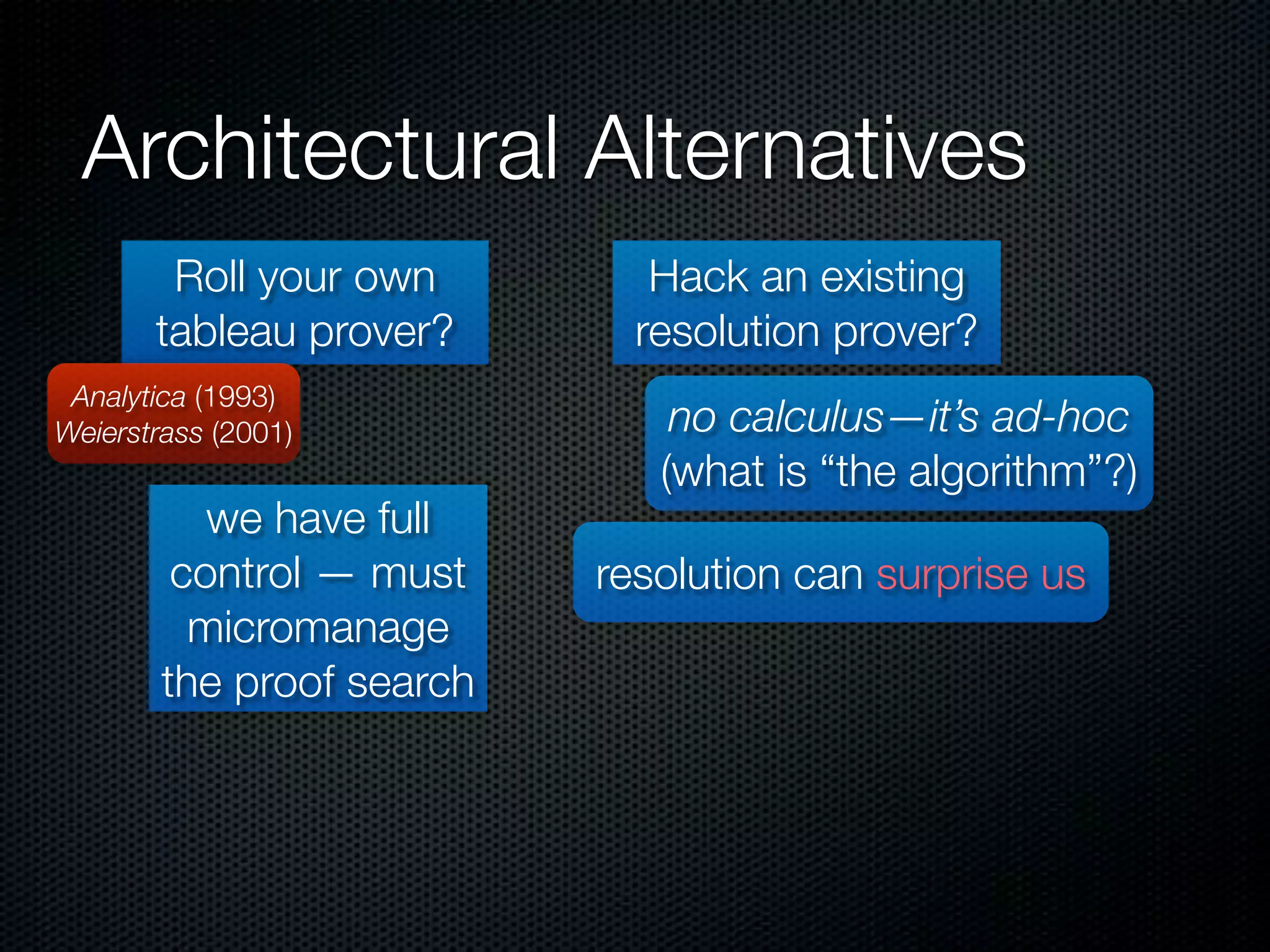
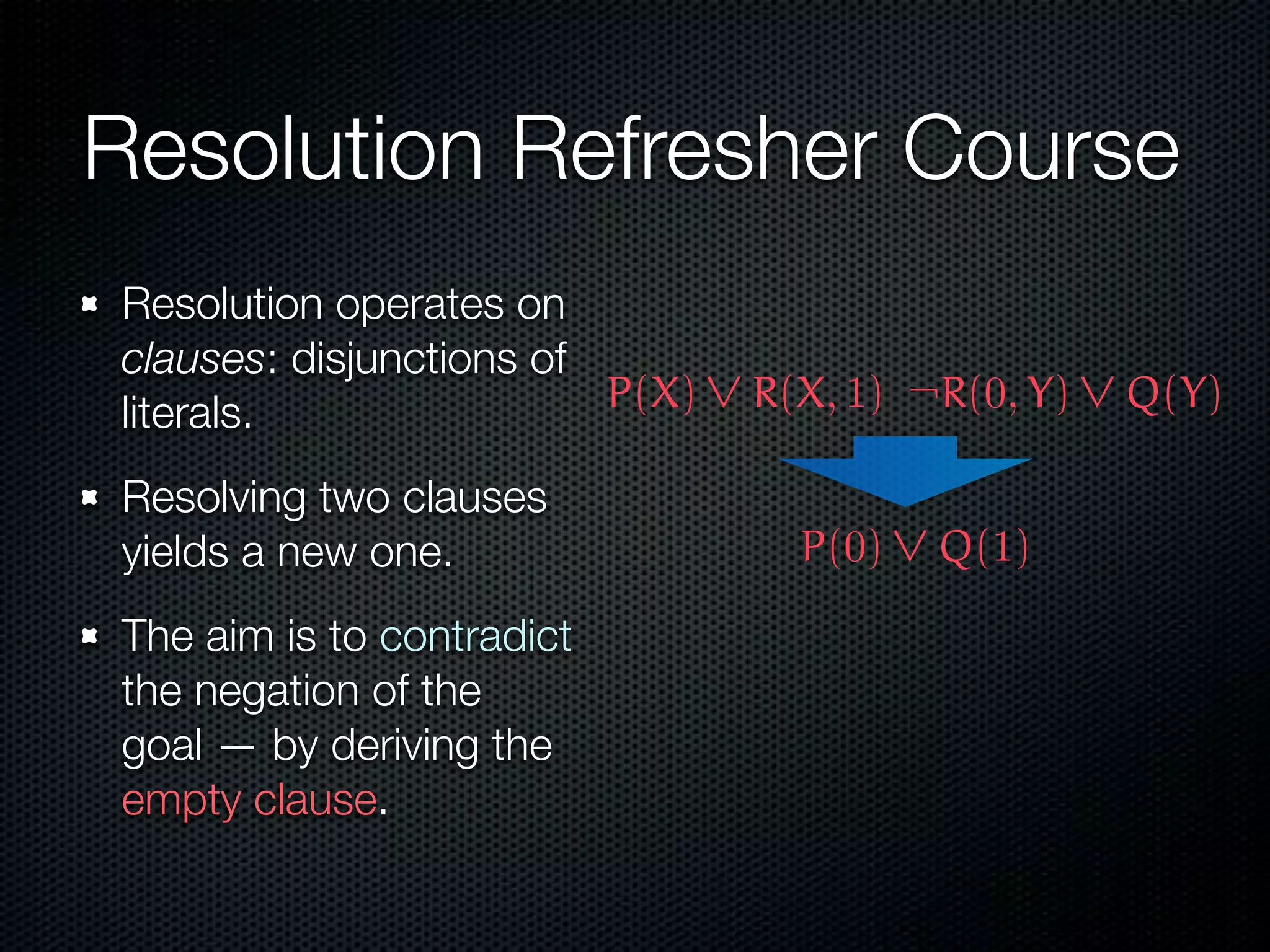
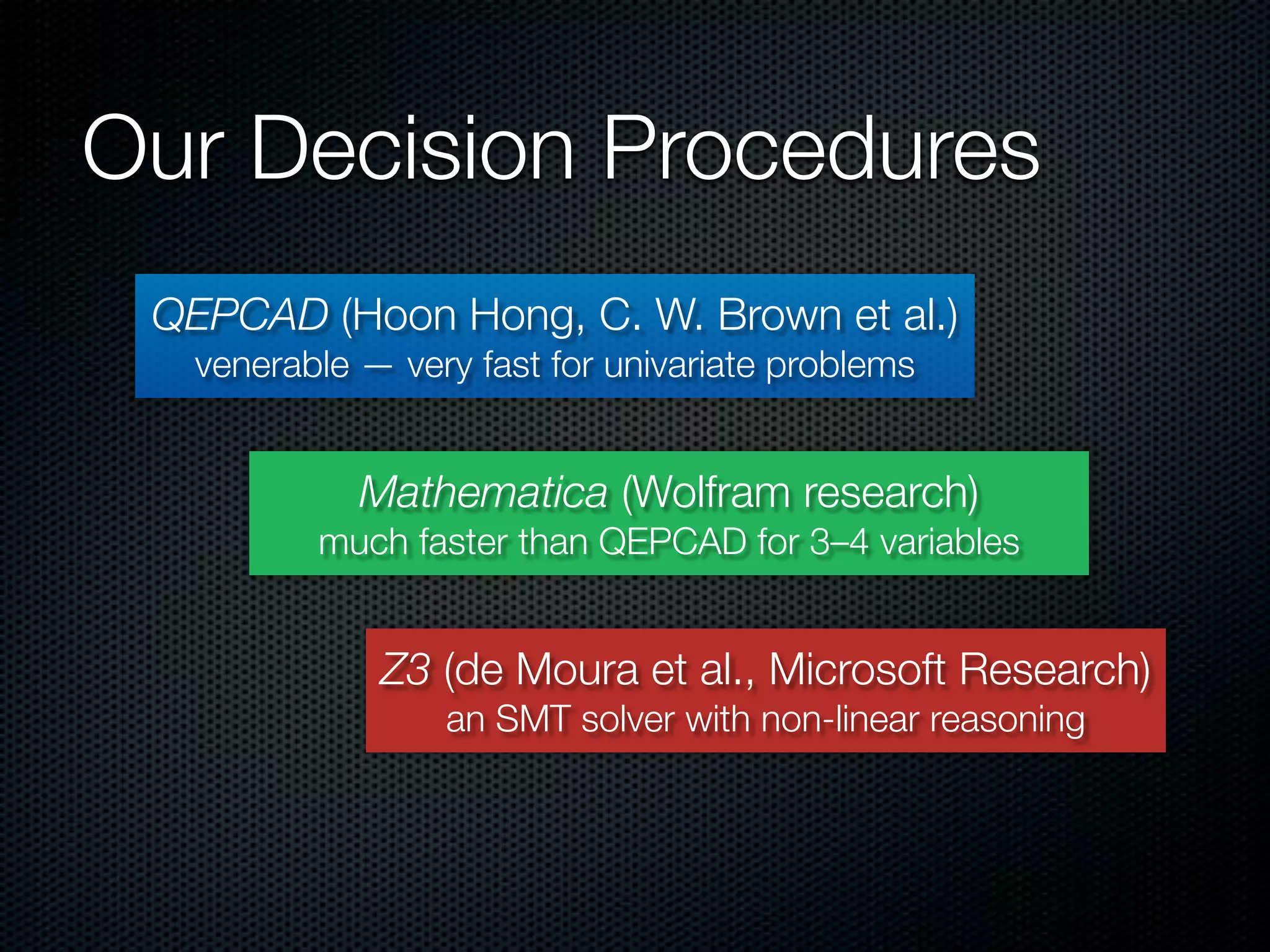
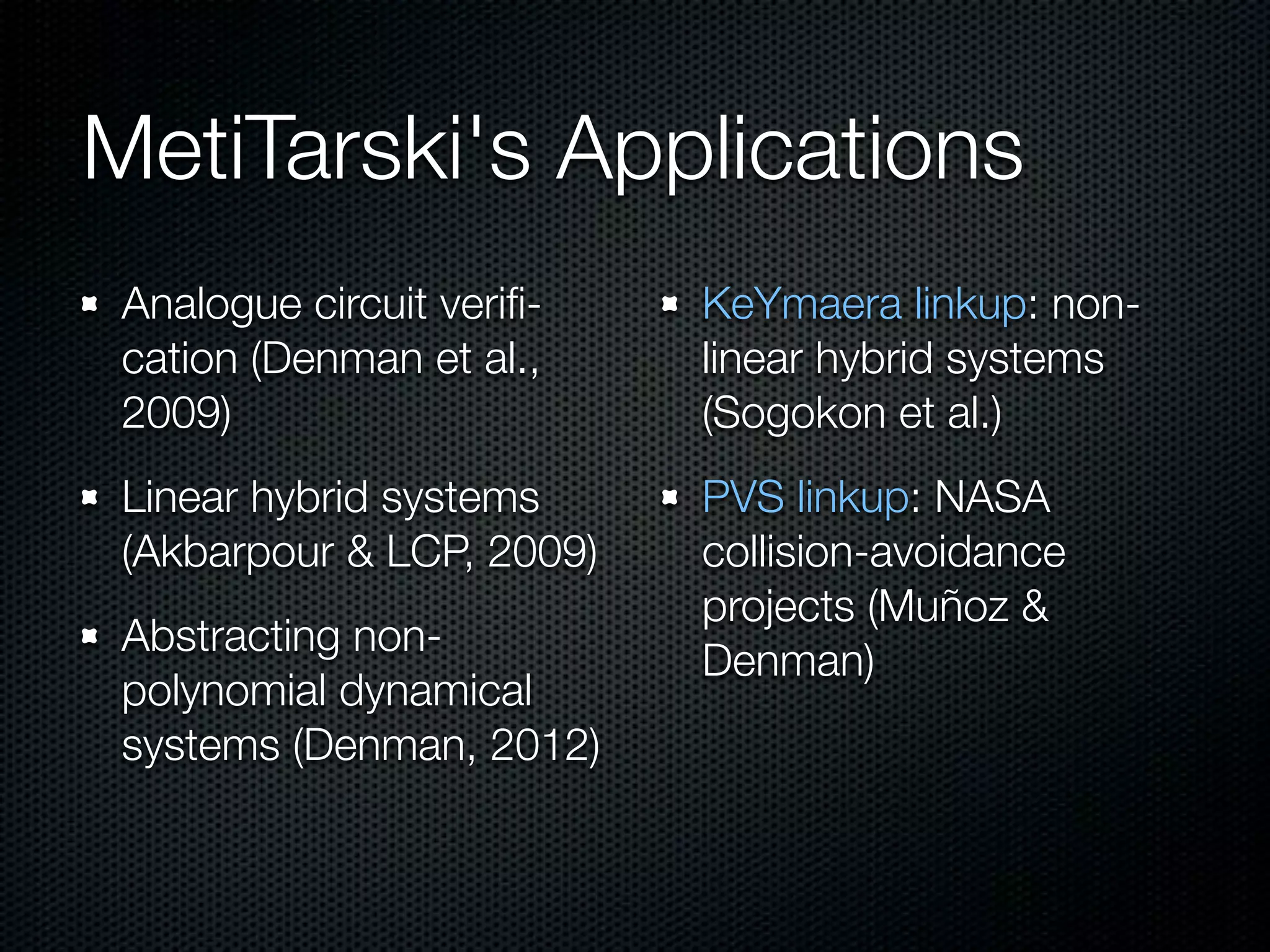
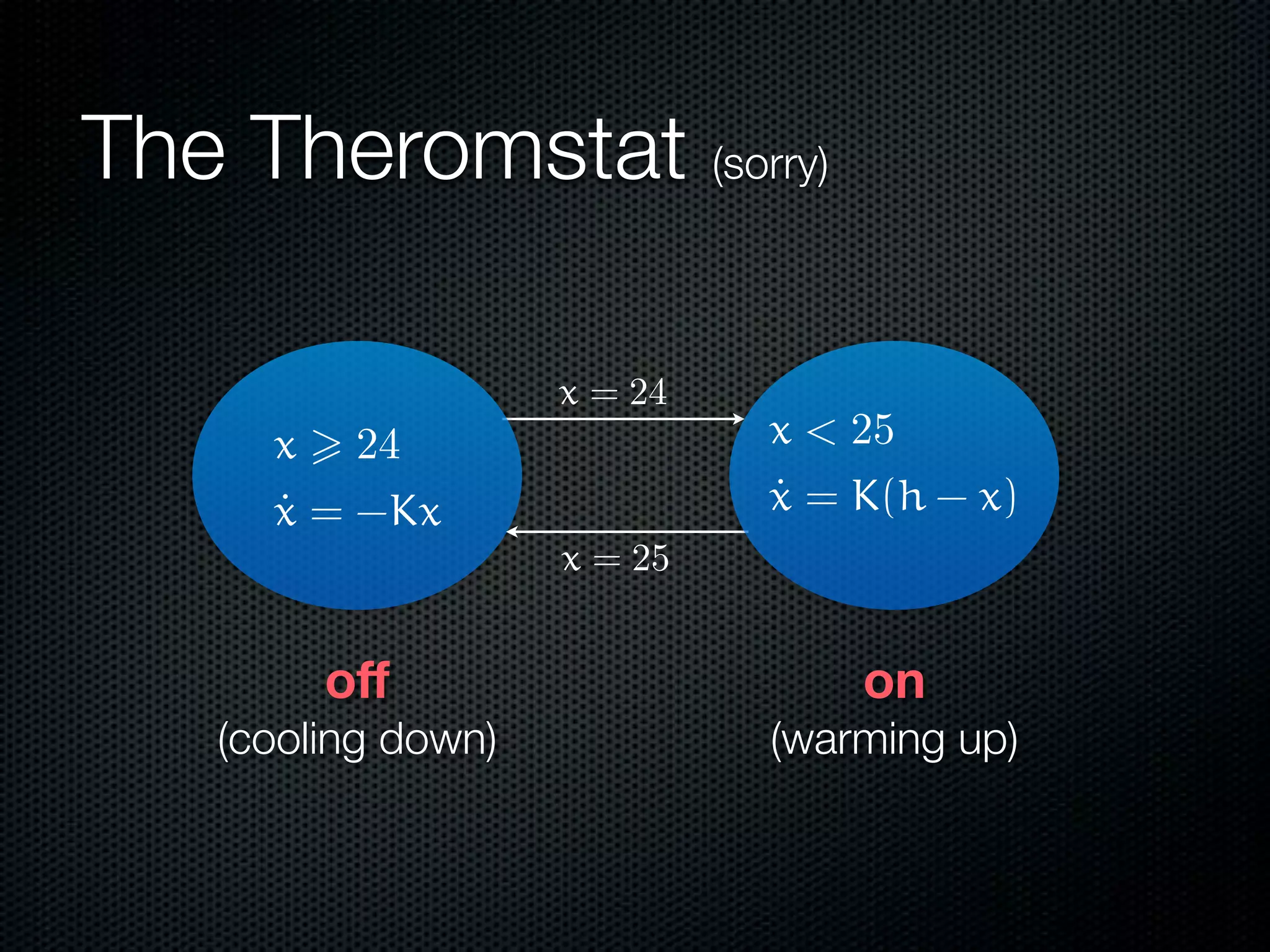
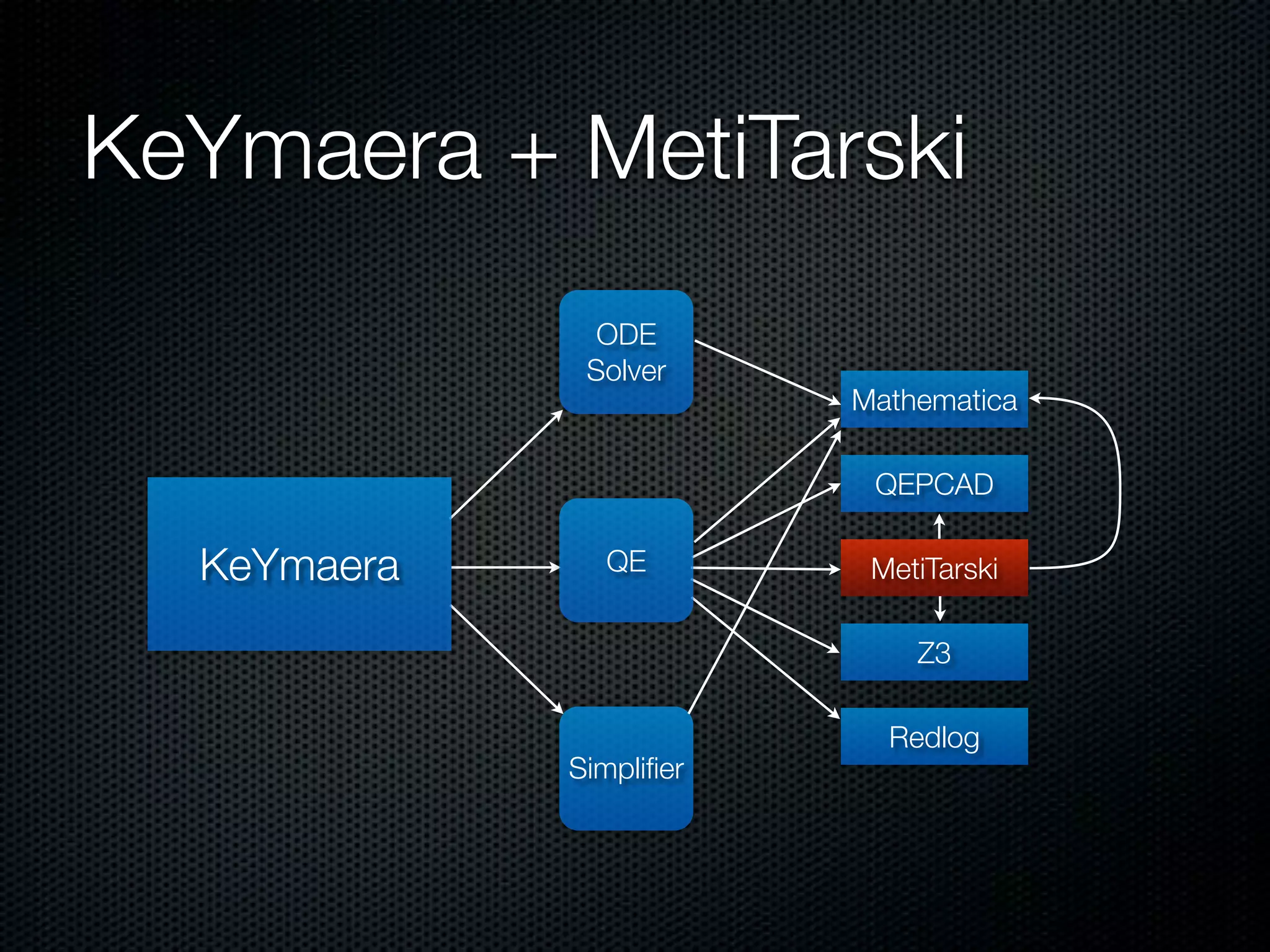
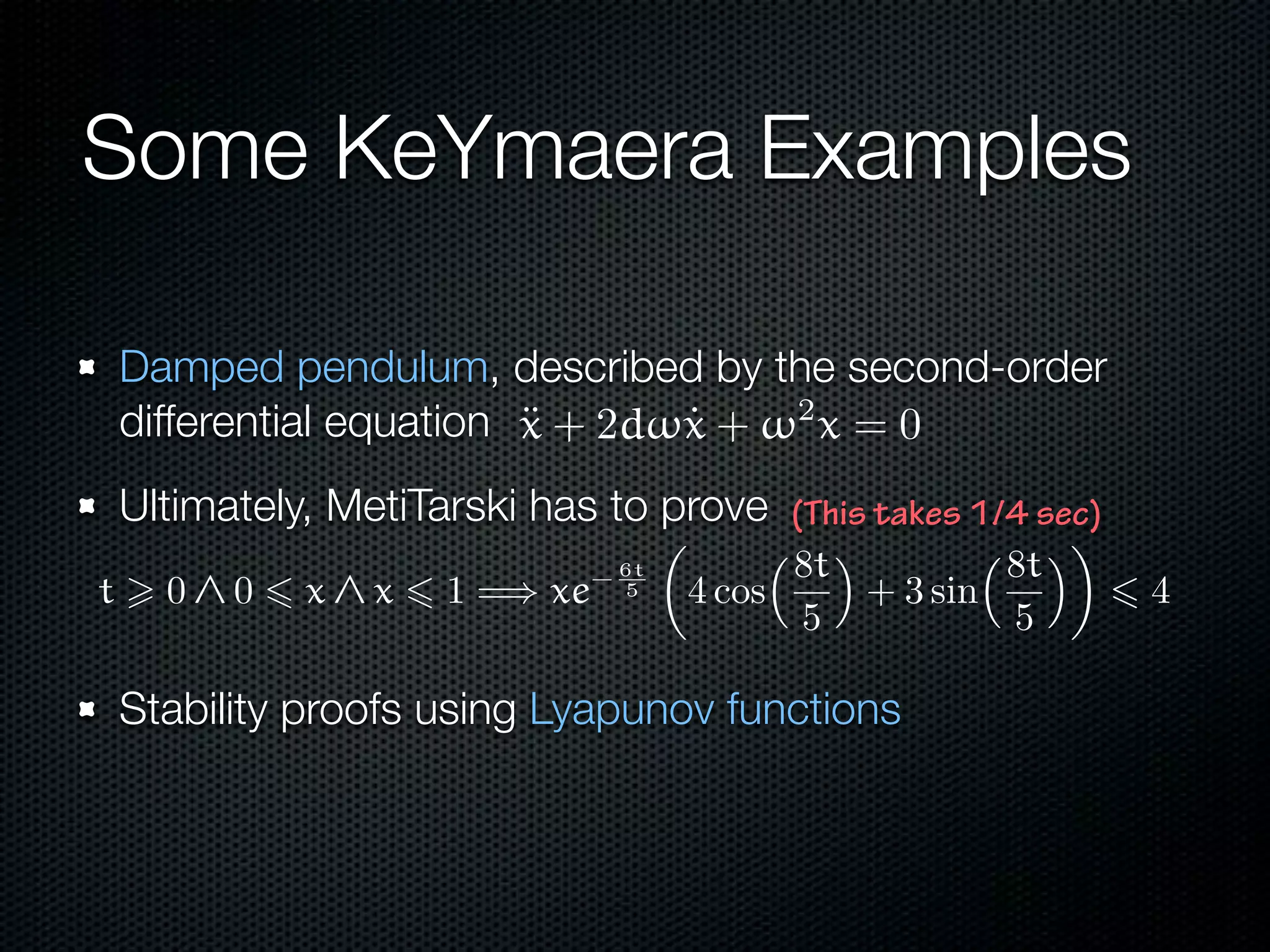
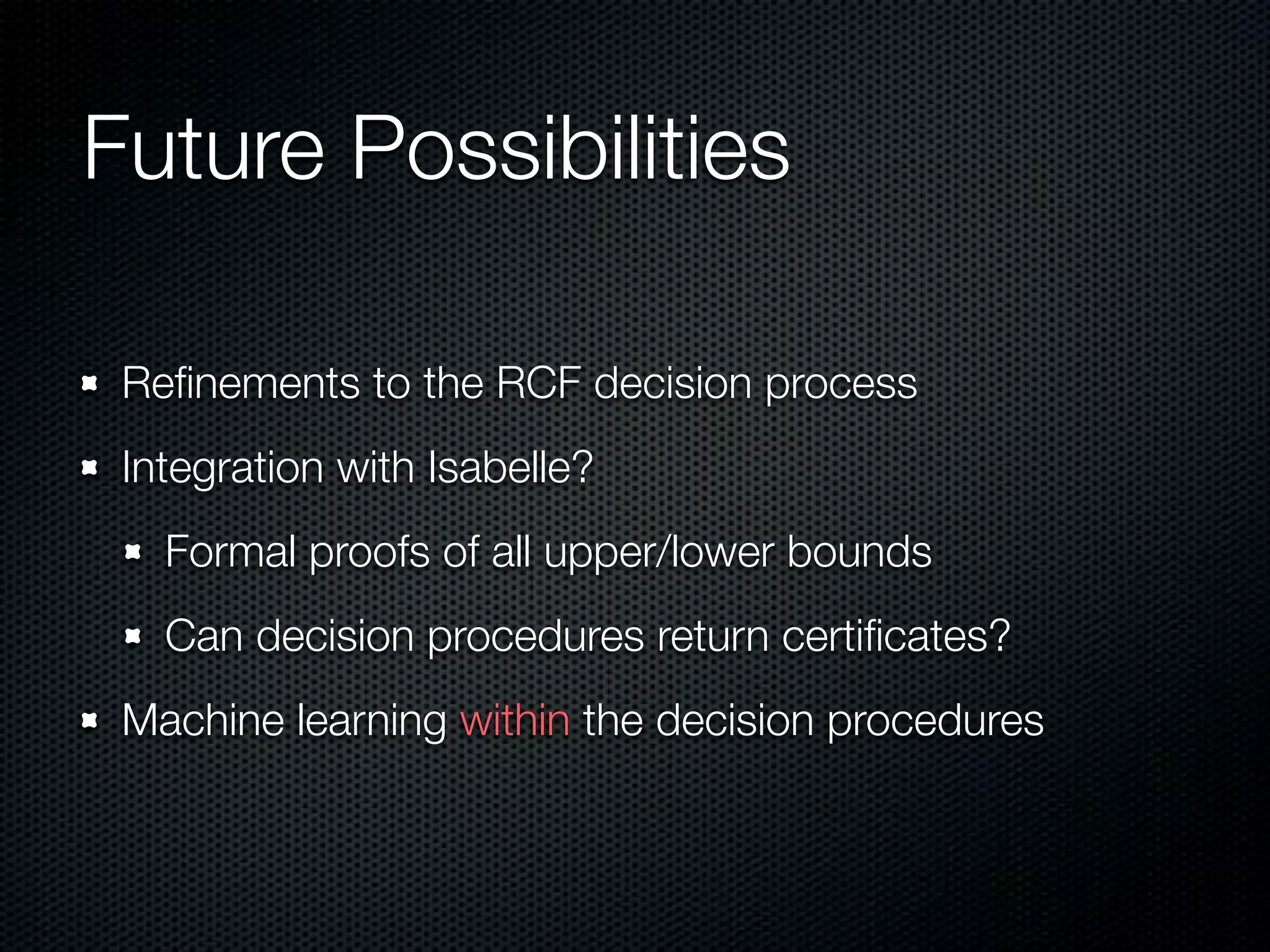
This document summarizes Lawrence Paulson's work on MetiTarski, a system that combines resolution theorem proving with decision procedures for real arithmetic. MetiTarski aims to prove theorems involving transcendental functions by replacing functions with rational bounds and using decision procedures to simplify the problems into decidable forms. The system has been integrated with other tools like KeYmaera and PVS to verify properties of hybrid systems involving both discrete and continuous dynamics. Future work includes improving decision procedures and exploring integrating MetiTarski with other systems like Isabelle.






![Literal Deletion Examples
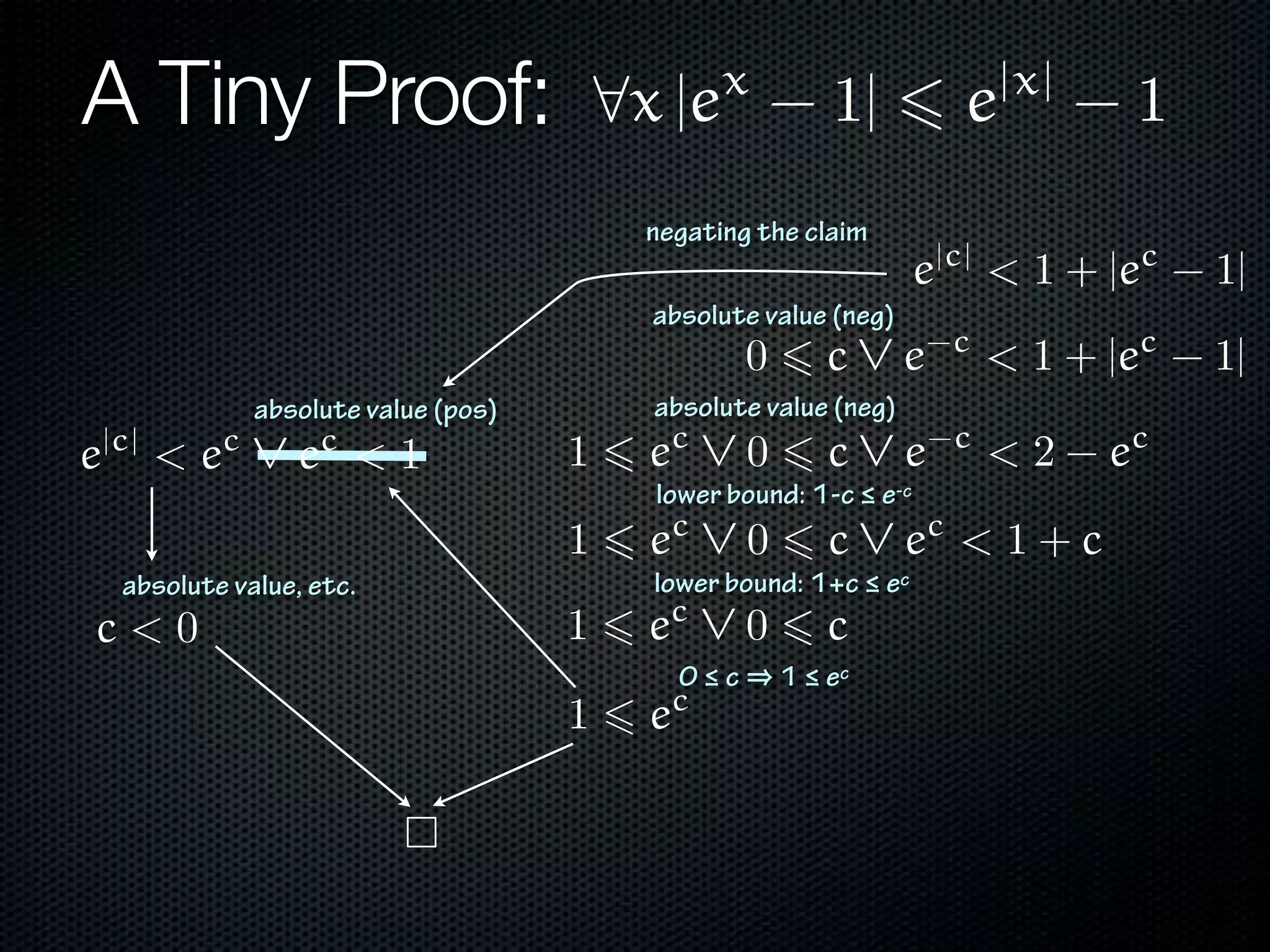
Unsatisfiable literals such as p2 < 0 are deleted.
If x(y+1) > 1 is known, then x=0 will be deleted.
The context includes the negations of adjacent literals
in the clause: z2 > 3 ∨ z > 5
… the decision procedure reduces
∃z [z2 ! 3 ∧ z > 5] to false.](https://image.slidesharecdn.com/frocos-presentation-141105062813-conversion-gate01/75/MetiTarski-s-menagerie-of-cooperating-systems-17-2048.jpg)






![Acknowledgements
Edinburgh: Paul Jackson, G Passmore, A Sogokon;
Manchester: Eva Navarro
Assistance from C. W. Brown, A. Cuyt, J. H. Davenport, J.
Harrison, J. Hurd, D. Lester, C. Muñoz, U. Waldmann, etc.
The research was supported by the Engineering and
Physical Sciences Research Council [grant numbers EP/
C013409/1,EP/I011005/1,EP/I010335/1].](https://image.slidesharecdn.com/frocos-presentation-141105062813-conversion-gate01/75/MetiTarski-s-menagerie-of-cooperating-systems-33-2048.jpg)